Keonne Rodriguez and William Lonergan Hill, founders of Samourai Wallet, a cryptocurrency mixing service, were sentenced in April 2024 and their sites taken down for executing more than US$2 billion in unlawful transactions and laundering more than US$100 million in criminal proceeds. Are all traces of the illegal business in the DNS gone? Or do some remain? The WhoisXML API research team sought to find out.
Our team obtained three domains tagged as Samourai Wallet indicators of compromise (IoCs)—samourai[.]io, samourai[.]support, and samouraiwallet[.]com—from threat researcher Dancho Danchev. To uncover possibly related threat artifacts that remain unidentified to date, we expanded the list of IoCs aided by our comprehensive DNS intelligence sources and found:
- Four IP addresses, three of which are malicious
- Two IP-connected domains
- 66 string-connected domains
Note that this post contains only a preview of our findings. The full research, including a sample of the additional artifacts obtained from our analysis are available for download from our website.
Samourai Wallet IoC Facts
We began our analysis by subjecting the three domains identified as IoCs to a bulk WHOIS lookup, which revealed that:
- They were split between two registrars. Namecheap, Inc. administered two domain IoCs while Gandi SAS handled one.

-
The threat actors seem to prefer using old domains, created at the time the services were first offered, that is 2015. Two domain IoCs were created in 2015 while one was created in 2021.

-
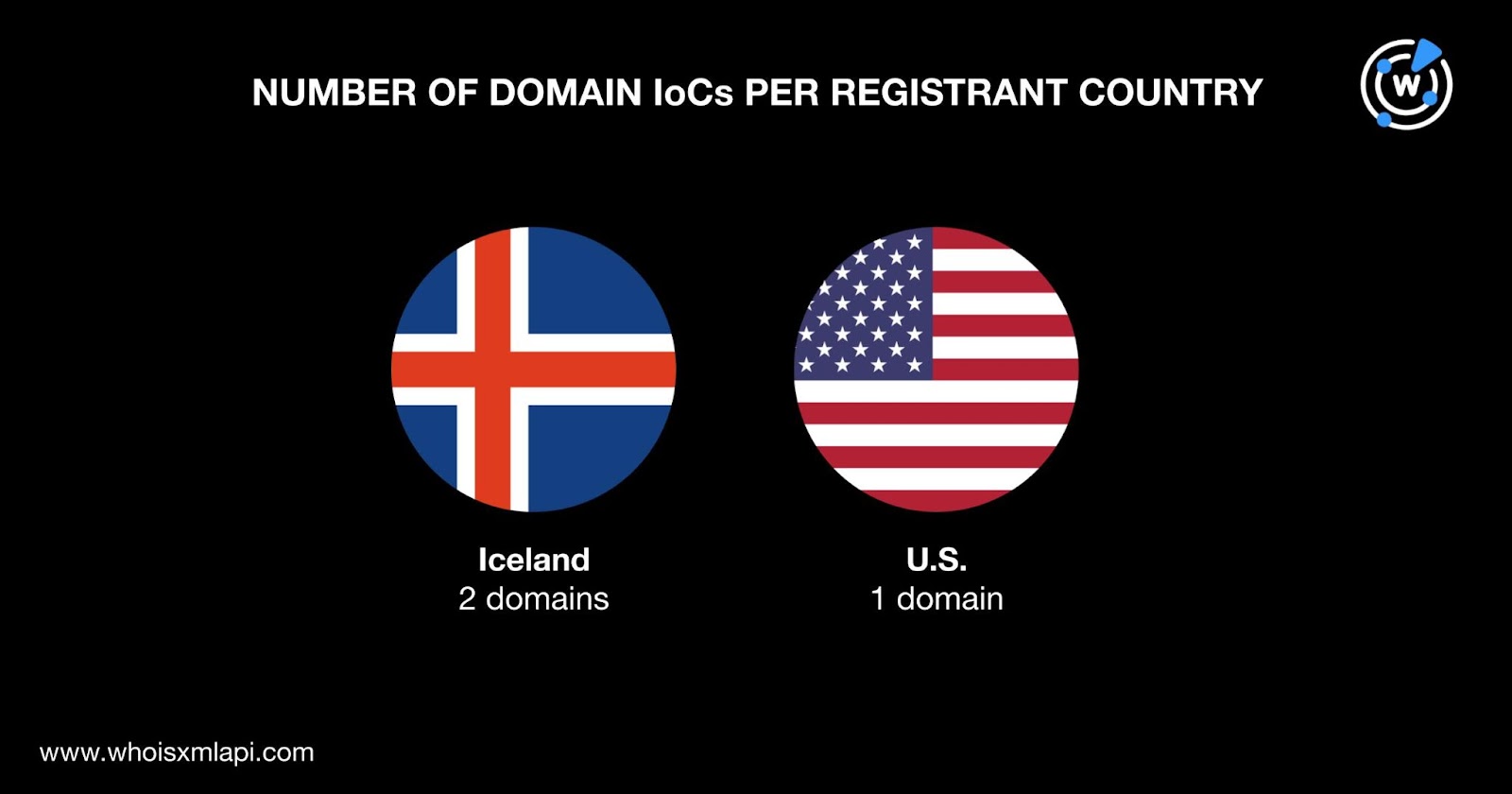
The domain IoCs were registered in two countries. Two were registered in Iceland and one in the U.S.
On to the Hunt for Connected Artifacts
We began our search for artifacts potentially connected to Samourai Wallet by conducting WHOIS History API queries for the three domains tagged as IoCs. That led to the discovery of three email addresses after duplicates were filtered out. None of them, however, were public email addresses, thus ending our search for email-connected domains.
Next, we subjected the three domains identified as IoCs to DNS lookups, which enabled us to uncover four unique IP address resolutions. Threat intelligence lookups for the IP addresses showed that three—104[.]21[.]68[.]107, 162[.]255[.]119[.]8, and 172[.]67[.]194[.]72—were associated with various threats. The IP address 104[.]21[.]68[.]107, for instance, was linked to phishing and generic threats.
We then sought to uncover more information about the four IP addresses via a bulk IP geolocation lookup.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Source: Original Post