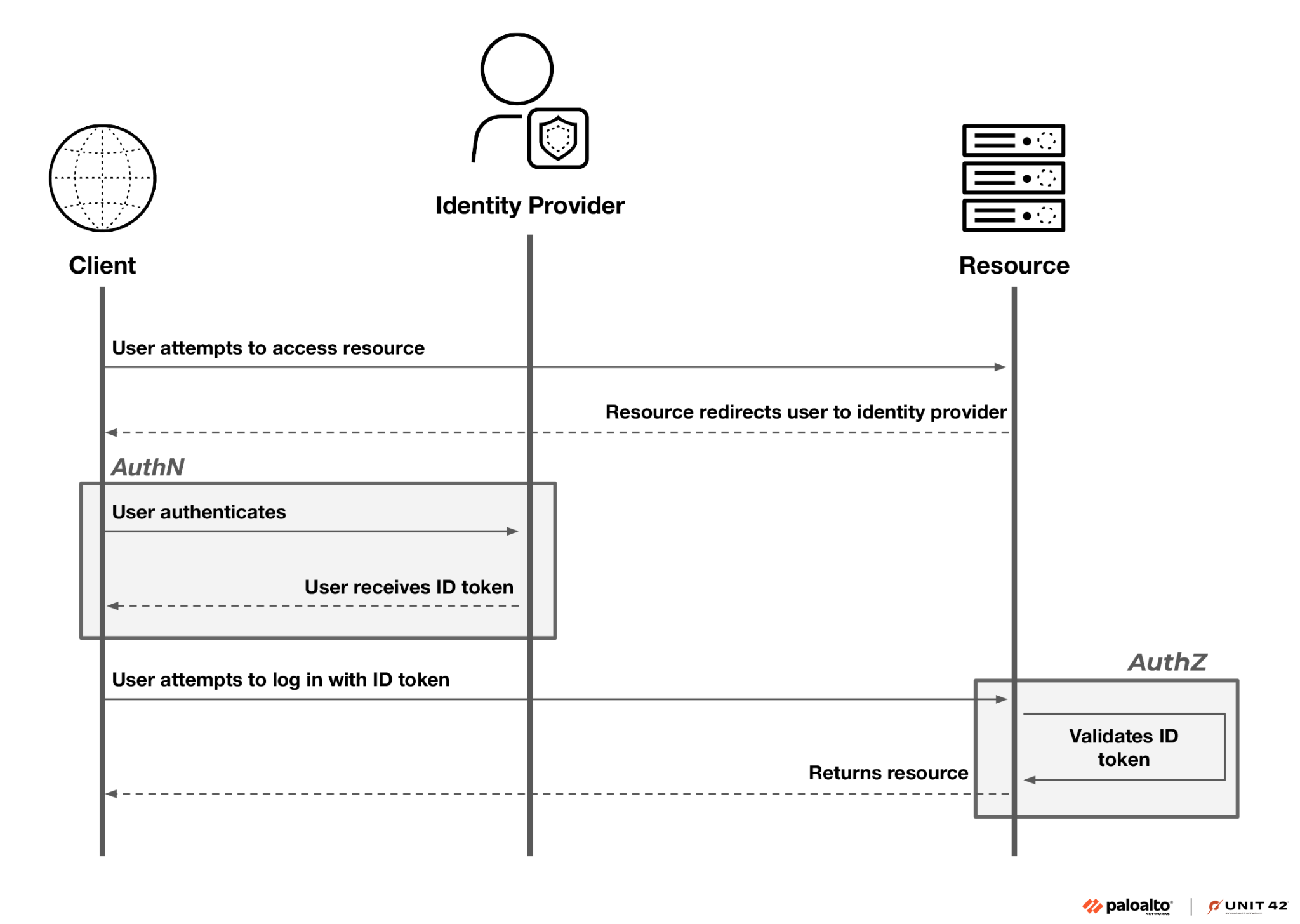
Unit 42’s investigation into OpenID Connect (OIDC) within CI/CD environments revealed significant vulnerabilities that could allow threat actors unauthorized access to restricted resources. Key risks stem from loose identity federation policies, reliance on user-controllable claim values, and potential exploitation of poisoned pipeline execution. It is critical for organizations to strengthen OIDC policies and CI/CD security. CircleCI has responded to these findings with remediation measures and security recommendations. Affected: CI/CD platforms, cloud security, CircleCI
Keypoints :
- Investigated vulnerabilities in OIDC implementations within CI/CD environments.
- Identified three key threat vectors: insufficient identity federation policies, reliance on user-controlled claims, and poisoned pipeline execution.
- Organizations are urged to enhance OIDC policies and tighten CI/CD security practices.
- CircleCI has acknowledged the issues and implemented recommendations for secure configurations.
- Palo Alto Networks offers protective solutions against these OIDC threats.
MITRE Techniques :
- T1078 – Valid Accounts: Threat actors leveraging misconfigured OIDC to gain access as registered users through lax federation policies.
- T1566 – Phishing: Exploitation of user-controlled claims to manipulate authorization decisions.
- T1071 – Application Layer Protocol: Abuse of CI/CD workflows to escalate privileges through poisoned pipeline execution vulnerabilities.
Indicator of Compromise :
- [Domain] circleci.com
- [Domain] github.com
- [Email Address] security@circleci.com
- [MD5] 8d969eef6ecad3a2c6c1d0d2f6b8f6a8
- [SHA-256] 821dbe4e8fbcf21b9fef83048e24c9e7e091f65c8c55c7e2ca82efc2d7cf5f7d
Full Story: https://unit42.paloaltonetworks.com/oidc-misconfigurations-in-ci-cd/