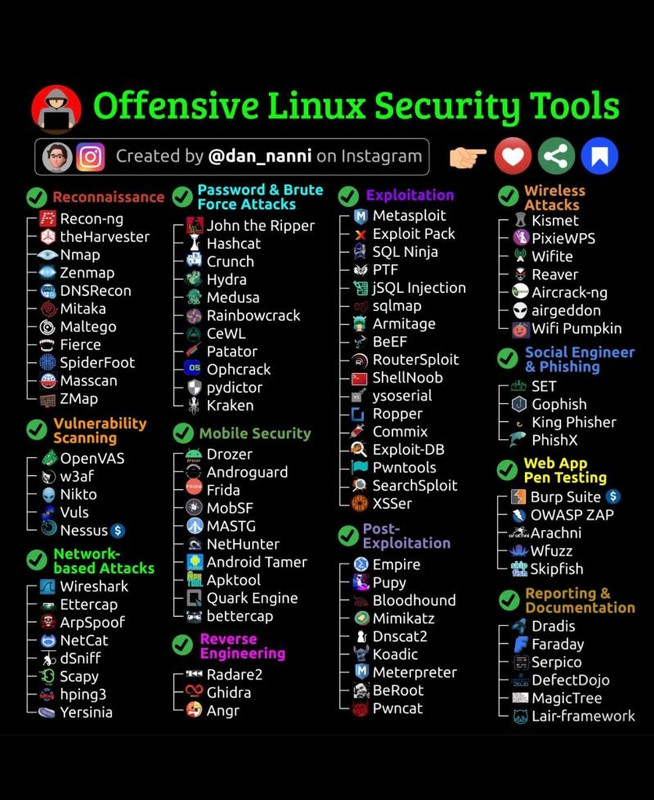
Reconnaissance in Cybersecurity: Overview and Essential Tools
What is Reconnaissance?
Reconnaissance is the first phase of the cyberattack lifecycle, where attackers gather as much information as possible about their target (individuals, networks, or organizations) before launching an attack. This stage involves collecting details such as IP addresses, domains, emails, servers, and potential vulnerabilities that can be exploited.
Essential Reconnaissance Tools and Their Functions
Below is an overview of the tools commonly used for reconnaissance, as depicted in the image:
1. Recon-ng
Recon-ng is a Python-based framework designed for web reconnaissance. It provides an interface similar to Metasploit and offers modules for collecting data such as domain information, subdomains, and WHOIS data. Its modularity and ease of use make it a favorite among security professionals.
2. theHarvester
TheHarvester is a tool for gathering email addresses, subdomains, hosts, and IP addresses from public sources like search engines (Google, Bing) and social media platforms. It’s highly efficient for footprinting and early-stage reconnaissance.
3. Nmap (Network Mapper)
Nmap is one of the most popular tools for network scanning and reconnaissance. It helps map networks, identify live hosts, discover open ports, and detect operating systems and services running on target devices.
4. Zenmap
Zenmap is the graphical user interface (GUI) for Nmap. It simplifies the process of creating and analyzing network scans, making it suitable for beginners and advanced users alike.
5. DNSRecon
DNSRecon focuses on DNS enumeration. It performs tasks such as zone transfers, brute-forcing subdomains, and checking for misconfigurations in DNS servers.
6. Mitaka
Mitaka is a browser extension used for OSINT (Open-Source Intelligence). It allows users to investigate domains, IPs, and other indicators directly from their browser using threat intelligence databases.
7. Fierce
Fierce is a domain scanner for locating non-contiguous IP space and subdomains. It uses brute force to identify subdomains and locate hidden domains within a network.
8. SpiderFoot
SpiderFoot is an open-source reconnaissance tool designed to automate OSINT tasks. It gathers data from hundreds of public sources, such as IP geolocation, DNS records, SSL certificates, and social media profiles.
9. Masscan
Masscan is a high-performance port scanner known for its speed. It can scan entire IP ranges and identify open ports within seconds, making it an excellent choice for large-scale reconnaissance.
10. ZMap
Similar to Masscan, ZMap is a fast network scanner focused on internet-wide scanning. It is used to collect data on the global exposure of specific ports or services.
Conclusion
Reconnaissance is a crucial step in understanding the security landscape of a target. The tools mentioned above provide various capabilities to gather critical information efficiently. However, they must be used responsibly and ethically, adhering to the laws and regulations in your region.