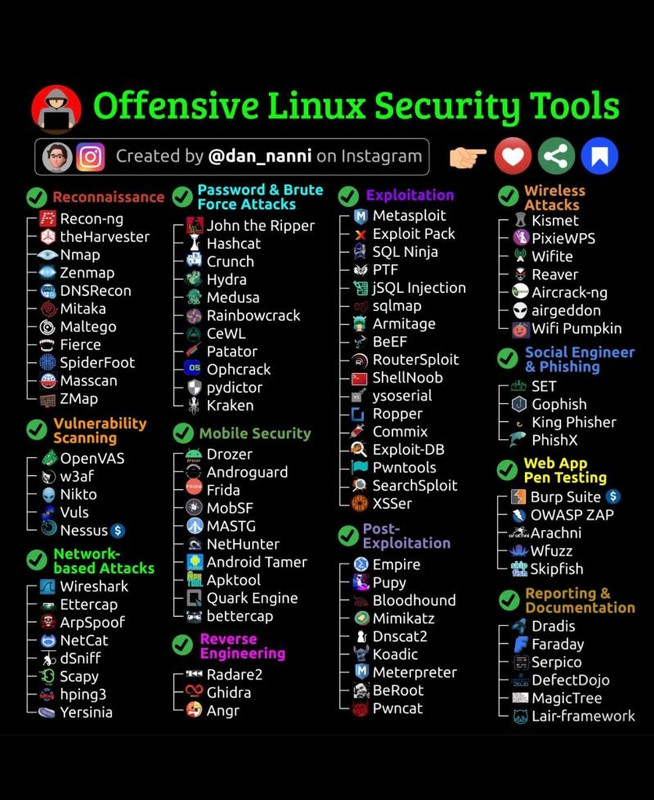
What is a Password and Brute Force Attack?
A password attack is an attempt to gain unauthorized access to a system by cracking or guessing a user’s credentials. One of the most common methods used in password attacks is brute force, where an attacker systematically tries different password combinations until they find the correct one.
Brute force attacks can be time-consuming, but attackers leverage automated tools to accelerate the process. Other advanced methods, such as dictionary attacks and hybrid attacks, combine brute force techniques with wordlists and predefined patterns to improve efficiency.
Popular Password Cracking and Brute Force Tools
The following tools are widely used in ethical hacking and penetration testing to test password security and identify weak credentials:
1. John the Ripper
John the Ripper is an open-source password cracking tool designed for security testing. It supports multiple hashing algorithms and works with password-protected files such as ZIP, PDF, and Linux shadow files. It uses both dictionary and brute force attacks to crack passwords.
2. Hashcat
Hashcat is one of the most powerful and fastest password recovery tools, capable of cracking various hash types (MD5, SHA1, NTLM, etc.). It supports GPU acceleration, allowing for high-speed brute force attacks using NVIDIA or AMD graphics cards.
3. Crunch
Crunch is a wordlist generator used for dictionary attacks. It allows users to create custom wordlists with specified patterns, making it useful for generating targeted passwords based on known information about the target.
4. Hydra
Hydra is a fast and versatile network login cracker that supports numerous protocols, including SSH, FTP, HTTP, SMTP, and MySQL. It performs online brute force attacks against remote authentication services.
5. Medusa
Medusa is similar to Hydra but optimized for speed and parallelism. It can test multiple passwords against multiple targets simultaneously, making it a preferred tool for large-scale password attacks.
6. RainbowCrack
RainbowCrack uses rainbow tables to crack password hashes quickly. Unlike traditional brute force, it precomputes hash values and stores them in tables, significantly reducing cracking time.
7. CeWL
CeWL (Custom Word List Generator) crawls websites and extracts words to generate targeted wordlists for dictionary attacks. This tool is useful for social engineering attacks where passwords are derived from personal or company-related information.
8. Patator
Patator is an advanced brute force tool that supports multiple protocols. It is highly flexible, allowing users to customize attack parameters and avoid detection by security mechanisms.
9. Ophcrack
Ophcrack is a Windows password cracker that uses rainbow tables to crack LM and NTLM hashes. It comes with a graphical interface and can retrieve Windows login credentials from offline systems.
10. Pydictor
Pydictor is a powerful wordlist generator designed for customized dictionary attacks. It can generate passwords based on specific rules and patterns, improving efficiency when targeting known password structures.
11. Kraken
Kraken is an advanced hash-cracking tool that supports distributed computing, enabling multiple machines to work together for faster password recovery.
How to Protect Against Brute Force Attacks
To defend against brute force attacks, consider implementing the following security measures:
- Use Strong Passwords: Create complex passwords with a mix of uppercase, lowercase, numbers, and special characters.
- Enable Account Lockout Policies: Lock user accounts after multiple failed login attempts to prevent brute force attacks.
- Implement Multi-Factor Authentication (MFA): Adding an extra layer of authentication makes it harder for attackers to gain access.
- Use CAPTCHA Verification: CAPTCHA challenges prevent automated brute force attacks on login pages.
- Monitor and Limit Login Attempts: Restrict the number of login attempts and monitor for unusual login activity.
Conclusion
Brute force attacks remain a major cybersecurity threat, but ethical hackers and security professionals use these tools to test and strengthen system defenses. Organizations should proactively implement security best practices to mitigate the risks associated with weak passwords and authentication vulnerabilities.