This article discusses three unique malware samples discovered recently: a C++/CLI IIS backdoor, a bootkit that installs a GRUB 2 bootloader, and a post-exploitation framework known as ProjectGeass. Each sample demonstrates unconventional techniques and complexities, highlighting the evolving threat landscape. Affected: IIS, Windows, system environments
Keypoints :
- Three unique malware samples discovered exhibiting novel characteristics.
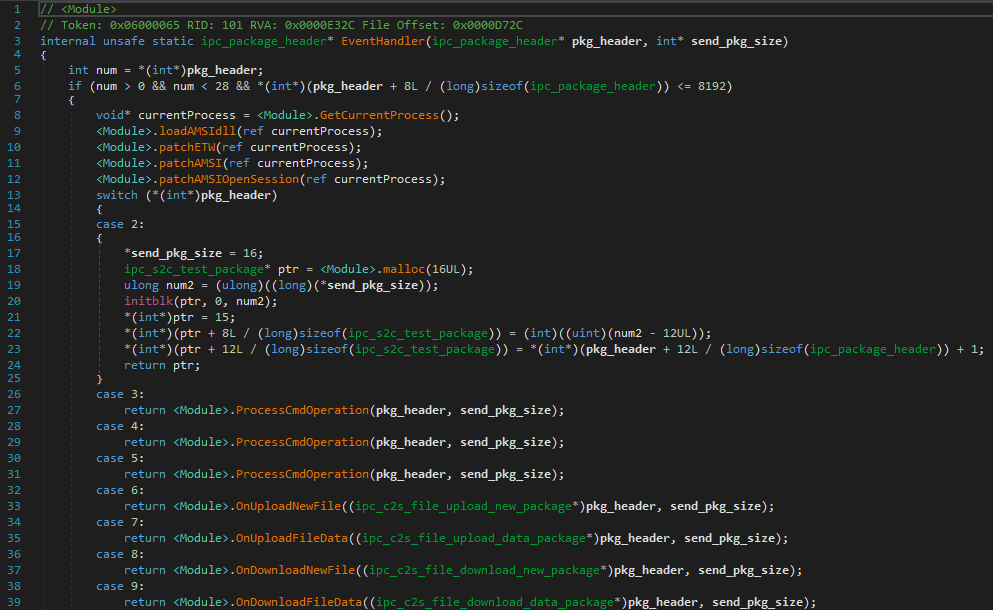
- The first sample is a C++/CLI backdoor as an IIS module with various command execution capabilities.
- The second sample is a bootkit installing a GRUB 2 bootloader, utilizing an insecure kernel driver.
- The third sample is a developing post-exploitation framework named ProjectGeass, showing multi-platform support.
- Palo Alto Networks customers are better protected through Advanced WildFire and Cortex XDR.
- Contact Unit 42 Incident Response for potential malware instances.
MITRE Techniques :
- T1048 – Exfiltration Over Command and Control Channel: The IIS backdoor uses custom encrypted HTTP commands for communication.
- T1218.011 – Signed Binary Proxy Execution: The bootkit installs the GRUB 2 bootloader via a legitimate signed kernel driver.
- T1071 – Application Layer Protocol: Multiple command executions using HTTP requests are processed by the backdoor.
- T1050 – New Service: The bootkit uses scheduled tasks for persistence under the SYSTEM account.
- T1070 – Indicator Removal: The bootkit deletes installed drivers post-setup to hide its presence.
Indicator of Compromise :
- [SHA256] 15db49717a9e9c1e26f5b1745870b028e0133d430ec14d52884cec28ccd3c8ab
- [SHA256] 8571a354b5cdd9ec3735b84fa207e72c7aea1ab82ea2e4ffea1373335b3e88f4
- [SHA256] a28d0550524996ca63f26cb19f4b4d82019a1be24490343e9b916d2750162cda
- [SHA256] 950243a133db44e93b764e03c8d06b99310686d010b52b67f4effa57f0d72e04
- [SHA256] cca5df85920dd2bdaaa2abc152383c9a1391a3e1c4217382a9b0fce5a83d6e0b
Full Story: https://unit42.paloaltonetworks.com/unusual-malware/