Nitrogen via Google ad for Advanced IP Scanner
Nitrogen, tested on May 3, 2024
Malvertising, the use of ads to deliver malware, has become very popular in the past couple of years. This is especially true for ads that appear on search results pages for Google, and to a lesser extent Bing.
The threat we are looking at today lures potential victims (likely system administrators) with an ad for Advanced IP Scanner, a popular networking tool. The malicious download leads to Nitrogen, a piece of malware that is used as initial access for ransomware deployment.
Distribution (Google ad->Phishing site->Download ZIP)
We searched on Google for the keywords ‘advanced ip scanner’ and saw the ad shown below. In this case, the threat actors used minimal effort as the domain name is clearly different than the official site, and the ad contains typos.
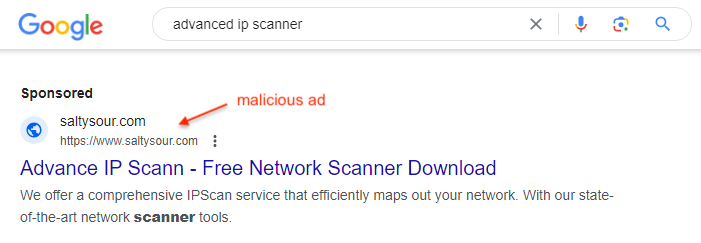
When you click on the ad, you are redirected through the decoy domain seen in the ad URL. This technique is known as cloaking and enables the threat actors to trick Google into thinking the ad is clean. Let’s pretend we are not a real user, by changing some of our browser settings to appear as a crawler. We see a website that looks real, although no one has ever heard about it before!
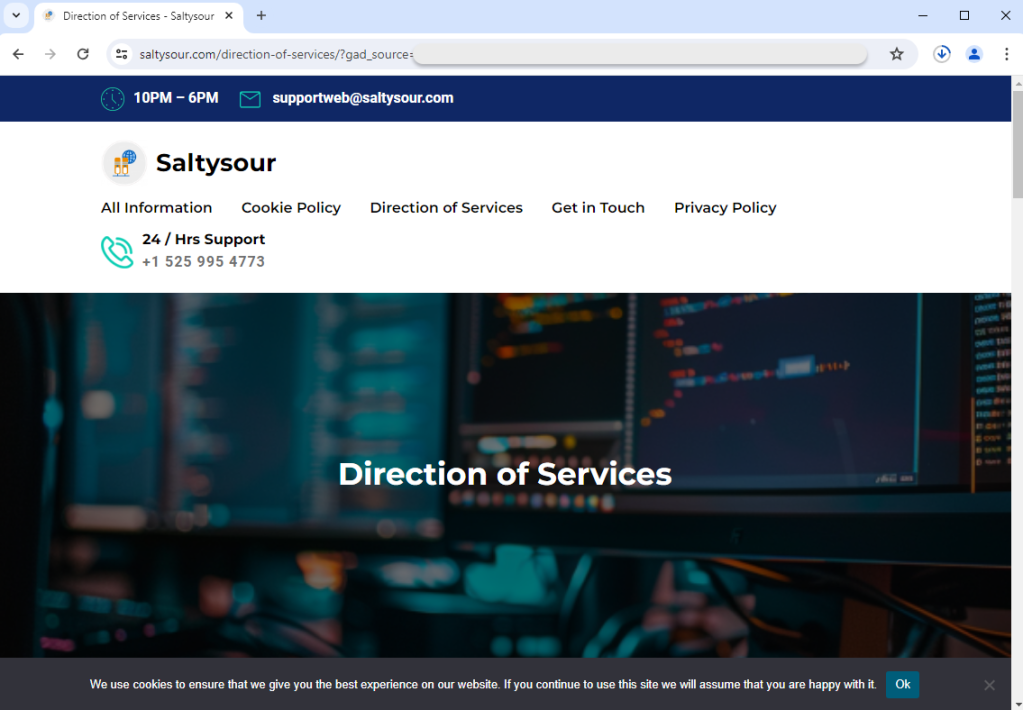
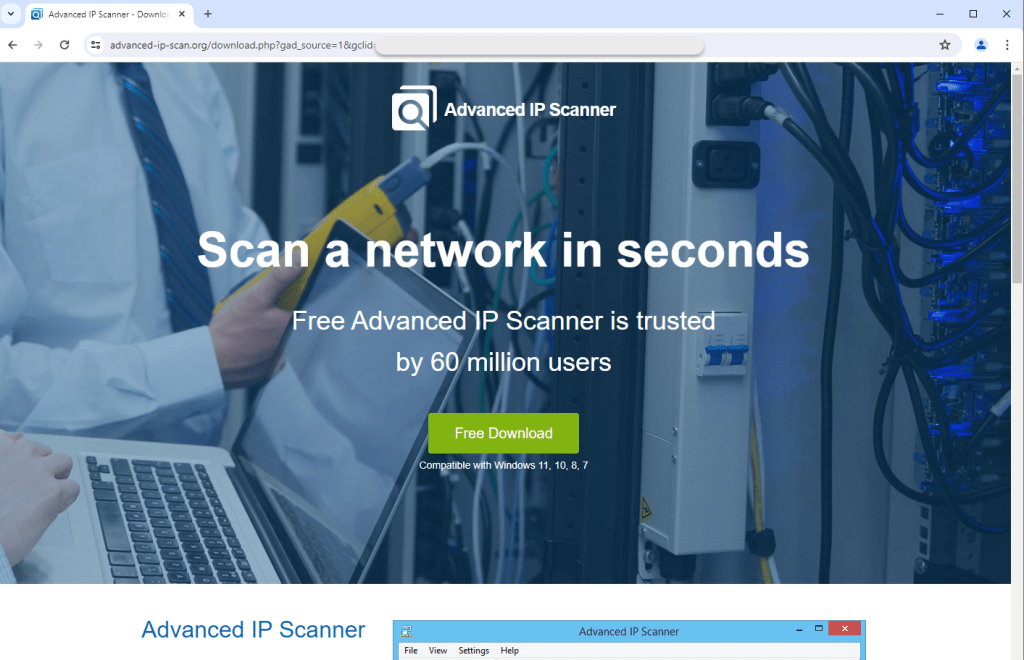
Threat actors go to great lengths to create these decoy pages, but often times they use AI to have them build those sites for them. Now, let’s return to the ad and click on it from a genuine user profile: we get a totally different final URL!
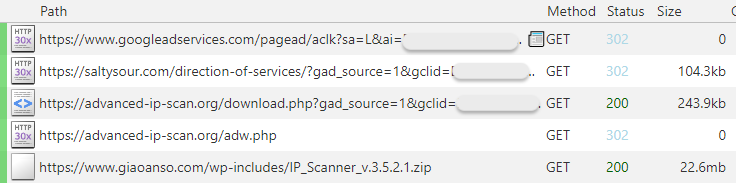
To understand what happened here, let’s look at the network traffic from the Google ad, to this page. We see that the saltysour[.]com domain immediately redirected us (via a 302 HTTP code) to a different site that impersonates the real Advanced IP Scanner website.
Real site: advanced-ip-scanner[.]com
Fake site: advanced-ip-scan[.]org
We press the download button and a file called IP_Scanner_v.3.5.2.1.zip is retrieved from what looks like a WordPress site, which is rather suspicious. We extract the content of that Zip archive and see the following.
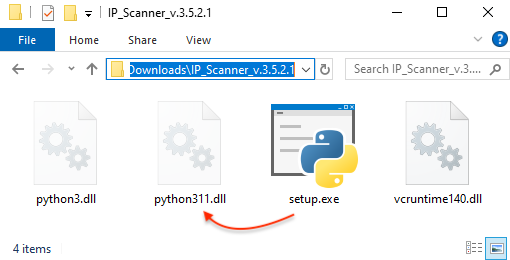
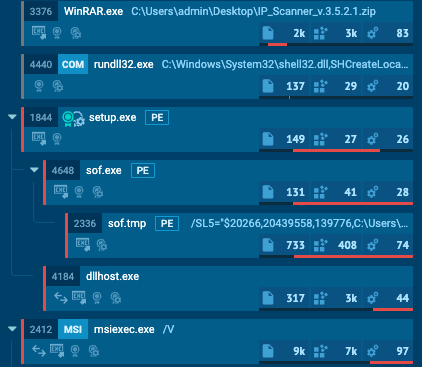
While the setup.exe file is legitimate, it sideloads a malicious DLL (python311.dll) which calls back to a command control and server. This is a signature move from a threat known as Nitrogen. This piece of malware is used as part of a longer attack chain which leads to ransomware. In fact, Nitrogen is associated with the deployment of the BlackCat (ALPHV) ransomware.
Process flow
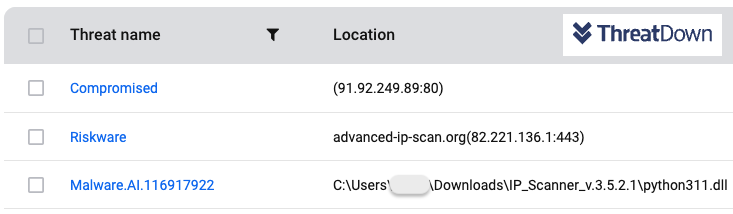
Protection
ThreatDown customers were already protected against this attack:
- The phishing website was detected via web protection
- The malicious DLL (Nitrogen) was detected via our AI-driven automated signature system
- The command and control server (C2) for Nitrogen was already detected by web protection
Mitigations
If you want to protect your users from a number of web based threats, it is crucial to scrutinize online ads. Downloading software by clicking on a search ad is a risky behavior because brands can be impersonated quite easily. You have several options here:
- you can block ads across the board which will make a malvertising attack very unlikely
- you can provide an internal repository from where you employees will download the software programs they need
We highly recommend web protection which goes beyond a simple ad blocker. ThreatDown gives you that extra piece of mind by blocking malicious infrastructure used by malvertisers as well as command and control servers that threat actors rely on.
Remember to treat such intrusions timely as Nitrogen is not the final payload in this attack chain. Threat actors will use it to profile victims before deploying ransomware.
Indicators of Compromise (IOCs)
Cloaking site
saltysour[.]com
Phishing site
advanced-ip-scan[.]org
Payload URL
giaoanso[.]com/wp-includes/IP_Scanner_v.3.5.2.1.zip
Payload SHA256
e2ee4d4798f74639686206770b4782ded7a63e7516602efbf9ef53ce00a8e3f8
Nitrogen SHA256
26c9be484d40491f190b771b3c412a7474f0da719df3ce17e7f057ac9e48e429
Nitrogen C2
91.92.249[.]89
Source: https://www.threatdown.com/blog/nitrogen-05-03-2024/
Views: 1