Short Summary
The criminal group behind Vidar is intensifying its operations in Italy, primarily using PEC mailboxes to conduct attacks. This strategy has proven effective in spreading malware across the country. The CERT-AGID has observed and countered three malicious campaigns from Vidar, with support from PEC managers.
Keypoints
- Vidar group is increasing its operations in Italy.
- PEC mailboxes are the main channel for their attacks.
- This is the third malicious campaign observed by CERT-AGID.
- New tactics include using Steam and Telegram profiles for command and control (C2).
- Indicators of Compromise (IoC) have been shared with PEC managers.
- Users are advised to be cautious with PEC communications, especially suspicious links.
MITRE ATT&CK TTPs – created by AI
- Phishing – T1566
- Utilizing PEC mailboxes to deliver malware.
- Command and Control – T1071
- Using Steam and Telegram for C2 communications.
- Malware – T1203
- Distributing malware through malicious links in emails.
Full Article Translation
26/09/2024
The criminal group behind Vidar is showing strong determination in Italy, intensifying its operations and using PEC mailboxes as the main channel to carry out its attacks. This strategy is proving particularly effective, highlighting an increasing interest in exploiting PECs to spread malware in our country.
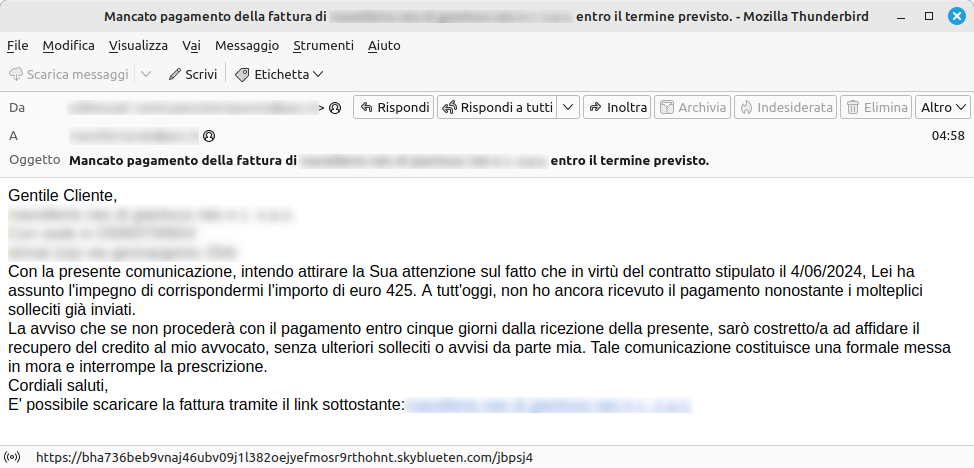
This is the third malicious campaign from Vidar observed and countered by CERT-AGID with the support of PEC managers, who have now become familiar with the template used.
C2 on Steam and Telegram
The analysis of this new campaign revealed a novelty in what seemed to be a well-known behavior: in addition to using profiles on Steam community, already observed in other campaigns, the attackers are also exploiting profiles on Telegram, where the bio is used to report the IP addresses of command and control (C2) servers.
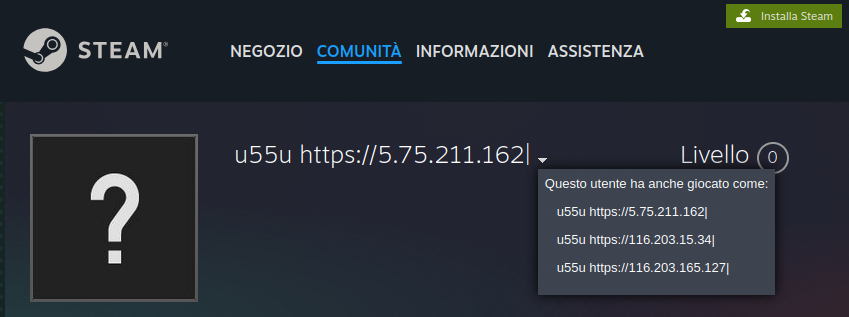
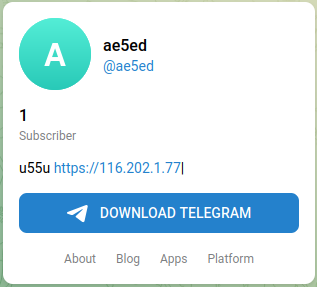
It is interesting to highlight that one of the IP addresses contacted by Vidar is already known to have been used by other malware, as highlighted yesterday in this tweet.
Counteractions
Countermeasures have already been implemented with the support of PEC managers. The IoCs related to the campaign have been disseminated through the CERT-AGID IoC Feed to PEC managers and accredited structures.
It is recommended to always pay maximum attention to communications received via PEC, especially when they contain links deemed suspicious. In case of doubt, it is always possible to forward suspicious emails to the email address malware@cert-agid.gov.it.
Indicators of Compromise
In order to make the details of today’s campaign public, the detected IoCs are reported below:
Link: Download IoC
Source: Original Post