### #PhishingAsAService #AiTMattacks #CredentialTheft
Summary: A new phishing-as-a-service platform, ‘Rockstar 2FA,’ has emerged, enabling large-scale adversary-in-the-middle attacks to steal Microsoft 365 credentials by bypassing multifactor authentication. This service, which has gained traction in the cybercrime community, offers various features to facilitate phishing operations.
Threat Actor: Cybercriminals | Rockstar 2FA
Victim: Microsoft 365 users | Microsoft 365
Key Point :
- Rockstar 2FA allows attackers to intercept valid session cookies, enabling access to accounts even with MFA enabled.
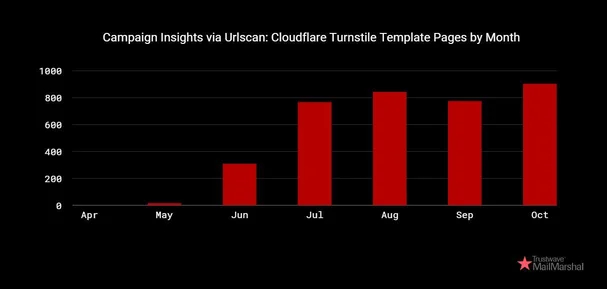
- The platform has gained popularity since August 2024, with over 5,000 phishing domains set up to facilitate operations.
- Phishing campaigns utilize legitimate email marketing platforms and various lures, including document-sharing notifications and password reset alerts.
- Advanced evasion techniques are employed, such as Cloudflare Turnstile challenges to filter out bots and redirect them to decoy pages.
- The persistence of such platforms highlights the ongoing risk of large-scale phishing operations despite law enforcement efforts against similar services.

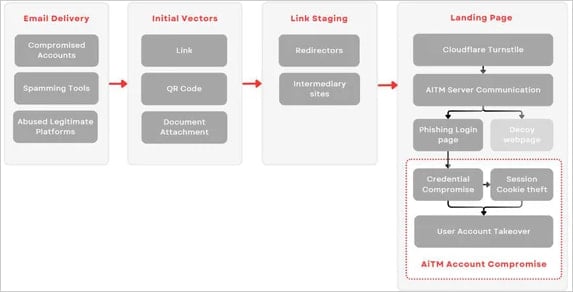
A new phishing-as-a-service (PhaaS) platform named ‘Rockstar 2FA’ has emerged, facilitating large-scale adversary-in-the-middle (AiTM) attacks to steal Microsoft 365 credentials.
Like other AiTM platforms, Rockstar 2FA enables attackers to bypass multifactor authentication (MFA) protections on targeted accounts by intercepting valid session cookies.
These attacks work by directing victims to a fake login page that mimics Microsoft 365 and tricking them into entering their credentials.
The AiTM server acts as a proxy, forwarding those credentials to Microsoft’s legitimate service to complete the authentication process and then captures the cookie when it is sent back to the target’s browser.
This cookie can then be used by the threat actors for direct access to the victim’s account, even if it’s MFA protected, with the threat actor not needing the credentials at all.
Source: Trustwave
Rise of Rockstar 2FA
Trustwave reports that Rockstar 2FA is actually an updated version of the phishing kits DadSec and Phoenix, which gained traction in early and late 2023 respectively.
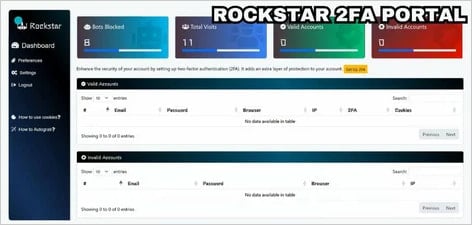
The researchers say Rockstar 2FA has gained significant popularity in the cybercrime community since August 2024, selling for $200 for two weeks or $180 for API access renewal.
Source: Trustwave
The service is promoted on Telegram, among other places, boasting a long list of features like:
- Support for Microsoft 365, Hotmail, Godaddy, SSO
- Randomized source code and links to evade detection
- Cloudflare Turnstile Captcha integration for victim screening
- Automated FUD attachments and links
- User-friendly admin panel with real-time logs and backup options
- Multiple login page themes with automatic organization branding (logo, background)
The service has set up over 5,000 phishing domains since May 2024, facilitating various phishing operations.
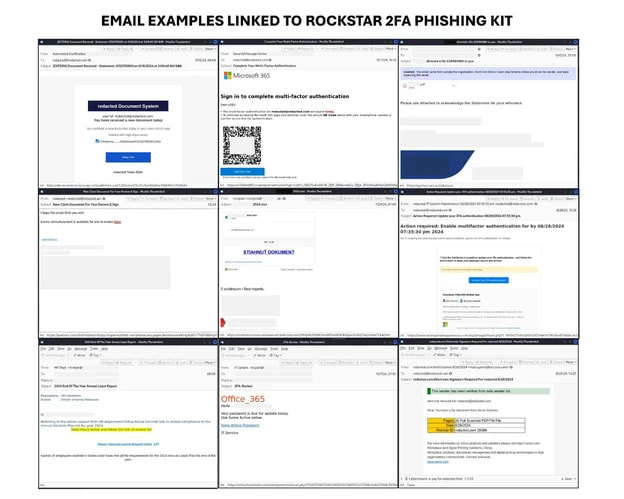
The researchers say that the related phishing campaigns they observed abuse legitimate email marketing platforms or compromised accounts for disseminating malicious messages to targets.
The messages use a variety of lures, including document-sharing notifications, IT department notices, password reset alerts, and payroll-related messages.
Trustwave says these messages utilize a range of block evasion methods including QR codes, inclusion of links from legitimate shortening services, and PDF attachments.
Source: Trustwave
A Cloudflare turnstile challenge is used to filter out bots, while the attack also likely includes IP checks before valid targets are directed to a Microsoft 365 login phishing page.
Source: Turstwave
If the visitor is deemed a bot, security researcher, or an out-of-scope target in general, they are redirected to a harmless car-themed decoy page instead.
The JavaScript on the landing page decrypts and retrieves either the phishing page or the car-themed decoy based on the AiTM server’s evaluation of the visitor.
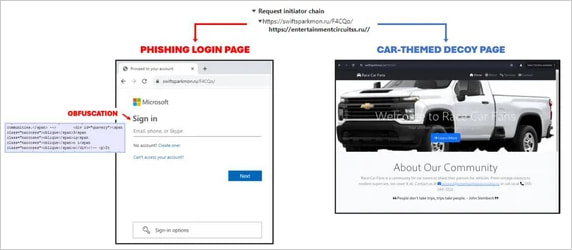
Source: Trustwave
The emergence and proliferation of Rockstar 2FA reflect the persistence of phishing operators, who continue to offer illicit services despite significant law enforcement operations taking down one of the largest PhaaS platforms recently and arresting its operators.
As long as these commodity tools continue to be accessible for cybercriminals at a low cost, the risk of large-scale effective phishing operations remains significant.