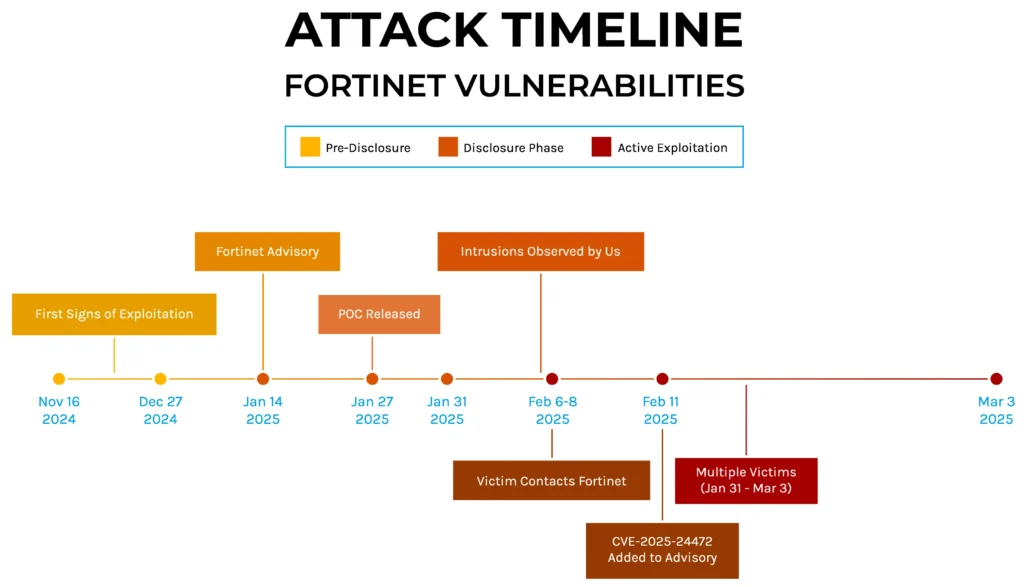
Forescout Research has identified a new ransomware strain, dubbed SuperBlack, linked to the threat actor “Mora_001”, exploiting vulnerabilities in Fortinet devices. This threat actor is connected to the LockBit ransomware ecosystem and demonstrates sophisticated tactics including rapid ransomware deployment, user account creation across victim networks, and the use of modified LockBit tools. The complexity of modern ransomware operations is emphasized by the collaboration between specialized teams. Affected: Fortinet devices, ransomware operations, organizations in cybersecurity sector.
Keypoints :
- Forescout Research identified a series of intrusions linked to vulnerabilities in Fortinet firewall devices.
- New ransomware strain named SuperBlack deployed by threat actor Mora_001.
- Mora_001 shows ties to the LockBit ransomware ecosystem while exhibiting unique operational patterns.
- Exploitation of CVE-2024-55591 and CVE-2025-24472 vulnerabilities allows attackers to gain unauthorized privileges on FortiOS devices.
- Unique techniques include rapid ransomware deployment and automated account creation to evade detection.
- Threat actor employs advanced methods for data exfiltration before encrypting sensitive files.
- Secure management practices are strongly recommended to mitigate risks associated with Fortinet devices.
MITRE Techniques :
- Exploit Public-Facing Application (T1190) – Exploiting CVE-2024-55591 and CVE-2025-24472 to gain super_admin privileges on FortiOS devices.
- Privilege Escalation (T1068) – Attaining elevated privileges through administrative access to vulnerable FortiGate firewalls.
- Create Account: Local Account (T1136) – Creating unauthorized admin accounts such as forticloud-tech and fortigate-firewall during post-exploitation.
- Data from Configuration Repository (T1003) – Downloading critical firewall configuration files containing sensitive data.
- Scheduled Task/Job (T1053) – Implementing automation scripts to recreate compromised accounts daily.
- Lateral Movement (T1075) – Using compromised user accounts to gain access to additional devices and networks.
- Ransomware (T1486) – Selectively encrypting files after data exfiltration to maximize disruption and extort victims.
Indicator of Compromise :
- [IP Address] 13.73.13.73
- [IP Address] 8.8.8.8
- [IP Address] 185.147.124[.]34
- [File Hash] c994b132b2a264b8cf1d47b2f432fe6bda631b994ec7dcddf5650113f4a5a404
- [File Hash] 917e115cc403e29b4388e0d175cbfac3e7e40ca1742299fbdb353847db2de7c2
Full Story: https://www.forescout.com/blog/new-ransomware-operator-exploits-fortinet-vulnerability-duo/