Summary: Checkmarx researchers have identified a series of malicious packages on the Python Package Index (PyPI) that masquerade as crypto wallet tools, designed to steal sensitive information from users. These packages specifically target popular cryptocurrency wallets, including Metamask and Trust Wallet, by exploiting supply chain vulnerabilities.
Threat Actor: Unknown | unknown
Victim: Cryptocurrency users | cryptocurrency users
Key Point :
- Malicious packages uploaded to PyPI included fake README files to enhance credibility.
- Attackers used obfuscated code and distributed functionality across multiple dependencies to evade detection.
- The malware activates only when users attempt to use specific features, allowing it to steal private keys and recovery phrases.
- Once stolen, the information is sent to a server controlled by the attackers, leading to irreversible financial losses for victims.
- Users are advised to exercise caution when downloading packages related to cryptocurrency services from PyPI.
Checkmarx researchers discovered PyPI malware posing as crypto wallet tools. These malicious packages stole private keys and recovery phrases, targeting wallets like Metamask, Trust Wallet, and Exodus.
The cybersecurity researchers at Checkmarx uncovered a series of new supply chain attacks that exploited the Python Package Index (PyPI) in September 2024 using malicious packages to target cryptocurrency wallets.
The attack involved a new user on the platform who uploaded several malicious packages designed to steal sensitive wallet data, including private keys and mnemonic phrases. These packages identified as “AtomicDecoderss,” “TrustDecoderss,” “WalletDecoderss,” and “ExodusDecodes,” targeted cryptocurrency wallets including Atomic, Trust Wallet, Metamask, Ronin, TronLink, and Exodus.
According to the Checkmarx report shared with Hackread.com ahead of publishing on Tuesday, each package came with a professionally written README file, complete with installation instructions, usage examples, and even “best practices” for virtual environments.
Even more concerning, these documents included fake statistics, making the packages seem like well-maintained and popular projects, thus increasing their credibility and download count.
One of the key tactics used by the attacker was the distribution of functionality across multiple dependencies. Six of the malicious packages relied on a dependency called “cipherbcryptors,” which contained the core malicious code. In the context of a cyberattack, dependencies refer to any external components, systems, software, or third-party services that an organization relies upon to function properly.
Further analysis revealed that threat actors heavily obfuscated the code within the “cipherbcryptors” package, making it difficult for automated security tools and cybersecurity researchers to identify its malicious intent.
Unlike others, these malicious packages didn’t start infecting the device immediately upon installation. Instead, they remained inactive until the user attempted to use certain features. Once the user began using one of the features advertised by the threat actors, the malware would activate and access the targeted user’s cryptocurrency wallet.
It then stole important information, such as private keys and recovery phrases, which are needed to control and access cryptocurrency wallets. The stolen information was then encoded and sent to a server controlled by the attacker.
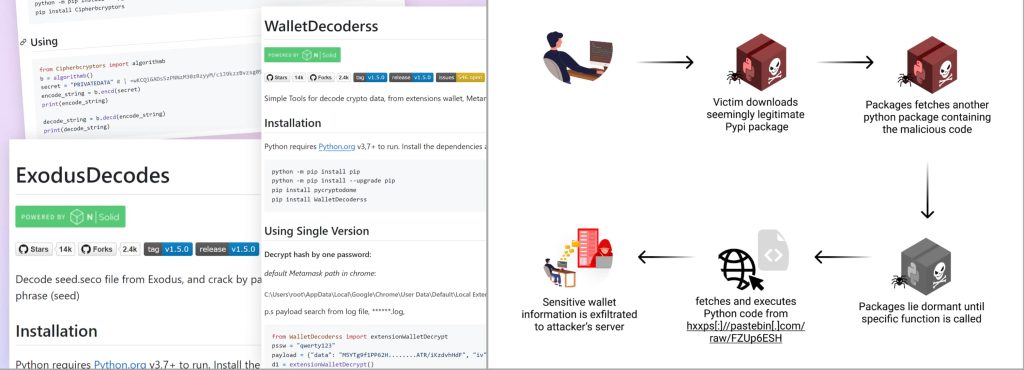
The impact of this type of supply chain attack can be severe for the victims. With access to private keys and recovery phrases, attackers can quickly drain cryptocurrency wallets. Due to the irreversible nature of blockchain transactions, once funds are stolen, recovering them is nearly impossible.
Therefore, software developers and unsuspecting users should be cautious of such attacks, especially when downloading packages from the PyPI platform, particularly those that offer cryptocurrency-related services and include access to wallets. Cybersecurity training for employees is also important in defending against these attacks, making protection a matter of common sense.
RELATED TOPICS
- OpenSSF Launches Malicious Packages Repository
- Crypto Stealing PyPI Malware Hits Both Windows, Linux Users
- PyPI Suspends New Projects, Users Due to Malicious Packages
- Hackers Exploit PyPI to Infiltrate Systems with Python Packages
- Luna Grabber Malware Hits Roblox Devs Through npm Packages
Source: https://hackread.com/pypi-malware-crypto-wallet-tools-steal-private-keys