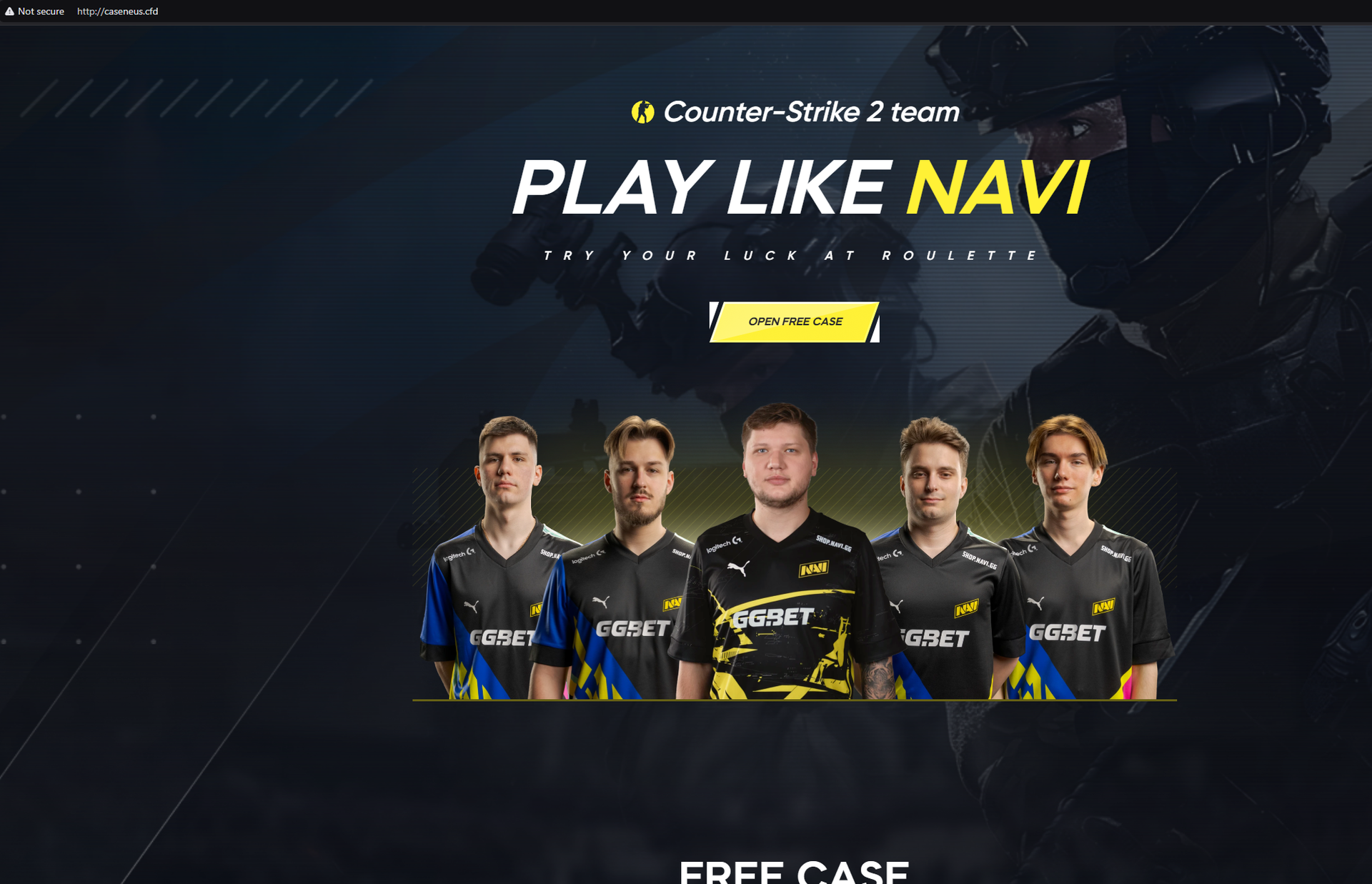
A new phishing campaign targets Counter-Strike 2 players through complex browser-in-the-browser (BitB) phishing attacks using fake pop-up windows that impersonate legitimate sites. The campaign aims to steal Steam credentials, especially affecting fans of the esports team Navi, with potential resale of compromised accounts on various platforms. Affected: Steam, Counter-Strike 2, Gaming sector, eSports
Keypoints :
- Silent Push analysts discovered a phishing campaign specifically targeting Counter-Strike 2 players.
- Phishing tactics involve browser-in-the-browser (BitB) attacks that use fake pop-up windows.
- The threat actors aim to steal and resell Steam accounts.
- Most scam websites were in English, with only one in Mandarin.
- The professional eSports team Navi is used as a lure in the attacks.
- Phishing domains and techniques used by the threat actor have been made public to assist researchers and the gaming community.
MITRE Techniques :
- Phishing (T1566): The threat actor uses fake browsers and pop-up windows to trick victims into entering their credentials for the Steam platform.
- Credential Dumping (T1003): Acquired Steam credentials are likely harvested for resale on illicit marketplaces.
Indicator of Compromise :
- [Domain] steampowered[.]com
- [Domain] simplegive[.]cn
- [Domain] caseneus[.]cfd
- [Domain] caserevs[.]com
- [IP Address] 77.105.161[.]50
Full Story: https://www.silentpush.com/blog/browser-in-the-browser-attacks/