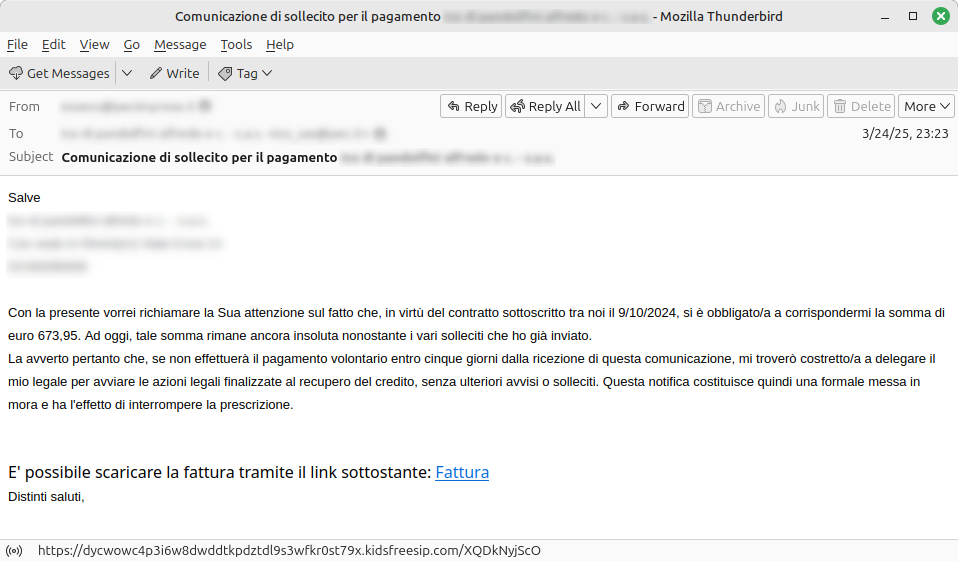
A new malicious campaign has been detected, targeting users of certified email (PEC) accounts. The attackers exploit the perceived reliability of these communications to enhance their success rate. The malware used has shifted from Vidar to AsyncRat, a remote access trojan (RAT), indicating a potential escalation in the attack’s objectives. Affected: PEC email users, cybersecurity sector
Keypoints :
- A new malicious campaign exploits compromised PEC email accounts.
- The campaign targets only PEC account holders, banking on the trust associated with these emails.
- The malware has transitioned from Vidar to AsyncRat, suggesting an evolution in attack methodology.
- AsyncRat allows for extended remote control over infected systems.
- MintsLoader, a known loader in Italy, is utilized for this campaign, featuring unique URL parameters for infection.
- The campaign employs a multi-stage infection process through various URLs and domains.
- Domains leverage a Domain Generation Algorithm (DGA) and frequently use the .top extension to evade preventive blocking.
- Countermeasures are in place, with IoCs disseminated through CERT-AGID to PEC managers and accredited entities.
- Users are advised to be vigilant with PEC communications, especially regarding suspicious links.
- Suspected emails can be forwarded to malware@cert-agid.gov.it for review.
MITRE Techniques :
- TA0001 – Initial Access: Phishing via compromised PEC emails to deliver malware payloads.
- TA0002 – Execution: Javascript and PowerShell are used to execute the MintsLoader and AsyncRat malware.
- TA0003 – Persistence: Use of AsyncRat to maintain control over infected systems.
- TA0011 – Command and Control: Utilization of domains generated through DGA to communicate with compromised systems.
- TA0040 – Impact: Data exfiltration through AsyncRat, which allows attackers to steal sensitive information remotely.
Indicator of Compromise :
- [URL] http://malicious.com/1.php?s=flibabc13
- [Domain] mintsXX.top (where XX represents variable numbers)
- [Domain] s=boicn.top
- [Email Address] malware@cert-agid.gov.it
- [Filename] sp0E9P1GcKZSuRTEsx.png (example filename format)
Full Story: https://cert-agid.gov.it/news/nuova-ondata-malevola-via-pec-mintsloader-ora-distribuisce-asyncrat/