Malware loaders (also known as droppers or downloaders) are a popular commodity in the criminal underground. Their primary function is to successfully compromise a machine and deploy one or multiple additional payloads.
A good loader avoids detection and identifies victims as legitimate (i.e. not sandboxes) before pushing other malware. This part is quite critical as the value of a loader is directly tied to the satisfaction of its “customers”.
In this blog post, we describe a malvertising campaign with a loader that was new to us. The program is written in the Go language and uses an interesting technique to deploy its follow-up payload, the Rhadamanthys stealer.
Malicious ad targets system administrators
PuTTY is a very popular SSH and Telnet client for Windows that has been used by IT admins for years. The threat actor bought an ad that claims to be the PuTTY homepage and appeared at the top of the Google search results page, right before the official website.
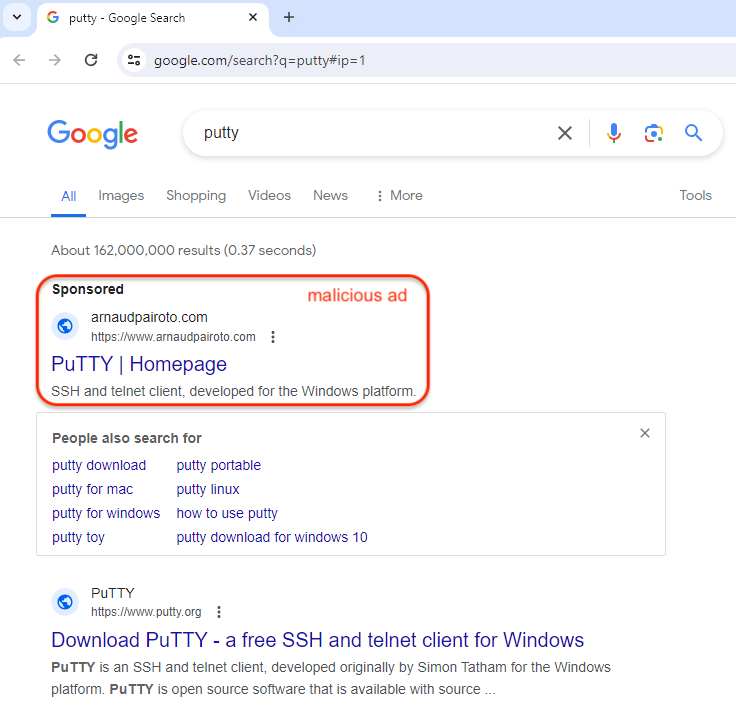
In this example, the ad looks suspicious simply because the ad snippet shows a domain name (arnaudpairoto[.]com) that is completely unrelated. This is not always the case, and we continue to see many malicious ads that exactly match the impersonated brand.
Fake PuTTY site
The ad URL points to the attacker controlled domain where they can easily defeat security checks by showing a “legitimate” page to visitors that are not real victims. For example, a crawler, sandbox or scanner, will see this half finished blog:

Real victims coming from the US will be redirected to a fake site instead that looks and feels exactly like putty.org. One of the big differences though is the download link.
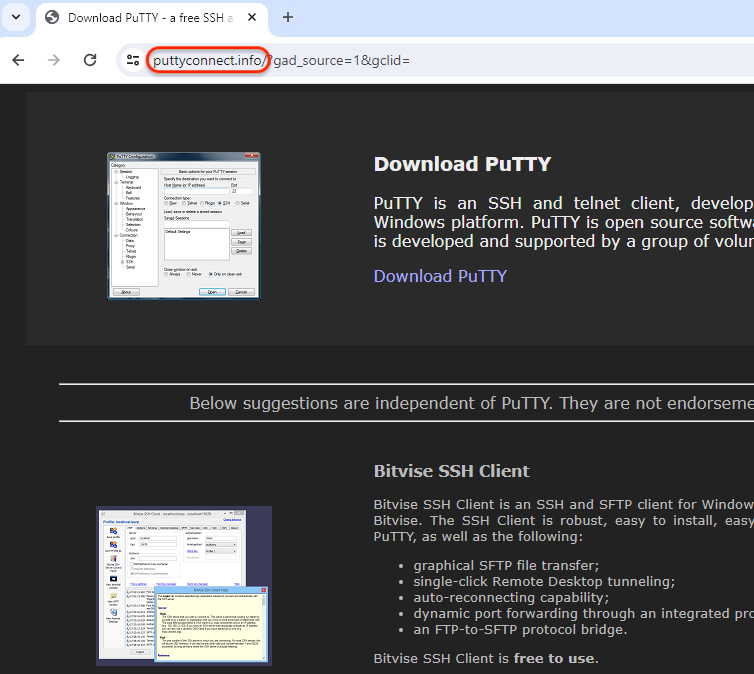
The malicious payload is downloaded via a 2 step redirection chain which is something we don’t always see.
puttyconnect[.]info/1.php HTTP/1.1 302 Found Location: astrosphere[.]world/onserver3.php
astrosphere[.]world/onserver3.php HTTP/1.1 200 OK Server: nginx/1.24.0 Content-Type: application/octet-stream Content-Length: 13198274 Connection: keep-alive Content-Description: File Transfer Content-Disposition: attachment; filename="PuTTy.exe"
We believe the astrosphere[.]world server is performing some checks for proxies while also logging the victim’s IP address. This IP address will later be checked before downloading the secondary payload.
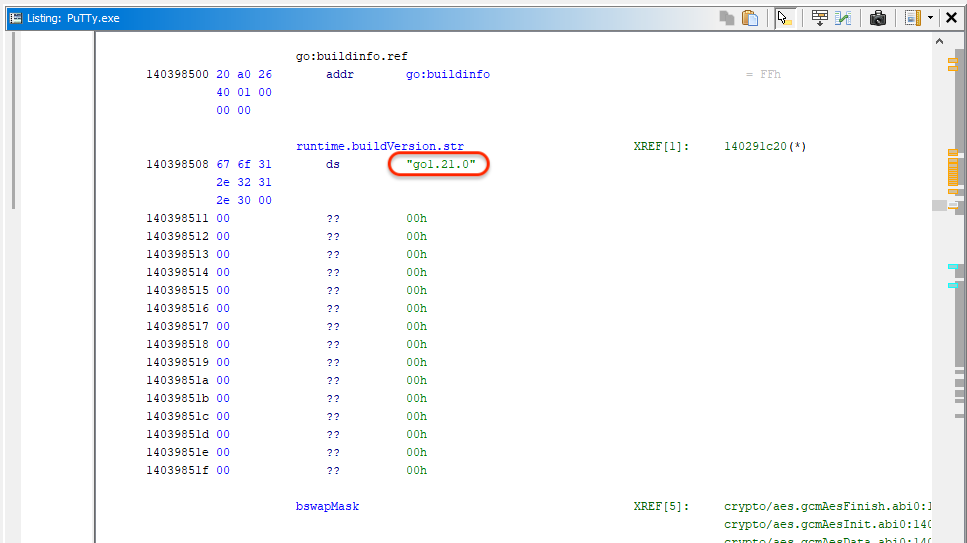
That PuTTy.exe is malware, a dropper written in the Go language (version 1.21.0).
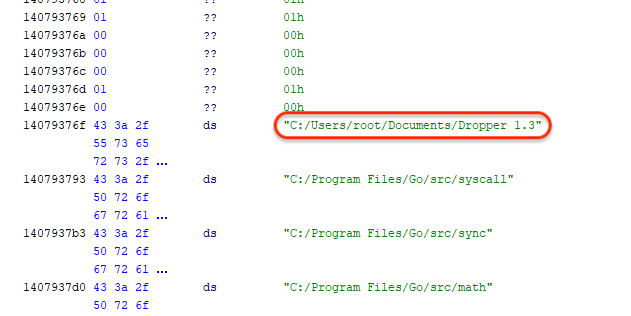
Its author may have given it the name “Dropper 1.3“:
Follow-up payload
Upon executing the dropper, there is an IP check for the victim’s public IP address. This is likely done to only continue with users that have gone through the malicious ad and downloaded the malware from the fake site.
zodiacrealm[.]info/api.php?action=check_ip&ip=[IP Address]
If a match is found, the dropper proceeds to retrieve a follow-up payload from another server (192.121.16[.]228:22) as seen in the image below:
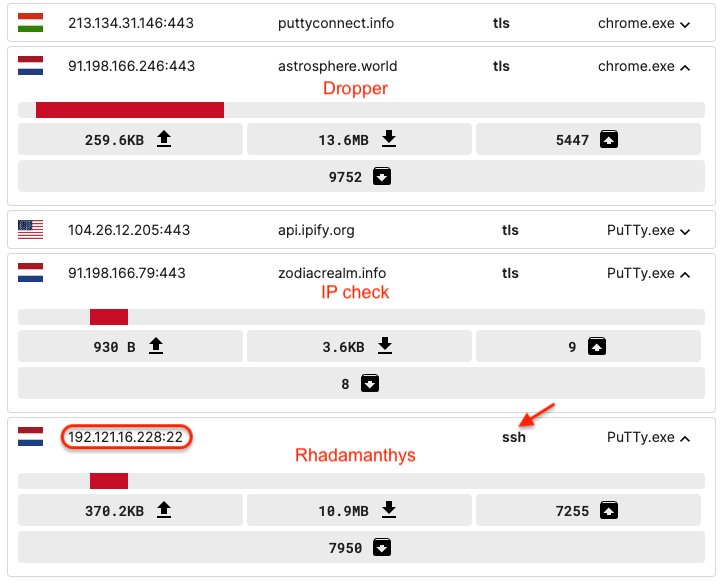
To get this data, we see it uses the SSHv2 (Secure Shell 2.0) protocol implemented via OpenSSH on a Ubuntu server. We can only think of using this protocol to make the malware download more covert.
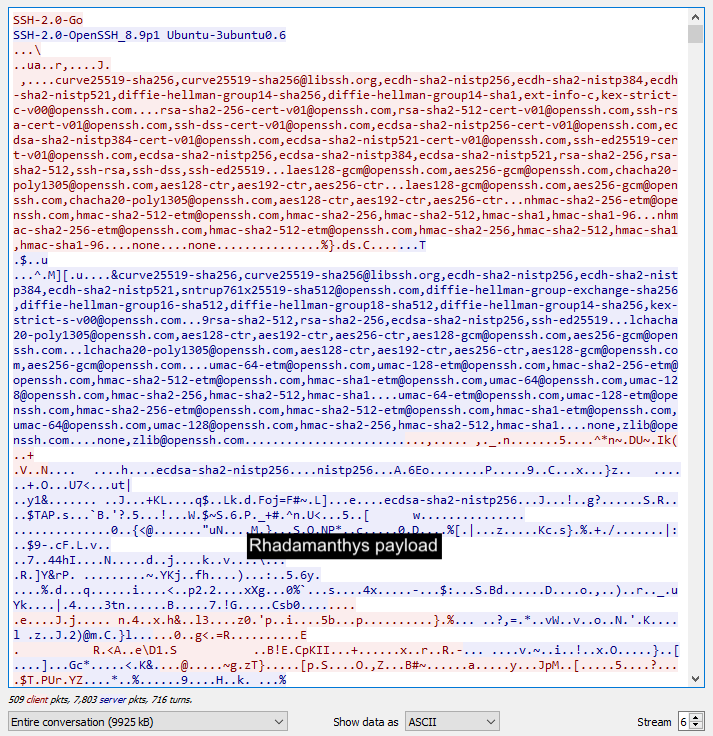
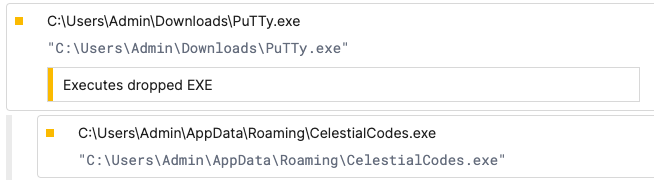
That payload is Rhadamanthys which is executed by the parent process PuTTy.exe:
Malvertising / loader combo
We have seen different types of loaders via malvertising campaigns, including FakeBat which we profiled recently. Given how closely the loader is tied to the malvertising infrastructure it is quite likely that the same threat actor is controlling both. The service they offer to other criminals is one of malware delivery where they take care of the entire deployment process, from ad to loader to final payload.
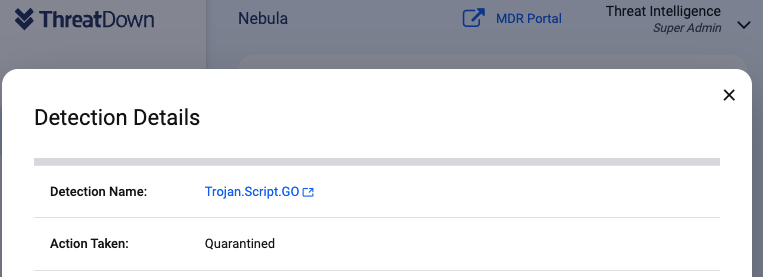
We reported this campaign to Google. Malwarebytes and ThreatDown users are protected as we detect the fake PuTTY installer as Trojan.Script.GO.
ThreatDown users that have DNS Filtering can enable ad blocking in their console to prevent attacks that originate from malicious ads.
Indicators of Compromise
Decoy ad domain
arnaudpairoto[.]com
Fake site
puttyconnect[.]info
PuTTY
astrosphere[.]world 0caa772186814dbf84856293f102c7538980bcd31b70c1836be236e9fa05c48d
IP check
zodiacrealm[.]info
Rhadamanthys
192.121.16[.]228:22 bea1d58d168b267c27b1028b47bd6ad19e249630abb7c03cfffede8568749203
Source: https://www.malwarebytes.com/blog/threat-intelligence/2024/03/new-go-loader-pushes-rhadamanthys
MITRE TTP :
- Technique: Drive-by Compromise (T1189)
- Procedure: The attacker sets up a malicious ad that appears at the top of Google search results, redirecting unsuspecting users to a fake website.
- Technique: Spearphishing Link (T1566.002)
- Procedure: The malicious ad mimics a legitimate website, such as the PuTTY homepage, to trick users into downloading a fake installer.
- Technique: User Execution (T1204)
- Procedure: The user is deceived into executing the fake installer, which is actually a dropper for the malware.
- Technique: Command and Scripting Interpreter: PowerShell (T1059.001)
- Procedure: The dropper uses PowerShell to download and execute the secondary payload, such as the Rhadamanthys stealer.
- Technique: Obfuscated Files or Information (T1027)
- Procedure: The dropper is written in the Go language and uses obfuscation techniques to avoid detection.
- Technique: Masquerading (T1036)
- Procedure: The dropper masquerades as a legitimate PuTTY installer to avoid arousing suspicion.
- Technique: Steal Web Session Cookie (T1539)
- Procedure: The Rhadamanthys stealer is designed to steal web session cookies and other sensitive information from the victim’s machine.
- Technique: Remote System Discovery (T1018)
- Procedure: The malware may perform remote system discovery to identify other potential targets within the network.
- Technique: Application Layer Protocol (T1071)
- Procedure: The dropper uses the SSHv2 protocol to download the secondary payload in a more covert manner.
- Technique: Exfiltration Over C2 Channel (T1041)
- Procedure: The stolen data, including session cookies, is exfiltrated over a command and control (C2) channel to the attacker’s server.
- Technique: Data Destruction (T1485)
- Procedure: In some cases, the malware may also be capable of destroying data on the victim’s machine as part of its payload.
Views: 1