Summary: The ransomware threat landscape has intensified, particularly affecting healthcare institutions, with a notable increase in coordinated attacks by nation-states and cybercriminals. Despite the rise in encounters, the percentage of attacks resulting in encryption has decreased, indicating some progress in countering these threats.
Threat Actor: BlackCat, LockBit | BlackCat, LockBit
Victim: Church of Sweden | Church of Sweden
Key Point :
- 389 U.S.-based healthcare institutions were attacked in the last fiscal year, leading to significant operational disruptions.
- Nation-states like Russia, North Korea, and Iran are increasingly using ransomware for financial gain, marking a shift in their cyber strategies.
- The most common initial access methods for ransomware attacks include social engineering techniques such as phishing.
- Microsoft’s collaborative platform, “Crystal Ball,” aims to enhance international cooperation in combating ransomware threats.
- Law enforcement has made strides in dismantling ransomware infrastructures, particularly targeting groups like LockBit and BlackCat.
The scale of the ransomware problem has grown significantly over the last year, with hundreds of healthcare institutions attacked in the last 12 months, Microsoft reported Tuesday.
In the last fiscal year, 389 U.S.-based healthcare institutions were successfully hit with ransomware, causing “network closures, systems offline, critical medical operations delayed, and appointments rescheduled,” Microsoft said in its annual Digital Defense Report released on Tuesday. The company did not say how many were successfully attacked last year.
The 114-page report assessed cyber trends between July 2023 and June 2024 based on the company’s access to troves of intelligence.
The company’s researchers found that nation-states and cybercriminals have been coordinating their activity to a greater degree than ever before.
They warned that Russia, North Korea and Iran are now deploying ransomware as a way to gain financially from their offensive cyber operations.
“This marks a change from previous behavior, whereby ransomware attacks that were designed to appear financially motivated were actually destructive attacks,” the researchers said.
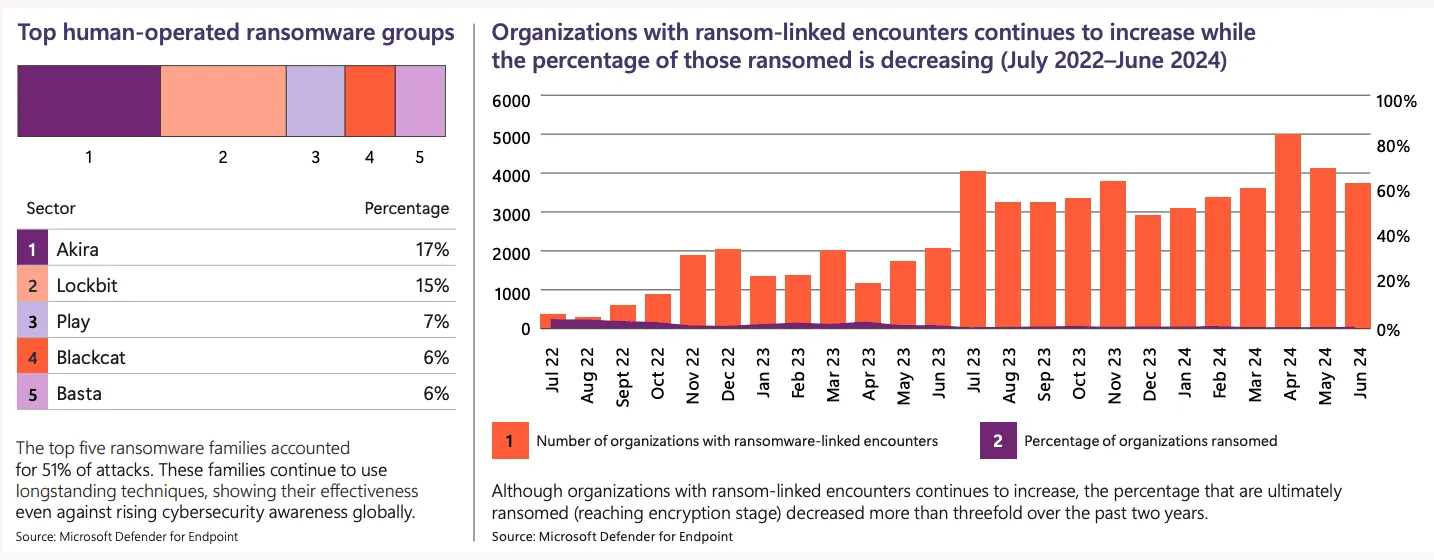
Overall, among Microsoft customers they found a 2.75x increase in human-operated ransomware-linked encounters — which are defined as having at least one device targeted in a network.
But the report did have some good ransomware news. The percentage of ransomware attacks that reached the stage of encryption — where devices are locked — has decreased significantly over the last two years.
In the cases where devices were encrypted and a ransom was issued, the attackers “had leveraged unmanaged devices in the network, either to gain initial access or to remotely encrypt assets at the impact stage.”
For years, experts have warned about the expansion of internet-of-things (IoT) devices and tools brought into work environments by employees that are not approved by IT departments, exposing organizations to increased risk.
“The most prevalent initial access techniques continue to be social engineering — specifically email phishing, SMS phishing, and voice phishing — but also identity compromise and exploiting vulnerabilities in public facing applications or unpatched operating systems,” said Tom Burt, Microsoft corporate vice president of customer security & trust.
Crystal Ball
As an example of the damage caused by ransomware attacks, Microsoft detailed the situation of the Church of Sweden, which was attacked by the now-defunct BlackCat ransomware gang in November 2023.
It took the church two months to recover from the attack and damaged its ability to fundraise during the Christmas season, hold funerals and serve its 5.4 million members.
The church’s data was sold to the LockBit ransomware gang, which published it after church officials refused to pay.
The top groups Microsoft tracked are Akira, which accounted for 17% of all attacks, and LockBit, which took credit for 15% of incidents. Play, BlackCat and Basta rounded out the rest of the list.
Credit: Microsoft
Microsoft noted that law enforcement was making progress in addressing ransomware, taking down infrastructure used by LockBit and BlackCat in the last year. The company added that it is “aggressively pursuing our ability to share information as authorized by law and policy to combat the most significant threats to our customers and our business.”
It touted a collaborative threat intelligence platform called “Crystal Ball” that was built alongside the Israel National Cyber Directorate and the Cyber Security Council of the United Arab Emirates.
The tool is used by the more than 10 members of the International Counter Ransomware initiative (CRI) and provides each country with threat intelligence, attribution guides, deterrence manuals and ways nations can better collaborate. Microsoft said it hopes to onboard the rest of the CRI by the end of the year.
Recorded Future
Intelligence Cloud.
Source: https://therecord.media/ransomware-healthcare-microsoft-last-year