For each of these domains, the sample tries to connect to many of its subdomains. Most subdomains will start with the letter x, w, or m, followed by a number. In this sample, the first hardcoded domain is fywkuzp[.]ru:7432, and we could observe a infected machine trying to connect to the following domains:
In the end, Mylobot produces thousands of DNS requests, which makes it quite noisy. If the sample successfully connects to one of those domains, it keeps the connection open and waits for an instruction from the command and control server (C2).
When Mylobot receives an instruction from the C2, it transforms the infected computer into a proxy. The infected machine will be able to handle many connections and relay traffic sent through the command and control server.
Message ID (msg_id) | Description |
1 | Connect to an IP:port |
2 | Close connection (specified by its ID (data[0:4]) |
3 | Send data to a connected IP/domain:port (specified by its ID (data[0:4]) |
4 | Restart the client networking stuff |
5 | End all active connections |
6 | Echo |
7 | Download a binary using HTTP |
8 | Download multiple binaries using HTTP + delay (8 hours) |
17 | Connect to an domain:port |
19 | Force re-read from socket (specified by its ID) |
A typical message exchanged between the C2 and the client has the following structure:
struct msg
{
uint32_t conn_id;
uint8_t msg_id;
char* msg_data;
}
The figure below shows an example of a C2 instruction telling the infected machine to connect to google.com on port 443.
Lumen that, at that time, infected computers were receiving samples of Khalesi or Zusy malwares using the msg_id 7 and 8. We only observed self binary updates through those commands, as well as new versions of its downloader (see section below).
Since the samples we found contain many hardcoded domain names, we started to monitor them to get infection telemetry and get an idea about the botnet size.
In the end, Mylobot is nothing more than a proxy bot, with some ability to download and run other samples. The sample that is implementing the proxy functionality will be referred to as “Mylobot’s proxy bot” in the rest of this post.
A new downloader (2018 – )
In 2018, we started seeing Mylobot’s proxy bot being distributed by a new malware sample.
This new binary presents a lot of similarities with Mylobot, but the last stage acts as a downloader. Let’s begin by exposing the similarities between this new sample and Mylobot’s proxy bot sample, and describe how it is downloading Mylobot on an infected system.
The first thing to note is that the new sample uses WillExec, the same dropper used for Mylobot samples. The dropped file performs anti virtual machine checks, and tries to remove other malware running on the system as well, after that, it connects to its command and control, and downloads the next stages. This sample has been well described by Minerva, so we won’t go into too much detail.
The downloader has a huge list of hard-coded encrypted command and control domains (more than 1000).

Figure 6 – Hardcoded encrypted domain names
Those domains are AES-ECB encrypted with the key GD!brWJJBeTgTGSgEFB/quRcfCkBHWgl, and have probably been generated using the same DGA mentioned in the first part of this post. Indeed, there’s a strong similarity between Mylobot downloader’s domain names and Mylobot proxy’s ones.
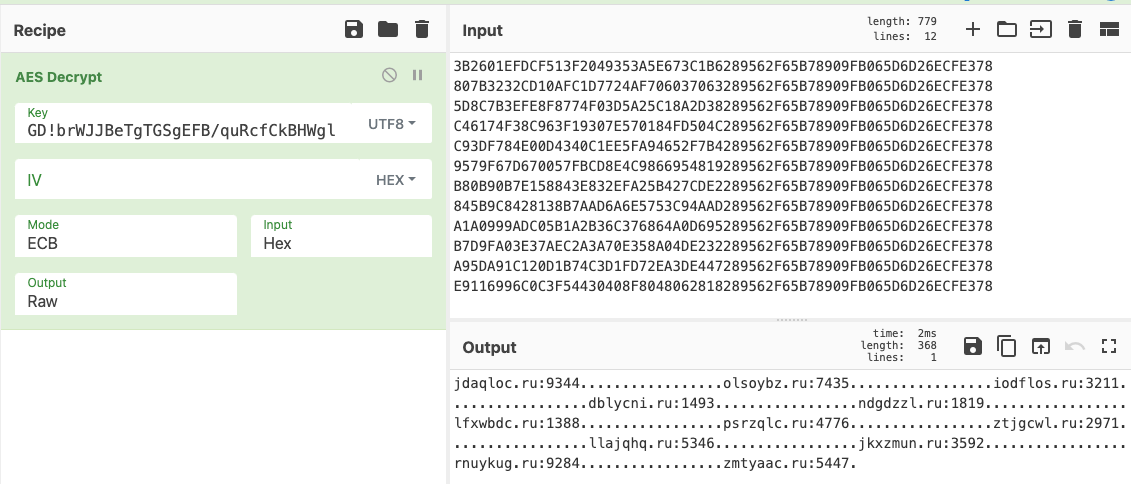
Figure 7 – Decryption of domain names
The downloader decrypts the domains at runtime, and tries to connect to the subdomain buy1, v1 or up1 (depending on the sample) of those domains. In the end, it tries to connect to the following domains:
- v1.flkpuod[.]ru:5796
- v1.iqaagar[.]ru:2919
- v1.fchbwme[.]ru:7533
- …
The command and control server responds with an AES encrypted message that, when decrypted, contains a link to download the next stage.
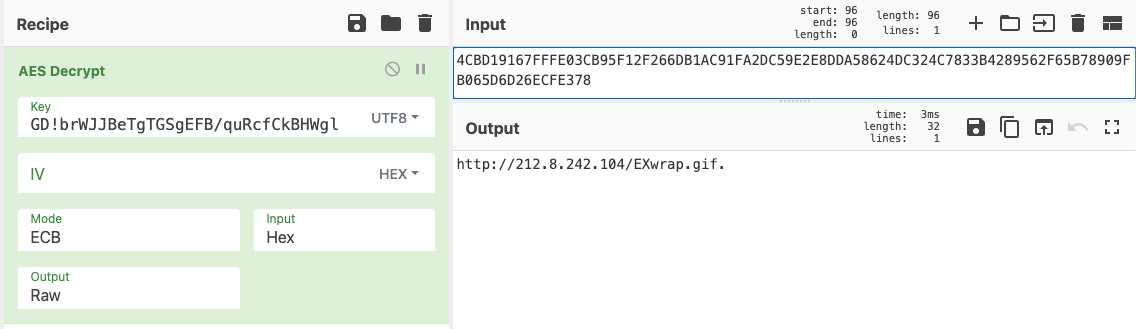
Figure 8 – Decryption of the response from the command and control
Once again, as the sample we found contains many hardcoded domain names, we started to monitor some of them to get an overview of the botnet.
The downloaded payload is a Mylobot sample, embedded in a WillExec dropper, the same way it was distributed in 2017. We’ve seen Mylobot’s downloader distributing other samples than Mylobot’s proxy bot (Minerva is showing an example), but it was quite rare.
The distribution has evolved in the way described in figure 9.
BlackHatWorld forum shows up. This post was written on May 12, 2014. The post author using the alias BHProxies, is still very active on this post, as his last messages were posted in December 2022. The author promotes bhproxies[.]com, and provides a Telegram channel and a Skype account to discuss with the potential customers. He also provides a free trial to convince users to buy his service. The free trial is available at the address http://clients.bhproxies.com/panel/trial.php
At this point, we cannot prove that BHProxies is linked to Mylobot, but we have a strong suspicion, since Mylobot and BHProxies used the exact same IP 46.166.173.180 on an interval of 24 hours.
To confirm our hypothesis, we tested the trial version of BHProxies. Once you enter your public IP address on the service, you receive an IP address and a list of ports to connect to.
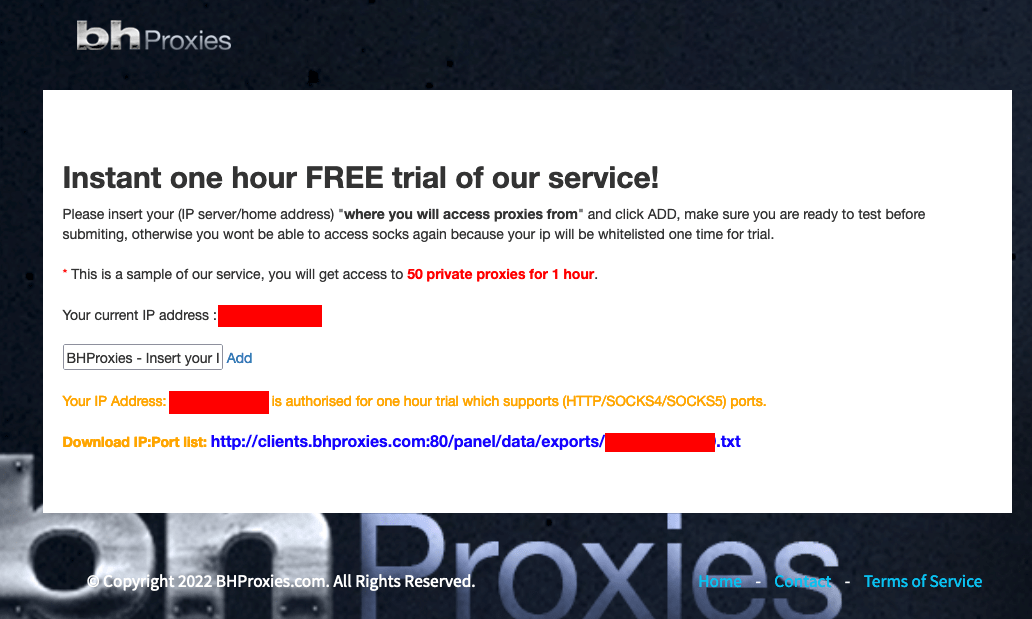
Figure 12 – BHProxies free trial
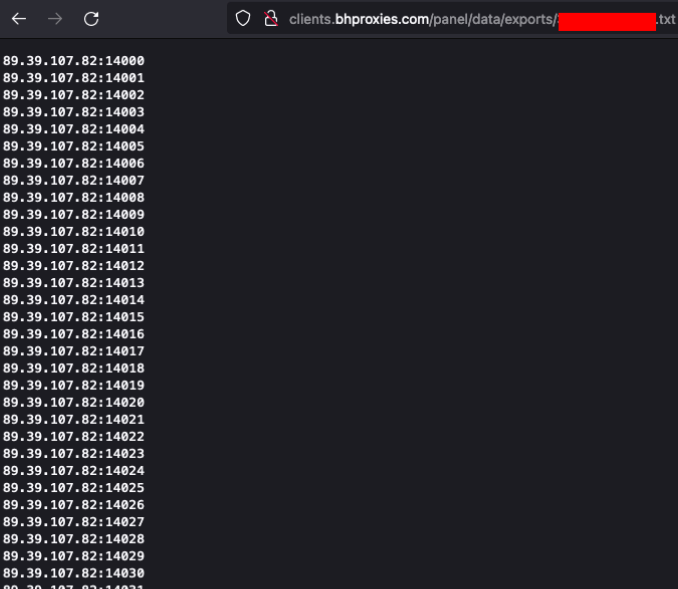
Figure 13 – BHProxies trial proxies
Each of those pairs of IP and port is a frontend for the residential proxies of BHProxies. We recovered the residential proxies IP addresses by performing an HTTP request to a server we control.
On the 50 frontend proxies provided, we were able to perform a HTTP request for 48 of those. Among these 48 recovered residential proxies IP addresses, 28 (58.3%) of those were already present in our sinkhole systems, associated with the Mylobot malware family. This number is probably higher, but we don’t have a full visibility of the botnet. This gave us clear evidence that Mylobot infected computers are used by the BHProxies service.
The trial proxies list is another indicator of the strong ties between BHProxies and Mylobot, since m41.fywkuzp[.]ru, one of Mylobot proxy C2, resolves to IP 89.39.107[.]82:

Telemetry
We started sinkholing Mylobot in November 2018. At that time, Mylobot’s proxy sample contained a lot of hardcoded DGA domains, so we were able to observe the majority of the botnet. It had led us to a maximum of 250,000 unique daily infected machines in the beginning of 2020.
Since the beginning of 2022, we’re not able to get infection telemetry from the latest Mylobot version as the sample doesn’t contain unregistered DGA domains anymore. Instead, we started monitoring Mylobot downloader’s domains and continue to see the evolution of Mylobot’s botnet.
We are currently seeing more than 50,000 unique infected systems every day, but we believe we are only seeing part of the full botnet, which may lead to more than 150,000 infected computers as advertised by BHProxies’ operators.
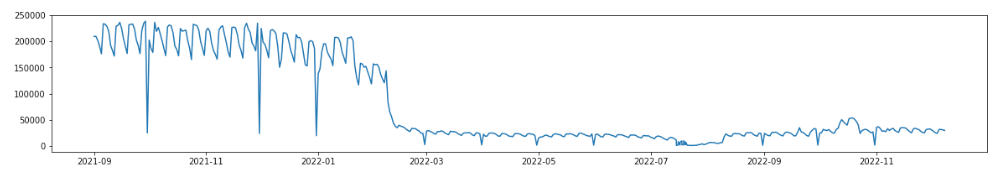
Figure 14 – Unique mylobot’s infected system per day
Figure 15 shows the countries where the most computers infected with Mylobot are found. India appears to be the most targeted country, followed by the US, Indonesia, then Iran.
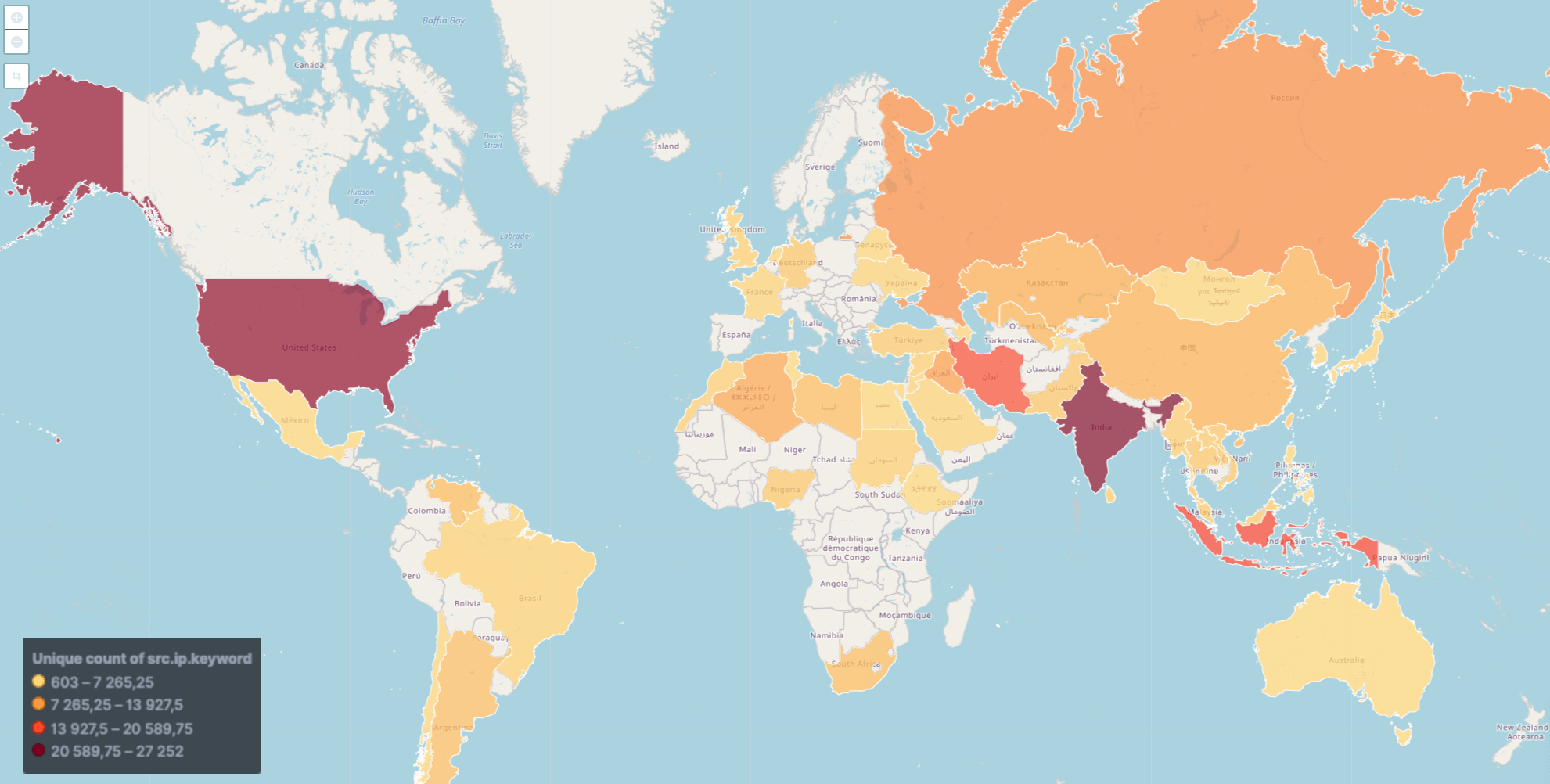
Figure 15 – Heat map of infected computers
IOCs
Mylobot proxy
84733af3b60b966042d5cd17e12fd8d90650e0731297d203bd913dc5c663b91c
11fc02dd825c8e67d58cc40a47e3f4c572097bd58c6aae80591a5fb73b9167f2
392f1054815c5f805d50b60ea261210012bdda386158a1da92d992a929eb77c2
03b2164da6318fff63b6cad2fc613c3d885bd65432a7b8744c2b1709f2f9a479
69a36e6f12b4e9b9cd15528a068385f2311b0c540336c142aabdd73c2a2e2015
a63a5639d0cb6a10f7af5bd0dd30ca1800958a0f5bb47f358b6d37f51d0f0a31
2ae61c8c2a8e83cde33f38b89599032a6fb455256aa414a15f2724c94d3460d2
40cfb7b7fad1602276ebf3fa63514ba91be6186d5d3bd190f593bdec0b6d8d64
Mylobot downloader
cfde42903367d77ab7d5f7c2a8cfc1780872d6f1bfac42e9c2577dfd4b6cdeb2
fcdb7247aa6e41ff23dc1747517a3682e5a89b41bfd0f37666d496a1d3faa4ba
ad53ad1d3e4ac4cc762f596af8855fd368331d9da78f35d738ae026dd778eb9f
Mylobot proxy C2 IPs
89.39.105.47
89.38.96.140
89.38.96.14
217.23.12.80
178.132.3.12
168.119.15.229
89.38.98.48
49.12.128.181
37.48.112.111
109.236.82.28
49.12.128.180
144.76.8.93
194.88.106.18
95.211.203.197
89.39.104.201
95.168.169.43
95.211.198.102
91.229.23.112
217.23.13.104
95.211.140.149
62.112.11.245
178.132.2.82
116.202.114.236
217.23.12.50
89.39.104.58
89.38.98.47
194.88.105.108
109.236.83.166
109.236.91.239
89.39.107.92
190.2.134.165
217.23.8.12
89.39.104.62
89.39.107.82
Source: https://www.bitsight.com/blog/mylobot-investigating-proxy-botnet