
Executive Summary
CYFIRMA Research Team has been tracking three campaigns – Evian, UNC064, and Siberian bear – that are potentially operated by Russian-speaking threat groups on behalf of their Russian Masters.
CYFIRMA Research Team has uncovered a comprehensive threat story originating from similarities between the three campaigns based on the target industries, geographies, methods used, motivation, campaign infrastructure indicators, and hacker conversations.
Multiple suspected Russian-speaking threat groups are involved:
- TA505
- FIN7
- Cozy Bear
- Fancy Bear
The motivation for operating these campaigns include:
- Retribution (due to geo-political fallouts).
- Espionage
- Financial Gains.
- Establishing Reconnaissance for launching Cyber Attacks at a later stage.
Introduction
For the past 4 months, CYFIRMA Research Team has been tracking three campaigns namely Evian, Unnamed Campaign – UNC064, and Siberian bear, that are suspected to be operated by Russian-speaking threat groups.
Based on the campaigns’ targeted industries, geographies, motives, TTPs, malware leveraged, and hacker’s conversations observed, CYFIRMA Research Team has established a series of calculated analysis and hypothesis. Connecting these dots has led us to ascertain possible collaboration between the cyber campaigns and the threat groups operating them.
Timelines
Below are the timelines observed for the active campaigns and the threat actors believed to be operating them.
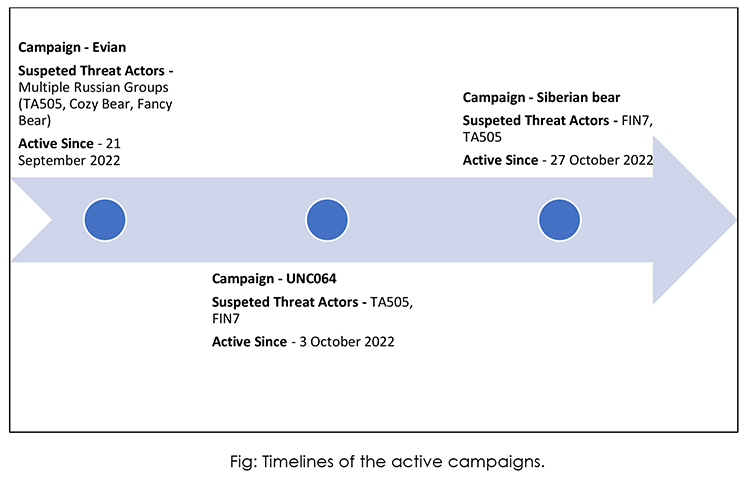
Campaign Analysis
The following inferences were established upon carrying out the research analysis of the campaigns.
(I) Similarities Observed Amongst the Campaigns
Following are the parallels observed between the three campaigns – Evian, UNC064, and Siberian bear.
1) Top Targeted Industries
2) Top Targeted Geographies
3) Objectives of Operating the Campaigns
4) Methods Discussed by Hackers and their Interest
(II) Attributions Around Hacker Conversations
CYFIRMA Research Team found several similarities among various hacker conversations observed in the underground and dark web forums. Details are illustrated below:

Evian Campaign
The above conversation when translated into English is as follows.
- (1) – Let’s show them to everyone who supports Ukraine
- (2) – Expand Target List.
- (3) – Add Later
Parallel observations were seen in the other two campaigns with similar conversations. The following are their translation in English.
UNC064 Campaign
- (1) – Let us go after them and punish them
- (2) – Expand Target List.
- (3) – Lots of money to make
Siberian bear Campaign
- (1) – Gather the potential asset list for cyber attacks
- (2) – Expand Target List.
- (3) – We get a lot of money
(III) Correlation in Campaign Infrastructure
According to our aggregated research & analysis, we have observed sharing of campaign infrastructure – specifically identified IOCs, their TTPs, and malware used across the three campaigns. The indicators are signalling towards Russian-speaking threat groups.
Details of the indicators are as below:
- 8bcd45559f6cb8834016d8e8eb0752cc
- 8363e265a2f79666f9bfca8ef23c453c
- 179.43.147.77
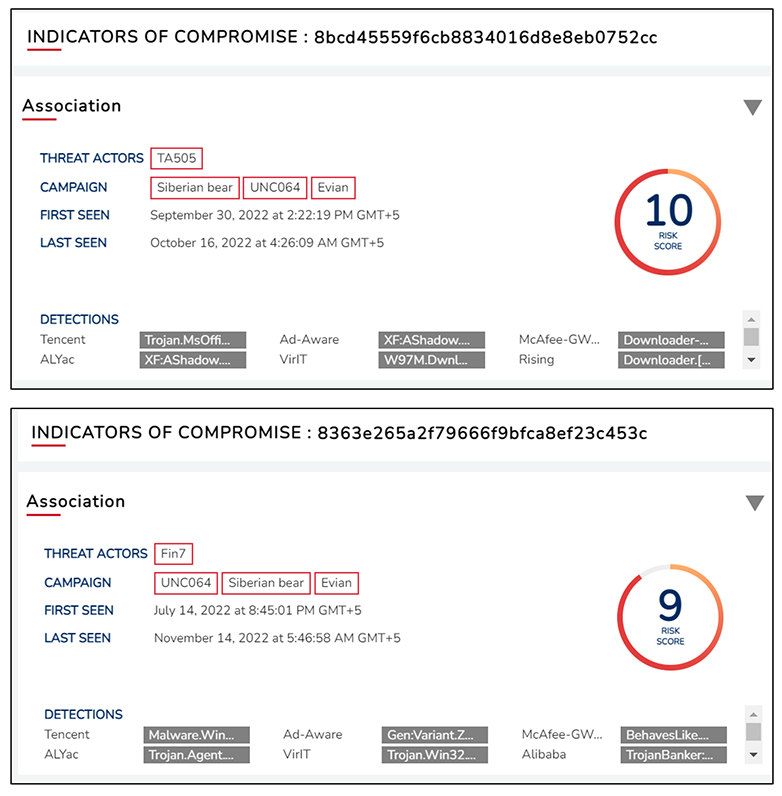
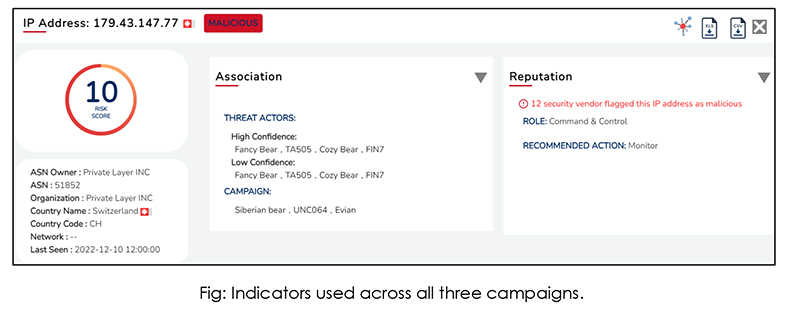
Based on the analysis of the common indicators observed in the campaign’s infrastructure, CYFIRMA Research Team observed that the Russian-speaking threat groups are using malware such as Emotet, Qakbot, FlawedAmmyy RAT, and Clop Ransomware; across the three campaigns. Such similarities correlated with additional indicators led CYFIRMA Research Team to suspect that the three campaigns are operated by Russian-speaking threat groups, many of whom are of the state- sponsored flavour.
As an outcome of our analysis of the campaign infrastructure indicators, we have observed the following TTPs being used by threat groups:
- Botnet malware is used as the launchpad.
- Malware and Ransomware attacks.
- The exploitation of weaknesses in the systems.
- Phishing emails with attachments/links.
Correlating with the MITRE ATT&CK framework, the TTPs observed after analyzing the samples mentioned above are as below:
| Sr.no | Tactics | Technique ID |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter T1059.004: Command and Scripting Interpreter: Unix Shell T1053: Scheduled Task/Job |
| 2 | TA0005: Defense Evasion | T1055: Process Injection |
| 3 | TA0007: Discovery | T1057: Process Discovery |
Conclusion
CYFIRMA Research Team believes the motivation of the following campaigns based on the observed and analysed details, and hacker conversations are as follows:
Campaign Name

Motivation

CYFIRMA Team has observed an emerging trend of individual Russian-speaking threat groups moving towards the development of their proprietary ransomware as a potent way of targeting the victim organization’s infrastructure for increasingly deeper penetration and faster lateral movement.
From an External Threat Landscape Management (ETLM) perspective, CYFIRMA suspects Russian-speaking threat groups are likely carrying out campaigns on behalf of their Russian state-masters. We continue to witness an uptick in cyberattacks against the nations that have imposed economic sanctions on Russia, while the threat groups would also be expanding their attack footprint against such nations by carrying out malware & ransomware attacks for financial gains, espionage activities, and establishing reconnaissance for launching further cyber-attacks.
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português