This article discusses the targeting tactics of a threat actor known as “TA4557”, who employs resumes as a phishing lure to distribute malware dubbed “more_eggs” that aims for credential theft. The article identifies multiple indicators of compromise (IoCs), including domains and IP addresses associated with this threat. Affected: phishing campaigns, credential theft, internet security, organizations applying for jobs.
Keypoints :
- TA4557 uses resumes as a lure in targeted phishing attacks.
- The malware “more_eggs” enables credential theft through links in the resumes.
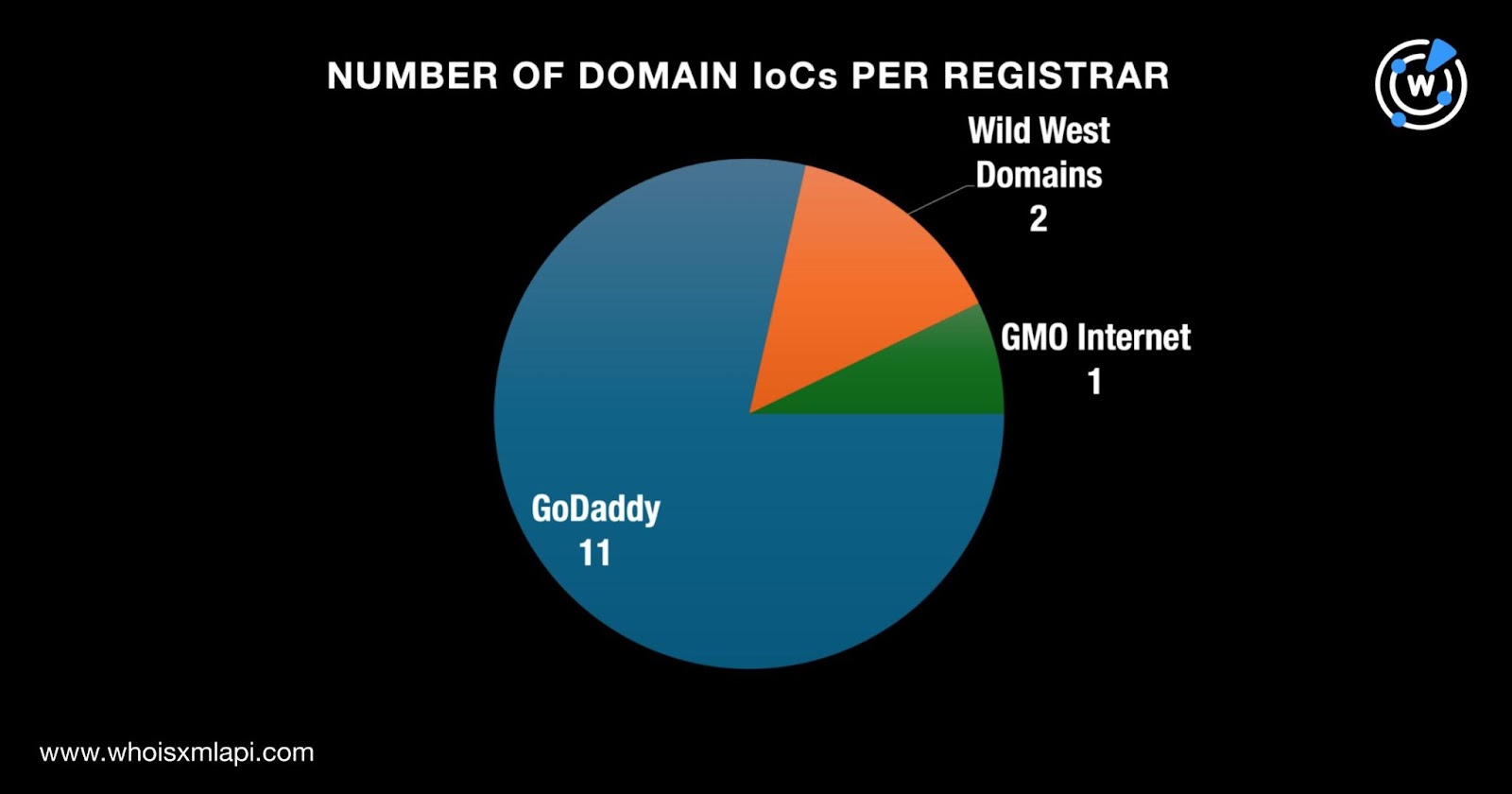
- DFIR Report identified 14 initial domain IoCs and 3 IP address IoCs related to more_eggs.
- Research uncovered additional IoCs, including 35 email-connected domains and 700 IP-connected domains.
- Domains linked to TA4557 were created between 1997 and 2024.
- Most domains registered in the U.S. indicate a possible preference for older domains.
- Historical analysis showed 13 domains had numerous public email addresses in their WHOIS records.
- Some IP addresses have been linked to prior malicious activities such as phishing and malware distribution.
MITRE Techniques :
- Phishing (T1566): The threat actor uses resumes as a bait to solicit victims and distribute malware.
- Command and Control (T1071): The malware connects to an external server for remote access following infection.
- Credential Dumping (T1003): The final payload of the attack formulates the theft of user credentials.
Indicator of Compromise :
- [Domain] annetterawlings[.]com
- [Domain] howasit[.]com
- [Domain] johnshimkus[.]com
- [Domain] markqualman[.]com
- [Domain] shehasgone[.]com
Full Story: https://circleid.com/posts/more-signs-of-the-more-eggs-backdoor-found-in-the-dns