Two weeks ago I wrote about the PDF Toolbox extension containing obfuscated malicious code. Despite reporting the issue to Google via two different channels, the extension remains online. It even gained a considerable number of users after I published my article.
A reader tipped me off however that the Zoom Plus extension also makes a request to serasearchtop[.]com. I checked it out and found two other versions of the same malicious code. And I found more extensions in Chrome Web Store which are using it.
So now we are at 18 malicious extensions with a combined user count of 55 million. The most popular of these extensions are Autoskip for Youtube, Crystal Ad block and Brisk VPN: nine, six and five million users respectively.
Update (2023-06-01): With an increased sample I was able to find some more extensions. Also, Lukas Andersson did some research into manipulated extension ratings in Chrome Web Store and pointed out that other extensions exhibited similar patterns in their review. With his help I was able to identify yet another variant of this malicious code and a bunch more malicious extensions. So now we are at 34 malicious extensions and 87 million users.
Update (2023-06-02): All but eight of these extensions have been removed from Chrome Web Store. These eight extensions are considerably different from the rest, so I published a follow-up blog post discussing the technical aspects here.
The extensions
So far I could identify the following 34 malicious extensions. Most of them are listed as “Featured” in Chrome Web Store. User counts reflect the state for 2023-05-30.
Update (2023-06-12): The complete list of extension IDs from this article series can be found here. This repository also contains the check-extensions command-line utility which will search local browser profiles for these extensions.
| Name | Weekly active users | Extension ID |
|---|---|---|
| 9,008,298 | lgjdgmdbfhobkdbcjnpnlmhnplnidkkp | |
| Soundboost | 6,925,522 | chmfnmjfghjpdamlofhlonnnnokkpbao |
| 6,869,278 | lklmhefoneonjalpjcnhaidnodopinib | |
| 5,595,420 | ciifcakemmcbbdpmljdohdmbodagmela | |
| 3,499,233 | meljmedplehjlnnaempfdoecookjenph | |
| 3,483,639 | lipmdblppejomolopniipdjlpfjcojob | |
| 2,797,773 | lmcboojgmmaafdmgacncdpjnpnnhpmei | |
| 2,786,137 | icnekagcncdgpdnpoecofjinkplbnocm | |
| 2,782,790 | bahogceckgcanpcoabcdgmoidngedmfo | |
| 2,571,050 | bkpdalonclochcahhipekbnedhklcdnp | |
| 2,437,224 | magnkhldhhgdlhikeighmhlhonpmlolk | |
| 2,430,636 | edadmcnnkkkgmofibeehgaffppadbnbi | |
| 2,370,645 | ajneghihjbebmnljfhlpdmjjpifeaokc | |
| 2,366,136 | nadenkhojomjfdcppbhhncbfakfjiabp | |
| 2,353,436 | pbdpfhmbdldfoioggnphkiocpidecmbp | |
| 2,237,147 | hdgdghnfcappcodemanhafioghjhlbpb | |
| Amazing Dark Mode | 2,228,049 | fbjfihoienmhbjflbobnmimfijpngkpa |
| 2,226,293 | kjeffohcijbnlkgoaibmdcfconakaajm | |
| Awesome Auto Refresh | 2,222,284 | djmpbcihmblfdlkcfncodakgopmpgpgh |
| 1,973,783 | obeokabcpoilgegepbhlcleanmpgkhcp | |
| 1,967,202 | mcmdolplhpeopapnlpbjceoofpgmkahc | |
| 1,852,707 | dppnhoaonckcimpejpjodcdoenfjleme | |
| Volume Frenzy | 1,626,760 | idgncaddojiejegdmkofblgplkgmeipk |
| 1,493,741 | deebfeldnfhemlnidojiiidadkgnglpi | |
| 1,471,726 | gfbgiekofllpkpaoadjhbbfnljbcimoh | |
| 1,460,691 | pbebadpeajadcmaoofljnnfgofehnpeo | |
| 1,459,488 | flmihfcdcgigpfcfjpdcniidbfnffdcf | |
| 1,457,548 | pinnfpbpjancnbidnnhpemakncopaega | |
| 1,456,013 | iicpikopjmmincpjkckdngpkmlcchold | |
| Leap Video Downloader | 1,454,917 | bjlcpoknpgaoaollojjdnbdojdclidkh |
| 1,451,822 | okclicinnbnfkgchommiamjnkjcibfid | |
| Qspeed Video Speed Controller | 732,250 | pcjmcnhpobkjnhajhhleejfmpeoahclc |
| HyperVolume | 592,479 | hinhmojdkodmficpockledafoeodokmc |
| Light picture-in-picture | 172,931 | gcnceeflimggoamelclcbhcdggcmnglm |
Note that this list is unlikely to be complete. It’s based on a sample of roughly 1,600 extensions that I have locally, not all the Chrome Web Store contents.
The malicious code
There is a detailed discussion of the malicious code in my previous article. I couldn’t find any other extension using the same code as PDF Toolbox, but the two variants I discovered now are very similar. There are minor differences:
- First variant masquerades as Mozilla’s WebExtension browser API Polyfill. The “config” download address is
https://serasearchtop.com/cfg/<Extension_ID>/polyfill.json, and the mangled timestamp preventing downloads within the first 24 hours islocalStorage.polyfill. - The second variant masquerades as Day.js library. It downloads data from
https://serasearchtop.com/cfg/<Extension_ID>/locale.jsonand stores the mangled timestamp inlocalStorage.locale.
Both variants keep the code of the original module, the malicious code has been added on top. The WebExtension Polyfill variant appears to be older: the extensions using it usually had their latest release end of 2021 or early in 2022. The extensions using the Day.js variant are newer, and the code has been obfuscated more thoroughly here.
The extension logic remains exactly the same however. Its purpose is making two very specific function calls, from the look of it: chrome.tabs.onUpdated.addListener and chrome.tabs.executeScript. So these extensions are meant to inject some arbitrary JavaScript code into every website you visit.
What does it actually do?
As with PDF Toolbox, I cannot observe the malicious code in action. The configuration data produced by serasearchtop[.]com is always empty for me. Maybe it’s not currently active, maybe it only activates some time after installation, or maybe I have to be in a specific geographic region. Impossible to tell.
So I went checking out what other people say. Many reviews for these extensions appear to be fake. There are also just as many reviews complaining about functional issues: people notice that these extensions aren’t really being developed. Finally, a bunch of Brisk VPN reviews mention the extension being malicious, sadly without explaining how they noticed.
But I found my answer in the reviews for the Image Download Center extension:
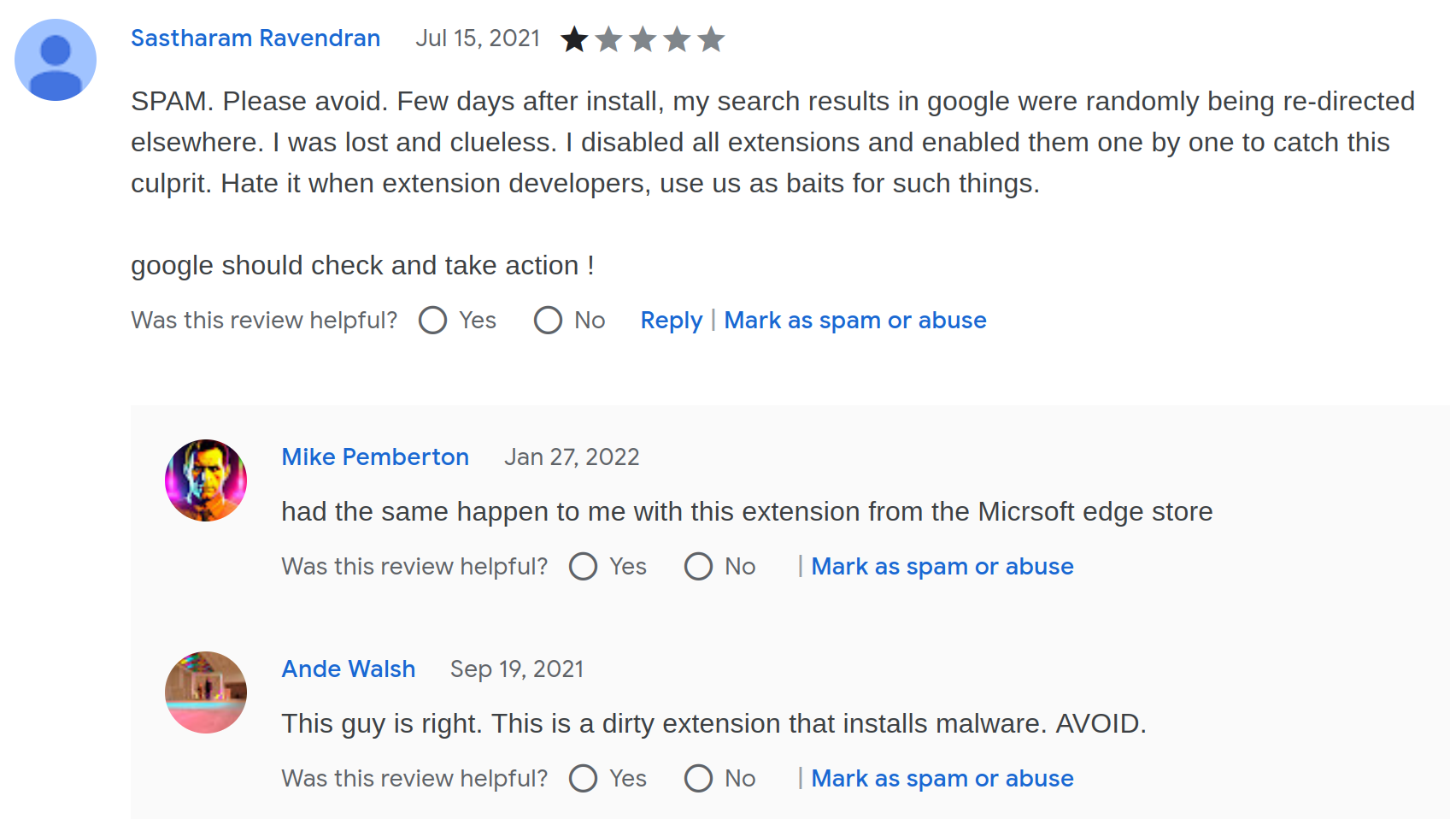
So it would seem that at least back in 2021 (yes, almost two years ago) the monetization approach of this extension was redirecting search pages. I’m pretty certain that these users reported the extension back then, yet here we still are. Yes, I’ve never heard about the “Report abuse” link in Chrome Web Store producing any result. Maybe it is a fake form only meant to increase customer satisfaction?
There is a similar two years old review on the OneCleaner extension:
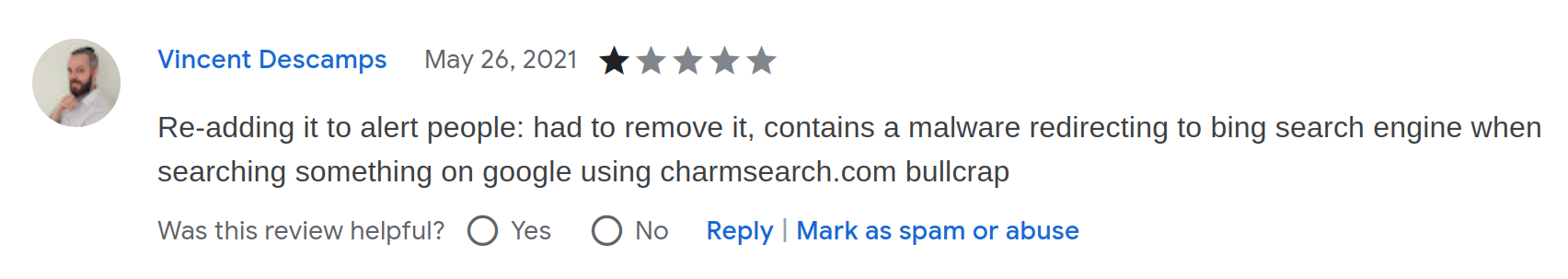
Small correction: the website in question was actually called CharmSearching[.]com. If you search for it, you’ll find plenty discussions on how to remove malware from your computer. The domain is no longer active, but this likely merely means that they switched to a less known name. Like… well, maybe serasearchtop[.]com. No proof, but serasearchtop[.]com/search/?q=test redirects to Google.
Mind you: just because these extensions monetized by redirecting search pages two years ago, it doesn’t mean that they still limit themselves to it now. There are way more dangerous things one can do with the power to inject arbitrary JavaScript code into each and every website.
Source: https://palant.info/2023/05/31/more-malicious-extensions-in-chrome-web-store/
Views: 0