
New research from Recorded Futures Insikt Group focuses on the growing threat of a possible "mobile NotPetya" event. Through zero-click exploits, a self-propagating mobile malware could infiltrate smartphones at scale. The threat has increased sharply in the past few years as spyware companies continually refine zero-click exploits. This fact is driven home by the alarming rise in disclosures of zero-click vulnerabilities in 2023, which surpassed the total figures of the preceding four years.
The Escalating Risk of Mobile Malware in Todays Geopolitical and Cyber Landscape
With mobile devices becoming vital tools in corporate security and operations, the potential impacts of self-propagating mobile malware are increasingly severe. The global geopolitical climate and the growing sophistication of cybercriminals add weight to the possibility of either deliberate or inadvertent execution of a mobile NotPetya event.
Discussing historical instances of mobile malware, the document references Cabir and Commwarrior. However, the current complexity of mobile platform processes and protocols presents a more challenging task of protection from zero-click exploits. Spyware companies like the NSO Group persistently develop these exploits, elevating the risk factor.
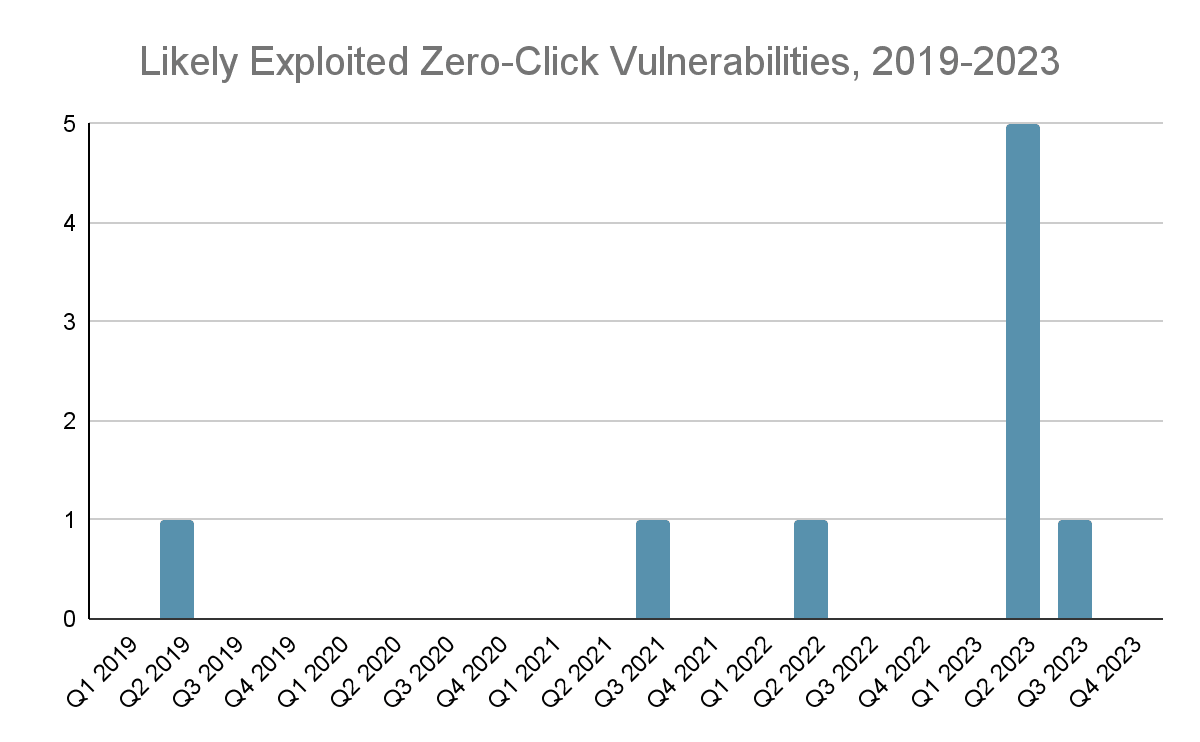 Reports of zero-click vulnerability exploitation began to proliferate at an alarming rate in 2023 compared to the previous four years
Reports of zero-click vulnerability exploitation began to proliferate at an alarming rate in 2023 compared to the previous four years
While solutions like Lockdown Mode for iOS exist, the document highlights the lack of incentives for most users to adopt such solutions. The parallels between a "mobile NotPetya" event and the 2017 NotPetya ransomware attack are also discussed, noting the severe impact of the latter incident.
For such an event to occur, certain conditions must be met, including the ongoing development of zero-click exploits, the potential for mobile malware to spread independently, vulnerabilities within Android and iOS consumer bases, the scarcity of effective countermeasures, and motivations for threat actors to initiate an attack. All conditions are either active or possible today.
The potential spread of a mobile NotPetya event is predicted using models from epidemiology, revealing similarities between malware and disease dissemination. Measures to thwart such an event are suggested, involving telecommunications providers or mobile device manufacturers filtering messages based on header information or geographic location. However, these measures' practicality is yet to be tested on a large scale, and implementation might only be possible after infection rates have spiked.
To read the entire analysis, click here to download the report as a PDF.
Source: Original Post