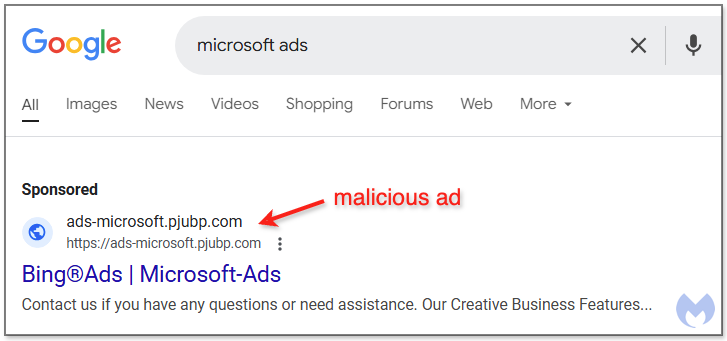
A recent phishing campaign targeting Microsoft advertisers has been uncovered, utilizing malicious ads on Google Search to steal login information. The attack employs various techniques to evade detection and has been linked to a larger ongoing issue of phishing through online advertising. Affected: Google Search, Microsoft Advertising
Keypoints :
- Malicious ads targeting Microsoft advertisers appear on Google Search.
- Attackers use techniques like redirection and cloaking to evade detection.
- Users are subjected to a Cloudflare challenge to verify their authenticity.
- The phishing page mimics the legitimate Microsoft Advertising platform.
- Campaigns targeting Microsoft Ads accounts may have been ongoing for years.
- Users are advised to verify URLs and use 2-Step verification for security.
MITRE Techniques :
- Phishing (T1566): Attackers create fake ads to lure users into providing login credentials.
- Redirection (T1071): Malicious users redirect genuine traffic to phishing sites.
- Cloaking (T1070): Attackers present different content to security scanners and genuine users.
- Credential Dumping (T1003): Phishing page attempts to capture user credentials.
Indicator of Compromise :
- [domain] ads[.]mcrosoftt[.]com
- [domain] account-microsoft[.]online
- [domain] account-mircrosoft-ads[.]com
- [domain] ads-microsoft[.]click
- [domain] login-adsmicrosoft[.]helpexellent[.]com
- Check the article for all found IoCs.
Full Research: https://www.malwarebytes.com/blog/cybercrime/2025/01/microsoft-advertisers-phished-via-malicious-google-ads