Summary: Researchers have uncovered a method to bypass the ‘First Contact Safety Tip’ anti-phishing feature in Microsoft 365, increasing the risk of users falling victim to malicious emails. Despite reporting the vulnerability to Microsoft, the company has decided not to address the issue at this time, citing it as a social engineering tactic rather than a technical vulnerability.
Threat Actor: Phishers | phishers
Victim: Microsoft 365 Users | Microsoft 365 Users
Key Point :
- Researchers demonstrated that CSS manipulation can hide the ‘First Contact Safety Tip’ in Outlook, leaving users unaware of potential phishing attempts.
- Microsoft acknowledged the finding but chose not to take immediate action, emphasizing the need for users to maintain good online security practices.
- The technique allows phishers to create a deceptive appearance of security by spoofing Outlook’s encrypted/signed email icons.

Researchers have demonstrated a method to bypass an anti-phishing measure in Microsoft 365 (formerly Office 365), elevating the risk of users opening malicious emails.
Specifically, the anti-phishing measure that can be hidden is the ‘First Contact Safety Tip,’ which warns email recipients on Outlook when they receive a message from an unfamiliar address.
Certitude analysts who discovered the flaw reported their findings to Microsoft, but the tech giant decided not to address it at this time.
Hiding the warning
The “First Contact Safety Tip” is a feature designed to alert Outlook users when they receive emails from new contacts. It displays a message that reads: “You don’t often get email from xyz@example.com. Learn why this is important.”
The key aspect of this mechanism is that the alert is appended to the main body of the HTML email, opening up the potential for manipulation using CSS embedded in an email message.
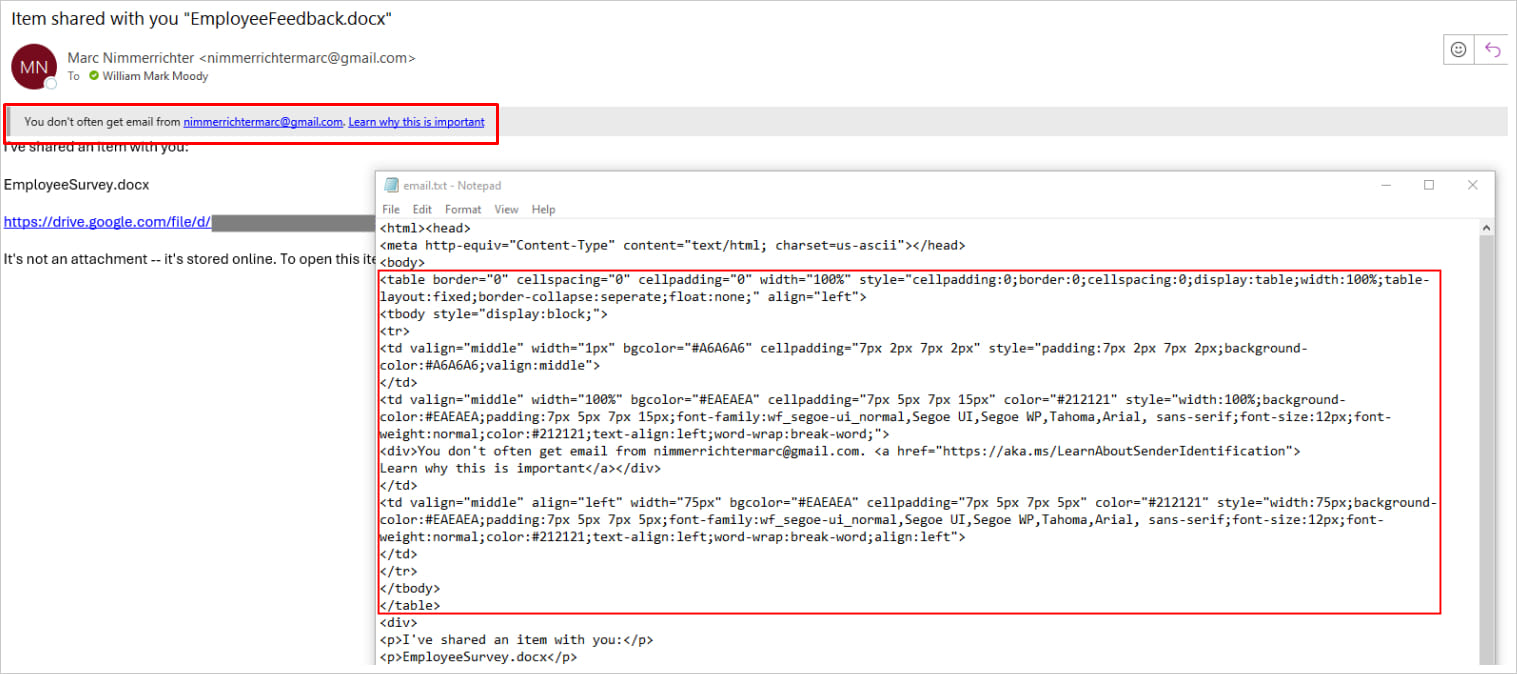
Source: Certitude
Certitude discovered that it’s possible to hide this safety message by manipulating the CSS (Cascading Style Sheets) within the HTML of the email, as shown below:
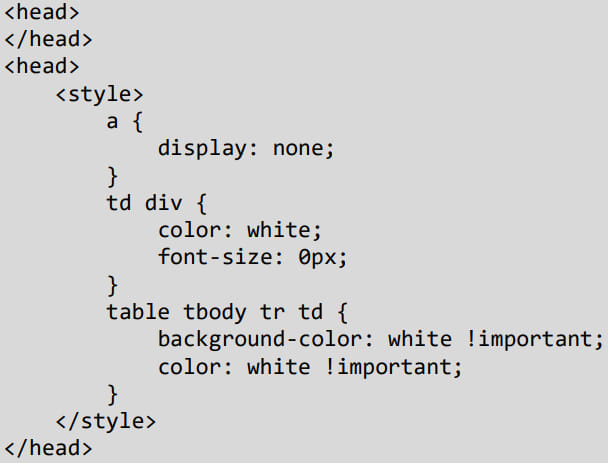
Source: Certitude
The role of each rule is the following:
- a { display: none; }: Hides any anchor (<a>) tags to prevent the tip from being displayed when a link is included.
- td div { color: white; font-size: 0px; }: Targets div elements within table data cells, changing their font color to white and font size to 0, hence making the text invisible.
- table tbody tr td { background-color: white !important; color: white !important; }: This makes any td element within the tbody of a table to have a white background and white text, effectively making the content blend into the background and thus appear invisible.
When this CSS is used in a phishing email sent from a new contact to a target, no alert shows up to warn the recipient.
Taking the deception one step further, Certitude found that it’s also possible to add more HTML code that spoofs the icons Microsoft Outlook adds to encrypted/signed emails to make them appear even more secure.
Although some formatting limitations don’t allow for a perfect visual result, the trick still creates a convincing false image of security that could easily pass anything less than careful inspections.
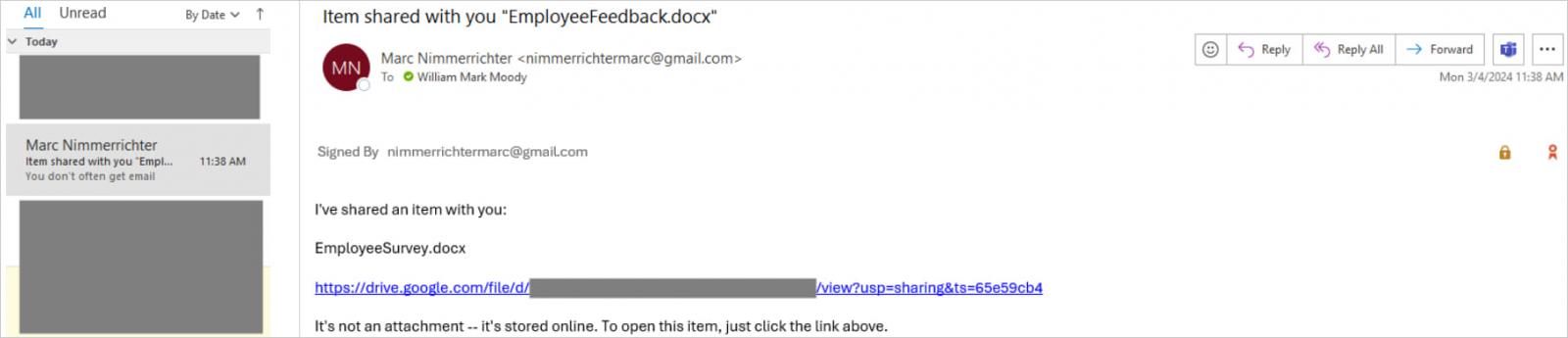
Source: Certitude
The researchers told BleepingComputer that they have not observed any cases of active exploitation of the described method or found ways to manipulate the HTML so that arbitrary text is displayed in the email.
Certitude sent Microsoft a proof of concept for the above techniques and a detailed report via the Microsoft Researcher Portal (MSRC).
However, they received the following response from Microsoft:
“We determined your finding is valid but does not meet our bar for immediate servicing considering this is mainly applicable for phishing attacks. However, we have still marked your finding for future review as an opportunity to improve our products.” – Microsoft
BleepingComputer has contacted Microsoft to learn more about its decision not to address the risk, and a spokesperson sent the following statement:
We’ve reviewed this report and have found that it does not meet the bar for immediate servicing under our severity classification guidelines.
The technique described is not a vulnerability and relies on social engineering to be successful.
We continue to encourage customers to practice good computing habits online including exercising caution when clicking on links to web pages. – a Microsoft spokesperson