This report details the vulnerabilities discovered in the Mercedes-Benz User Experience (MBUX) infotainment system, particularly focusing on the first generation of MBUX subsystems. The research highlights the importance of diagnostic software, the architecture of MBUX, and the various attack vectors identified during testing. Affected: Mercedes-Benz MBUX
Keypoints :
- Research focused on the first generation of MBUX infotainment system.
- Diagnostic software was essential for analyzing the vehicle architecture.
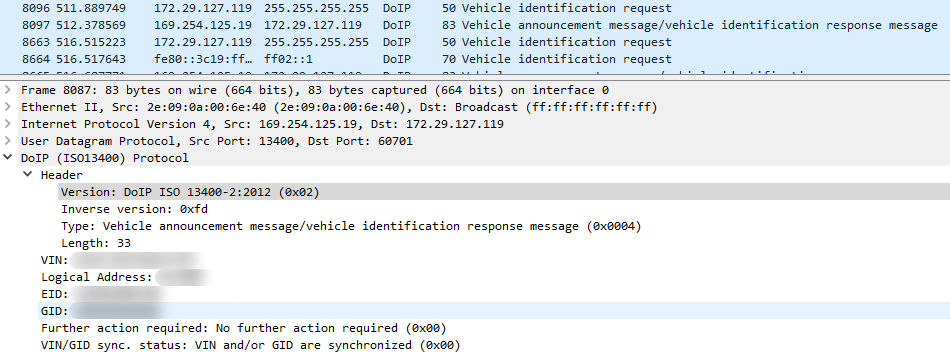
- Communication protocols used include DoIP and custom ASCII-based protocols.
- Identified vulnerabilities include buffer overflows and command injections.
- Test setups included both a real car and a custom-designed testbed.
- Firmware extraction was necessary for vulnerability analysis.
- Custom IPC protocols used for inter-service communication within MBUX.
- Vulnerabilities can be exploited through physical access, particularly via USB.
- Multiple CVEs were assigned during the vulnerability disclosure process.
MITRE Techniques :
- TA0001 – Initial Access: Exploitation of vulnerabilities in USB subsystem.
- TA0002 – Execution: Command injection through improperly handled input.
- TA0005 – Credential Access: Exploiting privilege escalation vulnerabilities.
- TA0007 – Discovery: Use of diagnostic tools to gather information on the ECU.
- TA0008 – Lateral Movement: Communication between microservices using custom IPC protocols.
Indicator of Compromise :
- [file name] pduparser.lua
- [file name] triggerRestore.py
- [file name] triggerBackup.py
- [file name] ud2codec.py
- [others ioc] Check the article for all found IoCs.
Full Research: https://securelist.com/mercedes-benz-head-unit-security-research/115218/