Estimated reading time: 5 minutes
Our recent research has highlighted the presence of the MedusaLocker ransomware, which first surfaced in mid-2019. Its primary targets are the Hospital and Healthcare industries. MedusaLocker employs AES and RSA encryption techniques to encrypt victims’ data.
Technical analysis
At the start, it performs a check for the presence of a Mutex. If the Mutex does not exist, it proceeds to create the Mutex using the CreateMutexW() function, as shown in the below fig:
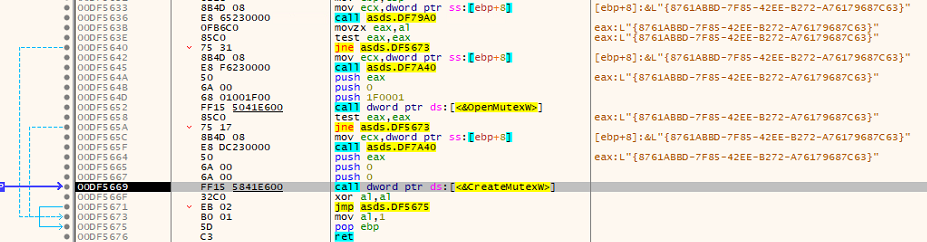
Fig: Creating the Mutex
MedusaLocker checks to determine whether the current process runs with administrative privileges. If it detects that the process lacks admin privileges, it employs a User Account Control (UAC) bypass technique to attain elevated privileges.
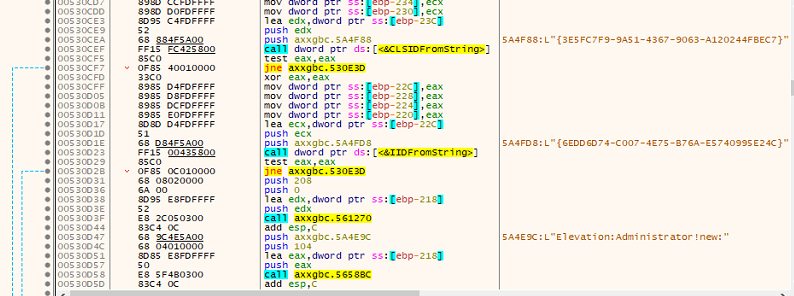
Fig: Elevating administrator privilege
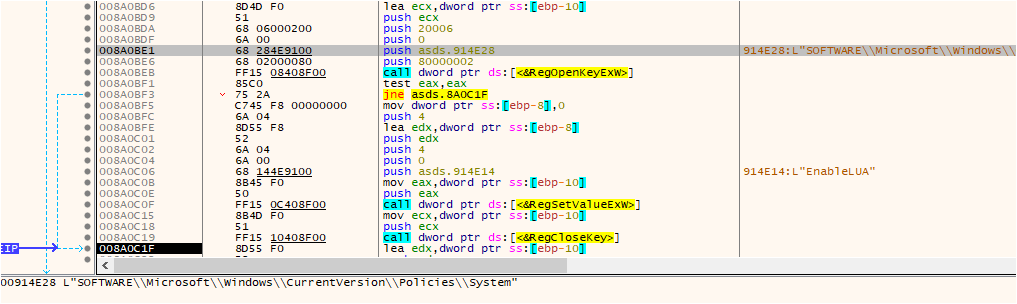
Fig: UAC bypass
It adds the registry key HKEY_CURRENT_USERSOFTWAREMDSLK with the name “self” and data as the application name, designating the system being infected by MDuSaLocker.
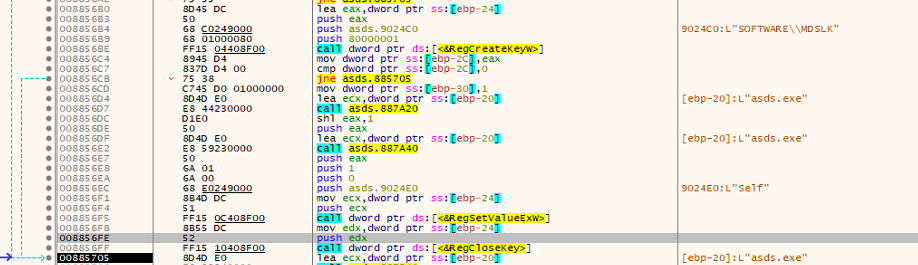
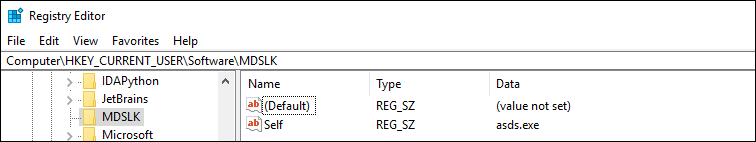
Fig: Registry entry
Disables the services and terminates the processes:
Like other ransomware, MedusaLocker also terminates specific services by referencing a hardcoded list of services. It compares this list with the currently running services, and if any of the hardcoded services are found to be running, it stops them using the CloseServiceHandle(), as shown in the below fig:
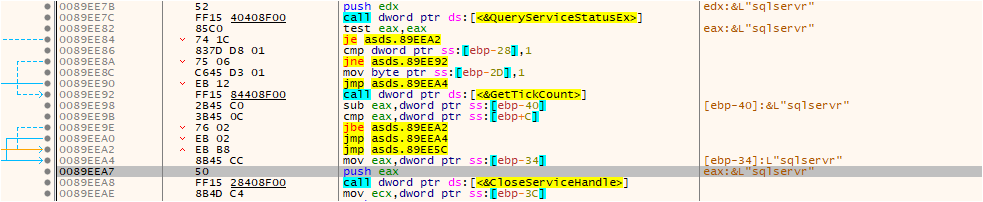
Fig: Disables the running service
List of hardcoded services:
wrapper, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, sqlservr, sqlagent, sqladhlp, Culserver, RTVscan, sqlbrowser, SQLADHLP, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, sqlwriter, msmdsrv, tomcat6, zhudongfangyu, SQLADHLP, vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8
Ransomware uses CreateToolhelp32Snapshot() to retrieve the running processes. It compares with a predefined list of hardcoded processes. If any of the hardcoded processes are detected as running, the ransomware proceeds to terminate those processes using the TerminateProcess, as shown in the below fig:
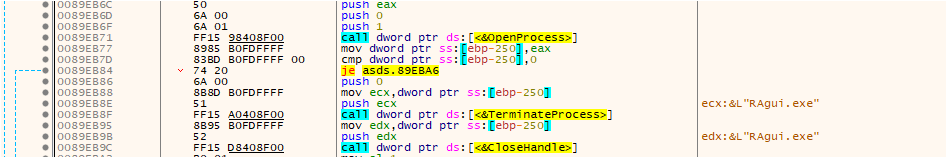
Fig: Terminating the running process
List of hardcoded processes:
wxServer.exe, wxServerView, sqlservr.exe, sqlmangr.exe, RAgui.exe, supervise.exe, Culture.exe, RTVscan.exe, Defwatch.exe, sqlbrowser.exe, winword.exe, QBW32.exe, QBDBMgr.exe, qbupdate.exe, QBCFMonitorService.exe, axlbridge.exe, QBIDPService.exe, httpd.exe, fdlauncher.exe, MsDtSrvr.exe, tomcat6.exe, java.exe, 360se.exe, 360doctor.exe, wdswfsafe.exe, fdlauncher.exe, fdhost.exe, GDscan.exe, ZhuDongFangYu.exe
Deleting shadow copy and disabling data recovery:
MedusaLocker uses hardcoded commands to remove backups, delete the shadow copy, etc.
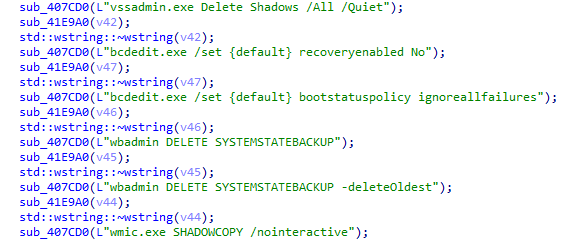
Fig: Hardcoded commands
Persistence
Medusa Locker ransomware duplicates its malicious executable as either “svhost.exe” or “svchostt.exe” within the user’s roaming application data directory (%AppData%Roaming) to establish persistence and ensure the malware runs during system start-up, allowing it to continue encrypting files.
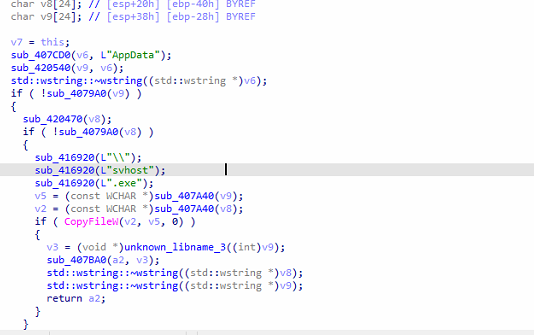
Fig: Persistence mechanism
Encryption
In the encryption process like other ransomware, it also excludes the list of files, folders, and hardcoded extensions from the encryption process.
The ransomware uses both AES+RSA encryption keys. The ransomware employs AES 256 encryption to lock the victim’s files, creating a unique AES encryption key. This AES key is then encrypted using an embedded RSA public key, resulting in the ciphertext. The RSA encryption ensures that without the corresponding private key, decryption of the AES key is practically impossible.
The AES key is essential for unlocking the victim’s files, making access contingent on obtaining the private key from the attackers.
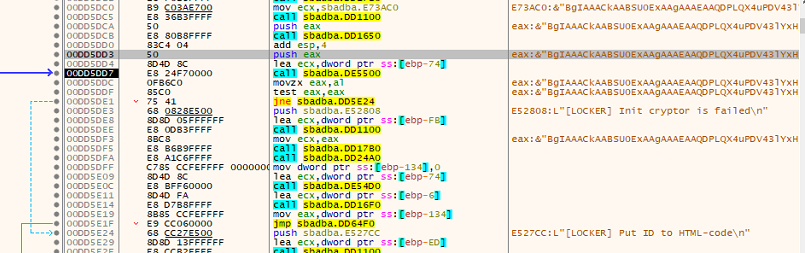
Fig: RSA-KEY
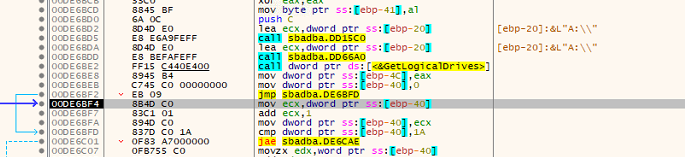
Fig: Iteration of drive
The ransomware tries to retrieve the logical drives using the API call GetLogicalDrives to encrypt the system.
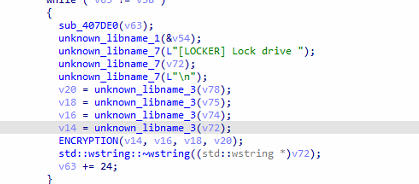
Fig: Calling encryption function
It drops the Ransom note in an HTML file which contains the personal ID, Tor link, and emails of attackers.
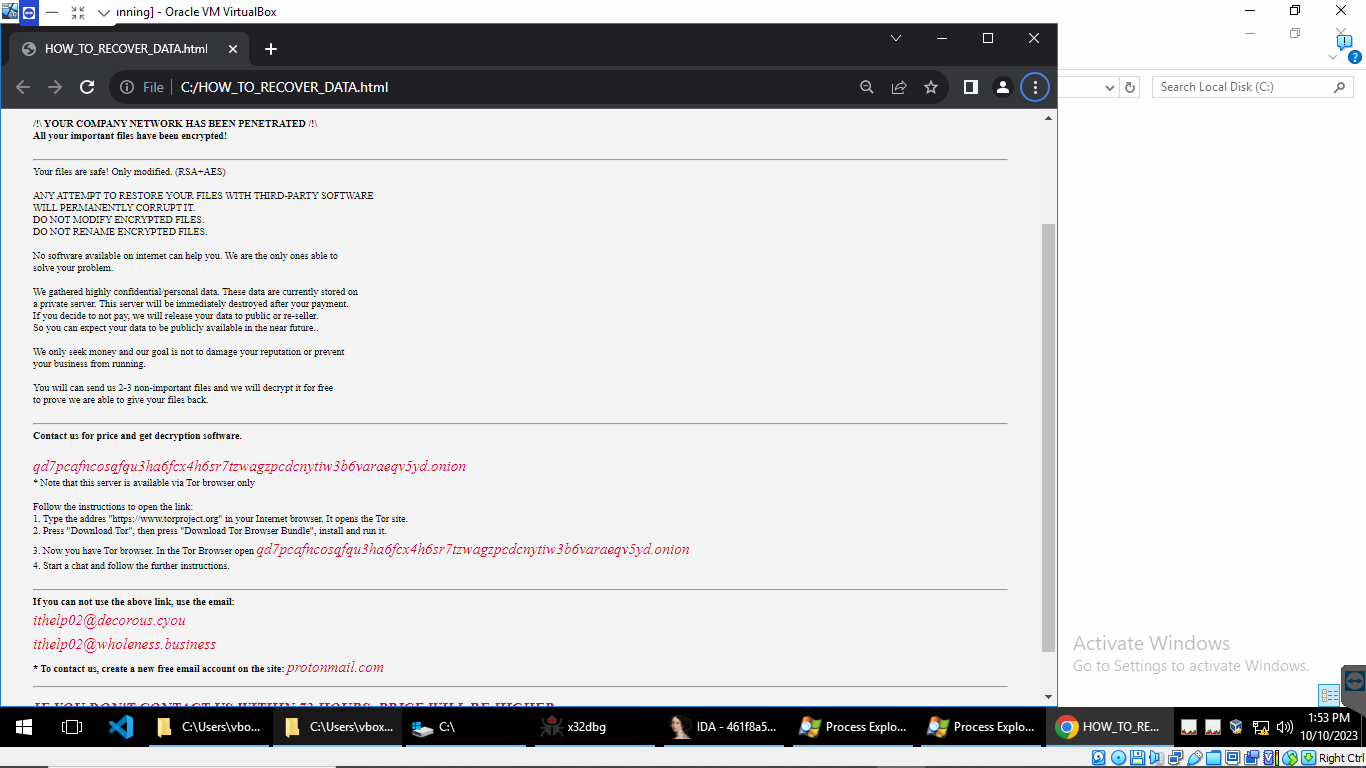
Fig: Ransom note dopped by Medusa Ransomware
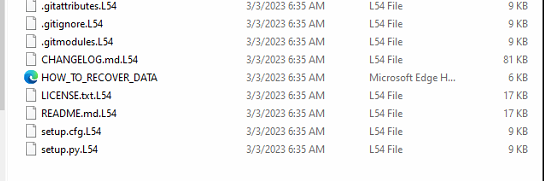
Fig: Encrypted files with extension “L54”
Network infection
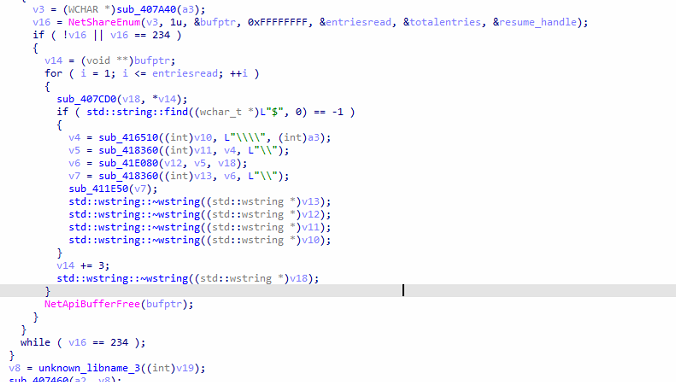
Fig: Network Enumeration
After Encryption, the ransomware uses Windows Network API NetShareEnum to enumerate network share. It processes share names, performs string manipulations, and checks for the presence of “$” in share names.
It seeks to spread to other devices on the same network, attempting to infect them like a digital contagion.
How do we prevent such kinds of attacks?
- Do not download and open any attachments from unknown sources.
- Avoid clicking on any unverified link. The leading cause of ransomware attacks is clicking on untrusted links and attachments.
- Regularly update your operating system, applications, and software to fix known vulnerabilities, often exploited by ransomware.
- Back up your data so that it can be recovered in case of a ransomware attack.
Conclusion
Medusa Locker ransomware is a notorious strain of malicious software that encrypts victims’ files, rendering them inaccessible until a ransom is paid. This dangerous malware has caused widespread damage to individuals and organizations alike. As cybercriminals continually evolve their tactics, the threat of Medusa Locker remains ever-present.
SEQRITE protection:
- Generic Signature names:
- Medusa.S27286013
- Medusa.S13913779
- MedusaLock.S9836707
- YakbeexMSIL.ZZ4
- Medusa.S10272352
MITRE ATT&CK TTPs:
| Command and Scripting Interpreter | T1059 |
| Inhibit System Recovery | T1490 |
| File and Directory Discovery | T1083 |
| System Information Discovery | T1082 |
| Data Encrypted for Impact | T1486 |
| Service Stop | T1489 |
- IOCs:
- 6da9c76a6e319c17f1d39e0ae2eaf2af
- 4ef811b784b985769645e03bc0b9cd24
- 61b0906f31ce772130b0ee9c4b86dc92
Source: Original Post