
This post is also available in:
日本語 (Japanese)
Executive Summary
We’ve probably all received advice for how to avoid phishing, such as to be on the lookout for spelling errors or other mistakes that would alert us to the presence of fraudsters. However, this advice is only helpful for traditional phishing techniques. Meddler in the Middle (MitM) phishing attacks show how threat actors find ways to get around traditional defenses and advice.
MitM phishing attacks are a state-of-the-art type of phishing attack capable of breaking two-factor authentication (2FA) while avoiding many content-based phishing detection engines. Rather than showing a spoofed version of a target login page, a MitM attack uses a reverse-proxy server to relay the original login page directly to the user’s browser.
As of November 2022, several phishing attacks have used MitM tactics to compromise business email accounts and to successfully steal organizations’ confidential information. There are several popular MitM phishing toolkits that make it easy for hackers to launch their own MitM phishing attacks in just a few clicks.
These toolkits are continually expanding their sets of features while simultaneously becoming more intuitive and easy to use. Many already employ sophisticated cloaking techniques, allowing them to evade detection by traditional phishing detection systems. As such, we expect that the prevalence of these MitM phishing attacks will continue to rise in the near future.
Palo Alto Networks customers receive protection from the attacks discussed in this blog through Advanced URL Filtering by blocking MitM phishing pages in real time.
Table of Contents
Introduction: Traditional Phishing Attacks
MitM Phishing Attacks
MitM Phishing Attacks in the Real World
Mid-2022 MitM Phishing Campaign
Late 2022 MitM Phishing Campaigns
Present Day Phishing Activity
Conclusion
Indicators of Compromise
Additional Resources
Acknowledgements
Introduction: Traditional Phishing Attacks
The purpose of a phishing attack is to set up a false login page to trick users into entering their login credentials.
In traditional phishing attacks, attackers will usually create their own phishing page to mimic a legitimate login page. They might host this either on a newly created domain, compromise a legitimate domain and host their phishing page on this domain, or use an existing SaaS platform to host their phishing content.
“Phishing kits” simplify the process of creating and deploying phishing attacks by providing a set of programs and/or scripts that allow even inexperienced cybercriminals to launch their own phishing attacks. These kits often employ templated webpages that mimic targeted companies’ actual login pages. Web-based phishing-as a-service (PhaaS) platforms such as Caffeine (shown in Figure 1) and Robin Banks go one step further by providing easy-to-use interfaces that allow threat actors to configure and deploy phishing attacks.
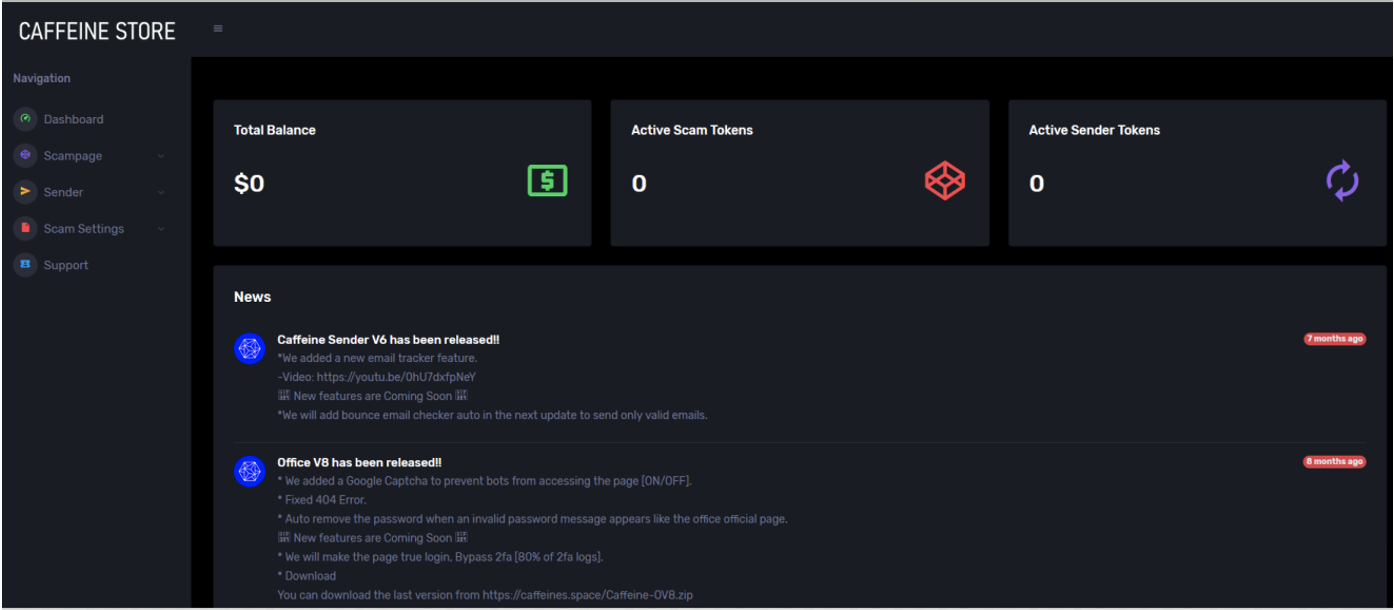
In traditional phishing attacks, the phishing page is typically hosted directly on the malicious or compromised server, and might not necessarily be a perfect replica of a legitimate login page. For example, if an attacker were to create a phishing page mimicking a GitHub login, they might not care to recreate all the various other features surrounding the core login feature, such as the “Forgot My Password” link.
An expert or careful observer might be able to notice subtle discrepancies between the legitimate GitHub login page and the spoofed phishing page and realize that the spoofed page is illegitimate. Figure 2 shows an example of how phishing pages can differ from the original target login page.
Similarly, automated content-based phishing prevention engines might notice that these illegitimate login pages contain signs of suspicious content (such as broken links or misspellings) and flag them as a possible phishing site.
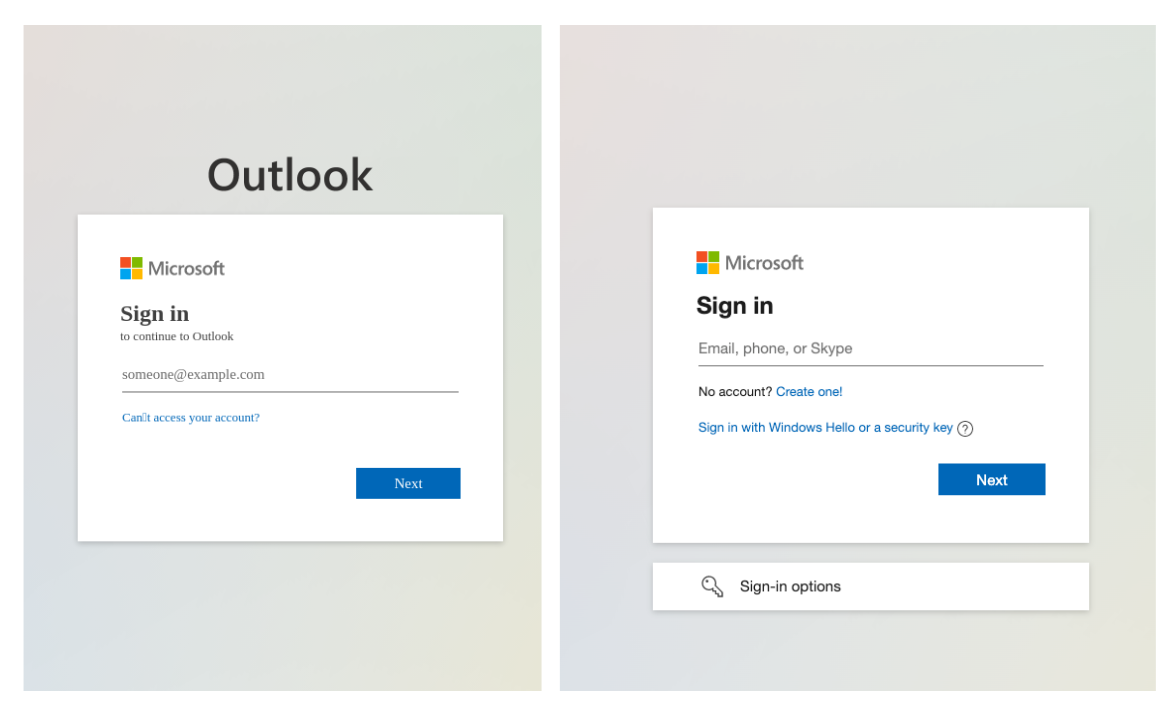
Even with these flaws, the sheer number of recipients in these phishing campaigns mean that some targets could still fall victim to these attacks. Two-factor authentication (2FA), aka multifactor authentication (MFA), has become an increasingly popular way of adding an additional layer of security to protect against successful phishing attacks.
An example of 2FA in action is when, in addition to requiring a username and password, a legitimate login site also requires an additional form of authentication such as a one-time password (OTP) sent to the user’s registered email address. Even if an attacker were to gain access to a victim’s username and password via a successful phishing attack, they would not be able to log in as that user, because they would not be able to retrieve the OTP that would be sent during the malicious login attempt.
MitM Phishing Attacks
MitM phishing attacks are a new type of phishing attack that bypasses both content-based defenses and 2FA. Unlike traditional phishing attacks, which show a separate but spoofed version of a legitimate login page, MitM attacks show the user the exact same content that they would see on the legitimate login page. Instead of hosting a replica of a legitimate login page, MitM servers simply take the content rendered on the legitimate site and relay it to the end user, as shown in Figure 3.
In other words, MitM servers act as a proxy between the target and the legitimate login page. When the target enters their credentials into the proxied page, the MitM server stores the credentials away and forwards them to the legitimate login page, resulting in a successful login attempt. From the victim’s perspective, everything appears as if they had logged in to the legitimate page itself.
Furthermore, both connections (MitM server to legitimate site, and victim to MitM server) are served via the HTTPS protocol, so the victim will see that the connection is “secure” according to the padlock icon in the web browser’s address bar.
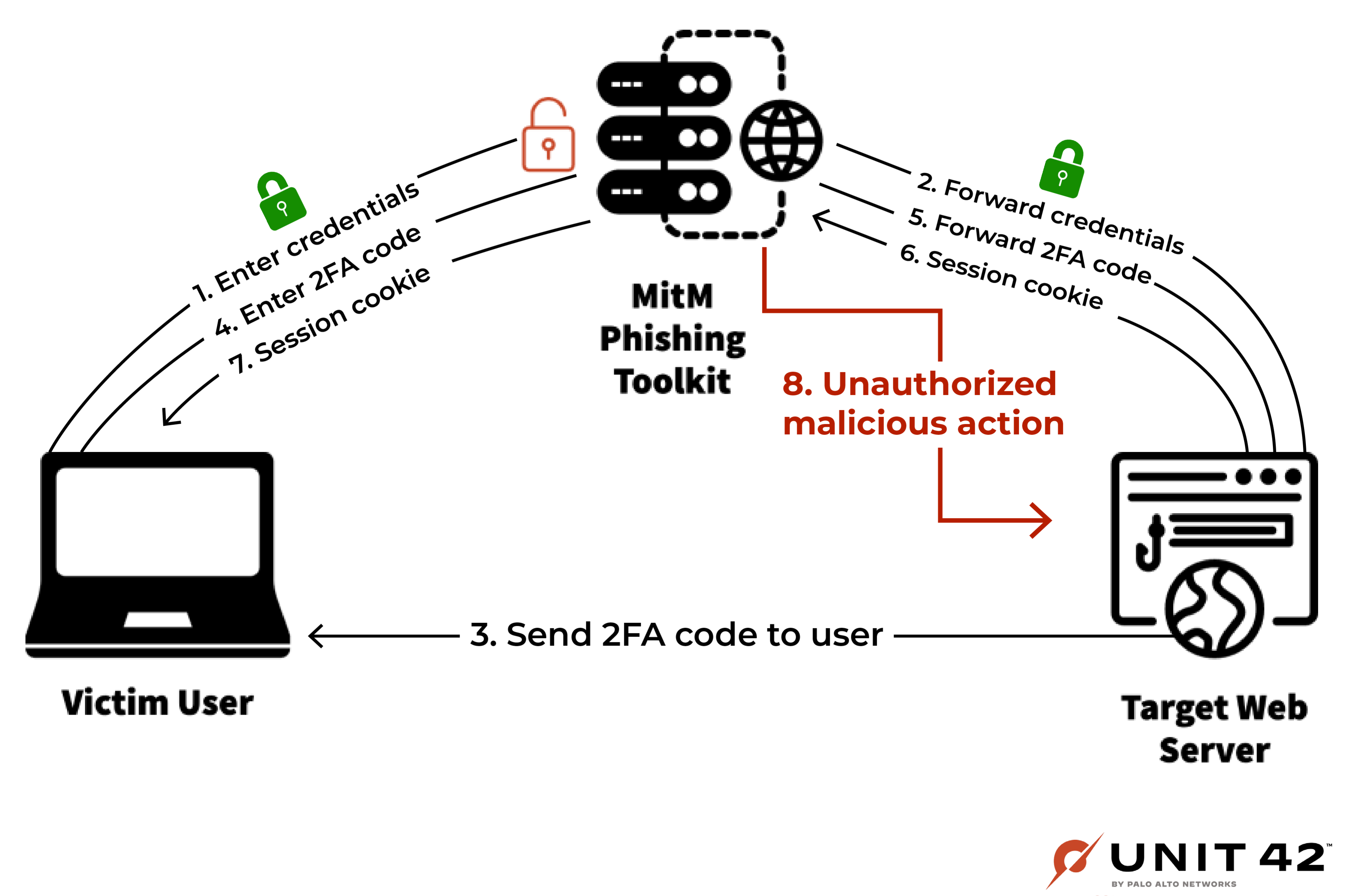
Since the content shown to the target is exactly the same as the content that they would see on the legitimate login page, this proxy-based approach makes it much harder for victims to visually discern that something suspicious is happening, and makes it very difficult for content-based phishing detection engines to notice anything suspicious.
To use a painting as an analogy, we can consider a traditional phishing attack to be like looking at a (potentially sloppy) replica of a $20 million Van Gogh painting made by a fraudulent artist. A MitM phishing attack is like viewing the original painting via a well-hidden mirror.
MitM attacks have several other benefits in addition to cosmetic ones. For example, if the user has 2FA set up, this proxy-based approach allows the MitM server to automatically bypass this 2FA as well.
After the MitM server forwards the username and password to the legitimate site, the legitimate site will then follow its normal behavior of sending an OTP to their client. The target – if tricked – will then input the one-time password into the MitM phishing page. This allows the MitM server to relay the password to the legitimate site, thereby fully completing the login attempt.
At this point, the MitM server would receive a real session cookie from the legitimate site. This persistent login allows the victim to continue to browse the site apparently as normal (though still via the attacker’s web server), further perpetuating the phishing attack’s air of legitimacy.
MitM Phishing Attacks in the Real World
At the time of writing, there are several tools that make it easy for hackers to deploy their own MitM phishing attacks in just a few clicks. Similar to traditional phishing kits, these MitM phishing kits provide a set of scripts – or in some cases, even graphical user interfaces (GUIs) – that make it easy for attackers to configure and launch MitM phishing attacks.
In Table 1, we introduce some of the more popular MitM phishing kits available at the time of writing. Each of these kits employ the core tactic of relaying the original login page to the victim’s browser, but they differ in their implementation details and additional features (e.g., cloaking and TLS certificate generation).
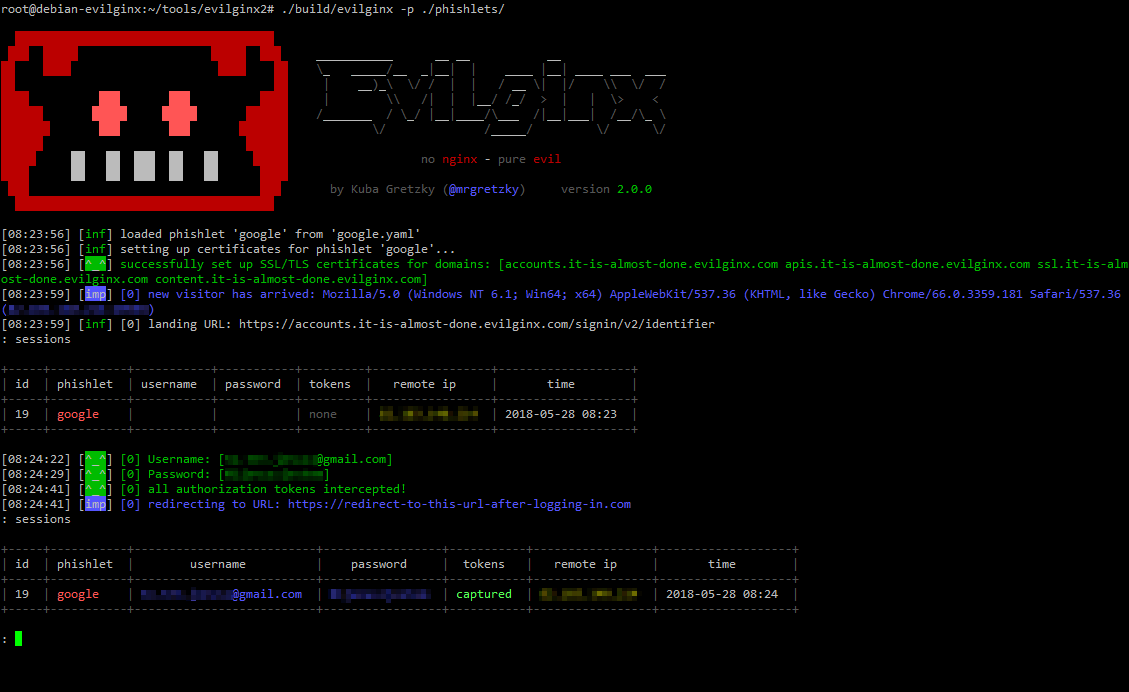
For example, Evilginx2 generates unique tokenized URLs (aka “lures”) that must be directly visited to show the phishing content. Requests to any other path result in a redirect to a benign site.
| Name | First Released/Reported | Description |
| Evilginx2 | July 2018 (first version released May 2017) | Feature-rich MitM phishing kit with an easy-to-use command-line interface. Has cloaking features built in. Generates unique tokens (lures) that must be present in the URL to reveal the phishing content. The command-line interface for this tool is shown in Figure 4. |
| Modlishka | January 2019 | Automates several configuration steps and post-compromise actions, such as launching an instrumented Chrome instance with the stolen session cookie. |
| Muraena | May 2019 | Barebones MitM toolkit. Unlike some other toolkits that automatically create TLS certificates, Muraena requires the attacker to provide their own certificate. |
| EvilnoVNC | September 2022 | Uses a real web browser to render the login page on the attack server, and serves the content to the victim’s browser via VNC. |
| EvilProxy | September 2022 | Phishing-as-a-service platform for MitM phishing attacks. Provides an easy-to-use GUI for threat actors to set up and manage their own MitM phishing campaigns. |
Table 1. Breakdown of popular MitM phishing kits.
Before this year, MitM-related tactics had already been used to successfully impersonate large software organizations, expose hundreds of millions of users’ personal data, and steal millions of dollars from up-and-coming startups. However, these attacks did not necessarily use phishing per se as their primary attack vector. Now, MitM-based phishing attacks have started to take center stage.
Mid-2022 MitM Phishing Campaign
In July 2022, Microsoft reported a phishing campaign using Evilginx2 to steal targets’ Microsoft credentials. The campaign sent emails to potential victims prompting them to download an important attachment. After opening the attachment and routing through a series of redirects, the victim would arrive at a MitM phishing page like that shown in Figure 5. After the attackers successfully intercept an authentication cookie, they would log on to the compromised Outlook account and continually search for finance-related emails and attachments in order to find opportunities for payment fraud.
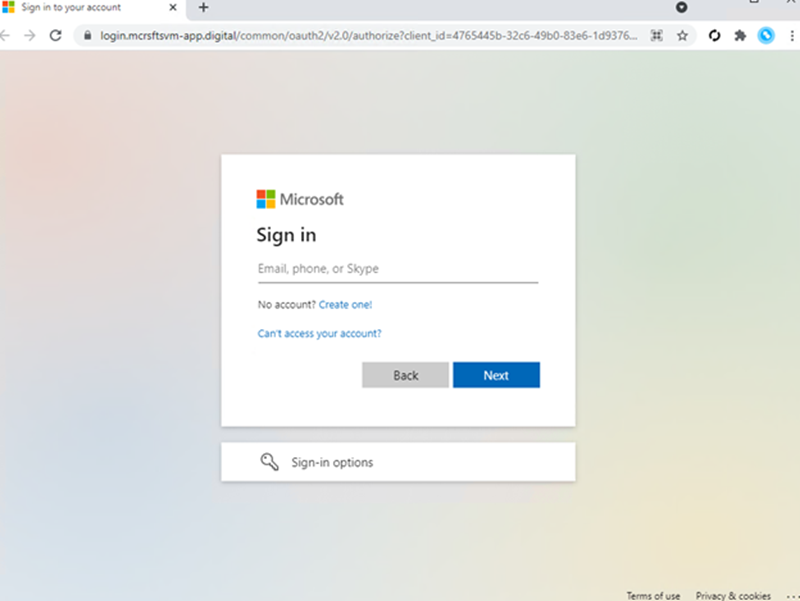
In an attempt to avoid detection, the campaign used a variety of cloaking techniques to ensure that the phishing content would only load if the victim had navigated to the page via the original HTML attachment. By the time Microsoft’s threat intelligence article was published, more than 10,000 organizations had been targeted by this campaign over the span of several months.
According to Palo Alto Networks Advanced URL Filtering logs, our Advanced URL Filtering service had begun blocking web traffic to tokenized phishing URLs hosted on the attackers’ domains (e.g., login[.]mcrsfts-passwdupdate[.]com/HMxVQmxZ) as early as September 2021.
Late 2022 MitM Phishing Campaigns
In September 2022, a separate campaign was found to be using MitM phishing tactics to steal targets’ GitHub login credentials. Several domains were used to mimic a CircleCI login page, prompting victims to log in with their GitHub credentials (as shown in Figures 6 and 7).
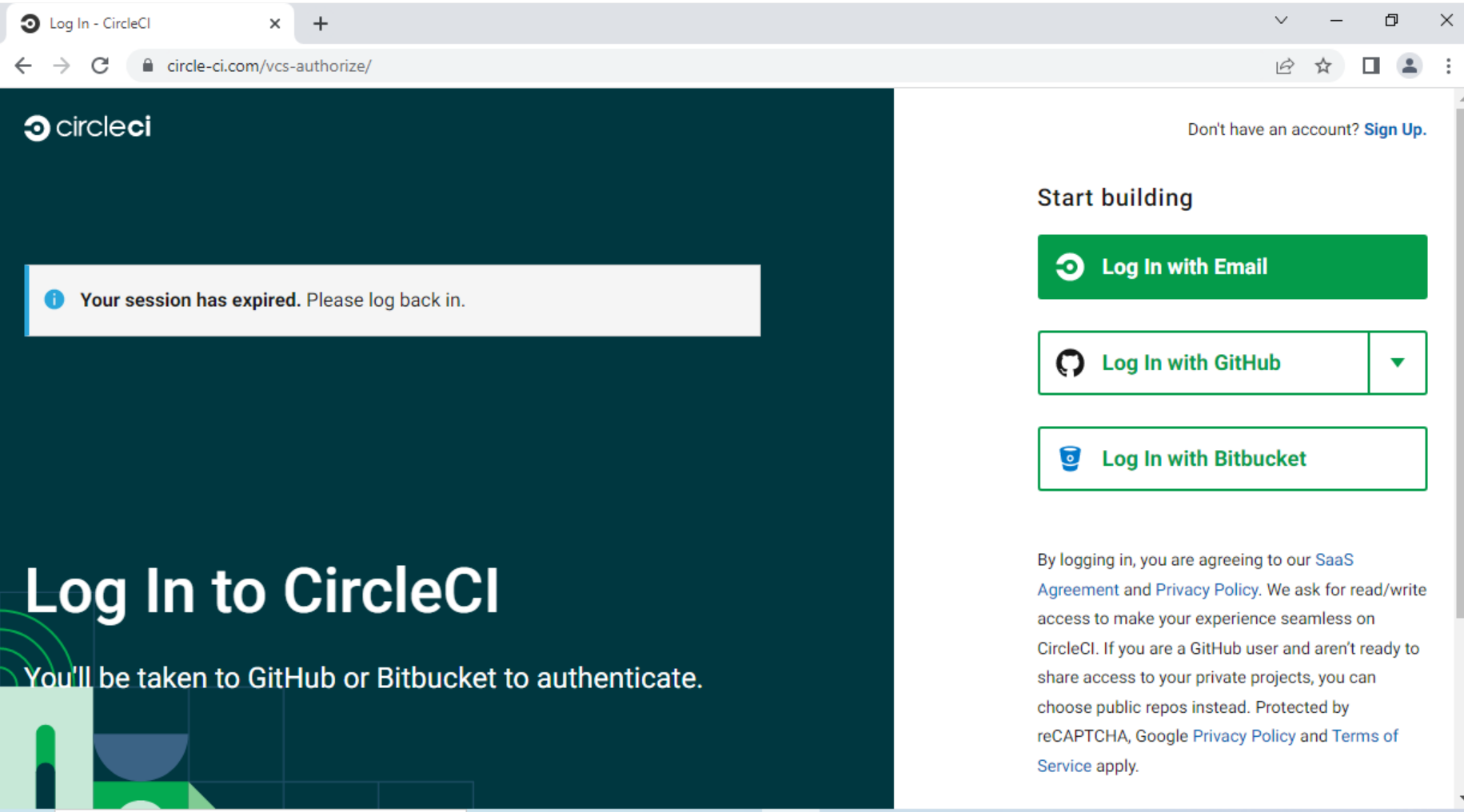
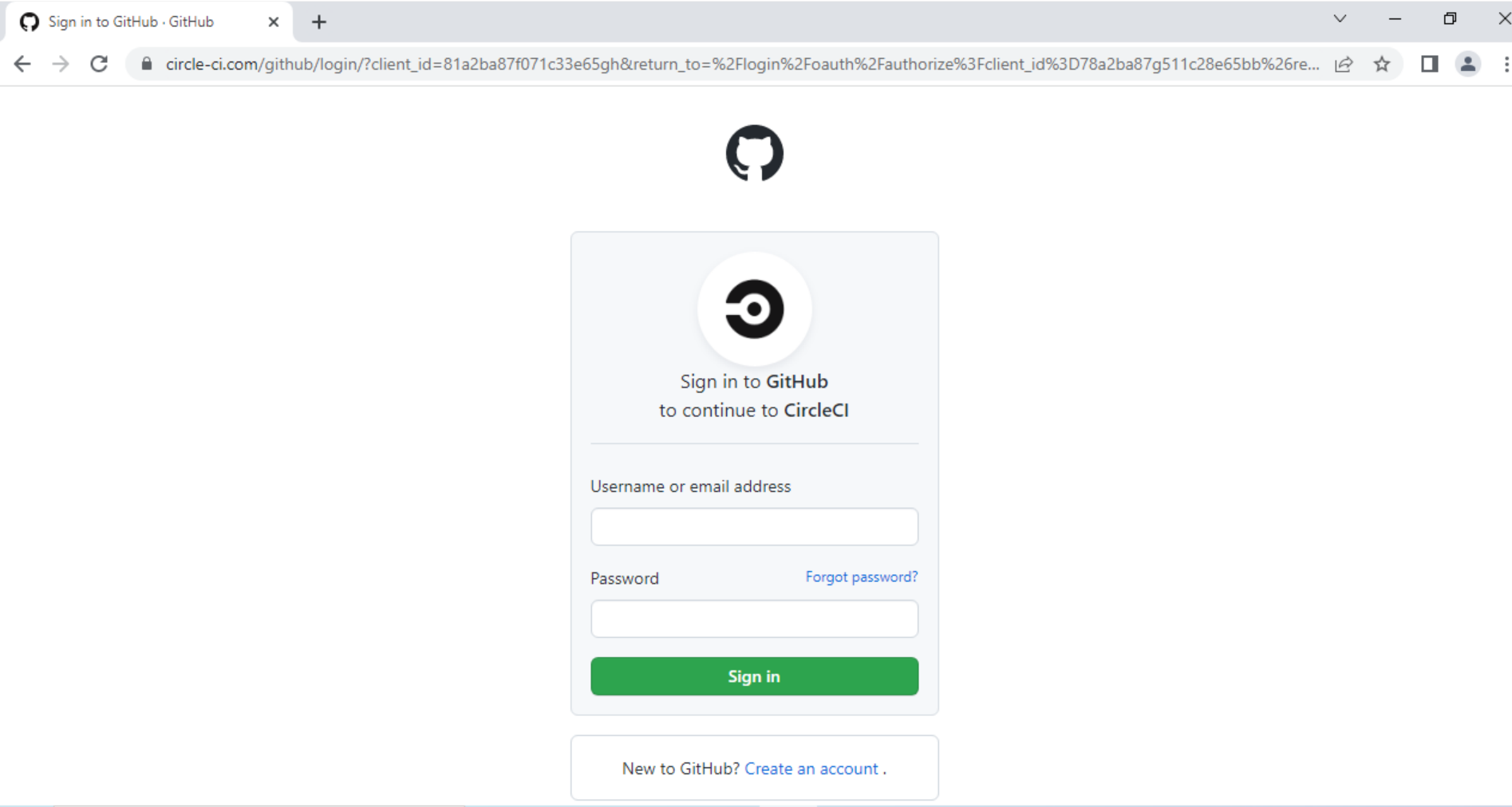
For targets with OTP-based 2FA set up, the MitM server also prompted them to enter the OTP, which was then forwarded to GitHub, allowing for a successful login. From there, attackers would persist in their access by quickly creating personal access tokens (PATs) or adding their own SSH keys to the victim’s account. That way, attackers would continue to have access to the compromised account even if the victim were to change their username and password.
In November 2022, it was revealed that Dropbox had fallen victim to a MitM phishing attack that allowed attackers to compromise and copy 130 private repositories. This shows that these MitM phishing attacks are already making a significant impact in the real world. In Dropbox’s response to this attack, they stated that they plan to move their 2FA protocols from OTP to WebAuthn, which is a more phishing-resistant form of 2FA.
Present Day Phishing Activity
In recent weeks, our Advanced URL Filtering service has been detecting more MitM phishing URLs, with enterprise logins like Microsoft 365 being prime targets (shown in Figures 8 and 9).
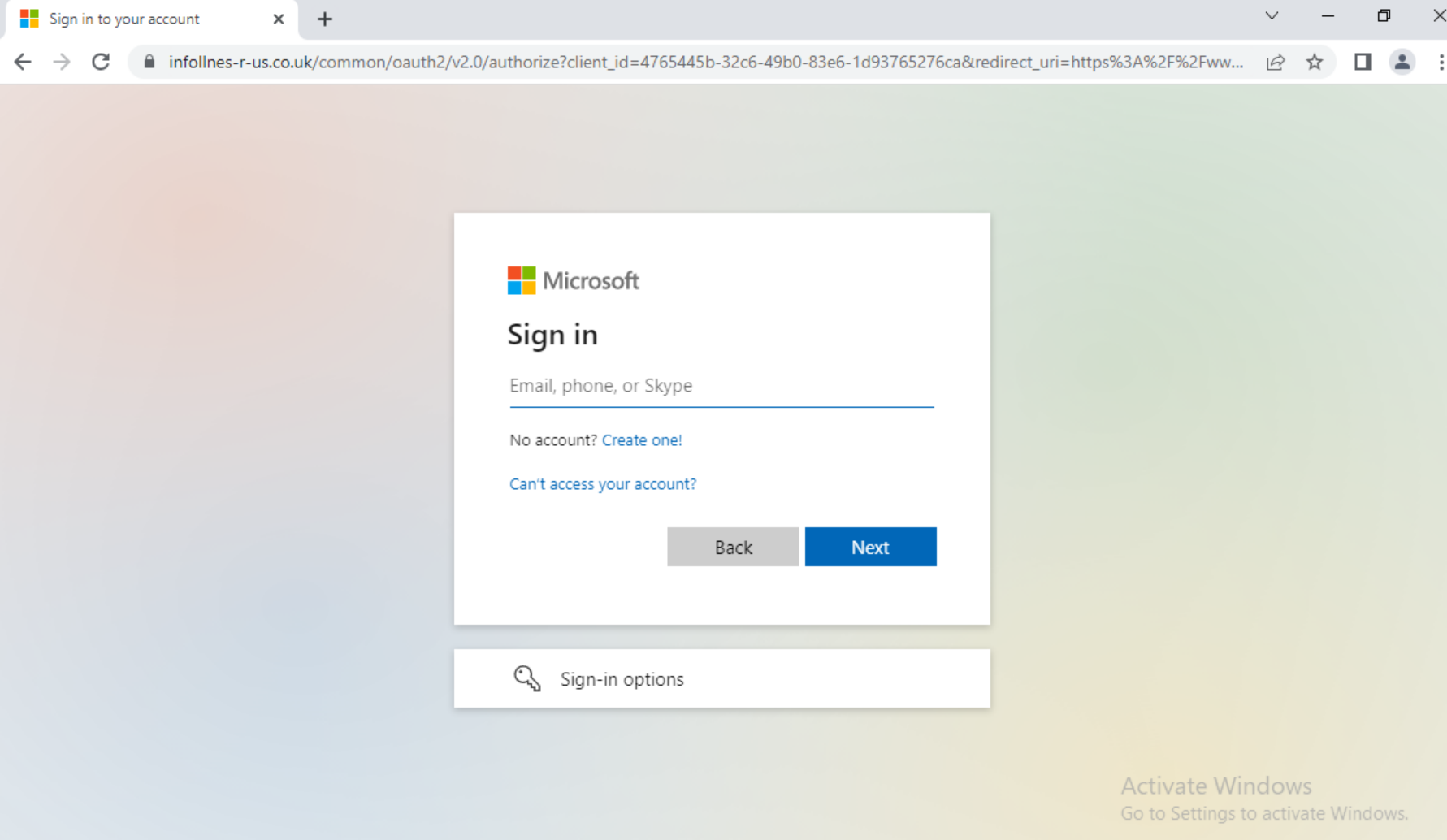
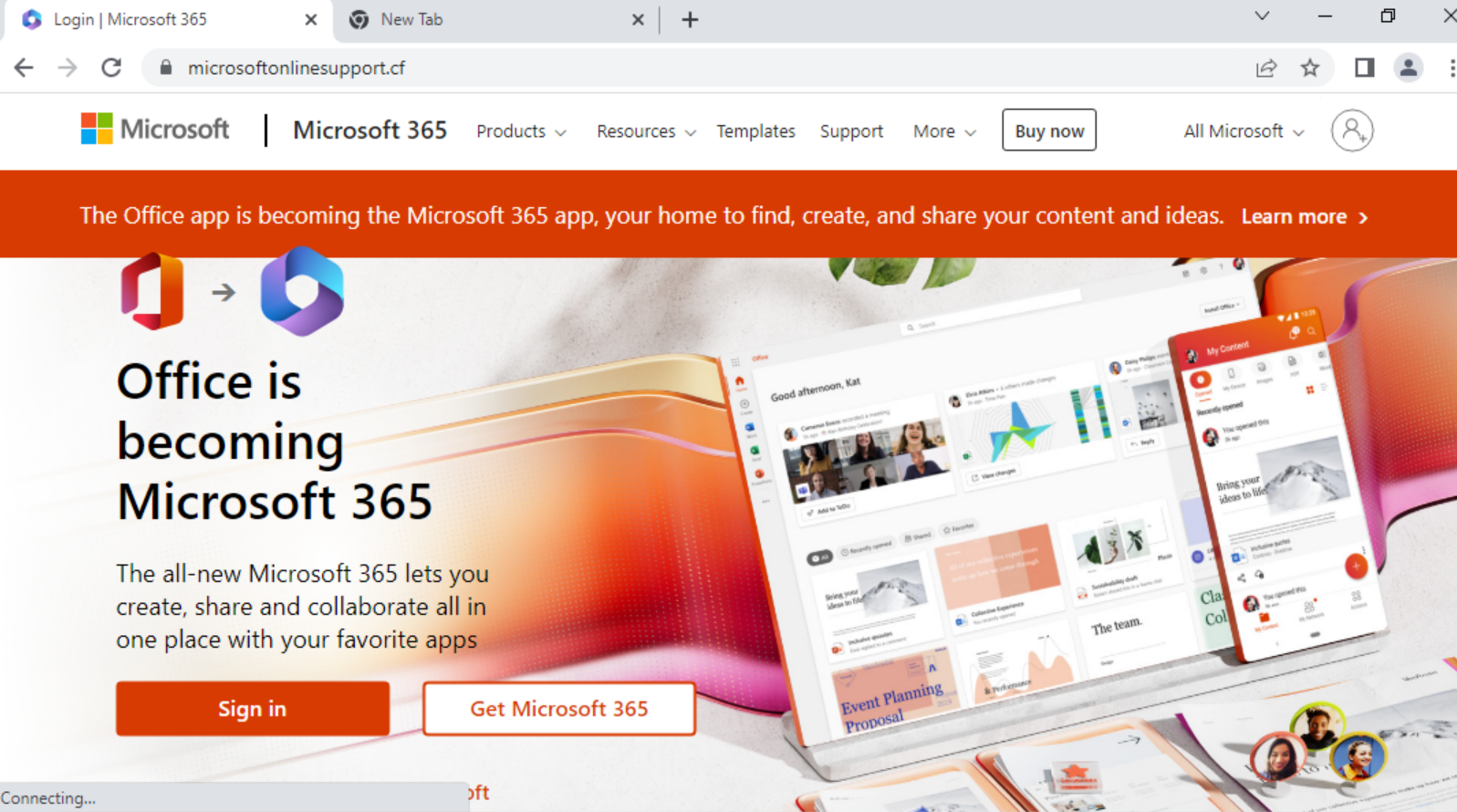
As MitM phishing kits grow in popularity and continue to expand their feature sets, we expect the prevalence of MitM phishing attacks to increase as well. Threat actors are already making strides in this direction. In fact, Evilginx 3.0 is expected to be released in the near future, along with an online course on how to successfully execute a MitM phishing attack.
Conclusion
MitM phishing attacks have already resulted in significant real-world breaches, and are expected to rise in prevalence as MitM phishing toolkits continue to expand and evolve. As such, it becomes increasingly important for organizations to protect themselves from these sorts of cutting-edge phishing attacks.
At the moment, actions that end users can take to protect themselves against MitM phishing attacks include:
- Verifying the validity of a URL before inputting any credentials
(e.g., ensure that a URL is really “github[.]com” and not something like “github-impersonator[.]org”). - Using a password manager to store and enter credentials. If you find yourself on a MitM phishing page hosted on a website that the password manager does not recognize, the password manager will warn you before entering your credentials.
- Using more up-to-date MFA methods, such as hardware security keys or WebAuthn 2FA.
Furthermore, customers who subscribe to Palo Alto Networks Advanced URL Filtering service receive protection from MitM phishing attacks via our in-line phishing URL detection, including the MitM phishing URLs mentioned in this article. Advanced URL Filtering analyzes web traffic in real time to block attacks before they make their way to the target. That way, even if a MitM phishing attack uses cloaked URLs (as is the case with Evilginx2), Advanced URL Filtering can block the attack before credentials are stolen.
Indicators of Compromise
- mcrsfts-passwdupdate[.]com
- circle-ci[.]com
- infollnes-r-us[.]co[.]uk
- microsoftonlinesupport[.]cf
Additional Resources
What Is a Proxy Server
Multifactor Authentication (CISA)
Legitimate SaaS Platforms Being Used to Host Phishing Attacks
Catching Transparent Phish
Acknowledgements
The authors would like to thank Wei Wang and Javier Wang for their guidance in researching for and writing this article.
Updated December 21, 2022 at 1:00 p.m. PT.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
Source: https://unit42.paloaltonetworks.com/meddler-phishing-attacks/
Views: 0