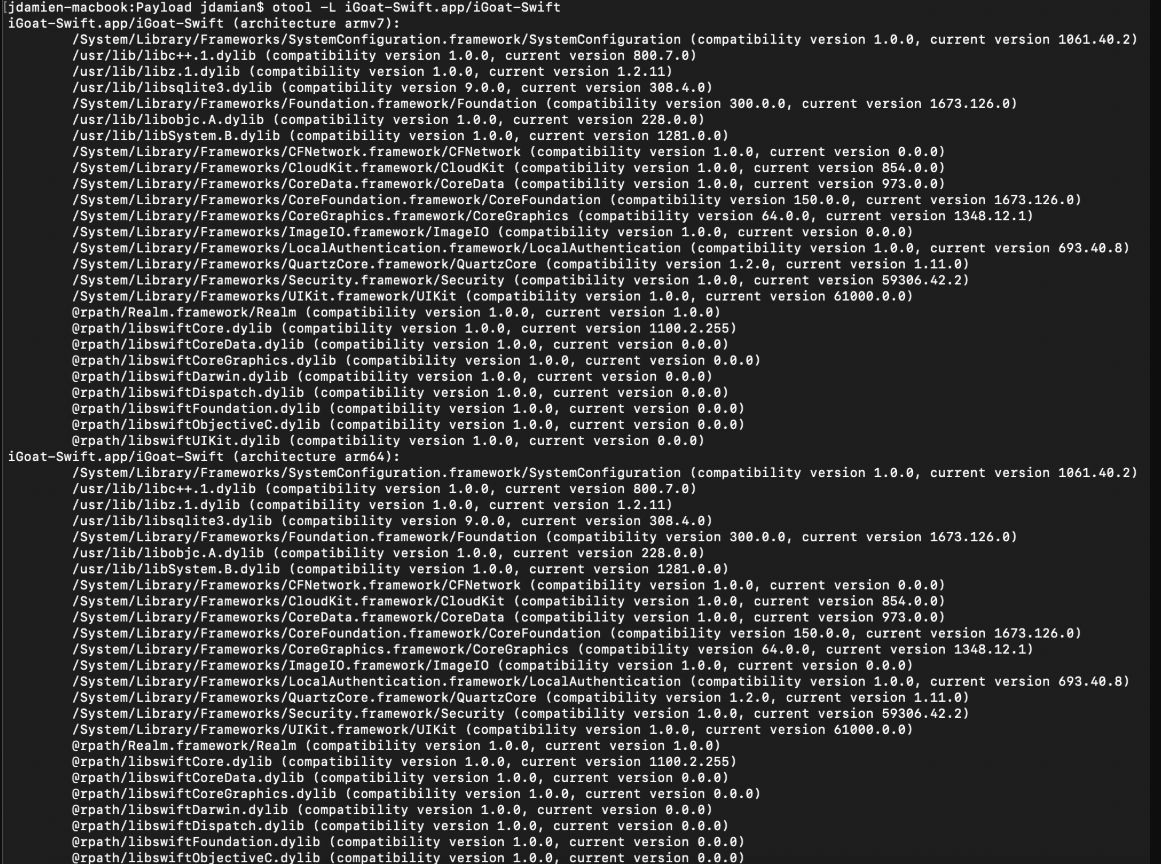
This article explores how otool can be utilized for security analysis of iOS applications. It provides a comprehensive checklist for conducting security checks on iOS binaries to identify vulnerabilities and potential exploits, including inspections of libraries, protections, and system calls. Affected: iOS applications
Keypoints :
- otool is a command-line utility for macOS/iOS, helpful in reverse engineering.
- Security checks include examining linked libraries, PIE support, and stack canary protection.
- It assists in identifying memory management vulnerabilities through ARC checks.
- Examinations for encryption status and protection mechanisms (NX Bit/DEP) are crucial.
- Weak hashing algorithms and using deprecated APIs can be flagged during analysis.
- A script automates the above checks for enhanced efficiency in iOS pentesting.
- Checks for hardcoded strings, excessive app entitlements, and insecure functions are included.
Full Story: https://infosecwriteups.com/mastering-ios-pentesting-with-otool-0803bd65c7ed?source=rss—-7b722bfd1b8d—4