Summary: The content discusses the analysis of a malicious script that downloads a file named dllhope.txt from a Bitbucket repository, which is associated with AsyncRAT malware. It details the method parameters and the reflective loading technique used to execute the payload while evading security mechanisms.
Threat Actor: AsyncRAT | AsyncRAT
Victim: Potential targets of AsyncRAT | Potential targets of AsyncRAT
Key Point :
- The script downloads a file from a Bitbucket repository, which is linked to AsyncRAT.
- Reflective loading is used for in-memory execution, allowing the malware to bypass traditional security measures.
- The ClassLibrary3.dll file contains critical attack functionalities, including persistence and payload execution.
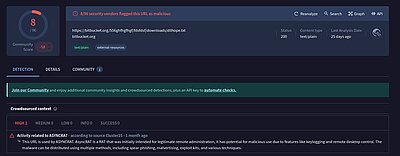
The code (figure 5) downloads a file named dllhope.txt[2] from a Bitbucket repository. It is also worth noting that VirusTotal marked the URLs used by the script to be associated with AsyncRAT (see figure 6).
Opening the ClassLibrary3.dll [3] file in DNSpy reveals the code and the method “ZxKHG” together with the six parameters needed. The passed arguments can be found in the initial script [1].
The method parameters are as follows:
- _5 is a URL to fetch data from the reversed URL
- ‘txt[.]pes4oivne/sdaolnwod/sds/cfrrpiaj/gro[.[tekcubtib//[:spxxh’
- (‘hxxps://bitbucket[.]org/jaiprrfc/sds/downloads/envio4sep[.]txt’)
- eMozMBl holds the full path of the VBScript file
- PdjLvfa is used for naming and creating shortcuts
- UmZbL contains the value ‘1’, likely indicating a configuration setting or feature flag.
- MbmvK was not used by the method at the time of analysis
- RMMYL was not used by the method at the time of analysis
The code section highlighted in Figure 8 is reflectively loaded using [system.AppDomain]::CurrentDomain.Load. This technique allows for in-memory execution, bypassing traditional security mechanisms that use pattern scanning on files. The ClassLibrary3.dll[3] reveals the core functionality of the attack, including persistence mechanisms and the execution of the downloaded payload – AsyncRAT. A flag parameter, UmZbL, dictates how the code will proceed.
Source: https://www.gdatasoftware.com/blog/2024/10/38043-asyncrat-bitbucket
Views: 0