Formbook is a type of malware that specializes in stealing sensitive information from infected systems, primarily focusing on capturing keystrokes, clipboard data, and form data from web browsers.

After downloading and extracting the .bat file, we observed a relatively simple obfuscation technique — Base64 encoding. At the end, there was a large chunk of code that appeared to be a file.
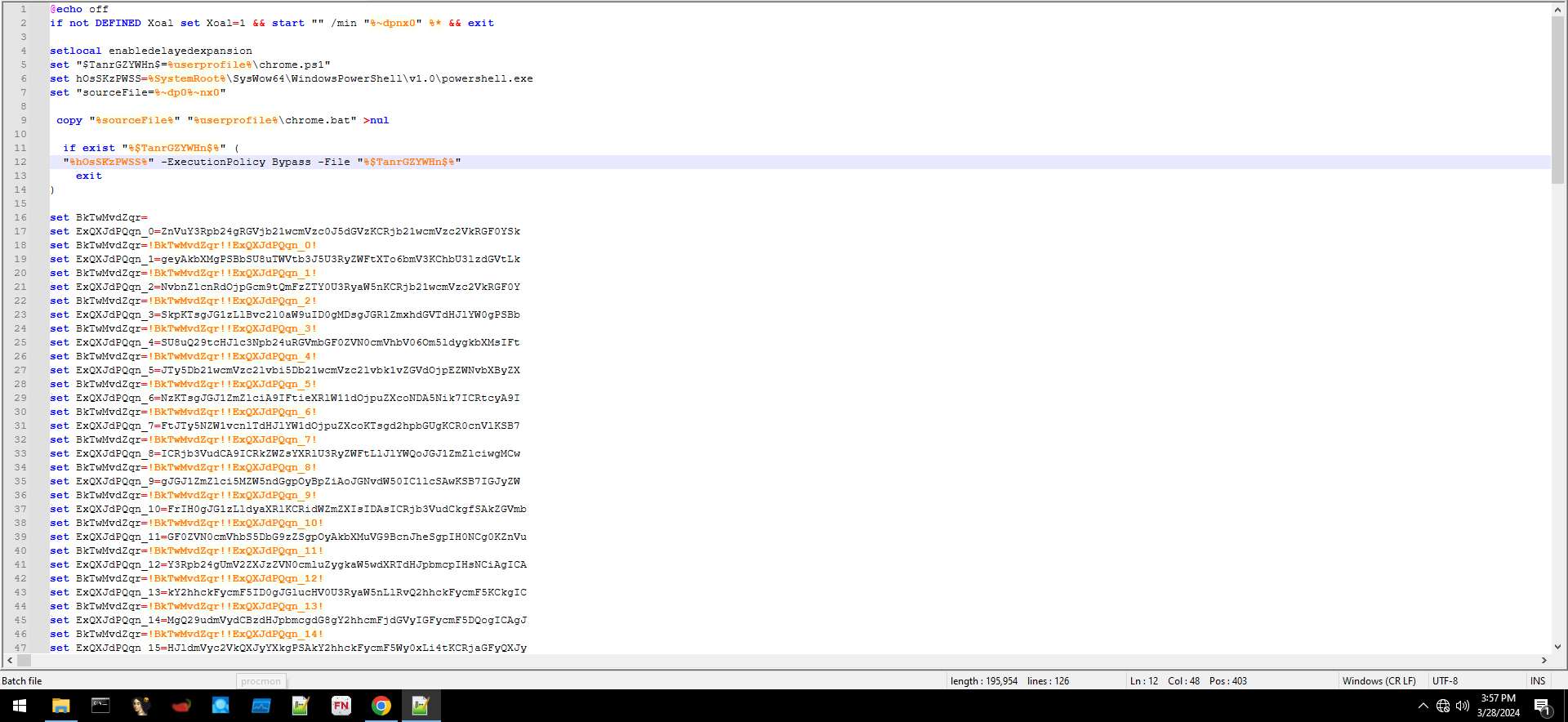
This was easily decoded using CyberChef as shown in Figure 3 + 4.


In the decoded code, we can already observe some manipulation using decompression and reversal. Therefore, I decided to use this technique on the code at the end of the script, as shown in Figure 5.

After extracting the new EXE file, I used DIE and found that it is written in .NET, which means we can further investigate it using dnSpy.

While debugging the new file, it was observed that a new array is being created and used. This array had the magic header ‘4D5A’, which indicates the presence of another new EXE file that is being used or created, as shown in Figure 7.

After further analysis, it was seen that there were actually two files (arrays) being created with this header. I decided to dump those arrays to new files for further investigation.


We can use PEStudio for quick and precise analysis. As shown in Figure 9, we can see that we are dealing with the actual malware and its DLL.


While debugging this new and final staged malware, it was observed that it is using a lot of keylogging techniques and sending information to the attacker. For example, system information and public IP are being sent, as shown in Figure 10.



At the end, I managed to extract the malware configuration, as shown in Figure 11. These details are essential for the malware to work properly and contain sensitive data such as Smtp sender, receiver and password.

IOC:
- 463b92101e5f2912781dd6eb61374b97f14fb27b6fe05c0ef3fb734d8ef4d4ec.bat — 2effd68ca29fb310fbe40749eb566d0e
- output.exe— 56e3f56dda234344fb2799c10727e642
- array2.exe — f362f6f1dd0d9521752008cb1789a699
- array.dll— cbd924de2846331d88a342757c53fe08
- mail[.]agagroup[.]lv
- info@agagroup[.]lv
- remiset@remisat[.]com[.]uy
- hxxps://api[.]ipify[.]org
In summary, Formbook is a powerful malware focused on data theft through keylogging and information exfiltration. My analysis revealed its obfuscation methods, exposing a .NET-based executable that deploys the malware and its DLL. Furthermore, I successfully extracted the malware’s configuration.
https://medium.com/@b.magnezi/malware-analysis-formbook-d88de50f5977
MITRE Techniques and Procedures:
T1566.001 – Phishing: Spearphishing Attachment: Formbook is distributed through a .bat file that is likely delivered via a phishing email attachment.
T1027 – Obfuscated Files or Information: The malware uses Base64 encoding to obfuscate its payload within the .bat file.
T1140 – Deobfuscate/Decode Files or Information: Formbook decodes the obfuscated Base64 content to extract the executable payload.
T1059.003 – Command and Scripting Interpreter: Windows Command Shell: The initial .bat file is a Windows batch script used to execute the malware.
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder: Formbook may use registry run keys or the startup folder to achieve persistence on the infected system.
T1056.001 – Input Capture: Keylogging: Formbook captures keystrokes to steal sensitive information such as credentials.
T1113 – Screen Capture: The malware may capture screenshots to gather additional information from the victim’s system.
T1071.001 – Application Layer Protocol: Web Protocols: Formbook uses HTTP to communicate with its command and control server and to send stolen data.
T1573.001 – Encrypted Channel: Symmetric Cryptography: The malware may use symmetric encryption to protect the data it exfiltrates.
T1082 – System Information Discovery: Formbook collects system information to send to the attacker.
T1590 – Gather Victim Network Information: Formbook gathers the public IP address of the infected system.
T1567.002 – Exfiltration Over Web Service: Exfiltration to Cloud Storage: The malware may exfiltrate stolen data to a cloud storage service controlled by the attacker.
Views: 4