“Malverposting” — With Over 500K Estimated Infections, Facebook Ads Fuel This Evolving Stealer Campaign
By Nati Tal (Guardio Labs)
Malverposting, the use of promoted social media posts and tweets to propagate malicious software and other security threats — is on the rise. One of those campaigns, linked to a Vietnamese threat actor, has been ongoing for months now gaining more traction lately using resilient deployment techniques and is estimated to surpass 500k infections worldwide so far. Yet, the initial enabler for those numbers is the abuse of Facebook’s Ads service as the first stage delivery mechanism responsible for this mass propagation.
In this post we will uncover the overwhelming numbers behind Malverposting, as well as dive deeper into this one campaign using adult-rated click bates delivering sophisticated malware — making it even harder for detection, and too easy to mass propagate.
Update 26th April 2023: On initial detection, we’ve shared the details and worked together with Meta’s engineering and research teams who were super responsive, taking immediate actions to stop the propagation of this campaign in their ad network.
The Unstoppable Malverposting Continues
Abuse of advertisement networks and services is unfortunately no news. It seems like we got used to promoted-search results in Google propagating malware as well as sponsored posts on Facebook delivering everything from financial scams, and fake clothing stores to malicious “ChatGPT” branded Chrome extensions.
Yet, every once in a while it peaks in a way you just can’t overlook. Here at Guardio, we monitor and protect from online threats of all kinds. Some of those are propagating with what we call “Malverposting” — Social-media delivered threats that gain traction using paid promotion. In other words, threat actors pay for ads that amplify their malicious posts, thus abusing the enormous delivery power (as well as reputation) of Facebook, Twitter, and other social platforms to pinpoint targets and deliver malicious content directly to their screens.
Below are some examples of how those attacks start with posts people see, some containing baity content and some masquerading as legitimate services or discounts — all fake and leading to scams or malware installation.
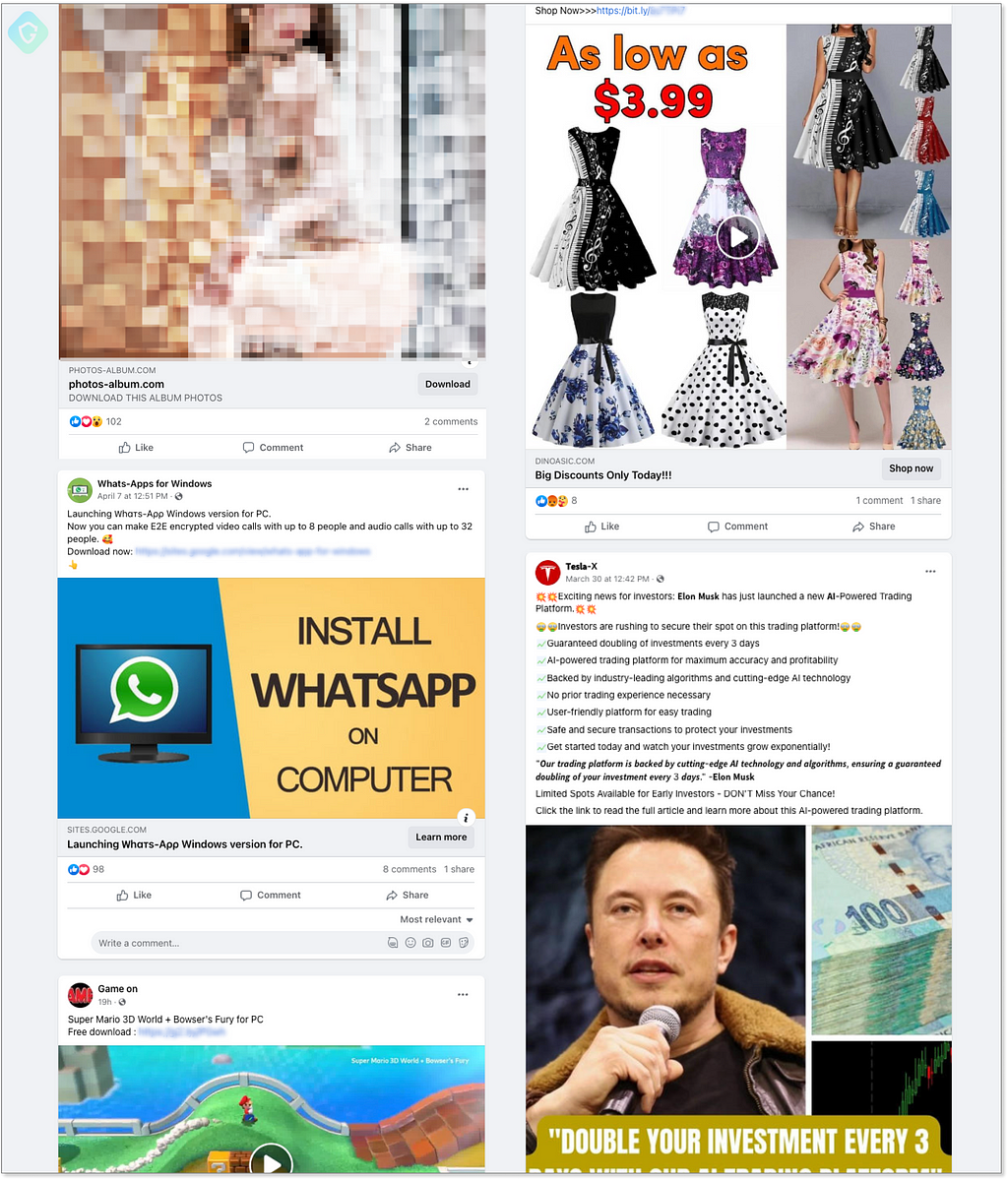
A Vietnamese Originating Malverposting Campaign
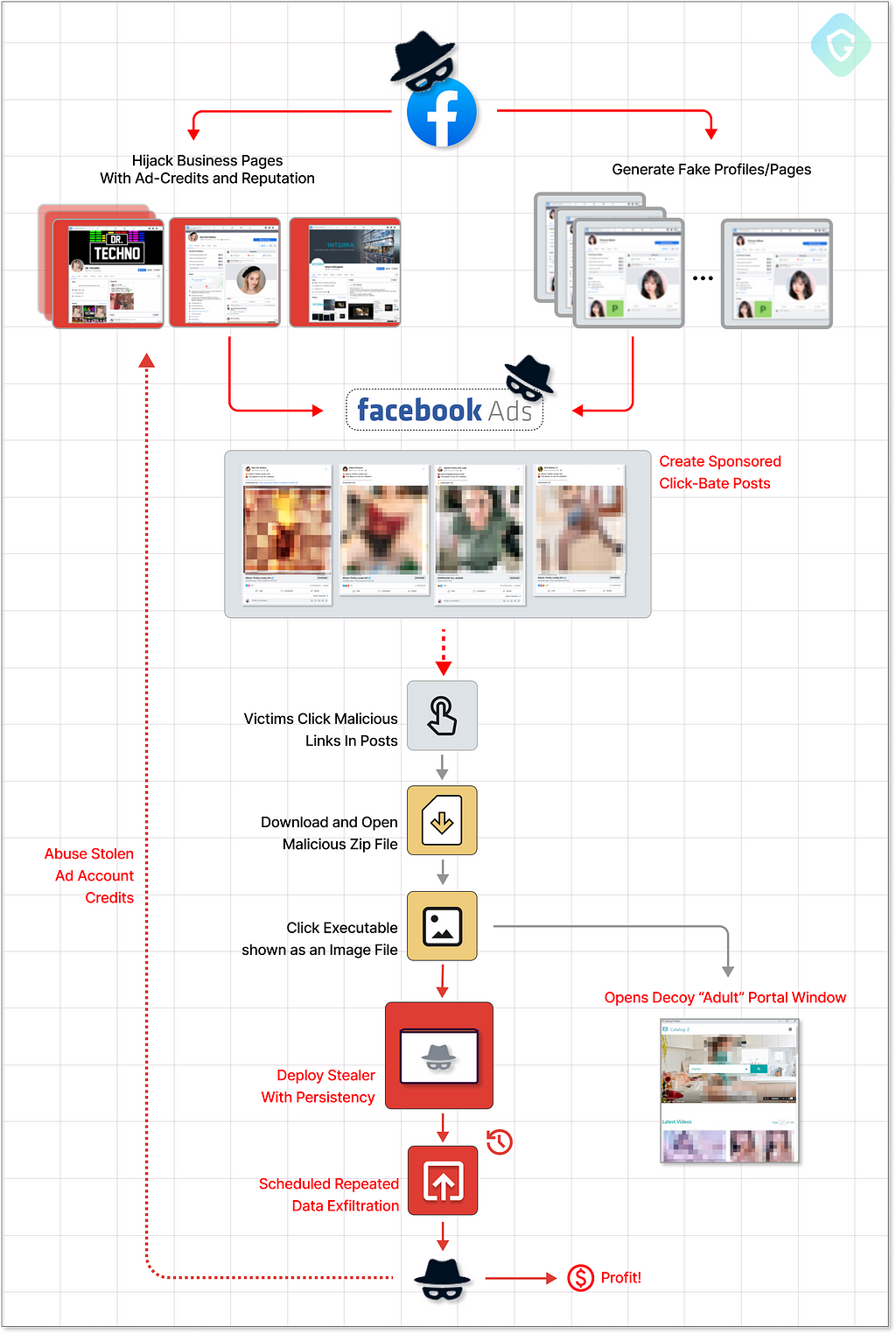
One specific threat actor is doing the extra mile lately, in a data-stealing campaign that started a few months ago and continues to evolve and evades detection with novel techniques — yet, propagates in the same “old-fashioned” way — Malverposting on Facebook by the masses.
This threat actor is creating new business profiles, as well as hijacking real, reputable profiles with even millions of followers (and probably some cash credits left in their advertisement account), and quickly bombards people’s Facebook feeds with malicious click-bates promising adult-rated photo album downloads for free:
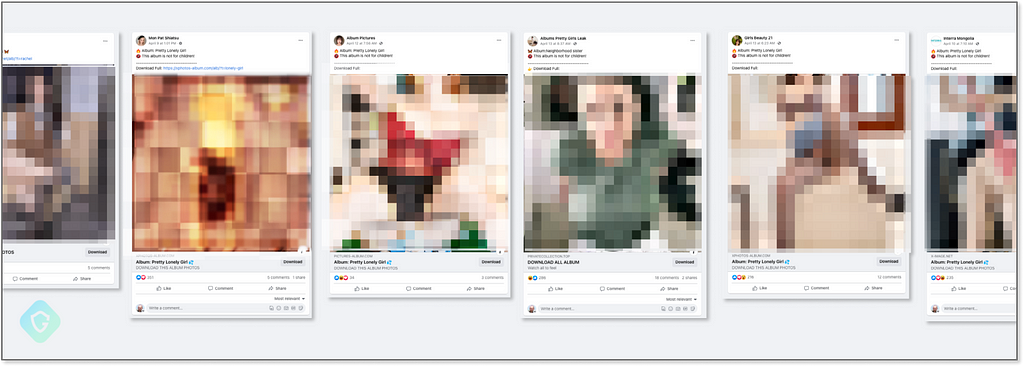
Once victims click on those posts/links, a malicious ZIP file is downloaded to their computers. Since the “intent” of the user is relatively high because of the baity content, many proceed to extract the Zip file content:
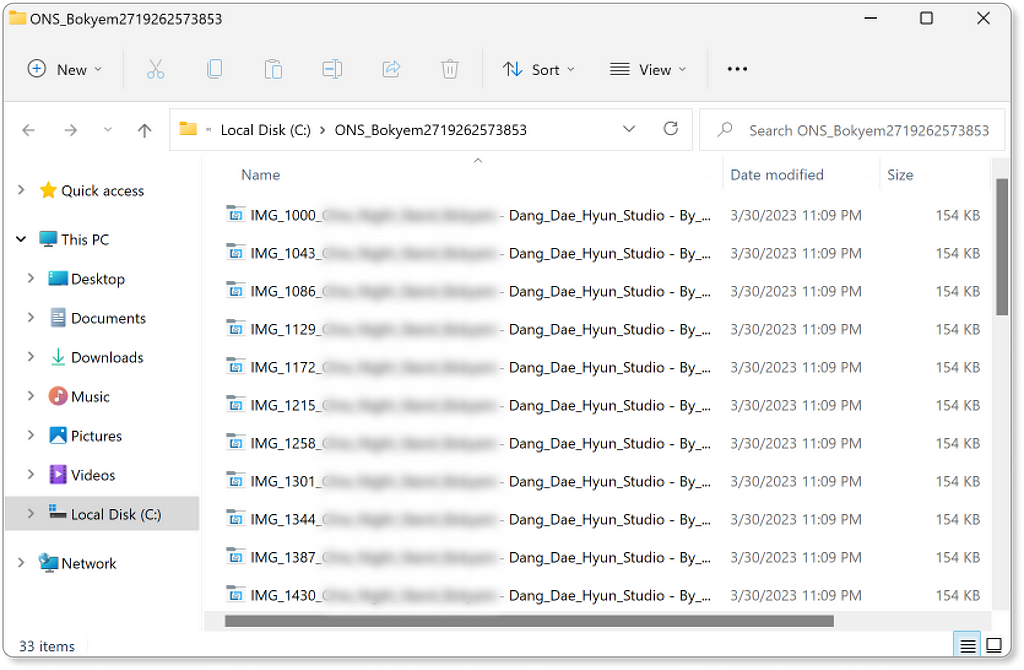
Inside are photo files (that are actually masqueraded executable files) that when clicked will initiate the infection process.
To let the user feel everything is “in order”, the infecting payload opens a browser window popup with a decoy website showing content from a similar genre, while in the background the stealer will silently deploy, execute and gain persistency to periodically exfiltrate your sessions cookies, accounts, crypto-wallets and more.
Damage And Origin
Some of the Facebook accounts targeted by this malverposting campaign belong to business owners. When their details are compromised, the attacker hijacks their account to leverage the business’s reputation, following their advertisement account (which sometimes still holds funds).
The attacker assumes the identity of the business and branches out to propagate more bad ads through this account.
Not only this amplifies the reach, hurting new users, it completely halts the legitimate business activity of reputable brands and stores that may have been building their accounts for years. Here are some examples of an IT company, a shoe store, and a music artist's Facebook business profiles that were hijacked as part of this campaign:
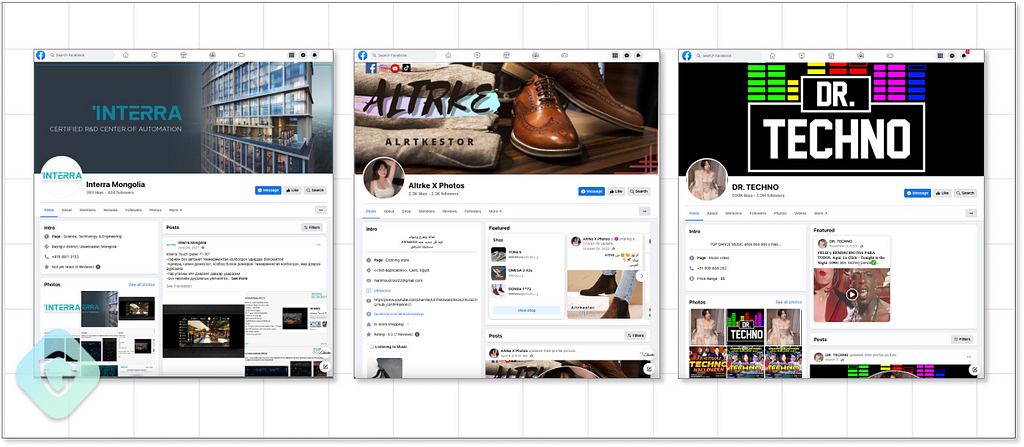
One of the above examples is a hijacked business page of a Techno music artist from Peru with 1.3M followers (Dr. Techno). This one specific post also unintentionally reveals a possible clue to the origin of the threat actor (as also suggested by past analysis of this campaign) — Vietnam:
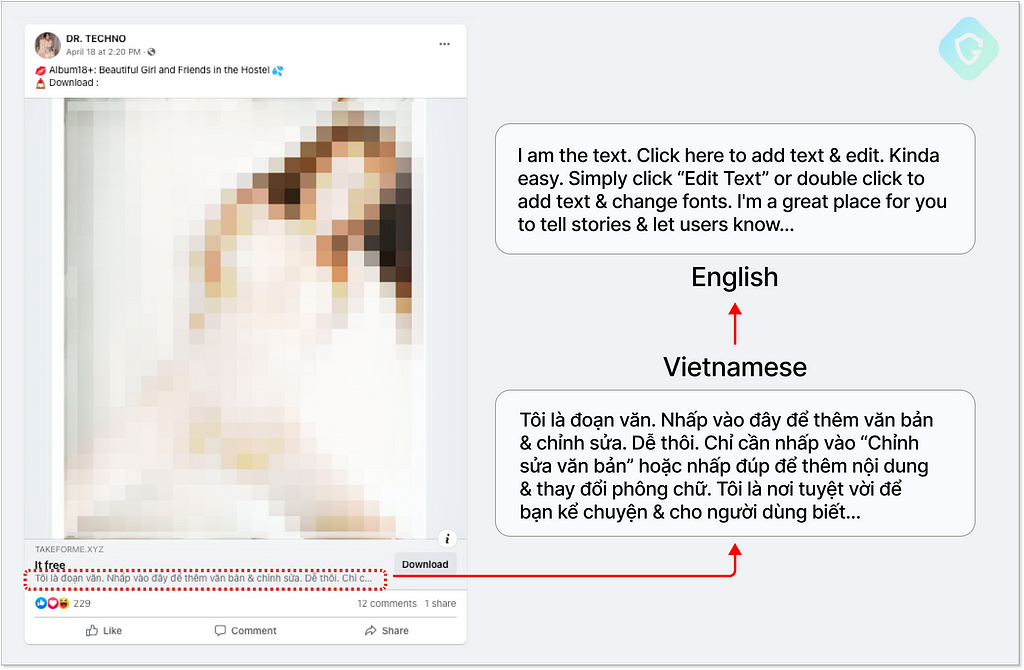
Although those posts are, to say the least inappropriate, this campaign still escapes Facebook’s detection and content control and seems to be on the rise in the last weeks with new records of social presence as well as infection rates.
Furthermore, on the subject of detection, the malicious payload dropped from the posts, also evolves along the way and does a decent job of evading top-of-the-line protection methods like AVs and End Point Detection tools with its very sophisticated deployment techniques using DLL sideloading, code encryption as well as other concepts (more on that later on).
Malverposting By The Numbers
Looking at the numbers behind this specific campaign reveals the scale and efficiency Malverposting can quickly gain. With APIs from Facebook as well as web automation tools — threat actors can automate the entire process and scale it even further.
For reference, here are some key numbers from this operation of the last 14 days — remember that this operation is up and running for months now using similar techniques to propagate:
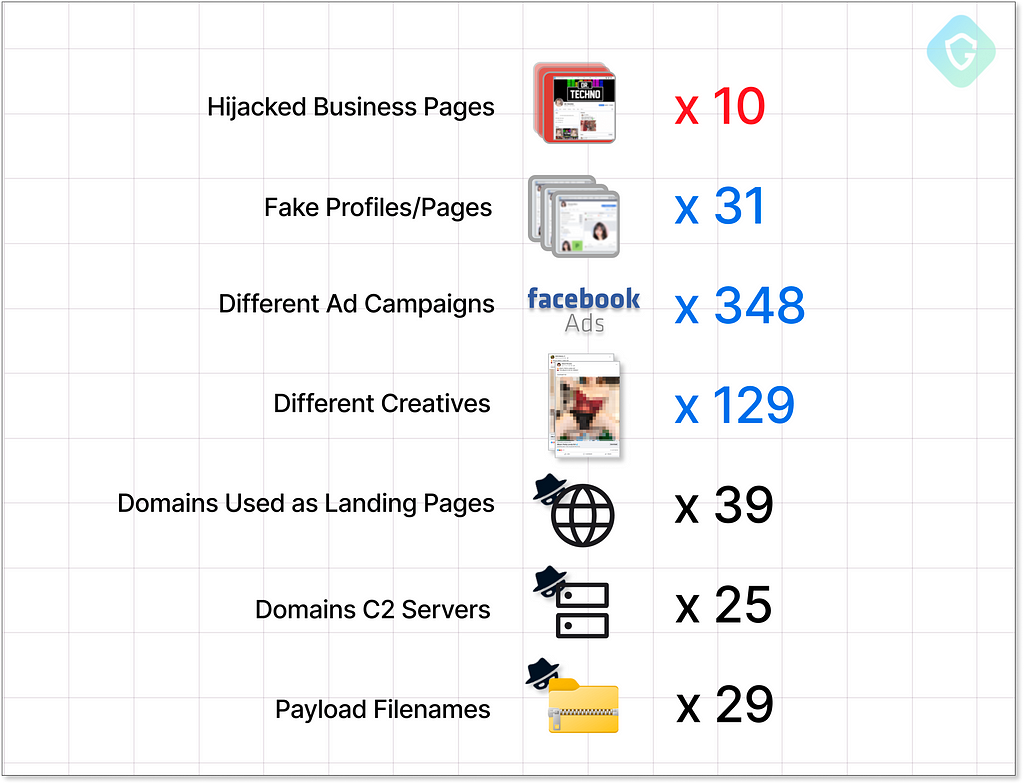
Note how the basic operation is always sustainable using newly generated profile pages, mostly as “Photographers” business accounts that serve only one thing — malverposting for adult content under the radar of Facebook policy enforcers. Adding the ability to target other genuine business account owners — the campaign levels up by fueling itself with better coverage, reputation, and of course advertisement credits stolen from others. They don’t even need to change anything on the hijacked page — it can continue as usual — in most cases, the only thing changed is the profile pictures as it is visible on the promoted posts next to the channel name.
With the above, this campaign reaches 500k+ deployments in the past 3 months only. The reputation and tight integration of Facebook in people’s day-to-day activities give those threat actors very high “conversion” rates:
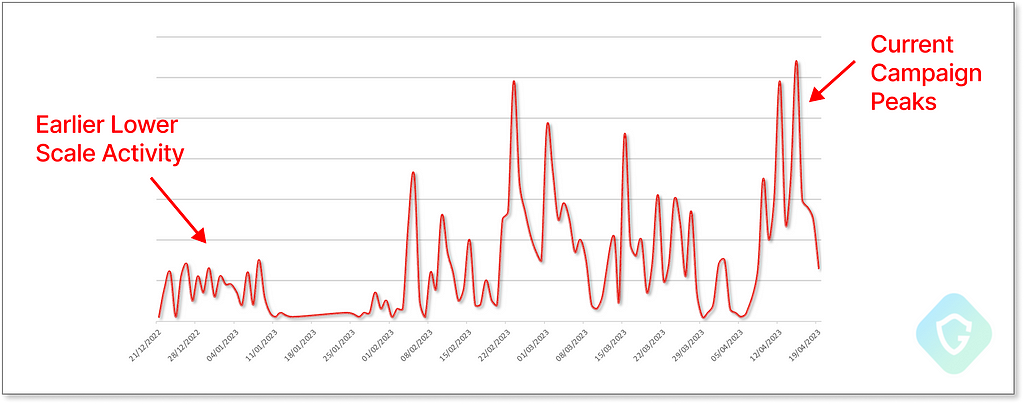
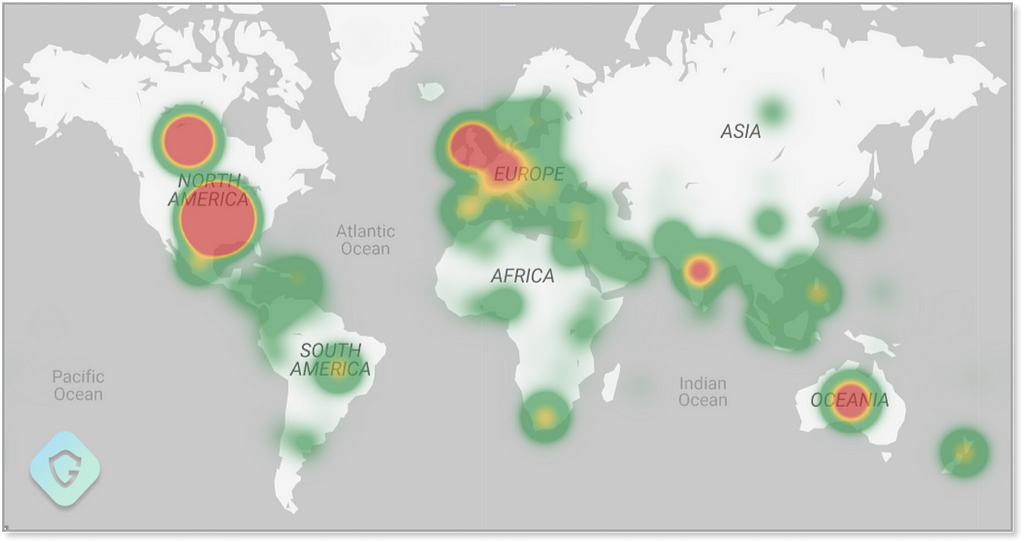
As far as it goes to global distribution, we do see a focus on USA, Canada, England, and Australia — serving as great candidates for gaining more profit, yet the campaign reaches practically every point in the world — at least in the past 3 months of analysis as shown here:
Observed Evolution of The Stealer Payload
Adding to the power of distribution, the malicious payload itself is also quite advanced and unique, using techniques used to be found mostly in APTs.
Following the analysis of our friends at Morphisec and Zscaler, a new variant started to pop up in the last few weeks marking a major leap in detection-evasion techniques. This makes this Vietnamese-originated threat actor’s campaign harder and even more time-consuming to detect by traditional Anti-virus software as well as corporate-grade End-Point-Detection mechanisms.
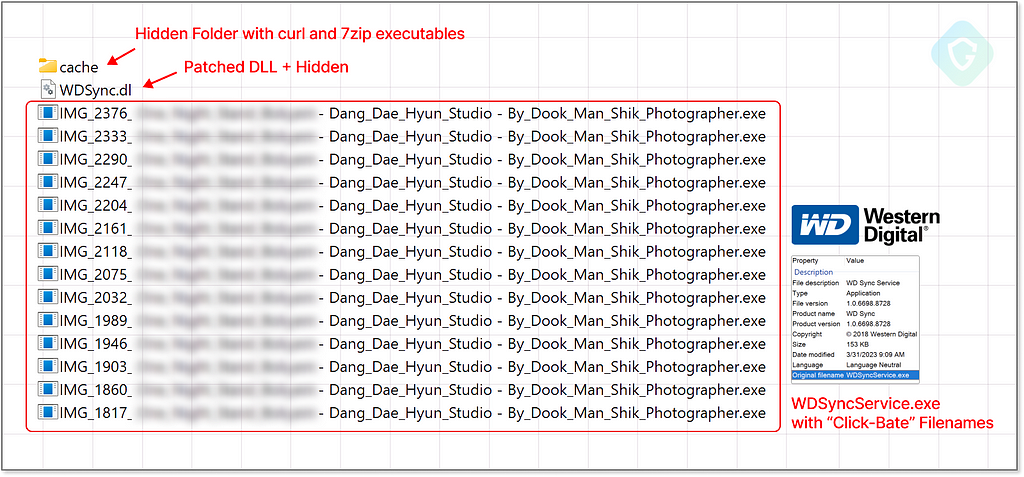
There are several variations of the latest payload, yet all share the usage of a benign executable file that starts the infection flow. The attacker used common system tools from Hard-Drive manufacturers (WesternDigital and Seagate) — executables you will probably find on most desktop systems today — thus making it a legit candidate for a clean verdict from Antiviruses and End Point Detection agents.
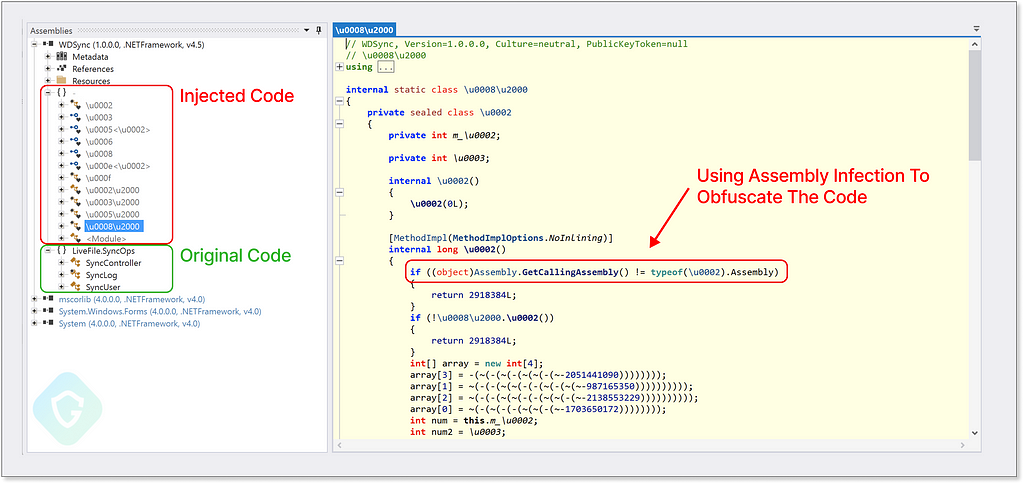
The actual malicious activity is triggered by a sideloaded DLL (also part of the original tool) that was altered to include some obfuscated code to execute the malicious activity once loaded. The original DLL is compiled with .NET technology, and we can see here how decompiling it quickly reveals the added functionality — using assembly and obfuscated strings to further hide itself:
Interesting to see that in one case (a Seagate Toolkit executable) the threat actor actually owned the original source code (or at least part of it) from Seagate — allowing them to easily recompile the specific DLL in need to include their malicious payload. An unintentional mistake of leaving the debug database file (PDB) in the ZIP file gave us these insights into the sophistication of this operation. Also notable is the compilation computer’s user name (“Elon Musk”) which is, of course, made up to not disclose the identity of the attacker:
[...]
*** LINES
** Module: "CommonUtils.EncryptHelper" from "5EFB9F15"
C:UsersElon MuskDesktoptestToolkitSeagateCommonUtilsCommonUtilsCommonUtilsEncryptHelper.cs (None), 0001:00000000-0000000B, line/addr pairs = 1
87:43 - 87:92 00000000
C:UsersElon MuskDesktoptestToolkitSeagateCommonUtilsCommonUtilsCommonUtilsEncryptHelper.cs (None), 0001:0000000B-00000041, line/addr pairs = 7
91:7 - 91:36 0000000B 92:12 - 92:25 00000013
feefee:0 00000015 93:9 - 93:97 00000017
92:98 - 92:105 0000002E 92:27 - 92:96 00000032
94:7 - 94:21 0000003F
[...]
*** STRINGTABLE
00000001 C:UsersElon MuskDesktoptestToolkitSeagateCommonUtilsCommonUtilsCommonUtilsEncryptHelper.cs
00000065
00000066 c:userselon muskdesktoptesttoolkitseagatecommonutilscommonutilscommonutilsencrypthelper.cs
000000ca C:UsersElon MuskDesktoptestToolkitSeagateCommonUtilsCommonUtilsCommonUtilsExtensions.cs
0000012b c:userselon muskdesktoptesttoolkitseagatecommonutilscommonutilscommonutilsextensions.cs
0000018c C:UsersElon MuskDesktoptestToolkitSeagateCommonUtilsCommonUtilsCommonUtilsFileFolderHelper.cs
000001f3 c:userselon muskdesktoptesttoolkitseagatecommonutilscommonutilscommonutilsfilefolderhelper.cs
[..]
The above techniques were partially used also in earlier variants of this intense campaign, as also spotted and profoundly analyzed by BitDefender, yet as an evolving campaign — those new variants we observed in the last week have some new tricks up their sleeves.
The next stage of the operation is getting the Stealer into the system. This is done, this time, by dynamically downloading the relevant code from C2 servers using curl and 7zip binaries also hidden inside the original zip payload (with changed names of course). This gives the attacker added flexibility and also removes the potential for detection by fingerprinting the actual malicious payload — the zip file downloaded by the victim remains totally legit all along the way.
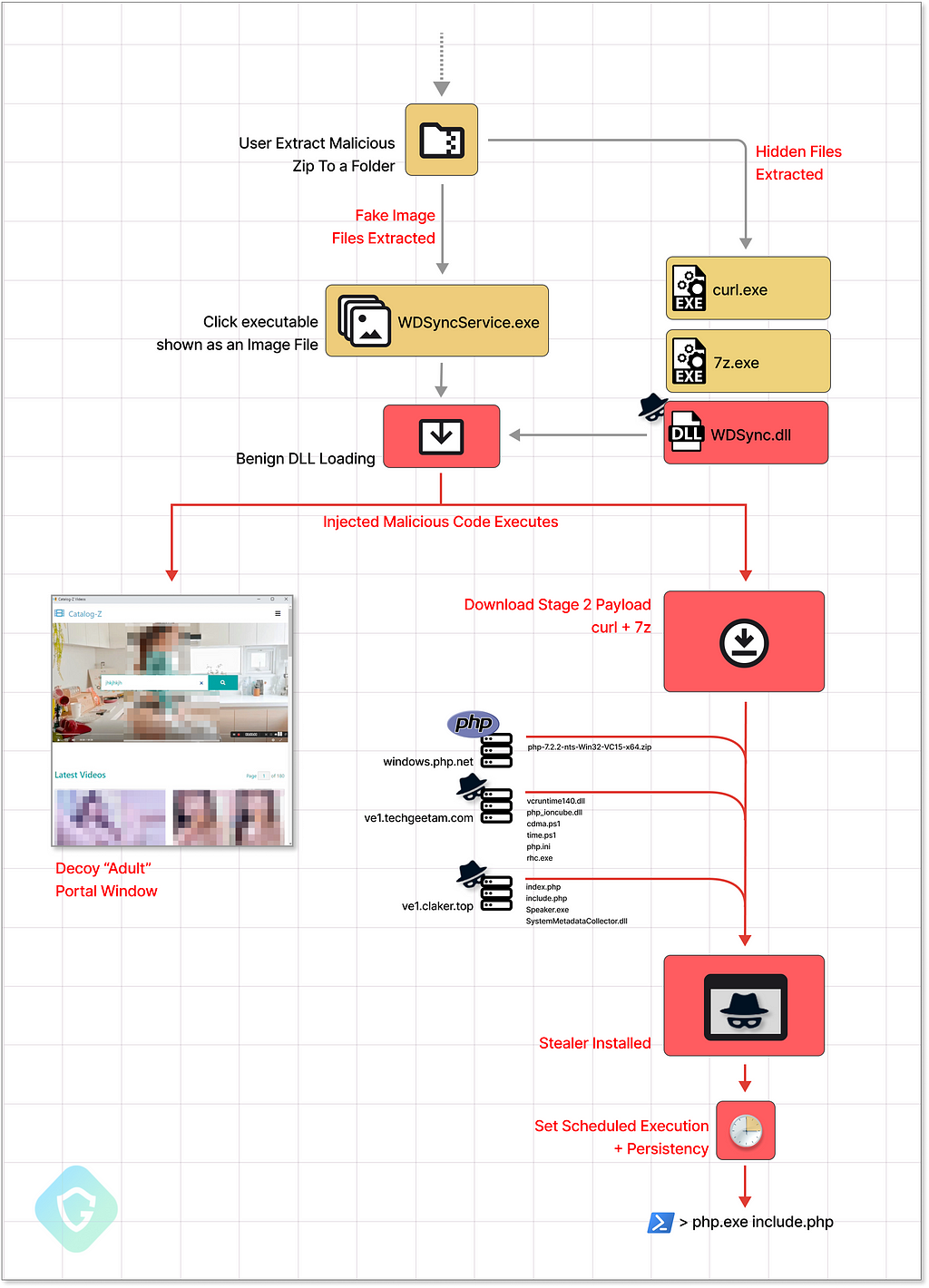
The last leap in this operation is the stealer itself which is a PHP-based stealer (with variants also known as Ducktail or SYS01). This new variant, although still using PHP (that is a scripting language that is quite easy to fingerprint), is now being encrypted and pre-compiled to bytecode using a tool called “ionCube Loader”. This makes the entire PHP code of the stealer look like this:
HR+cPoxrUtMlRa1xnZJkLjbt8vNvqsVXAfYm18F8E/h/1pJ6O4aVv6UQpFfbDa11Fo++taacG0/L
VyZw4hgBLL6pkNsdronCiSkBh1Pn4XRKAuASFNrPIkpAE1/hQYvD2PocTLsVVazrYavDiumYnD0+
VpRQQBzGm/3RHff/b5JJ5as9yrLYtmErkZ3CFditt+eg7NNJedbSPYkacKp5d0CXCuicKMIHPY+y
tcBx/HpTVlwg+FUs7wG9C/gzzMUIvJBkkpNoMJvOm6YQgXMaJsHRtXJvbe/b9rMH8X3h0U8kDz1G
irH5SGWTH6Rf0H2dj71LlBufMmiruJ4HuTfjdM3tTPiiFVCb0vXglm+x7jFeYnWoAUE76BOgG8xv
KH0YXvtPlyzrmbylZ7DQd9247qqmp1+2/Iq5JDx0v+1LOPRg7GsgefCsyTkrFvkK094Y6uBWQ/Nh
Cw25V6rgY5JEzLRiXE6EdymzvMLFNLzZCvAQdYRDobdmvIwUG1lTTrJRBphiQVSs3TzYHvLS72JC
[.......]
There is no way to quickly revert it back to scripting code — only actually decompiling this byte/assembly code directly from memory or reversing the encryption algorithm. All are doable, but now you can’t really use automated techniques to scan the code and quickly find IOCs to mark it as malicious — you actually need to reverse engineer it and dynamically analyze it.
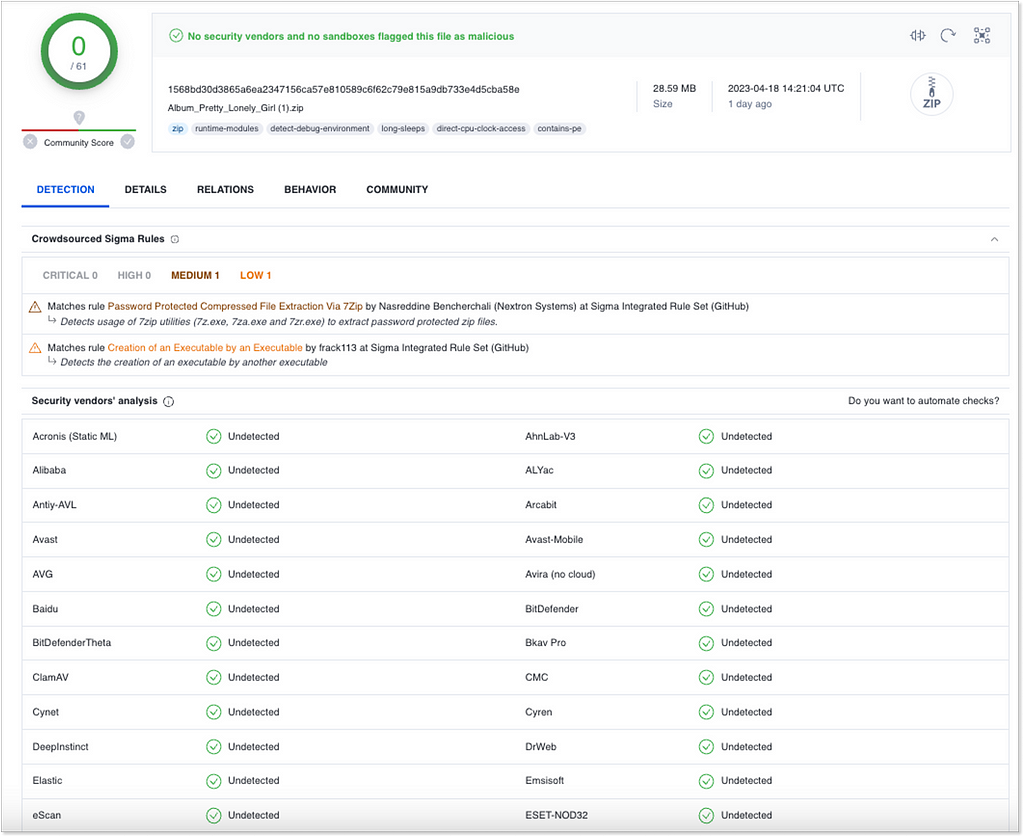
This gives the attackers may be the most precious resource they need to succeed — TIME. With the opportunity to effortlessly distribute millions of copies a day with the power of social networks advertisement infrastructure — the damage these threat actors can do in just a few hours, without detection, is overwhelming.
Fighting The Security Gap
Malverposting campaigns as intense and advanced as the above are indeed hard to fight back. The malicious payload is quite sophisticated and varies all the time introducing new evasive techniques. As we’ve seen, it takes time for security vendors to fingerprint it and create relevant verdicts to block — especially when it’s done out of context. And the context is sometimes the major lead, much more than the actual malicious activity.
When looking at threat actors from a wide angle, we see more and more misuse of generally available and legit file hosting, content hosting, and especially delivery mechanisms like Ad-Networks and Social Media. Pinpointing the bad guys in this endless content stream constantly generated by almost every human in the world is a big challenge, yet seems like one of the most relevant contexts to detect malicious activities. This is exactly the security gap we put in our top priority here at Guardio.
IOC’s
Affected Facebook Pages/Profiles:
Hijacked Accounts (last 14 days):
https://www[.]facebook[.]com/altrkstore
https://www[.]facebook[.]com/arambindia/
https://www[.]facebook[.]com/DrTechnoPeru
https://www[.]facebook[.]com/JanimagePhotography
https://www[.]facebook[.]com/MON.PAT.SHIATSU/
https://www[.]facebook[.]com/Movaks-417677965449830/
https://www[.]facebook[.]com/sict321
https://www[.]facebook[.]com/amplopcantikqeetaa
https://www[.]facebook[.]com/hallakinsulation
https://www[.]facebook[.]com/rtsleksikon/
Fake Profiles Created (last 14 days):
https://www[.]facebook[.]com/Jelly-Studio-120458764282549/
https://www[.]facebook[.]com/Shooop-Store-109582122115528/
https://www[.]facebook[.]com/Xpicture-Lady-18-109848348747430
https://www[.]facebook[.]com/Pictures-Album-104410945964034/
https://www[.]facebook[.]com/Pictures-Lab-106791609059352/
https://www[.]facebook[.]com/Pictures-Land-103158319425698/
https://www[.]facebook[.]com/profile.php?id=100089878329069
https://www[.]facebook[.]com/profile.php?id=100090678589841
https://www[.]facebook[.]com/profile.php?id=100091214258073
https://www[.]facebook[.]com/profile.php?id=100091364883811
https://www[.]facebook[.]com/profile.php?id=100091537913341
https://www[.]facebook[.]com/profile.php?id=100091549101555
https://www[.]facebook[.]com/profile.php?id=100091563985326
https://www[.]facebook[.]com/profile.php?id=100091569796450
https://www[.]facebook[.]com/profile.php?id=100091611648780
https://www[.]facebook[.]com/profile.php?id=100091652232000
https://www[.]facebook[.]com/profile.php?id=100091706393095
https://www[.]facebook[.]com/profile.php?id=100091721351037
https://www[.]facebook[.]com/profile.php?id=100091725404023
https://www[.]facebook[.]com/profile.php?id=100091731676745
https://www[.]facebook[.]com/profile.php?id=100091746189370
https://www[.]facebook[.]com/profile.php?id=100091751239191
https://www[.]facebook[.]com/profile.php?id=100091805619917
https://www[.]facebook[.]com/profile.php?id=100091814560890
https://www[.]facebook[.]com/profile.php?id=100091848215737
https://www[.]facebook[.]com/profile.php?id=100091859890204
https://www[.]facebook[.]com/profile.php?id=100091904521011
https://www[.]facebook[.]com/profile.php?id=100091905933028
https://www[.]facebook[.]com/profile.php?id=100091927594815
https://www[.]facebook[.]com/profile.php?id=100091949672195
https://www[.]facebook[.]com/profile.php?id=100091986969520
Domains:
Landing Page Domains (as used in Facebook Ads):
apps-blue[.]com
canva2023[.]com
chatgpt-premium[.]com
download5s[.]com
gaming-box[.]com
lydownload[.]net
movies-box[.]net
movies-cine[.]com
movies-cinema[.]com
myprivatephotoalbum[.]top
nctitds[.]top
office-2023[.]com
office-2023[.]net
office2023[.]net
payforme[.]top
photo-cam[.]com
photography-hq[.]com
pictures-album[.]com
privatecollection[.]top
programe[.]top
simpli[.]top
super-mario-deluxe[.]net
sportydesktops[.]com
takeforme[.]xyz
videovip[.]org
www-x-videos[.]com
x-album[.]com
x-album[.]net
x-albums[.]net
x-image[.]net
x-images[.]com
x-images[.]net
x-photobucket[.]top
x-photos[.]net
x-picture[.]net
x-pictures[.]net
xphotos-album[.]com
xphotos[.]net
xpictures[.]net
File Serving Domains / C2 Servers:
c[1-7].cembuyukhanli[.]com
c[1-7].somalisounds[.]com
h[1-7].helenrosi[.]com
v[1-7].viayonetici[.]com
k[1-7].karbilyazilim[.]com
n[1-7].nskfyl[.]com
i[1-7].vaishnaviinterior[.]com
i[1-7].ictorganisers[.]com
j[1-7].jinghuaqitb[.]com
j[1-7].jmooreassoc[.]com
e[1-7].wetterkameras[.]com
r[1-7].ritikajoshi[.]com
r[1-7].romeflirt[.]com
p[1-7].preppypm[.]com
kh[1-7].kimhasa[.]com
sb[1-7].shble[.]com
dl.privatecollection[.]top
dl.payforme[.]top
cdn.axphotoalbum[.]top
nctitds[.]top
phcde[.]top
ve1.techgeetam[.]com
ve2.techgeetam[.]com
te1.techgeetam[.]com
ve1.claker[.]top
Malicious Payload Files:
Filename Variations:
ONS_Bokyem{randomseed}.zip
Album Over Night With Me - Yuan Hee.zip
Album_Bad_Girl_Style.zip
Album_BeautifuIgirl_Inhostels.zip
Album_Beautiful_Girl_In_Hotels.zip
Album_Beautiful_Girl_In_The_Hotels.zip
Album_Beautiful_Girl_and_Friends_in_the_Hostel.zip
Album_Emily_In_Hotels.zip
Album_Fresh_Girl_Hwa_Mun_Hee_Sam_Myung_Buck_Studio_By_Ryeom_Dong_Sun_Photography.zip
Album_Hot_Girl_In_Hotel_Mei_Ying.zip
Album_Hot_Gymer_Yoon_So_Young_Jang_Myung_Dae_Studio_By_Yong_Jung_Hwa_Photographer.zip
Album_Jessica_and_Boyfriend_at_Home.zip
Album_ONS_Dang_Dae_Hyun.zip
Album_One_Night_Stand_Jing_Len.zip
Album_One_Night_Stand_Li_Shaw_Hwang_Chung_Wa_Studio_By_Gal_Dong_Min_Photographer.zip
Album_One_Night_Stand_Li_Shaw_In_Gook_Chin_Hae_Studio_By_Dong_Kyong_Photographer.zip
Album_One_Night_Stand_Li_Shaw_In_Jeomok_Daesung_Studio_By_Seong_Hwan_Photography.zip
Album_One_Night_Stand_Ren_Shi.zip
Album_One_Night_Stand_Shen_Zhi.zip
Album_One_Night_Stand_Yun_Hee.zip
Album_Over_Night_With_Me_Yuan_Hee_Ren_Tingguang_Studio_Chang_Jianjun_Photographer.zip
Album_Overnight_with_Beautiful_Girl.zip
Album_Pretty_Lonely_Girl.zip
Album_Rachel_In_The_Hotels.zip
Video_Helen_and_Boyfriend_at_Home.zip
GirlLeakFull.zip
CCleaner Professional 2023.zip
New_Super_Mario_Bros_U_Deluxe.zip
Office_2023_Full.zip
File Hashs (Partial List)
011c8af33ecff78288588aa434e4cc4ea78d208c669c01b2f724e68aae3f0a0c
01ba6ccb04787905b57b634dd7549081e989d0d1efcfb9f9efc93bcd558811ee
048b270391223a6f41aedbcd45f135c719f8b843c10b620a7c7cc4e4f11f46fe
0c944be48ead85db28f6abdad316736cf32a3f1047fed32e402140449dec985f
0e039b30986daeaa243a3eb02c9a7c5cf0dafc286302b4a1974aebf5ecc9bc1b
127039843ddbcf36fb8fffeaf0b6a1b1dd0523895788ba3ec077d2b1d60d0307
13c9558832abd4143522e4e6b84de884aa7af4184aed2f347e44511716d4a1fe
1568bd30d3865a6ea2347156ca57e810589c6f62c79e815a9db733e4d5cba58e
17f25e771110e1bbc1e6a4f2e4f662a851432f50693a2b5e7d2ba9c8290869d6
18287a851c3de040140c0a8015d6fe52342199cea86e565bcda2c36af5a646fb
18f3b519affcedc770a70009171cc6e454a7c7f855eab187a548b11f2bdfec46
1cbab44f2002b729fb743691096aefc19d4c21cc0497da0429b696901bbe339e
1d0b3654cab30ec51b4c8975547ea4428af54f9f250a25a5651cf005cd50763d
1d93b2edf0d9481d60f766e891f0aa21e2972292b610a1d952f52f4e9e76e14f
1dccd631d425919bdb0eeeb9ddab3bc4d372666796ef1db25e1274388733bf43
1fb47cec9095356217033f62ca9106f0724c6335d2136dbfcd8f59a3be6c2a88
2006dc7cbcfaa500a387d42e49a28d041e7b48cb54edc99ef1cdd1ada2f2f662
20b3254d43d14e2605454efa511f79d67c65b51f24e2eb8dd48a0c1d73a24c63
2158751e32774545bdefcbe445b741c869264b181c83d024da52bffffbc968c8
28b9952a6be452f821764e1f91ae9a99d3bfc36d7cb67df8b4cbec164f3980a7
2901f2d39820b1a46db1c095da3250f78d3a62acfcb9b46221dd790f8bab284b
29e7350ac07b1c2ed0f130694885b90030a22141cccb567865e4281616a04567
368d1aa7c621a61496da7c553585ef6f29157b247a28b535677cc84650a63e99
39a4c6bb4465799fbe9e77af16271600a08ed263e927233638906d6ceaab98d3
3ae71c6ee4e9f848183283caa95183a6778d6bb93cae24cd1024b9964be11cbc
3bff68194ab76b9ba96468fbb2f9c8b9b62d1a0502fecd2d6889849be204c8ed
3dc2ed2ca4a6d3b10c54bd6fb3b775b28f39f26b58d1e8f0edbdd22a7d124b28
4095ffa9e7391a9fd3de0a5d5649367afd1476d03f1933e6b933af93b3f2cf0c
43dba2bbd2085a515e2be3dfe53b31a0fb467e976a66e7af38832ed3ef6a7310
45379a07babf75c4b8608d507bfc588bfa08e17f419f9b470086d2e0c991ff7a
48ab2be4c0b2443b4ed8580bd8263b115fd4c22751adc2a21b5fe52898ce665f
4a838b726fada4cd128ad67750fb735a659548a142783a9d50e84b8acc4ac027
4b592255c796f18fa66ecabfa3e4ddbe808df1464421d1d487d81949427a8073
4dfcaa193d32b1b52a917f3cbd7f90e5a878e14f5eaa55ff1e127bd82ff1fcd5
54790f72f86d56140c08c34fcba24cc7de47a3d5e8c7f76ee5ce422b7b5e1381
60e892043a837f5b2224a5351a215c9bf14f3938b6b573f9f077d944bae48deb
64b7bcf7689e70aac6d1f1bf35d7db953b7943484dffd005eb8c92b38cd45cc8
65466adbdfe9559b2c046f35acc2681aafa117196467c7859e393c74202a6cf2
67ef86ea3e8903458c0ca018abab3b48058c045f649bad1f1b6048ab1a238f41
6819b70eaf85e1b8c5762fa88bfe3a7ab45bf6ee41aeb095959c2df5b7af695f
6b7530bc89eb386c3b1d89a2847ea1f569ac08960f00af2a344e5b821e476516
6c7d3b2f3400ec3ac84868b7c86339e6cac2652970d63a2e0d8703d364b86fa0
6e8a3b0f91dbbcacea3f34e79c12976f2b1e0630e200bff9265726b980dc01f7
738db32652ec2fd1fa8140f57e0a5f8b645bfdf3357d281056433690fa66219d
752e95c7d41fe917f6ae2b6627333719961feb98675826573c1f0681c651f61c
76d61c0bd8d1d66d670b4a0176e6868892701094788fb9c8599694bfc0dab44f
7776b5c7ecb9fb43618eea22bad42dfe92384129484cbee7722edec14786392d
777903b6d0545cd5feeac43d9f2b0e2ca89fcc0346b7f771b616845e2c84bab4
7ddd36067df13eead457fa4d107a1f8e66559a8129c7a5e228119d17241aae5c
7f6a851278ed5138b6f731f85760b70b8813ff2e563962b16905c7408797fc8d
84e790800ef6d5604c50e8854984610eeb005966902842335eaf3bc44b543f4c
872da30d1ee44494026dd09fc5f1207c5d0163f2d1d0d6096749b54096af51fe
87e02275cc993071c3fd3a026f8f4c2fd889edca888818ffaa4c2fa26f9b8091
87e995a07836a3f465b1ab39e964f4bfa161732156f142237803ed06cc06b13a
886ce15963e2241962eb52009d31fb848b54ef40c72434d889685afeea7cb7b0
8c9cf2b8dd4a0c1f1335c8644ef6afc39c1359a9998afaf51f96355637b68925
8f4a7a96d51933de7965a5ee4c5a56d36f0962111e8668b177ca79be770604f2
9451b7b4898deb6975039f13eed608700f6fe48a9a62c792327556a69d08d199
983b23ba4116e7643f0f01b9e4a4370822832212b2e5208791925af88b09b3c5
9943e11d067a45b75f5a6ba32a0857d1cb285be01d15f1cb6beed0393b8380f1
a00ac6357ae3e449d49f49cab2b0d095e2e0f3ac63b074e5d0257c6905677032
a18d8a42b74587363a56b178a5bc7df64860ebf388bcd1f42bc6c9924bbb094b
a1ab93bb1c2560585277283ed7dde95634cdcff01b0920d101824591390127a8
ac10cd180e9fbde1ff54024a31af67d07fd909d5d543bb751bbc6c93d5b7edef
b0590bbb1b8da28db4ee14ccc5756794714c08d25088edd627ba82521ec3ce63
b3bc502d42704033eccdfe8edd79b406a9d141e6755ed4225be32659383dcff4
b3c6157495b8cb0ca6a5c8e4d3189715a06e9011f792ddf439fefcbd08b63b69
b3c6157495b8cb0ca6a5c8e4d3189715a06e9011f792ddf439fefcbd08b63b69
b89c1d7dec6a46bd7e8d55520d82f6120d0341ce03abef30aa7fb195a6212f43
b8e1152e035ffcda72d31daef0ead565f0b26e869c7c4a5916b89f9152337252
badf98997da06f881e4ce840c5e782aa4fc3971786be5942704a4deab52cf9b7
bda6cb175689b8e6e0b0ce67fbef4d4070293aac24999f6883f9699a3bc9173d
c3940fe14a5216706a53ceee13b75f23d0f671027cb07c26ae7f4472ae746233
c9d57fdaefa6f88a7596571488cfe749b3c662cfbe860ebfb5bab5a6a0e31bf5
cd729da6dde5694eecf3a3a259e31fd6c5170642998367629b9690be43cceae0
ce19c1a4e7aa5b2160392a6529452556b8f371c0103f844632397a9f7535dfa8
cfa908fe922bd59dd162740e9e71744c81a9abec02e14a390e3f78d3551ff52c
d1476f64cd98c05c906d4b0ed3985e2c6070367c751202bac769668afa9ca3a2
d23332fc8c58c56de7c2d7693a4140087b25a5d6645914242104f039c1964ffd
d2de1dc79bef2e03ca8b53fc345a5ccfa224ea7237aeb74bcb155391e804e149
d35265e4ecc1636138ef372f780215199292235e52c0e7c733b66e29813c50d1
d453c795fde75a2b25ba3d2fd5af75771a41793302a463c0027ee0638b5d0ecd
d68aafb217a558417cf6a9991755dd9708206774002bb98007dbf31e87946144
d6d971bd5485c3241cd8ad25afea515aa5a0fe948a30015554ddb69fac3498af
d818e0899649e5963160aff698bbce56700bd3336efc92bde3c04e331d06610c
db4eba8a2e4d5cc9ab88152560f875810114414b390055e57089c4fbed512702
db8e416efe6ef3be79c9132eb576610ca80342cdb925be3b059ec63ec2cc807f
ddeb210f4ff5082e4fbbbc3a2c23b232f50066759e16c74e64fd69dd4bce7311
e43cc3e57cdb89967fd89bd2636d057781a7821f3d06d288c494e1a755ae4b9e
ee45f117b685536cdc8af14f98cda87bbb0ad48b73200ba1716da76884fb84c2
f546a4d9c15d5f91392fbf40173c193bbf8c90f3f5b27287b0767e57a6e8fc92
f58d1a0b33f846c90f808ba656b29b3d55ac94171beb5fcb1de891d4639173b5
f59c7259254c7229ddfe456e605a017d59921e51c4f14e686182f97bf40f9936
f73c482de2cea8cfbe9c1c72e5bbfee630017b219543eacdd6f83aa81a053850
f7c95ba1f577bb38e61e67202145a861780bc712374b341dfb4332654068ecb4
f8bee99baf8f53ac1260a9f6ef20de05f66835750dbb7799b0b67fa815a4e92a
fca625e970416f2d32713b402f0bf510a08c2bbde5b8d3618544158e142b14fa
ffd698d63fe407fce60977dc8367aad6ef42e13f30e0d2040ecdac82a95c9759
Source: Original Post
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português