While performing regular threat hunting activities, we identified multiple downloads of previously unclustered malicious Tor Browser installers. According to our telemetry, all the victims targeted by these installers are located in China. As the Tor Browser website is blocked in China, individuals from this country often resort to downloading Tor from third-party websites. In our case, a link to a malicious Tor installer was posted on a popular Chinese-language YouTube channel devoted to anonymity on the internet. The channel has more than 180,000 subscribers, while the view count on the video with the malicious link exceeds 64,000. The video was posted in January 2022, and the campaign’s first victims started to appear in our telemetry in March 2022.
The installation of the malicious Tor Browser is configured to be less private than the original Tor. Unlike the legitimate one, the infected Tor Browser stores browsing history and data entered into website forms. More importantly, one of the libraries bundled with the malicious Tor Browser is infected with spyware that collects various personal data and sends it to a command and control server. The spyware also provides the functionality to execute shell commands on the victim machine, giving the attacker control over it.
We decided to dub this campaign ‘OnionPoison’, naming it after the onion routing technique that is used in Tor Browser.

Screenshot of the video with a link to the malicious Tor Browser installer in the description section
Initial infection
Victims of the OnionPoison campaign likely reach the video with the malicious link after a YouTube search. The video heads the list of search results for the ‘Tor浏览器’ (‘Tor Browser’ in Chinese) query. The description of the video contains two links: the first one goes to the official Tor Browser website, while the other leads to a malicious Tor Browser installer executable hosted on a Chinese cloud sharing service. As the original Tor website is banned in China, viewers of the video have to navigate to the cloud sharing service link in order to download the browser.

Download page of the malicious Tor Browser installer
The malicious installer
| MD5 | 9AABCABABD5B677813589F7154302EE0 |
| SHA1 | 7E8B9D2BD32B3AEA0E298B509D3357D4155AF9BC |
| SHA256 | 877FE96CDFA6F742E538396B9A4EDB76DD269984BFB41CAD5D545E72CE28FFDE |
| Link time | 2021-Sep-25 21:56:47 |
| File type | PE32+ executable (GUI) x86-64, for MS Windows |
| Compiler | Visual Studio 2003 – 7.10 SDK |
| File size | 74 MB |
| File name | torbrowser-install-win64-11.0.3_zh-cn.exe |
The user interface of the malicious Tor Browser installer is identical to the original one. However, the malicious installer does not have a digital signature, and some of the files dropped by the malicious installer differ from the ones bundled with the original installer:
| File name | Comment |
| freebl3.dll | The file freebl3.dll is present in the original Tor Browser installer; however, its contents are entirely different from the DLL in the malicious installer |
| freebl.dll | A file with this name is found only in the malicious installer. It is a copy of the freebl3.dll library from the original installer |
| firefox.exe | The executable in the infected installer differs from the original by only one byte: the infected installer contains the string https://aus1.torproject.org/torbrowser/update–3/%CHANNEL%/%BUILD, while the corresponding string in the original installer is https://aus1.torproject.org/torbrowser/update_3/%CHANNEL%/%BUILD. By replacing the underscore with a dash, adversaries prevented the malicious Tor Browser installation from updating. They have likely disabled updates in order to prevent overwriting of the modified freebl3.dll library. |
What is also interesting about the malicious Tor Browser installation is that the adversaries made it less private. By modifying the defaultspreferences00-tor-browser.js configuration file that is stored in the browseromni.ja archive, they have configured Tor to:
- Store the browsing history;
- Enable caching of pages on disk;
- Enable automatic form filling and memorization of login data;
- Store extra session data for websites.

Snippets of the modified (left) and original (right) 000-tor-browser.js file
The freebl3.dll library
| MD5 | 87E33DF76D70103A660783C02AAC44AC |
| SHA1 | 04C5A6543E61328B235339358D2E48C0002F0E46 |
| SHA256 | 3BA945FD2C123FEC74EFDEA042DDAB4EB697677C600F83C87E07F895FB1B55E2 |
| Link time | 2021-Dec-21 09:44:08 |
| File type | PE32+ executable (DLL) (GUI) x86-64, for MS Windows |
| Compiler | Visual Studio 2010 – 10.10 SP1 |
| File size | 114 KB |
| File name | freebl3.dll |
When Tor Browser (either the legitimate or the infected one) starts up, it loads the freebl3.dll library into the address space of a firefox.exe process. In the case of the infected browser installation, the adversaries replaced this library with a malicious one. To ensure Tor functions correctly, this malicious library proxies all its exports to freebl.dll (a copy of the original freebl3.dll library).
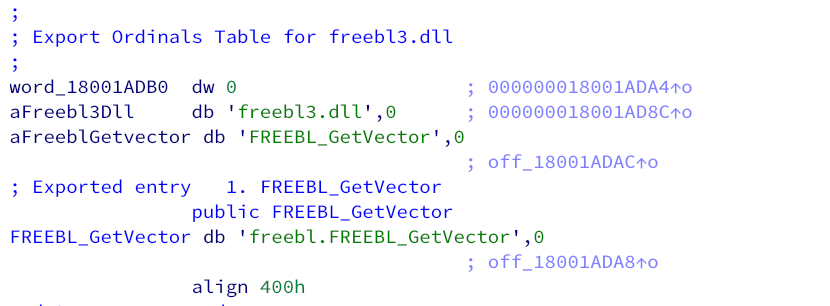
Forwarded exports of the malicious freebl3.dll library
Upon startup, the malicious library creates a mutex with the name GlobalTBrowser that prevents two instances of the malware from running at the same time. It then pseudorandomly chooses one of the following C2 server URLs and makes a POST request to it:
- https://torbrowser.io/metrics/geoip
- https://tor-browser.io/metrics/geoip
Interestingly, the POST request made to the C2 server contains the following headers:
| Header name | Header data |
| Date | Current date and time in GMT format (e.g., Mon, 10 Aug 2022 11:21:55 GMT) |
| User-Agent | Default User Agent obtained through the ObtainUserAgentString API function |
| Host | C2 server address |
| Authorization | Contains a HMAC-SHA1 signature of the request data (example header value: Authorization: SIGN QbqCdtmBBk3uH2Zj:gNe34o6RkQ/Hn82bRPSk7q1DO8w=). Here QbqCdtmBBk3uH2Zj is an identifier of the HMAC key, and gNe34o6RkQ/Hn82bRPSk7q1DO8w= is a Base64-encoded HMAC-SHA1 hash. This hash is formed from a string containing:
|
In response to the POST request, the C2 server returns a blob containing an encrypted second stage payload. This payload is decrypted using two XOR keys: the first key is derived from the payload length, while the second key is D65CB35A-58CB-4456-A7B7-E1B218770A9E. After decrypting the blob, the malicious DLL decompresses it using the RtlDecompressBuffer function, thus obtaining another DLL file. The malware then reflectively loads this DLL and invokes its entry point function.
Obtaining the DLL from the C2 infrastructure
During our research, we attempted to communicate with the C2 server and retrieve the second stage DLL. At first, the server did not return the DLL in response to our POST request. Then, through trial and error, we discovered that the C2 server checks the IP address of the victim machine and only dispatches the payload to victims from China. After making a POST request from a machine with a Chinese IP address, we successfully downloaded the second stage DLL. We can therefore say that the OnionPoison campaign targets users that are located in China. Another thing to note is that the IP address check makes it difficult to obtain the second stage payload via automated malware analysis sandboxes.
The second stage DLL
| MD5 | 34C43C9B23B40D9D70B4530DE781F88A |
| SHA1 | 3EBF1E989791E3743CEAC1C7B397242DD717AEA9 |
| SHA256 | E5CC91FBE01005EF058B1C1D727CFBFB584B012390106BB9C941BC9B1AA96FF7 |
| Link time | 2022-Feb-16 09:56:56 |
| File type | PE32+ executable (DLL) (GUI) x86-64, for MS Windows |
| Compiler | Visual Studio 2010 – 10.10 SP1 |
| File size | 788 KB |
| File name | cloud.dll |
When loaded, the second stage DLL retrieves the following system information:
- GUID of the operating system disk volume;
- Machine GUID;
- Computer name;
- Computer locale;
- Current user name;
- MAC addresses of network adapters.
If launched for the first time on the victim machine, the DLL also generates a pseudorandom victim GUID and saves it inside in the SoftGuid value of the HKCUSOFTWAREMozillaFirefox registry key.
After collecting system information, the DLL starts sending heartbeat messages to the C2 server every two minutes. The body of every heartbeat message contains a JSON object with collected system information. Heartbeats are sent as POST requests to either the https://torbrowser.io/metrics/heartbeat or the https://tor-browser.io/metrics/heartbeat URL. The DLL also encrypts the request body by first encrypting it with a pseudorandom AES-128 (ECB) key and then encrypting the AES key with an RSA public key specified in the configuration.
In response to heartbeats, the C2 server may request to collect the following additional information:
- Installed software;
- Running processes;
- TOR browser history;
- Google Chrome and Edge history;
- IDs of WeChat and QQ accounts that belong to the victim;
- SSIDs and MAC addresses of Wi-Fi networks to which the victims are connected.
The collected additional information is sent to the C2 server together with the next heartbeat message.
In addition to that, the C2 server may request to execute an arbitrary shell command on the victim machine. To do so, the DLL creates a new cmd.exe process, passing the command as an argument. It also redirects the output of the command line process to a pipe that is later used to retrieve the command execution results. Once the shell command finishes executing, its results are encrypted (also with a combination of symmetric and asymmetric cryptography) and sent via a POST request to either the https://torbrowser.io/metrics/geoip or the https://tor-browser.io/metrics/geoip URL.
An interesting fact about the C2 server websites is that they are visually identical to the original Tor Browser website. The browser download links on the replica website lead to the legitimate Tor Browser website.
![Screenshot of the torbrowser[.]io webpage](https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2022/10/03113741/OnionPoison_05-1024x421.png)
Screenshot of the torbrowser[.]io webpage
Victims
According to our telemetry, all detections appear to be geographically located in China. This was to be expected because, as we mentioned above, the C2 server checks that the external IP address of the victim’s machine originates from China.
Conclusion
In this campaign, the attackers use anonymization software to lure targets. Placing a link on a popular YouTube channel makes the malicious Tor Browser installer appear more legitimate to potential targets. Curiously, unlike common stealers, OnionPoison implants do not automatically collect user passwords, cookies or wallets. Instead, they gather data that can be used to identify the victims, such as browsing histories, social networking account IDs and Wi-Fi networks. The attackers can search the exfiltrated browser histories for traces of illegal activity, contact the victims via social networks and threaten to report them to the authorities. In the past, we have also seen cases where law enforcement agencies, for instance, the FBI, have used 0-days to unmask the identity of Tor users involved with darknet pedophile websites. Another similar case involved the distribution of OnionDuke malware through injections into unencrypted HTTP connections on TOR exit nodes.
Regardless of the actor’s motives, the best way to avoid getting infected with OnionPoison implants is to always download software from official websites. If that’s not an option, verify the authenticity of installers downloaded from third-party sources by examining their digital signatures. A legitimate installer should have a valid signature, and the company name specified in its certificate should match the name of the software developer.
Source: https://securelist.com/onionpoison-infected-tor-browser-installer-youtube/107627/
Views: 0