This article discusses a new phishing campaign targeting Microsoft advertisers, leveraging Google ads to obtain user login information. The research identified a variety of IoCs linked to this campaign, including domains, email addresses, and IP addresses. Findings noted a mix of old and newly created domains, with most registrations occurring in the U.S. Affected: Microsoft advertising platform, users of Microsoft’s advertising services
Keypoints :
- Microsoft and Google frequently appear on phishing lists due to their popularity.
- Malicious Google ads were used to steal login information from Microsoft advertisers.
- 97 domains were identified as indicators of compromise (IoCs) in the phishing campaign.
- Additional IoCs included 204 email-connected domains and 25 IP addresses, 16 of which were malicious.
- A sample of the additional artifacts is available for download.
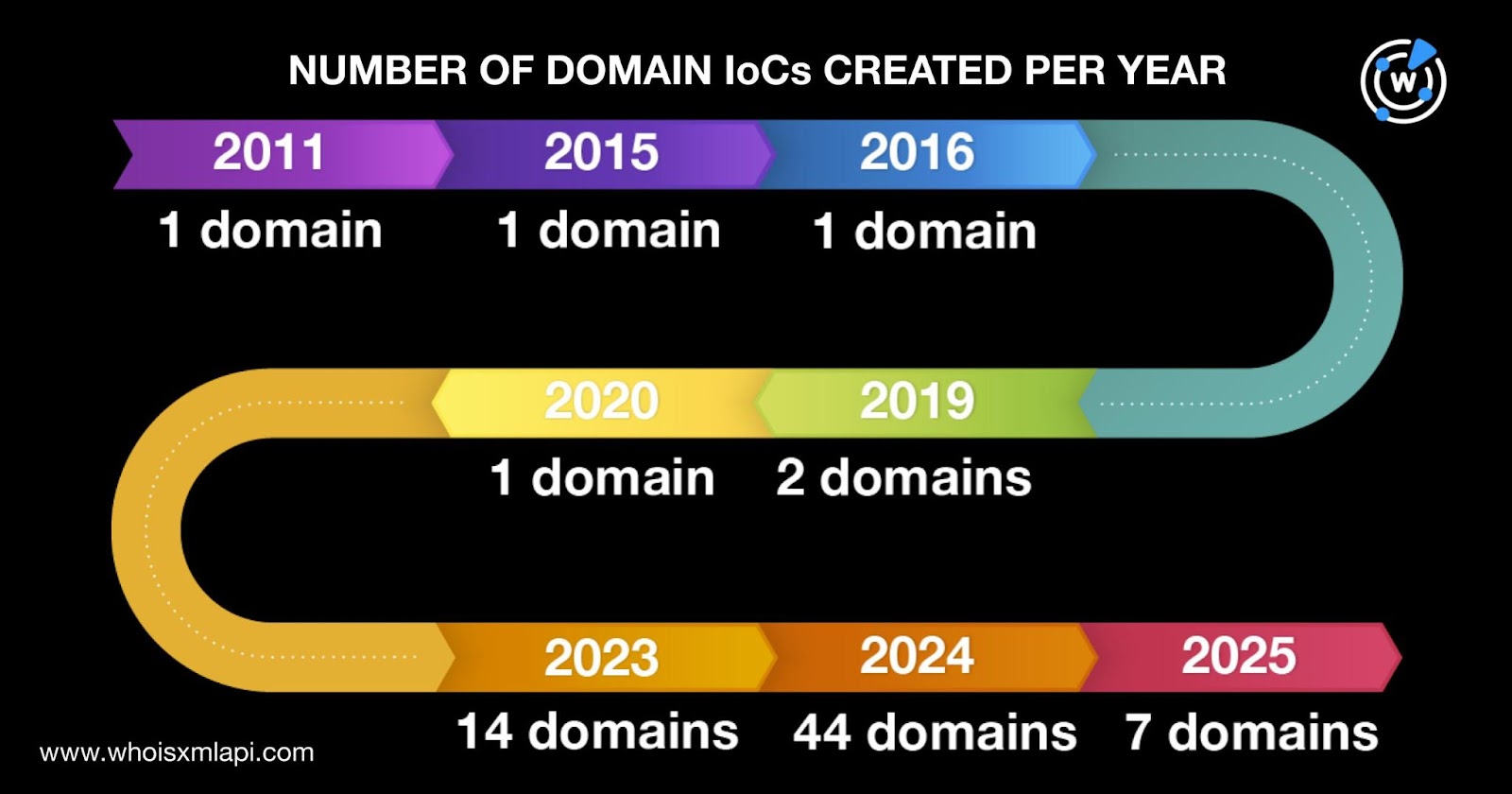
- 2024 saw the highest number of new domains created among the IoCs.
- The U.S. was the leading country for domain registrations associated with the IoCs.
- 84 of the initial 97 IoCs had recorded DNS histories with numerous IP resolutions.
- Malicious activities were associated with several specific IP addresses found in the analysis.
MITRE Techniques :
- T1071 – Application Layer Protocol: Used to communicate with command and control (C&C) servers via normal web traffic.
- T1203 – Exploitation for Client Execution: Phishing campaigns leveraged Google ads to trick users into providing credentials.
- T1499 – Endpoint Denial of Service: Targeting users by overwhelming them with fake login prompts.
- T1552 – Unsecured Credentials: Obtaining users’ credentials from compromised accounts.
Indicator of Compromise :
- [Domain] euroinvest[.]ge
- [Domain] 30yp[.]com
- [Domain] advertising[.]online
- [IP Address] 104[.]21[.]32[.]1
- [IP Address] 15[.]197[.]130[.]221
Full Story: https://circleid.com/posts/malicious-ads-targeting-advertisers-in-the-dns-spotlight