Short Summary
The oil and gas extraction industry is increasingly vulnerable to cyberattacks due to its reliance on digital technologies and geopolitical tensions. A significant percentage of energy professionals are aware of potential vulnerabilities, particularly in Operational Technology (OT) systems. Key threats include ransomware, phishing, supply chain attacks, and advanced persistent threats (APTs). Recent high-profile incidents highlight the urgent need for robust cybersecurity measures to protect critical infrastructure and maintain operational integrity.
Key Points
- Geopolitical Tensions: 78% of energy professionals report increased awareness of vulnerabilities due to geopolitical uncertainty.
- Supply Chain Vulnerabilities: 57% of professionals believe their organizations have good oversight of supply chain risks.
- Ransomware Threats: Ransomware attacks can halt operations and cause significant financial losses, exemplified by the Colonial Pipeline attack.
- Phishing Attacks: Deceptive emails can lead to unauthorized access to critical systems.
- Advanced Persistent Threats: State-sponsored attacks aim to steal sensitive information or disrupt operations.
- Recent Cyber Incidents: Notable breaches include attacks on Hitachi Energy, Halliburton, and Suncor, highlighting the sector’s vulnerabilities.
- Unpatched Vulnerabilities: 49% of ransomware incidents in 2024 were due to exploited vulnerabilities, emphasizing the need for robust cybersecurity measures.
MITRE ATT&CK TTPs – created by AI
- Ransomware – T1486
- Encrypting files to demand ransom for decryption.
- Phishing – T1566
- Using deceptive emails to trick users into revealing sensitive information.
- Supply Chain Compromise – T1195
- Exploiting third-party vendors to gain access to larger networks.
- Denial of Service – T1499
- Overloading systems to disrupt services.
- Credential Dumping – T1003
- Stealing credentials to gain unauthorized access to systems.
The oil and gas extraction industry, a critical sector for global energy supply, has become a prime target for cyberattacks due to its increasing reliance on digital technologies and the growing geopolitical tensions worldwide.

AI illustration of “Cybersecurity Attacks in Oil And Gas Extraction Industry” by DALL-E
According to DNV’s Cyber Priority research, almost eight in ten energy professionals (78%) report that geopolitical uncertainty has made them more aware of potential vulnerabilities in their Operational Technology (OT) systems, highlighting the heightened concern over state-sponsored and politically-driven cyber threats.
And surprisingly in the same research more than half (57%) of energy professionals report that their organization has good oversight of supply chain vulnerabilities, indicating some confidence in their third-party risk management. However, addressing supply chain vulnerabilities remains one of the top-five challenges in cybersecurity for the industry.
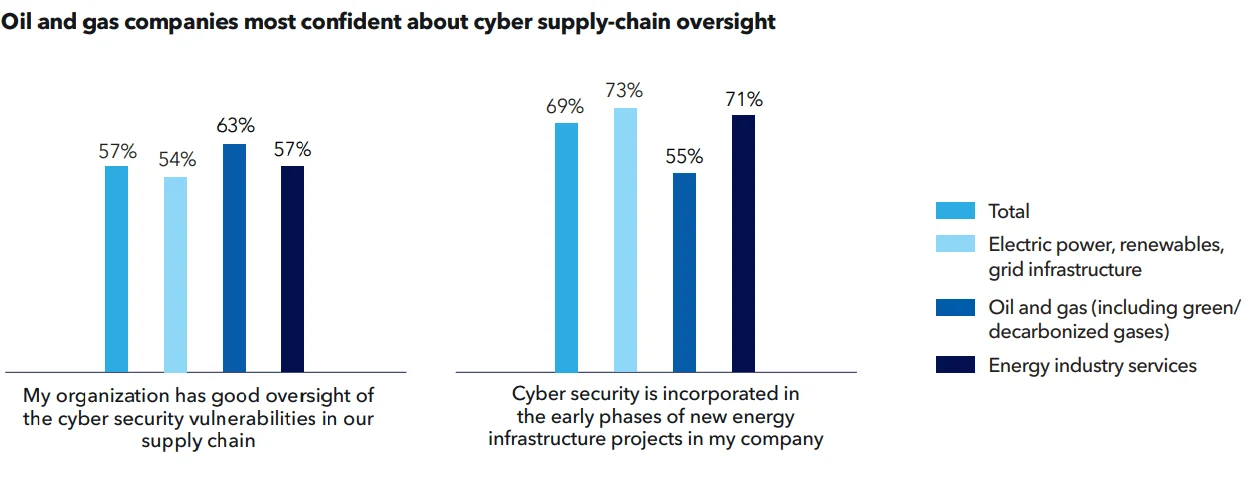
Oil and gas companies indicates to have oversight over supply chain related cyber attacks (source: DNV’s Cyber Priority research)
In industries like oil and gas, understanding the ever-changing threat landscape is critical, especially when it comes to ransomware. SOCRadar’s Operational Intelligence goes beyond monitoring and includes a specialized Ransomware Intelligence service that provides dynamic, real-time insights into the rise and fall of major ransomware groups. This service monitors geographical trends in threat actor activity, identifies target regions, and provides the most recent threat reports.
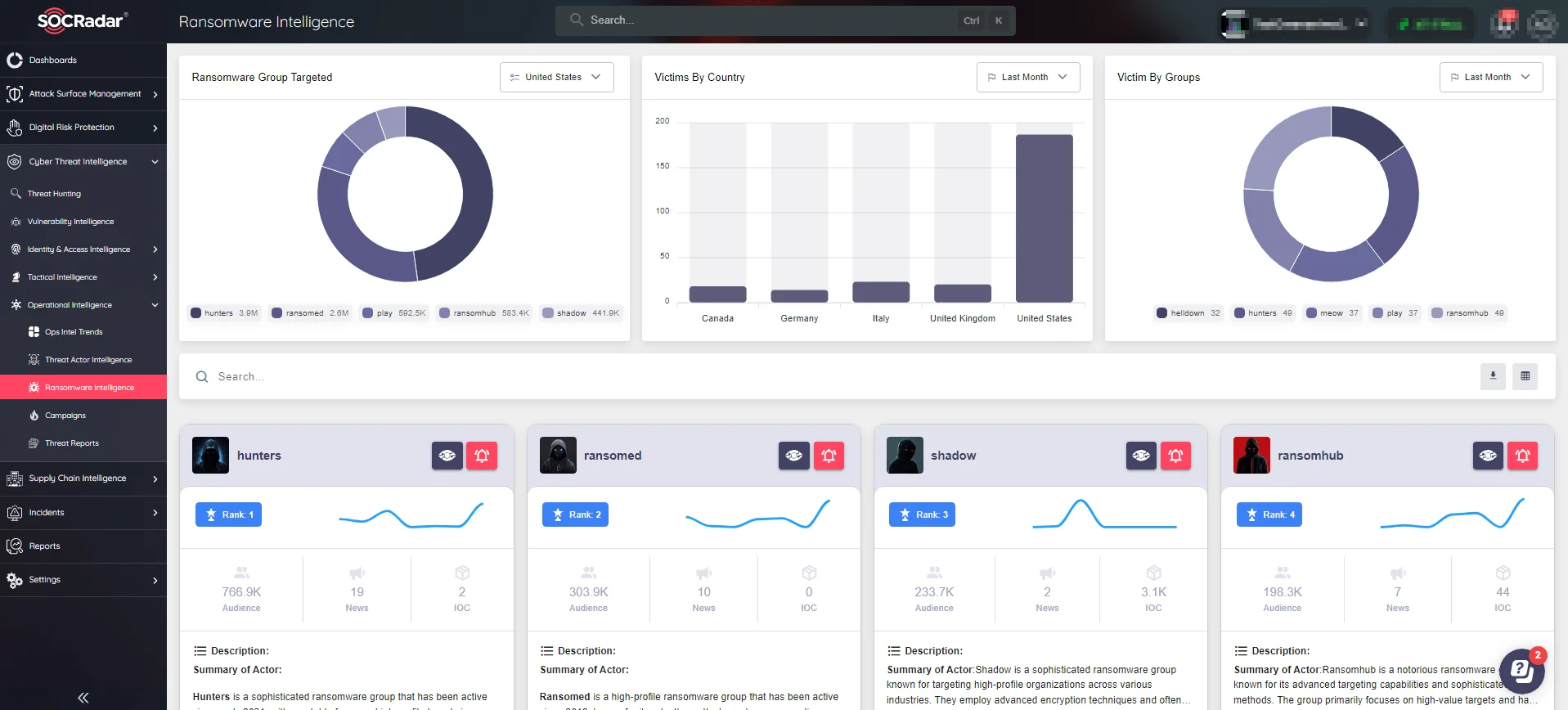
Monitor ransomware activities in real-time using SOCRadar’s Ransomware Intelligence service
SOCRadar’s detailed ransomware group profiles, with Indicators of Compromise (IOCs), and MITRE ATT&CK visualizations allow you to anticipate and counteract ransomware attacks before they disrupt your operations. SOCRadar’s Ransomware Intelligence keeps your organization one step ahead of these ever-changing threats, protecting your critical infrastructure from potential devastation.

Key Cyber Threats Facing the Oil And Gas Extraction Industry
- Ransomware Attacks: Cybercriminals encrypt critical data, demanding ransom for its release. This can halt operations, disrupt supply chains, and cause significant financial losses. A notable example is the 2021 Colonial Pipeline attack, which resulted in widespread fuel shortages along the US East Coast.
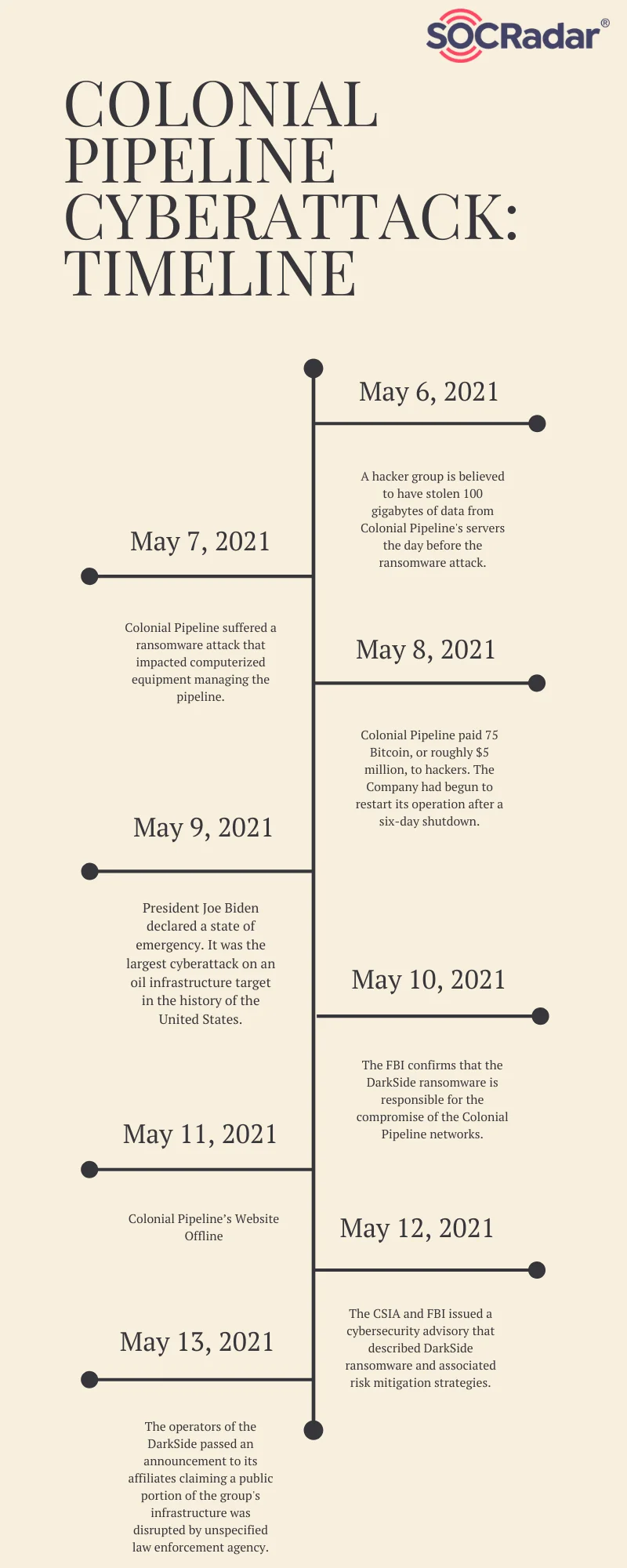
Colonial Pipeline attack timeline
- Phishing and Spear Phishing: Attackers use deceptive emails or messages to trick employees into disclosing sensitive information or downloading malware. In oil and gas companies, phishing campaigns can result in unauthorized access to critical systems, potentially jeopardizing operations.
- Supply Chain Attacks: Attackers exploit third-party vendors or suppliers to gain access to a larger company’s network. The interconnected nature of the oil and gas industry makes it especially vulnerable to such attacks, which can be difficult to detect and mitigate.
- Denial-of-Service (DoS) Attacks: These attacks cause systems to overload and disrupt services, potentially affecting production or distribution processes. In the oil and gas industry, DoS attacks can target critical infrastructure, causing significant operational downtime.
- Advanced Persistent Threats (APTs): Sophisticated, long-term cyber intrusions that, in many cases, are state-sponsored and seek to steal sensitive information or cause long-term operational disruption. APTs are a significant threat to the oil and gas industry, as they can lead to the theft of proprietary data or the sabotage of critical systems.
Top Cybersecurity Attacks in Oil And Gas Extraction Industry (2023-2024)
This section discusses some of the most significant cybersecurity breaches in this sector, demonstrating the wide range of tactics used by attackers and the serious consequences these attacks can have on various aspects.
1. Hitachi Energy Data Breach Following CLOP Ransomware Attack
In March 2023, Hitachi Energy confirmed a data breach caused by a CLOP (aka CL0P) ransomware attack that exploited a zero-day vulnerability in Fortra’s GoAnywhere MFT software (CVE-2023-0669).
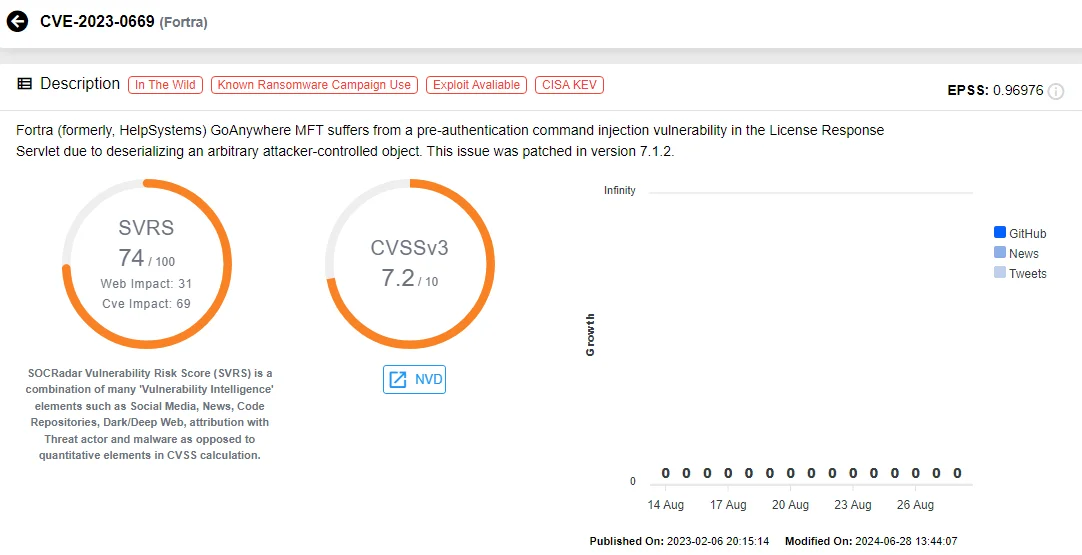
Vulnerability card of CVE-2023-0669 (SOCRadar Vulnerability Intelligence)
The breach compromised employee data in several countries, prompting Hitachi to disconnect the affected systems and conduct an internal investigation. Despite the breach, Hitachi claimed that its network operations and customer data were secure.
The CLOP group, known for targeting high-profile organizations, added Hitachi to its extortion portal, signaling a significant cybersecurity event in the energy industry.

Learn more about CLOP ransomware on SOCRadar’s Dark Web Profile
It is worth noting that the Fortra GoAnywhere MFT vulnerability (CVE-2023-0669) was a major contributor to a 91% increase in ransomware attacks in March 2023. This vulnerability enabled remote code execution, which CLOP ransomware exploited in 459 incidents, including Hitachi Energy’s data breach. The Health Sector Cybersecurity Coordination Center highlighted the threat posed by this exploit, which also affected organizations such as Brightline, resulting in the compromise of sensitive data for over 780,000 patients.

2. Halliburton
Halliburton, a major oilfield services company, confirmed in August 2024 that it had been the target of a cyberattack. The breach affected operations at the company’s North Houston campus and disrupted global connectivity networks, which caused employees to refrain from accessing internal systems.
The company activated its cybersecurity response plan, which included internal and external experts, and notified law enforcement. The investigation is still ongoing, with efforts aimed at restoring systems and assessing the damage. Halliburton did not disclose any information about the attackers or the nature of the disruption to its operations.
The incident has raised concerns about potential disruptions to the energy supply chain, though the U.S. Energy Department stated that there were no immediate effects on energy services. Cybersecurity experts believe the offline status of systems indicates a severe ransomware attack, which is especially concerning given the sector’s importance to the economy.
3. STORMOUS Cyberattack on PVC-MS
On September 7, 2023, the pro-Russian ransomware group Stormous announced via Telegram that it had compromised 300 GB of data from Petroleum Equipment Assembly & Metal Structure J.S.C. (PVC-MS), a PetroVietnam subsidiary. The stolen data consists of sensitive project documents, vendor information, and contract negotiation files. This attack is consistent with Stormous’s previous threats against Vietnam, the United States, and Peru. The group initially leaked 10% of the data, with the remainder potentially available for future exploitation.
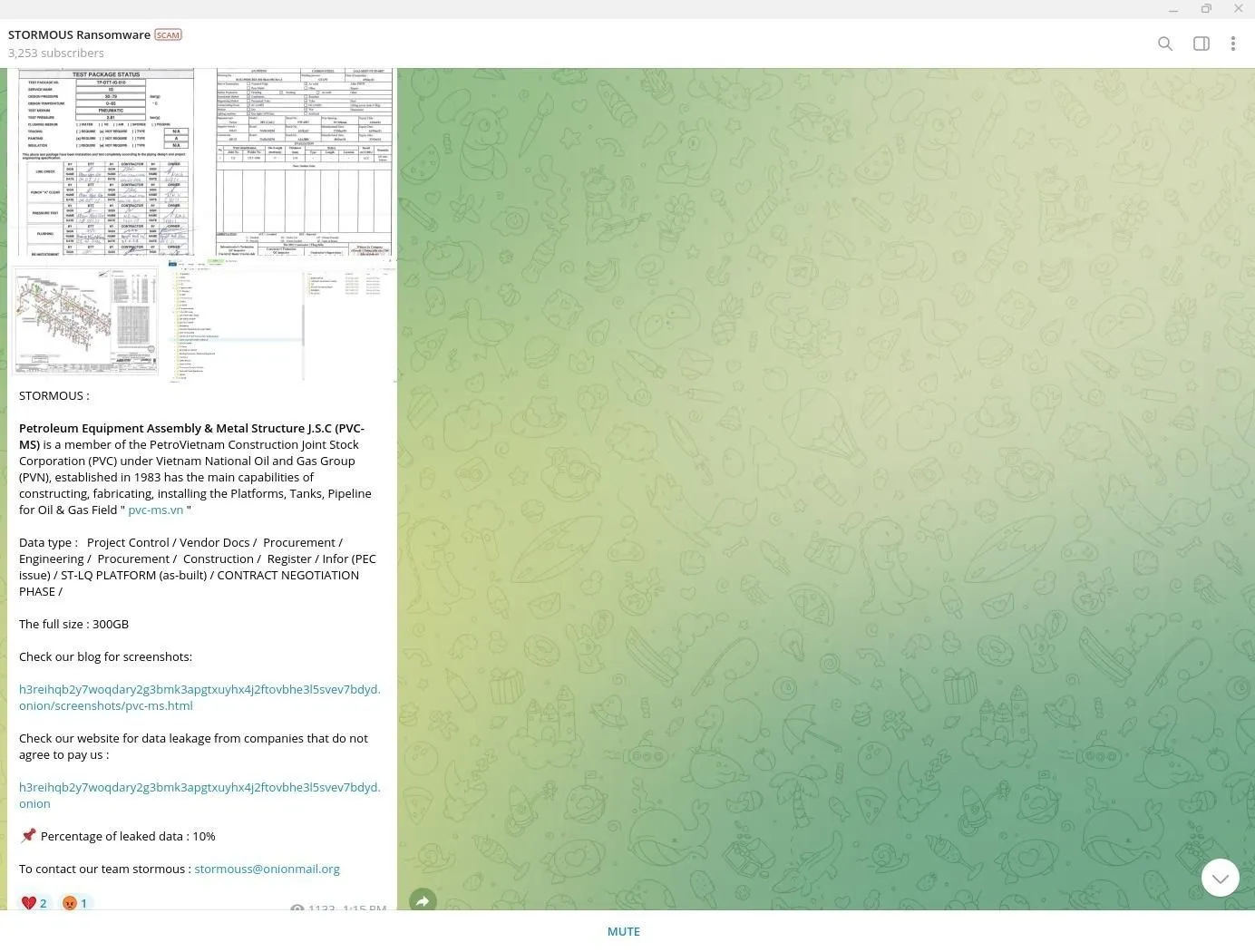
Stormous telegram claim of the compromised data (Source: Resecurity research)
According to research, Stormous has previously targeted countries for geopolitical reasons, and their actions are part of a larger strategy against nations they consider adversarial. The group, which resurfaced in May 2022 after a brief hiatus, has concentrated on disrupting key industries and disclosing sensitive information. This attack on PVC-MS emphasizes the ongoing cyber threat landscape, particularly in critical infrastructure sectors like oil and gas.
4. Danish Energy Sector Hit by Unprecedented Cyberattacks
In May 2023, Denmark’s energy sector was hit by its largest cyberattack, with 22 companies targeted in three coordinated waves. SektorCERT detected the attacks, which began on May 11 when hackers exploited a command injection vulnerability (CVE-2023-28771) in Zyxel firewalls, compromising the infrastructure of 11 companies. Despite Zyxel’s April 2023 patch, many companies did not update, allowing attackers to gain access. The attackers specifically targeted vulnerable companies, implying advanced planning and access to sensitive data.
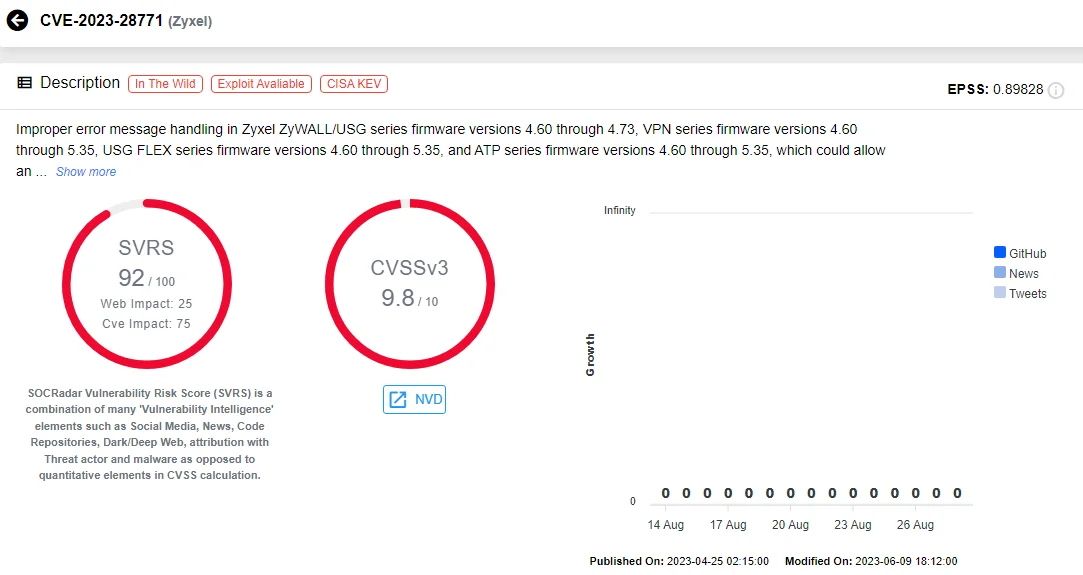
Vulnerability card of CVE-2023-28771 (SOCRadar Vulnerability Intelligence)
On May 22, the second wave involved the deployment of the Mirai botnet, which used compromised infrastructure to launch DDoS attacks against US and Hong Kong targets. Researchers believe that two new Zyxel vulnerabilities were exploited during this wave. The Russian-linked Sandworm group may have played a role in the final wave, but definitive attribution is uncertain. Despite the severity, the Danish power grid was unaffected, and SektorCERT made extensive recommendations to avoid future incidents.

5. Suncor

Suncor Energy factories
Suncor, a major energy company, experienced a cybersecurity breach in July 2023, disrupting debit and credit card processing at Petro-Canada gas stations across Canada. As a security precaution, Suncor began replacing employees’ laptops and desktop computers, indicating a serious breach. The incident raised concerns in the oil and gas industry, prompting companies to rethink their cybersecurity strategies, especially in light of rising threats to critical infrastructure.
The breach affected Petro-Canada’s payment systems and customer loyalty programs, potentially costing Suncor millions of dollars in lost revenue. The ongoing issue demonstrates the energy sector’s vulnerability to cyber threats. The incident serves as a wake-up call for the industry, highlighting the importance of strong cybersecurity measures as businesses across the sector reassess their IT systems and prepare for future attacks.
The Impact of Unpatched Vulnerabilities on Ransomware Attacks in the Energy Sector
According to the Sophos “The State of Ransomware in Critical Infrastructure 2024” report, the energy, oil, and gas sectors are increasingly vulnerable to ransomware attacks, with 49% of incidents in 2024 caused by exploited vulnerabilities, making it the leading entry point for attackers.
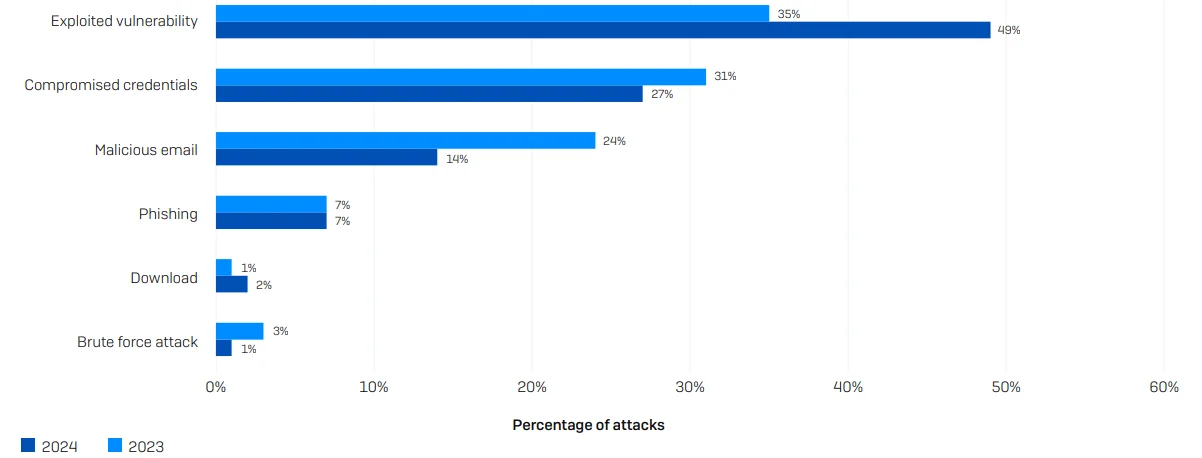
Percentage of ransomware attacks in the energy, gas and oil industries according to Sophos’ report
Compromised credentials also accounted for 27% of attacks, highlighting the ongoing risks associated with unpatched systems.
The report also noted that the proportion of attacks due to unpatched vulnerabilities has significantly increased over the past year, emphasizing the critical need for robust cybersecurity measures in these industries.
Unpatched vulnerabilities in the oil and gas industry pose a significant risk, frequently resulting in severe cyberattacks. SOCRadar’s Vulnerability Intelligence is critical for protecting against these threats, as it provides advanced alerts and real-time insights into critical exploits. Staying informed about actively exploited vulnerabilities allows you to quickly address unpatched systems and prevent disruptive breaches, ensuring your operations’ security.
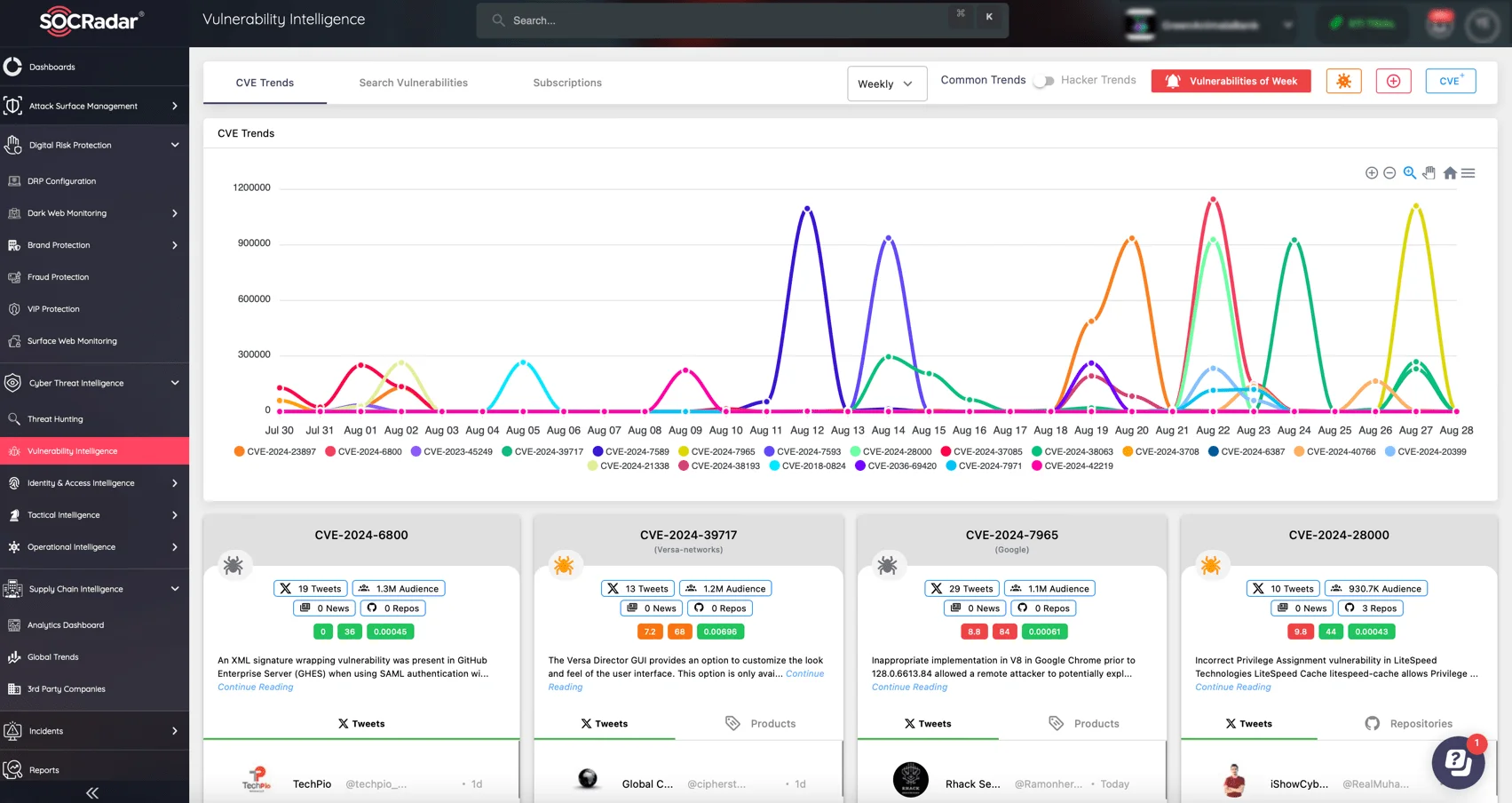
Stay alert with SOCRadar’s Vulnerability Intelligence module
SOCRadar’s instant alerting feature provides timely notifications about new vulnerabilities, allowing you to take immediate action to protect your digital assets. Tailored monitoring and global vulnerability trends enable you to stay ahead of emerging risks, strengthening your cybersecurity posture against the dangers posed by unpatched vulnerabilities.
Conclusion
As the oil and gas industry continues to navigate the complexities of an increasingly digital and interconnected world, the need for robust cybersecurity measures has never been more urgent. The high-profile cyberattacks of 2023-2024 underscore the vulnerability of critical infrastructure to disruptive and costly breaches.
From ransomware attacks, such as the Colonial Pipeline incident, to supply chain breaches and advanced persistent threats, the industry faces significant risks that can disrupt operations and cause substantial financial losses. As these examples demonstrate, a proactive approach to cybersecurity is essential for protecting critical infrastructure and maintaining the integrity of global energy supplies.
Protecting the oil and gas industry’s supply chain is critical. SOCRadar’s Supply Chain Intelligence provides complete visibility into your entire supply chain, analyzing over 50 million companies to detect potential risks before they occur. This allows you to proactively secure your supply chain while also maintaining a resilient digital ecosystem.
SOCRadar’s Supply Chain Intelligence module
SOCRadar’s advanced scoring systems, such as the Cyber Exposure Level and Popularity Score, allow you to make informed decisions about third-party relationships. SOCRadar streamlines your risk management strategy by focusing on the highest risk entities and automating third-party environment management, allowing you to stay ahead of emerging supply chain threats.

Source: Original Post