A January campaign of Lumma Stealer was observed utilizing an Italian domain, and a new campaign has since emerged exploiting a .it domain for malicious operations. This campaign employs a deceptive method known as ClickFix which tricks victims into executing malicious PowerShell code. By manipulating user interactions with a fake CAPTCHA, it covertly installs malware, rendering detection by security systems more difficult. Affected: Italian domain users, public administrations, cybersecurity sectors
Keypoints :
- A January campaign of Lumma Stealer observed using an Italian domain.
- A new campaign continues exploiting a .it domain for malicious activity.
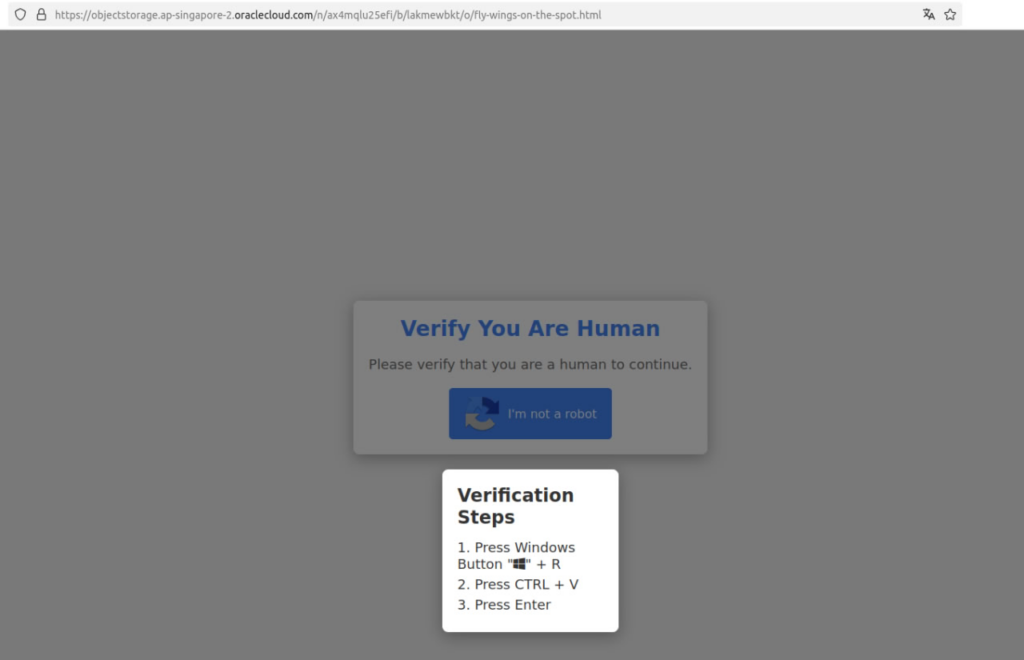
- The technique ClickFix presents a deceptive CAPTCHA to users.
- The CAPTCHA instruction prompts users to execute malicious PowerShell code.
- The malware disguises itself as an audio file with the .m4a extension.
- The initial malicious code is encoded in Base64 and subsequently generates more scripts.
- The final script uses PowerShell to download further malicious code from another domain.
- ClickFix has been increasingly utilized in other campaigns such as Safeguard Telegram.
- This approach leverages user actions, complicating detection efforts by security systems.
- Indicators of compromise (IoCs) have been published by CERT-AGID.
MITRE Techniques :
- T1059.001 – Command and Scripting Interpreter: PowerShell: The malicious code is executed using PowerShell commands embedded in a JavaScript file.
- T1071.001 – Application Layer Protocol: Web Protocols: The malicious PowerShell script downloads additional payloads from a new domain.
- T1005 – Data from Local System: The initial malware masquerades as an audio file and contains lengthy JavaScript payload coded in Base64.
- T1203 – Exploitation for Client Execution: The ClickFix method exploits user interaction to execute the malicious payload through deceptive CAPTCHA.
Indicator of Compromise :
- [Domain] .it (malicious domain used for redirection)
- [File] download URL for the disguised .m4a file (exact URL not provided)
- [PowerShell Command] JavaScript embedding malicious code that utilizes PowerShell.
- [JavaScript Code] Base64 encoded malicious JavaScript payload (exact code not provided).
- [XOR Key] AMSI_RESULT_NOT_DETECTED (refers to the XOR key for decoding the payload).
Views: 33